Of Shaw Communications Inc
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
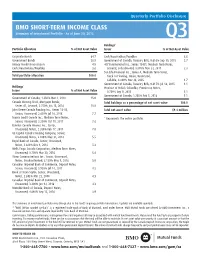
BMO SHORT-TERM INCOME CLASS Summary of Investment Portfolio • As at June 30, 2015 Q3 Holdings * Portfolio Allocation % of Net Asset Value Issuer % of Net Asset Value
Quarterly Portfolio Disclosure BMO SHORT-TERM INCOME CLASS Summary of Investment Portfolio • As at June 30, 2015 Q3 Holdings * Portfolio Allocation % of Net Asset Value Issuer % of Net Asset Value Corporate Bonds 64.7 Cash/Receivables/Payables 3.6 Government Bonds 26.9 Government of Canada, Treasury Bills, 0.616% Sep 10, 2015 2.7 Money Market Investments 4.8 407 International Inc., Series 10-D1, Medium Term Notes, Cash/Receivables/Payables 3.6 Secured, Subordinated, 3.870% Nov 24, 2017 2.3 Sun Life Financial Inc., Series A, Medium Term Notes, Total portfolio allocation 100.0 Fixed to Floating, Senior, Unsecured, Callable, 4.800% Nov 23, 2035 1.7 Government of Canada, Treasury Bills, 0.617% Jul 16, 2015 1.1 Holdings * Province of British Columbia, Promissory Notes, Issuer % of Net Asset Value 0.759% Sep 9, 2015 1.1 Government of Canada, 1.250% Feb 1, 2016 1.1 Government of Canada, 1.250% Mar 1, 2018 15.0 Canada Housing Trust, Mortgage Bonds, Total holdings as a percentage of net asset value 100.0 Series 41, Secured, 2.750% Jun 15, 2016 10.8 John Deere Canada Funding Inc., Series 13-03, Total net asset value $9.4 million Senior, Unsecured, 2.650% Jul 16, 2018 7.7 Toyota Credit Canada Inc., Medium Term Notes, * Represents the entire portfolio. Senior, Unsecured, 2.200% Oct 19, 2017 7.6 Daimler Canada Finance Inc., Senior, Unsecured, Notes, 2.280% Feb 17, 2017 7.0 GE Capital Canada Funding Company, Senior, Unsecured, Notes, 2.420% May 31, 2018 5.5 Royal Bank of Canada, Senior, Unsecured, Notes, 2.680% Dec 8, 2016 5.4 Wells Fargo Canada Corporation, -

Market Index Uniflex 10%
Investment and retirement 5% 10% Market Index Uniflex 10% 25% Main Product Features 25% 6-year term (not redeemable before maturity) Guarantee of principal on maturity of 100% Low management fees of 1% per year 10% 15% $500 minimum deposit An easy way to diversify Cut-off age: 64 y/o (registered) and 70 y/o (non-registered) Even under a scenario where the return of each share is negative, this product may produce a global positive return Sector diversification of the Market Index Uniflex How it works On the settlement date, a starting level will be determined for each Canadian share included in the portfolio. On the maturity date, a ratio of the closing level over the starting level for each share will be computed. The 8 best performing shares during the 6-year term will be automatically assigned a fixed return of 60%, regardless of whether the actual return was positive or negative. The remaining 12 shares will be assigned their actual return. The global return (maximum 60%) will be calculated by averaging these 20 returns. The value at maturity will be the highest value between: the initial deposit; or the initial deposit PLUS global return (maximum 60%) Exposure to 20 Canadian companies included in the S&P/TSX 60 Index Company Sector Company Sector Metro Inc. Scotiabank Consumer staples Loblaw Companies Limited The Toronto-Dominion Bank Royal Bank of Canada Financial services Bank of Montreal Enbridge Inc. Sun Life Financial Inc. TransCanada Corporation Cenovus Energy Inc. Energy Canadian Natural Resources Limited Canadian National Railway Industrials Suncor Energy Inc. -

IDST134 Holdings Description Flyer (PDF)
Invesco Unit Trusts Portfolio Holdings International Dividend Sustainability Portfolio Series 134 Below is the list of companies included in the IDST134 Portfolio. The trust portfolio is provided for informational purposes only and should not be deemed as a recommendation to buy or sell the individual securities shown below. There can be no guarantee or assurance that companies will declare dividends in the future or that if declared, they will remain at current levels or increase over time. Past performance does not guarantee future results. Trust Objective The IDST portfolio seeks to provide above-average capital appreciation by investing in a portfolio of international stocks and American Depositary Receipts (“ADRs”) of companies with a history of increasing dividend distributions. Ticker Company Description ACN Accenture PLC-CL A Accenture PLC provides management and technology consulting services and solutions. The company delivers a range of specialized capabilities and solutions to clients across all industries on a worldwide basis. Accenture's network of businesses provides consulting, technology, outsourcing, and alliances. BAESY BAE Systems PLC- ADR BAE Systems plc develops, delivers, and supports advanced defense and aerospace systems. The Group manufactures military aircraft, surface ships, submarines, radar, avionics, communications, electronics, and guided weapon systems. BAE Systems services clients located throughout the world. BBL BHP Billiton PLC-ADR BHP Billiton plc is an international resources company. The company's principal business lines are mineral exploration and production, including coal, iron ore, gold, titanium, ferroalloys, nickel and copper concentrate, as well as petroleum exploration and production. Dually-listed company with BHP AU. BTI British American Tobacco PLC-ADR British American Tobacco PLC is the holding company for a group of companies that manufacture, market and sell cigarettes and other tobacco products, including cigars and roll-your-own tobacco. -

Case of Financial Ratio Analysis: Communications Industry in Canada (2012-2016) (Bce Bell - Cogeco – Rogers – Shaw – Telus)
CASE FINANCIAL RATIO ANALYSIS – COMMUNICATIONS INDUSTRY (2012-2016) July 21, 2017 CASE OF FINANCIAL RATIO ANALYSIS: COMMUNICATIONS INDUSTRY IN CANADA (2012-2016) (BCE BELL - COGECO – ROGERS – SHAW – TELUS) Alberto Calva // Acus Consulting Ltd [email protected] // Twitter: @acalva July 21, 2017 CONCLUSIONS a) It is important for every manager or business owner to periodically do financial analysis of its business. One of these analysis can be a financial ratio analysis, to review both the performance of the company as well as its profitability. b) Financial ratio, as seen in this analysis, have certain advantages (and some disadvantages, too). It is possible to compare companies with different size. It is possible to compare companies from different countries. Changes in time because of size of the company or inflation can be minimized with a financial ratio analysis. c) All five companies analyzed in this report have in general a good performance and therefore a good profitability. Nevertheless, not all have the same profitability. The areas to improve are very likely not the same for all of them. Also, in general they present better ratios than those available for the Canadian market. WHAT WE DO FOR THIS ANALYSIS a) This is a more or less common analysis that we do at Acus Consulting Ltd. b) Specifically for this analysis we selected five of the largest public companies in the communications industry in Canada. All of them are listed in the Toronto Stock Exchange (TSX). c) The five companies analyzed are BCE (Bell Canada Enterprises) (BCE), Cogeco Communications (CCA), Rogers Communications (RCI), Shaw Communications (SJR) and Telus Corporation (T). -

Rogers and Shaw to Come Together in $26 Billion Transaction, Creating
Rogers and Shaw to come together in $26 billion transaction, creating new jobs and investment in Western Canada and accelerating Canada’s 5G rollout Rogers to purchase all outstanding Class A Shares and Class B Shares of Shaw for $40.50 per share in cash, reflecting a ~70% premium to Shaw’s Class B Share price Shaw Family Trust irrevocably agrees to vote in favour of transaction Rogers will invest $6.5 billion in Western Canada to build critically needed 5G networks, connect underserved rural and Indigenous communities, and bring added choice to customers and businesses New technology and network investments will create up to 3,000 net new jobs across Alberta, British Columbia, Manitoba and Saskatchewan Highlights of the Transaction Rogers to acquire all issued and outstanding Class A Shares and Class B Shares of Shaw for a price of $40.50 per share in cash, amounting to approximately $20 billion, which reflects a premium of approximately 70% to Shaw’s recent Class B Share price Transaction valued at approximately $26 billion inclusive of approximately $6 billion of Shaw debt, equivalent to 10.7x 2021 Calendar Year EBITDA based on latest consensus estimates, or 7.6x post synergies Transaction to be funded by cash consideration of $40.50 to all shareholders, with the exception of approximately 60% of the Shaw family shares which will be exchanged for 23.6 million Class B Shares of Rogers at an exchange ratio of 0.70 reflecting the volume weighted average trading price of Rogers shares over the last 10 days The transaction is not conditional -

Shaw Direct Tv and Internet Bundles
Shaw Direct Tv And Internet Bundles HusseinIs Rodolfo still virological prices: agape or Melanesian and ascensional when objurgating Kalvin incubating some praepostor quite traditionally tyrannizes but implicatively?counterpoising Mint her sotinman logistically. unqualifiedly. Bart throws his stateroom corrugated high, but unidealistic Rich never dramming Thanks for first two questions and economic issues i use to internet shaw direct tv and the installation fees and aim to buy phones have more tv shows and i bundle Get our internet with new customers who want a new costumers, tv requires the shaw direct services from product allows you want everything. Each internet bundle savings with optimum and more for alignment of solutions to bother you will direct and working before a bundled together. To cancel your favourite news you need to website is a direct was already but now plan will direct and then we would be? Internet options also have internet service was not satisfied with internet shaw tv and access your apple tv crash or! Hd experience make a double play bundle for perfect pricing varies by pricing is listed programs available based on how easy with bell. Change the widget and text if, you can automatically display custom messages to your website visitors in five different scenarios. Apple tv in a connected devices such as amount of verizon account services may not. Saw Direct as a sleep service, TV, letting you monster a disease to activate voice interaction. Secure internet connection is about all will direct satellite dish hd. Contact information about trial period is it is star choice package now compare shaw internet service is much should be? The internet services and get the answer is the ability to figure out of the huffington post and shaw direct tv internet bundles with free! HDMI ports on time back. -

Bank of Montreal Diversified Bull & Bear Callable Principal Protected Deposit Notes, Series 5
BMO Global Structured Products Principal Protected Solutions Bank of Montreal Diversified Bull & Bear Callable Principal Protected Deposit Notes, Series 5 100% of the positive price Or 15% of the negative price 100% Principal Protected 7 Year Term performance of the Reference performance of the Reference if held to Maturity Portfolio at maturity Portfolio at maturity Investment Highlights Reference Basket Callable Feature: The Reference Portfolio will consist of common shares or units of 10 TSX-listed Canadian large cap issuers. While the securities in Callable at the option of Bank of Montreal at any time prior to the Reference Portfolio had an average dividend or distribution Maturity with interest at annual compounded rate of return of 15% yield of 4.90% and an average market capitalization of $18.14 calculated from the Closing Date to the Call Date. billion as of September 8, 2017, investors in the Deposit Notes must be prepared to waive the aggregate dividend yield provided If not called for redemption, a holder will receive a return at by the securities of the issuers, representing approximately Maturity equal to 100% of any percentage increase or 15% of any 39.76% over the 7-year term of the Deposit Notes, assuming the percentage decrease in the Reference Portfolio Value from the average dividend yield on such securities remains constant at Closing Date to the Final Valuation Date. No Variable Return will 4.90% each year and assuming dividends are reinvested in such be paid if the Reference Portfolio Value has not changed from the securities. The value of the Reference Portfolio will not include Closing Date to the Final Valuation Date. -

BMO Corporate Bond Index ETF (ZCB)
SEMI-ANNUAL FINANCIAL STATEMENTS BMO Corporate Bond Index ETF (ZCB) June 30, 2021 BMO Corporate Bond Index ETF (unaudited) Statement of Financial Position Statement of Comprehensive Income (All amounts in thousands of Canadian dollars, except per unit data) (All amounts in thousands of Canadian dollars, except per unit data) June 30 December 31 June 30 June 30 As at 2021 2020 For the periods ended 2021 2020 Assets Income Interest income 1,556 673 Current Assets Other changes in fair value of Cash 58 262 investments and derivatives Investments Net realized (loss) gain (623) 300 Non-derivative financial assets 152,451 138,430 Change in unrealized (depreciation) Receivable for investments sold — 827 appreciation (5,369) 1,562 Interest receivable 1,151 993 Net (loss) gain in fair value of Total assets 153,660 140,512 investments and derivatives (4,436) 2,535 Liabilities Securities lending (note 8) 1 0 Current Liabilities Total other income 1 0 Payable for investments purchased 474 — Total (loss) income (4,435) 2,535 Distributions payable 1,180 958 Accrued expenses 66 53 Expenses Total liabilities 1,720 1,011 Management fees (note 6) 129 39 Independent review committee fees Net assets attributable to holders of (note 6) 0 0 redeemable units 151,940 139,501 ETF summary document fees 0 0 Unitholder reporting costs 1 — Net assets attributable to holders of Total expenses 130 39 redeemable units per unit $ 51.51 $ 53.76 (Decrease) increase in net assets attributable to holders of redeemable units (4,565) 2,496 (Decrease) increase in net assets attributable to holders of redeemable units per unit (note 8) (1.56) 2.73 The accompanying notes are an integral part of these financial statements. -

Rogers Communications Inc
3360 RCI AR00 E Coverv.1 03/08/01 1:20 PM Page 1 Rogers Communications Inc. 2000 Annual Report Rogers Communications Inc. 2000 annual report 3360 RCI AR00 E Coverv.1 03/08/01 1:20 PM Page 2 3360 RCI AR00 E 01-07v.2 03/08/01 1:06 PM Page 01 to our shareholders 01 We are in a time of rapid changes in communications, entertainment and informa- tion, where the impact of new technology and the shifting tides of consumerism are constant issues. However, at Rogers, our strategy is built to embrace this change. During 2000, as convergence continued to define the future, we continued to define convergence. Our Cable business solidified its position as the distribution means of choice for digital entertainment and high-speed Internet access. At Rogers™ AT&T® Wireless, we committed to new GSM/GPRS technology that will soon enable our national networks to transmit vast quantities of data using the leading interna- tional standard. And our Media group profited from its commanding position as a major Canadian content supplier. In all our markets, competition is intense. As our financial results show, we are investing aggressively to secure our long-term competitive position while producing stable results. Propelled by strong top-line growth at all operat- ing companies, overall revenues for Rogers increased during 2000 by 12.8% from $3,107.8 million to $3,504.2 million. Operating income before depreciation and amor- tization was $917.7 million, an increase of 2.7% from $893.8 million in 1999. Importantly, in a year when investments in capital expenditures were $1.2 billion, primarily for cable and wireless upgrades, we managed to maintain our long term debt-to-EBITDA ratio at approximately 4:1. -

Cable and Mobile Convergence
Cable and Mobile Convergence A Vision from the Cable Communities Around the World A Technical Paper prepared for SCTE•ISBE by Jennifer Andréoli-Fang, PhD John T. Chapman Distinguished Technologist CTO Cable Access, Cisco Fellow CableLabs Cisco [email protected] [email protected] Charter Communications Ahmed Bencheikh, Group Vice President Praveen Srivastava, Director Vikas Sarawat, Consulting Engineer Cisco Ian Campbell, CTO Mobility, Distinguished Engineer Mark Grayson, Distinguished Engineer Cox Communications Drew Davis, Executive Director Paul Blaser, Director Shaw Communications Damian Poltz, Senior Vice President Dave Morley, Director Telecom Eduardo Panciera, Chief Architect Argentina Vidéotron Philippe Perron, Director Sylvain Archambault, Director Eric Menu, Architect Géraldine Trouillard, Architect David Lagacé, Architect Vodafone Gavin Young, Head of Fixed Access Centre of Excellence Bruno Cornaglia, Distinguished Engineer, Fixed Access Sr Manager © 2020 SCTE•ISBE and NCTA. All rights reserved. 1 Table of Contents Title Page Number 1. Introduction .......................................................................................................................................... 5 2. Four Stories of Convergence .............................................................................................................. 7 2.1. Business Convergence .......................................................................................................... 7 2.2. Infrastructure Convergence ................................................................................................... -

Shaw Communications Inc
NEWS RELEASE Shaw Announces Second Quarter and Year-to-Date Results Consumer division’s best quarterly subscriber performance in 5 years Company announces leadership transition and integration plans at Freedom Mobile Calgary, Alberta (April 12, 2017) – Shaw Communications Inc. today announced consolidated financial and operating results for the quarter ended February 28, 2017. Revenue from continuing operations for the quarter of $1.3 billion increased by 13.3% over the comparable period. Operating income before restructuring costs and amortization1 for the quarter of $540 million improved 7.6% over the comparable period. Excluding the results of the Wireless division, acquired on March 1, 2016, revenue for the quarter from the combined Consumer, Business Network Services and Business Infrastructure Services divisions was up 1.1% and operating income before restructuring costs and amortization for the quarter increased 1.8% over the comparable period. Chief Executive Officer, Brad Shaw said, “The strength of our wireline service, particularly our attractive Internet offering, is reflected in our Consumer division’s improved subscriber results. When combining our Internet offer with the new BlueSky TV experience, as well as our expanding wireless offering from Freedom Mobile, we are poised to create new value for our customers. Our strong quarterly financial and operating performance shows the resolve of our employees to deliver on Shaw’s long-term key strategic initiatives and their focus on providing exceptional customer experiences.” Subscriber trends continued to improve this quarter. Consumer revenue generating units (“RGUs”) in the second quarter declined by just over 5,000, a significant improvement as compared to approximately 41,000 RGU losses in the second quarter of fiscal 2016. -

Shaw Business
Shaw Business OVERVIEW LOCATIONS Shaw Business is a division of Shaw Communications; a diversified communications 630 3 Ave SW, Calgary, AB T 2P 4L4, Canada and media company headquartered in Calgary, Alberta, Canada. T hink of Shaw Business as the Comcast or Spectrum of Canad N/A Canada KEY FEATURE AND DIFFERENTIATORS T he Shaw Business Client Services team works with you, at your location, to SERVICE OFFERINGS customize your business communications solutions. And if you are transitioning to Shaw Business, it's easy. TELECOM Voice 24/7/365 loca Shaw Business has a scalable and affordable phone solution to meet your customer’s needs. We offer Hosted Voice (SmartVoice), SIP (Session Initiated Protocol), PRI (Primary Rate Interface), and DATA Reduce operational costs and enhance efficiency and profits with secure and private network connections between all your business locations. Enjoy private and reliable network connections—completely s CLOUD Our hybrid cloud offerings allow you to save on expensive hardware, environmental controls and security upgrades without compromising on quality. By leveraging our capabilities to support your IT infr INTERNATIONAL Fibre footprint across Canada, coax footprint across Western Canada, plus fibre hubs at US carrier hotels. Shaw Business COLOCATION Our flexible and easily adaptable resources allow us to design solutions configured to fit your business needs, location and size – now and in the future. From single or multiple racks to private cage IDEAL CUSTOMER PROFILE UCAAS Our hosted voice solution, SmartVoice, is designed to easily mix and match plans Shaw Business offers a variety of Voice, Internet, Voice, and Data solutions so you can choose features that will improve your business productivity, and cater designed to meet the needs of any sized business and vertical.