The Finite Field with 2 Elements the Simplest Finite Field Is GF(2) = F2
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Algorithmic Factorization of Polynomials Over Number Fields
Rose-Hulman Institute of Technology Rose-Hulman Scholar Mathematical Sciences Technical Reports (MSTR) Mathematics 5-18-2017 Algorithmic Factorization of Polynomials over Number Fields Christian Schulz Rose-Hulman Institute of Technology Follow this and additional works at: https://scholar.rose-hulman.edu/math_mstr Part of the Number Theory Commons, and the Theory and Algorithms Commons Recommended Citation Schulz, Christian, "Algorithmic Factorization of Polynomials over Number Fields" (2017). Mathematical Sciences Technical Reports (MSTR). 163. https://scholar.rose-hulman.edu/math_mstr/163 This Dissertation is brought to you for free and open access by the Mathematics at Rose-Hulman Scholar. It has been accepted for inclusion in Mathematical Sciences Technical Reports (MSTR) by an authorized administrator of Rose-Hulman Scholar. For more information, please contact [email protected]. Algorithmic Factorization of Polynomials over Number Fields Christian Schulz May 18, 2017 Abstract The problem of exact polynomial factorization, in other words expressing a poly- nomial as a product of irreducible polynomials over some field, has applications in algebraic number theory. Although some algorithms for factorization over algebraic number fields are known, few are taught such general algorithms, as their use is mainly as part of the code of various computer algebra systems. This thesis provides a summary of one such algorithm, which the author has also fully implemented at https://github.com/Whirligig231/number-field-factorization, along with an analysis of the runtime of this algorithm. Let k be the product of the degrees of the adjoined elements used to form the algebraic number field in question, let s be the sum of the squares of these degrees, and let d be the degree of the polynomial to be factored; then the runtime of this algorithm is found to be O(d4sk2 + 2dd3). -

January 10, 2010 CHAPTER SIX IRREDUCIBILITY and FACTORIZATION §1. BASIC DIVISIBILITY THEORY the Set of Polynomials Over a Field
January 10, 2010 CHAPTER SIX IRREDUCIBILITY AND FACTORIZATION §1. BASIC DIVISIBILITY THEORY The set of polynomials over a field F is a ring, whose structure shares with the ring of integers many characteristics. A polynomials is irreducible iff it cannot be factored as a product of polynomials of strictly lower degree. Otherwise, the polynomial is reducible. Every linear polynomial is irreducible, and, when F = C, these are the only ones. When F = R, then the only other irreducibles are quadratics with negative discriminants. However, when F = Q, there are irreducible polynomials of arbitrary degree. As for the integers, we have a division algorithm, which in this case takes the form that, if f(x) and g(x) are two polynomials, then there is a quotient q(x) and a remainder r(x) whose degree is less than that of g(x) for which f(x) = q(x)g(x) + r(x) . The greatest common divisor of two polynomials f(x) and g(x) is a polynomial of maximum degree that divides both f(x) and g(x). It is determined up to multiplication by a constant, and every common divisor divides the greatest common divisor. These correspond to similar results for the integers and can be established in the same way. One can determine a greatest common divisor by the Euclidean algorithm, and by going through the equations in the algorithm backward arrive at the result that there are polynomials u(x) and v(x) for which gcd (f(x), g(x)) = u(x)f(x) + v(x)g(x) . -
![2.4 Algebra of Polynomials ([1], P.136-142) in This Section We Will Give a Brief Introduction to the Algebraic Properties of the Polynomial Algebra C[T]](https://docslib.b-cdn.net/cover/8740/2-4-algebra-of-polynomials-1-p-136-142-in-this-section-we-will-give-a-brief-introduction-to-the-algebraic-properties-of-the-polynomial-algebra-c-t-408740.webp)
2.4 Algebra of Polynomials ([1], P.136-142) in This Section We Will Give a Brief Introduction to the Algebraic Properties of the Polynomial Algebra C[T]
2.4 Algebra of polynomials ([1], p.136-142) In this section we will give a brief introduction to the algebraic properties of the polynomial algebra C[t]. In particular, we will see that C[t] admits many similarities to the algebraic properties of the set of integers Z. Remark 2.4.1. Let us first recall some of the algebraic properties of the set of integers Z. - division algorithm: given two integers w, z 2 Z, with jwj ≤ jzj, there exist a, r 2 Z, with 0 ≤ r < jwj such that z = aw + r. Moreover, the `long division' process allows us to determine a, r. Here r is the `remainder'. - prime factorisation: for any z 2 Z we can write a1 a2 as z = ±p1 p2 ··· ps , where pi are prime numbers. Moreover, this expression is essentially unique - it is unique up to ordering of the primes appearing. - Euclidean algorithm: given integers w, z 2 Z there exists a, b 2 Z such that aw + bz = gcd(w, z), where gcd(w, z) is the `greatest common divisor' of w and z. In particular, if w, z share no common prime factors then we can write aw + bz = 1. The Euclidean algorithm is a process by which we can determine a, b. We will now introduce the polynomial algebra in one variable. This is simply the set of all polynomials with complex coefficients and where we make explicit the C-vector space structure and the multiplicative structure that this set naturally exhibits. Definition 2.4.2. - The C-algebra of polynomials in one variable, is the quadruple (C[t], α, σ, µ)43 where (C[t], α, σ) is the C-vector space of polynomials in t with C-coefficients defined in Example 1.2.6, and µ : C[t] × C[t] ! C[t];(f , g) 7! µ(f , g), is the `multiplication' function. -
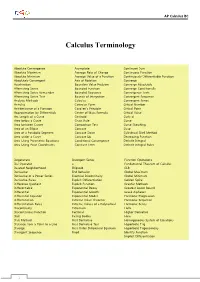
Calculus Terminology
AP Calculus BC Calculus Terminology Absolute Convergence Asymptote Continued Sum Absolute Maximum Average Rate of Change Continuous Function Absolute Minimum Average Value of a Function Continuously Differentiable Function Absolutely Convergent Axis of Rotation Converge Acceleration Boundary Value Problem Converge Absolutely Alternating Series Bounded Function Converge Conditionally Alternating Series Remainder Bounded Sequence Convergence Tests Alternating Series Test Bounds of Integration Convergent Sequence Analytic Methods Calculus Convergent Series Annulus Cartesian Form Critical Number Antiderivative of a Function Cavalieri’s Principle Critical Point Approximation by Differentials Center of Mass Formula Critical Value Arc Length of a Curve Centroid Curly d Area below a Curve Chain Rule Curve Area between Curves Comparison Test Curve Sketching Area of an Ellipse Concave Cusp Area of a Parabolic Segment Concave Down Cylindrical Shell Method Area under a Curve Concave Up Decreasing Function Area Using Parametric Equations Conditional Convergence Definite Integral Area Using Polar Coordinates Constant Term Definite Integral Rules Degenerate Divergent Series Function Operations Del Operator e Fundamental Theorem of Calculus Deleted Neighborhood Ellipsoid GLB Derivative End Behavior Global Maximum Derivative of a Power Series Essential Discontinuity Global Minimum Derivative Rules Explicit Differentiation Golden Spiral Difference Quotient Explicit Function Graphic Methods Differentiable Exponential Decay Greatest Lower Bound Differential -

Finding Equations of Polynomial Functions with Given Zeros
Finding Equations of Polynomial Functions with Given Zeros 푛 푛−1 2 Polynomials are functions of general form 푃(푥) = 푎푛푥 + 푎푛−1 푥 + ⋯ + 푎2푥 + 푎1푥 + 푎0 ′ (푛 ∈ 푤ℎ표푙푒 # 푠) Polynomials can also be written in factored form 푃(푥) = 푎(푥 − 푧1)(푥 − 푧2) … (푥 − 푧푖) (푎 ∈ ℝ) Given a list of “zeros”, it is possible to find a polynomial function that has these specific zeros. In fact, there are multiple polynomials that will work. In order to determine an exact polynomial, the “zeros” and a point on the polynomial must be provided. Examples: Practice finding polynomial equations in general form with the given zeros. Find an* equation of a polynomial with the Find the equation of a polynomial with the following two zeros: 푥 = −2, 푥 = 4 following zeroes: 푥 = 0, −√2, √2 that goes through the point (−2, 1). Denote the given zeros as 푧1 푎푛푑 푧2 Denote the given zeros as 푧1, 푧2푎푛푑 푧3 Step 1: Start with the factored form of a polynomial. Step 1: Start with the factored form of a polynomial. 푃(푥) = 푎(푥 − 푧1)(푥 − 푧2) 푃(푥) = 푎(푥 − 푧1)(푥 − 푧2)(푥 − 푧3) Step 2: Insert the given zeros and simplify. Step 2: Insert the given zeros and simplify. 푃(푥) = 푎(푥 − (−2))(푥 − 4) 푃(푥) = 푎(푥 − 0)(푥 − (−√2))(푥 − √2) 푃(푥) = 푎(푥 + 2)(푥 − 4) 푃(푥) = 푎푥(푥 + √2)(푥 − √2) Step 3: Multiply the factored terms together. Step 3: Multiply the factored terms together 푃(푥) = 푎(푥2 − 2푥 − 8) 푃(푥) = 푎(푥3 − 2푥) Step 4: The answer can be left with the generic “푎”, or a value for “푎”can be chosen, Step 4: Insert the given point (−2, 1) to inserted, and distributed. -

THE RESULTANT of TWO POLYNOMIALS Case of Two
THE RESULTANT OF TWO POLYNOMIALS PIERRE-LOÏC MÉLIOT Abstract. We introduce the notion of resultant of two polynomials, and we explain its use for the computation of the intersection of two algebraic curves. Case of two polynomials in one variable. Consider an algebraically closed field k (say, k = C), and let P and Q be two polynomials in k[X]: r r−1 P (X) = arX + ar−1X + ··· + a1X + a0; s s−1 Q(X) = bsX + bs−1X + ··· + b1X + b0: We want a simple criterion to decide whether P and Q have a common root α. Note that if this is the case, then P (X) = (X − α) P1(X); Q(X) = (X − α) Q1(X) and P1Q − Q1P = 0. Therefore, there is a linear relation between the polynomials P (X);XP (X);:::;Xs−1P (X);Q(X);XQ(X);:::;Xr−1Q(X): Conversely, such a relation yields a common multiple P1Q = Q1P of P and Q with degree strictly smaller than deg P + deg Q, so P and Q are not coprime and they have a common root. If one writes in the basis 1; X; : : : ; Xr+s−1 the coefficients of the non-independent family of polynomials, then the existence of a linear relation is equivalent to the vanishing of the following determinant of size (r + s) × (r + s): a a ··· a r r−1 0 ar ar−1 ··· a0 .. .. .. a a ··· a r r−1 0 Res(P; Q) = ; bs bs−1 ··· b0 b b ··· b s s−1 0 . .. .. .. bs bs−1 ··· b0 with s lines with coefficients ai and r lines with coefficients bj. -

Resultant and Discriminant of Polynomials
RESULTANT AND DISCRIMINANT OF POLYNOMIALS SVANTE JANSON Abstract. This is a collection of classical results about resultants and discriminants for polynomials, compiled mainly for my own use. All results are well-known 19th century mathematics, but I have not inves- tigated the history, and no references are given. 1. Resultant n m Definition 1.1. Let f(x) = anx + ··· + a0 and g(x) = bmx + ··· + b0 be two polynomials of degrees (at most) n and m, respectively, with coefficients in an arbitrary field F . Their resultant R(f; g) = Rn;m(f; g) is the element of F given by the determinant of the (m + n) × (m + n) Sylvester matrix Syl(f; g) = Syln;m(f; g) given by 0an an−1 an−2 ::: 0 0 0 1 B 0 an an−1 ::: 0 0 0 C B . C B . C B . C B C B 0 0 0 : : : a1 a0 0 C B C B 0 0 0 : : : a2 a1 a0C B C (1.1) Bbm bm−1 bm−2 ::: 0 0 0 C B C B 0 bm bm−1 ::: 0 0 0 C B . C B . C B C @ 0 0 0 : : : b1 b0 0 A 0 0 0 : : : b2 b1 b0 where the m first rows contain the coefficients an; an−1; : : : ; a0 of f shifted 0; 1; : : : ; m − 1 steps and padded with zeros, and the n last rows contain the coefficients bm; bm−1; : : : ; b0 of g shifted 0; 1; : : : ; n−1 steps and padded with zeros. In other words, the entry at (i; j) equals an+i−j if 1 ≤ i ≤ m and bi−j if m + 1 ≤ i ≤ m + n, with ai = 0 if i > n or i < 0 and bi = 0 if i > m or i < 0. -

Algebraic Combinatorics and Resultant Methods for Polynomial System Solving Anna Karasoulou
Algebraic combinatorics and resultant methods for polynomial system solving Anna Karasoulou To cite this version: Anna Karasoulou. Algebraic combinatorics and resultant methods for polynomial system solving. Computer Science [cs]. National and Kapodistrian University of Athens, Greece, 2017. English. tel-01671507 HAL Id: tel-01671507 https://hal.inria.fr/tel-01671507 Submitted on 5 Jan 2018 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. ΕΘΝΙΚΟ ΚΑΙ ΚΑΠΟΔΙΣΤΡΙΑΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΑΘΗΝΩΝ ΣΧΟΛΗ ΘΕΤΙΚΩΝ ΕΠΙΣΤΗΜΩΝ ΤΜΗΜΑ ΠΛΗΡΟΦΟΡΙΚΗΣ ΚΑΙ ΤΗΛΕΠΙΚΟΙΝΩΝΙΩΝ ΠΡΟΓΡΑΜΜΑ ΜΕΤΑΠΤΥΧΙΑΚΩΝ ΣΠΟΥΔΩΝ ΔΙΔΑΚΤΟΡΙΚΗ ΔΙΑΤΡΙΒΗ Μελέτη και επίλυση πολυωνυμικών συστημάτων με χρήση αλγεβρικών και συνδυαστικών μεθόδων Άννα Ν. Καρασούλου ΑΘΗΝΑ Μάιος 2017 NATIONAL AND KAPODISTRIAN UNIVERSITY OF ATHENS SCHOOL OF SCIENCES DEPARTMENT OF INFORMATICS AND TELECOMMUNICATIONS PROGRAM OF POSTGRADUATE STUDIES PhD THESIS Algebraic combinatorics and resultant methods for polynomial system solving Anna N. Karasoulou ATHENS May 2017 ΔΙΔΑΚΤΟΡΙΚΗ ΔΙΑΤΡΙΒΗ Μελέτη και επίλυση πολυωνυμικών συστημάτων με -

Formula Sheet 1 Factoring Formulas 2 Exponentiation Rules
Formula Sheet 1 Factoring Formulas For any real numbers a and b, (a + b)2 = a2 + 2ab + b2 Square of a Sum (a − b)2 = a2 − 2ab + b2 Square of a Difference a2 − b2 = (a − b)(a + b) Difference of Squares a3 − b3 = (a − b)(a2 + ab + b2) Difference of Cubes a3 + b3 = (a + b)(a2 − ab + b2) Sum of Cubes 2 Exponentiation Rules p r For any real numbers a and b, and any rational numbers and , q s ap=qar=s = ap=q+r=s Product Rule ps+qr = a qs ap=q = ap=q−r=s Quotient Rule ar=s ps−qr = a qs (ap=q)r=s = apr=qs Power of a Power Rule (ab)p=q = ap=qbp=q Power of a Product Rule ap=q ap=q = Power of a Quotient Rule b bp=q a0 = 1 Zero Exponent 1 a−p=q = Negative Exponents ap=q 1 = ap=q Negative Exponents a−p=q Remember, there are different notations: p q a = a1=q p q ap = ap=q = (a1=q)p 1 3 Quadratic Formula Finally, the quadratic formula: if a, b and c are real numbers, then the quadratic polynomial equation ax2 + bx + c = 0 (3.1) has (either one or two) solutions p −b ± b2 − 4ac x = (3.2) 2a 4 Points and Lines Given two points in the plane, P = (x1; y1);Q = (x2; y2) you can obtain the following information: p 2 2 1. The distance between them, d(P; Q) = (x2 − x1) + (y2 − y1) . x + x y + y 2. -

Early History of Algebra: a Sketch
Math 160, Fall 2005 Professor Mariusz Wodzicki Early History of Algebra: a Sketch Mariusz Wodzicki Algebra has its roots in the theory of quadratic equations which obtained its original and quite full development in ancient Akkad (Mesopotamia) at least 3800 years ago. In Antiq- uity, this earliest Algebra greatly influenced Greeks1 and, later, Hindus. Its name, however, is of Arabic origin. It attests to the popularity in Europe of High Middle Ages of Liber al- gebre et almuchabole — the Latin translation of the short treatise on the subject of solving quadratic equations: Q Ì Al-kitabu¯ ’l-muhtas.aru f¯ı é ÊK.A®ÜÏ@ð .m. '@H . Ak ú¯ QåJjÜÏ@ H. AJº Ë@ – h. isabi¯ ’l-gabriˇ wa-’l-muqabalati¯ (A summary of the calculus of gebr and muqabala). The original was composed circa AD 830 in Arabic at the House of Wisdom—a kind of academy in Baghdad where in IX-th century a number of books were compiled or translated into Arabic chiefly from Greek and Syriac sources—by some Al-Khwarizmi2 whose name simply means that he was a native of the ancient city of Khorezm (modern Uzbekistan). Three Latin translations of his work are known: by Robert of Chester (executed in Segovia in 1140), by Gherardo da Cremona3 (Toledo, ca. 1170) and by Guglielmo de Lunis (ca. 1250). Al-Khwarizmi’s name lives today in the word algorithm as a monument to the popularity of his other work, on Indian Arithmetic, which circulated in Europe in several Latin versions dating from before 1143, and spawned a number of so called algorismus treatises in XIII-th and XIV-th Centuries. -

Algebraic Properties of the Ring of General Exponential Polynomials
Complex Varrahler. 1989. Vol. 13. pp. 1-20 Reprints avdnhle directly from the publisher Photucopyng perm~ftedby license only 1 1989 Gordon and Breach, Science Pubhsherr. Inc. Printed in the United States of Amer~ca Algebraic Properties of the Ring of General Exponential Polynomials C. WARD HENSON and LEE A. RUBEL Department of Mathematics, University of Illinois, 7409 West Green St., Urbana, IL 67807 and MICHAEL F. SINGER Department of Mathematics, North Carolina State University, P.O. Box 8205, Raleigh, NC 27695 AMS No. 30DYY. 32A9Y Communicated: K. F. Barth and K. P. Gilbert (Receitled September 15. 1987) INTRODUCTION The motivation for the results given in this paper is our desire to study the entire functions of several variables which are defined by exponential terms. By an exponential term (in n variables) we mean a formal expression which can be built up from complex constants and the variables z,, . , z, using the symbols + (for addition), . (for multiplication) and exp(.) (for the exponential function with the constant base e). (These are the terms and the functions considered in Section 5 of [I 11. There the set of exponential terms was denoted by C. Note that arbitrary combinations and iterations of the permitted functions can be formed; thus such expressions as are included here.) Each exponential term in n variables evidently defines an analytic Downloaded by [North Carolina State University] at 18:38 26 May 2015 function on C";we denote the ring of all such functions on Cn by A,. This is in fact an exponential ring;that is, A, is closed under application of the exponential function. -

1 Polynomial Rings
AM 106/206: Applied Algebra Prof. Salil Vadhan Lecture Notes 16 November 16, 2009 1 Polynomial Rings • Reading: Gallian Ch. 16 • Def: Let R be a commutative ring with unity. The ring of polynomials over R is the ring 2 R[x] consisting of all expressions of the form a0 + a1x + a2x + ···, where each ai 2 R and 2 3 all but finitely many ai's are zero. (We usually omit the zero terms, so 1 + 5x + 10x + 3x is shorthand for 1 + 5x + 10x2 + 3x3 + 0x4 + 0x5 + ···.) P i P i For two polynomials p(x) = i aix and q(x) = i bix , their sum (p + q)(x) is defined to be P i P Pi i the polynomial i(ai +bi)x and their product (pq)(x) is the polynomial i( j=0(ajbj−i))x , where ai + bi and ajbj−i are defined using the operations of R. 2 • Example: sum and product of p(x) = 3x + 4x + 1 and q(x) = 5x + 6 in Z7[x]. • Remarks { R[x] is a commutative ring with unity. { Two different polynomials can define the same function on R, but we still treat them as different elements of R[x]. For example p(x) = x · (x − 1) ··· (x − p + 1) defines the zero function on Zp, but is not the zero polynomial (why?). { For polynomials of degree at most n, their sum can be computed using n operations over R and their product using O(n2) operations over R. (Best known multiplication algorithm uses O(n log n) operations.) Note similarity with sum and product of integers! P i • The degree deg(p) of a nonzero polynomial p(x) = i aix is the largest d such that ad 6= 0.