Hierarchical Models and the Tuning of RWM Algorithms
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Unclassified NEA/RWM/RF(2004)6 RWMC Regulators' Forum (RWMC
Unclassified NEA/RWM/RF(2004)6 Organisation de Coopération et de Développement Economiques Organisation for Economic Co-operation and Development 30-Sep-2004 ___________________________________________________________________________________________ English - Or. English NUCLEAR ENERGY AGENCY RADIOACTIVE WASTE MANAGEMENT COMMITTEE Unclassified NEA/RWM/RF(2004)6 RWMC Regulators' Forum (RWMC-RF) REMOVAL OF REGULATORY CONTROLS FOR MATERIALS AND SITES National Regulatory Positions Issues with the removal of regulatory controls are very important on the agenda of the regulatory authorities dealing with radioactve waste managemnt (RWM). These issues arise prominently in decommissioning and in site remediation, and decisions can be very wide ranging having potentiallly important economic impacts and reaching outside the RWM area. The RWMC Regulators Forum started to address these issues by holding a topical discussion at its meeting in March 2003. Ths present document collates the national regulatory positions in the area of removal of regulatory controls. A summary of the national positions is also provided. The document is up to date to April 2004. English - Or. English JT00170359 Document complet disponible sur OLIS dans son format d'origine Complete document available on OLIS in its original format NEA/RWM/RF(2004)6 FOREWORD Issues with the removal of regulatory controls are very important on the agenda of the regulatory authorities dealing with radioactive waste management (RWM). These issues arise prominently in decommissioning and in site remediation, and decisions can be very wide ranging having potentially important economic impacts and reaching outside the RWM area. The relevant issues must be addressed and clearly understood by all stakeholders. There is a large interest in these issues outside the regulatory arena. -

The RWM Benefit Cost Analysis Compendium
The Road Weather Management Benefit Cost Analysis Compendium Quality Assurance Statement The Federal Highway Administration (FHWA) provides high-quality information to serve Government, industry, and the public in a manner that promotes public understanding. Standards and policies are used to ensure and maximize the quality, objectivity, utility, and integrity of its information. FHWA periodically reviews quality issues and adjusts its programs and processes to ensure continuous quality improvement. Notice This document is disseminated under the sponsorship of the Department of Transportation in the interest of information exchange. The United States Government assumes no liability for its contents or use thereof. The Road Weather Management Benefit Cost Analysis Compendium TECHNICAL REPORT DOCUMENTATION PAGE 1. Report No. 2. Government Accession No. 3. Recipient's Catalog No. FHWA-HOP-14-033 4. Title and Subtitle 5. Report Date Road Weather Management Benefit Cost Analysis Compendium August 2014 6. Performing Organization Code 7. Author(s) 8. Performing Organization Report No. Michael Lawrence, Paul Nguyen, Jonathan Skolnick, Jim Hunt, Roemer Alfelor N/A 9. Performing Organization Name and Address 10. Work Unit No. (TRAIS) Leidos 11251 Roger Bacon Drive Reston, Virginia 20190 11. Contract or Grant No. Jack Faucett Associates 4915 St. Elmo Ave, Suite 205 DTFH61-12-D-00050 Bethesda, Maryland 20814 12. Sponsoring Agency Name and Address 13. Type of Report and Period Covered U.S. Department of Transportation Federal Highway Administration Office of Freight Management and Operations 14. Sponsoring Agency Code 1200 New Jersey Avenue, SE Washington, DC 20590 HOP 15. Supplementary Notes Far right image on cover source: Idaho Transportation Department Bottom image on cover source: Paul Pisano, Federal Highway Administration 16. -

KHF 950/990 HF Communications Transceiver PILOT’S GUIDE and DIRECTORY of HF SERVICES
KHF 950/990 HF Communications Transceiver PILOT’S GUIDE AND DIRECTORY OF HF SERVICES A Table of Contents INTRODUCTION KHF 950/990 COMMUNICATIONS TRANSCEIVER . .I SECTION I CHARACTERISTICS OF HF SSB WITH ALE . .1-1 ACRONYMS AND DEFINITIONS . .1-1 REFERENCES . .1-1 HF SSB COMMUNICATIONS . .1-1 FREQUENCY . .1-2 SKYWAVE PROPAGATION . .1-3 WHY SINGLE SIDEBAND IS IMPORTANT . .1-9 AMPLITUDE MODULATION (AM) . .1-9 SINGLE SIDEBAND OPERATION . .1-10 SINGLE SIDEBAND (SSB) . .1-10 SUPPRESSED CARRIER VS. REDUCED CARRIER . .1-10 SIMPLEX & SEMI-DUPLEX OPERATION . .1-11 AUTOMATIC LINK ESTABLISHMENT (ALE) . .1-11 FUNCTIONS OF HF RADIO AUTOMATION . .1-11 ALE ASSURES BEST COMM LINK AUTOMATICALLY . .1-12 SECTION II KHF 950/990 SYSTEM DESCRIPTION. .2-1 KCU 1051 CONTROL DISPLAY UNIT . .2-1 KFS 594 CONTROL DISPLAY UNIT . .2-3 KCU 951 CONTROL DISPLAY UNIT . .2-5 KHF 950 REMOTE UNITS . .2-6 KAC 952 POWER AMPLIFIER/ANT COUPLER .2-6 KTR 953 RECEIVER/EXITER . .2-7 ADDITIONAL KHF 950 INSTALLATION OPTIONS .2-8 SINGLE KHF 950 SYSTEM CONFIGURATION .2-9 KHF 990 REMOTE UNITS . .2-10 KAC 992 PROBE/ANTENNA COUPLER . .2-10 KTR 993 RECEIVER/EXITER . .2-11 SINGLE KHF 990 SYSTEM CONFIGURATION . .2-12 Rev. 0 Dec/96 KHF 950/990 Pilots Guide Toc-1 Table of Contents SECTION III OPERATING THE KHF 950/990 . .3-1 KHF 950/990 GENERAL OPERATING INFORMATION . .3-1 PREFLIGHT INSPECTION . .3-1 ANTENNA TUNING . .3-2 FAULT INDICATION . .3-2 TUNING FAULTS . .3-3 KHF 950/990 CONTROLS-GENERAL . .3-3 KCU 1051 CONTROL DISPLAY UNIT OPERATION . -
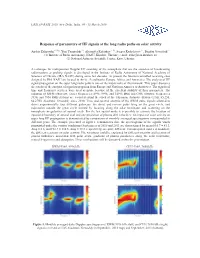
Response of Parameters of HF Signals at the Long Radio Paths on Solar Activity
URS I AP -RASC 2019, New Delhi, India, 09 - 15 March 2019 Response of parameters of HF signals at the long radio paths on solar activity Andriy Zalizovski (1, 2) *, Yuri Yampolski (1) , Alexander Koloskov (1, 2), Sergey Kashcheyev (1) , Bogdan Gavrylyik (1) (1) Institute of Radio Astronomy, NASU, Kharkiv, Ukraine; e-mail: [email protected] (2) National Antarctic Scientific Center, Kyiv, Ukraine A technique for multiposition Doppler HF sounding of the ionosphere that use the emission of broadcasting radio-stations as probing signals is developed in the Institute of Radio Astronomy of National Academy of Sciences of Ukraine (IRA NASU) during some last decades. At present the Internet-controlled receiving sites designed by IRA NASU are located in Arctic, Scandinavia, Europe, Africa, and Antarctica. The analysis of HF signal propagation on the super long radio paths is one of the major tasks of this network. This paper discusses the results of the analysis of signal propagation from Europe and Northern America to Antarctica. The signals of time and frequency services were used as probe because of the excellent stability of their parameters. The radiation of RWM (Moscow, carrier frequencies 4996, 9996, and 14996 kHz) and CHU (Ottawa, frequencies 3330, and 7850 kHz) stations are recorded round-the-clock at the Ukrainian Antarctic Station (UAS, 65.25S, 64.27W) Akademik Vernadsky since 2010. Time and spectral analysis of the RWM pulse signals allowed to detect experimentally four different pathways: the direct and reverse paths lying on the great circle, and trajectories outside the great circle formed by focusing along the solar terminator and scattering on the ionospheric irregularities of auroral ovals. -

STANDARD FREQUENCIES and TIME SIGNALS (Question ITU-R 106/7) (1992-1994-1995) Rec
Rec. ITU-R TF.768-2 1 SYSTEMS FOR DISSEMINATION AND COMPARISON RECOMMENDATION ITU-R TF.768-2 STANDARD FREQUENCIES AND TIME SIGNALS (Question ITU-R 106/7) (1992-1994-1995) Rec. ITU-R TF.768-2 The ITU Radiocommunication Assembly, considering a) the continuing need in all parts of the world for readily available standard frequency and time reference signals that are internationally coordinated; b) the advantages offered by radio broadcasts of standard time and frequency signals in terms of wide coverage, ease and reliability of reception, achievable level of accuracy as received, and the wide availability of relatively inexpensive receiving equipment; c) that Article 33 of the Radio Regulations (RR) is considering the coordination of the establishment and operation of services of standard-frequency and time-signal dissemination on a worldwide basis; d) that a number of stations are now regularly emitting standard frequencies and time signals in the bands allocated by this Conference and that additional stations provide similar services using other frequency bands; e) that these services operate in accordance with Recommendation ITU-R TF.460 which establishes the internationally coordinated UTC time system; f) that other broadcasts exist which, although designed primarily for other functions such as navigation or communications, emit highly stabilized carrier frequencies and/or precise time signals that can be very useful in time and frequency applications, recommends 1 that, for applications requiring stable and accurate time and frequency reference signals that are traceable to the internationally coordinated UTC system, serious consideration be given to the use of one or more of the broadcast services listed and described in Annex 1; 2 that administrations responsible for the various broadcast services included in Annex 2 make every effort to update the information given whenever changes occur. -

Vialitehd-EDFA-Datasheet-HRA-X-DS-1
www.vialite.com +44 (0)1793 784389 [email protected] +1 (855) 4-VIALITE [email protected] ® ViaLiteHD – EDFA Erbium-Doped Fiber Amplifiers (EDFA) Next generation variable gain EDFA Single or multi-channel EDFA available 8 dB to 36 dB gain variants SNMP and RS232 control Fast start-up time EDFA AGC (Automatic gain control) Bi directional Option Standard 5-year warranty The ViaLiteHD Eribium Doped Fiber Amplifier (EDFA) is available in either a single channel or multi-channel format depending on where it is utilized in the system. The EDFAs have low noise figures and variable gain ensuring the optimization of link noise figure and performance. They are available as part of a Ka-Band diversity antenna system, ultra-long distance system (up to 600 km) or as a stand-alone product. Options Low noise figure SNMP and RS232 control Fixed gain, auto power control, auto gain control software selectable Low switching time 8 dB, 18 dB, 20 dB, 23 dB, 24 dB, 33 dB or 36 dB gain (other gain variants available) Single channel or multiple channel Applications Formats 1U Chassis Ka-Band diversity rain fade application Fixed satcom earth stations and teleports Related Products Gateway reduction within a satellite footprint 50 km 1550 nm L-Band HTS Government installations 50 Ohm DWDM L-Band HTS Remote monitoring stations >50 km systems Remote oil and gas locations DWDM Multiplexers Remote wind farm locations Optical Switches Optical Delay Lines Popular products HRA-3-0B-8T-AF-D001 – ViaLiteHD EDFA, 24 dB Optical Amplifier, single channel HRA-4-0B-8T-AB-D008 -

Dispersion Compensation Module
www.vialite.com +44 (0)1793 784389 [email protected] +1 (855) 4-VIALITE [email protected] ViaLiteHD – Dispersion Compensation Module Dispersion Compensation Module (DCM) 1U Rack chassis Standard lengths and customer specific Compatible with any RF frequency SC/APC as standard DCM Standard 5-year warranty A DCM/Dispersion Compensation Fiber (DCF) provides fixed chromatic dispersion compensation for diverse and disaster recovery DWDM networks. ViaLiteHD DCMs are purely passive modules based on the ITU G.652 standard to provide negative dispersion for DWDM transmission systems, increasing transmission range and decreasing BER of optical links. It can be used to address dispersion on standard single mode optical fiber (SMF) across the entire C-Band and L-Band range. The DCMs are available as part of ViaLite’s Ka-Band diversity antenna system. Each DCM can be supplied in 5 km increments, supporting medium to long distance fiber optic systems ranging from 30 km to 600 km. Advantages Formats Low Insertion loss 1U Chassis 19” rack mountable Passive device Related Products Low polarization mode dispersion DWDM Mux/De-Mux Excellent performance price ratio DWDM EDFA’s and Boosters Signal performance improvements Delay Lines L-Band HTS 700-2450 MHz Applications Fixed satcom earth stations and teleports Ka-Band diversity systems L-Band long distance links G.652 100% C-Band compensation fiber Long distance DWDM optimization CATV Systems ViaLite System Designer For complex designs where multiple DWDM products are required the System Designer tool is essential for predicting and validating performance results. The software uses a drag and drop approach from a pallet of products. -

Marking Time Successful Navigating Requires Temporal Accuracy
HIGH SEAS EMBARKING ON MARITIME LISTENING James Hay Marking Time Successful Navigating Requires Temporal Accuracy illust how do ships find their way Table 1 isalist across the ocean? Navigational TABLE 1: Active Time Signal Stations of some of the methods and aids have evolved stations which Call Lenora Location Mode dramatically since the days of the Ereq_kfz are active. Polynesian navigators and Christo- 50 OMA Prague CW Most ofthese pher Columbus, centuries later. It has RTZ Irkutsk CW time signal 60 MSF Rugby CW stations are not often been said that Columbus find- WWVB Fort Collins CW ing America was an amazing feat. 75 HBG Nyon CW on 24 hours Seamen of that time used a form of 77.5 DCF 77 Mainflingen CW per day, but 2500 BPM Xi'an CW celestial navigation and instruments HLA Taejon AM/SSB time signals which pale beside the modern chro- JJY Tokyo AM/SSB will usually be nometer and sextant. What was truly RCH Tashkent CW found on the hour, or at intervals of VHG Sydney SSB 4 6 Midnight, 0600, amazing about Columbus was not WWV Fort Collins AM/SSB usually or hours. only that he found America, but that WWVH Kihai AM/SSB noon and 1800 local or universal time he managed to find it the second time 3330 CHU Ottawa AM/SSB are common. Don't be deterred by the 3810 HD2 lOA Guayaquil AM/SSB and returned to Europe to tell of it. 4286 VWC Calcutta CW strong presence of W W VH and WWV One of the things which has been 4996 RWM Moscow CW on 2.5, 5, 10, and 15 MHz. -

CONTRINEX Low-Frequency Radio Frequency Identification Systems
Low-FRequency technoLogy Low frequency hIghLIghts: High frequency ü All-metal components for aggressive operating environments ü Embeddable transponders ü Transponders can be written to and read through metal ü Memory of transponders: 120 words, 16 bit each ü Various transponder memory protection possibilities ü Interface possibilities with bus RS485, PROFIBUS, DeviceNet and EtherNet/IP ü USB adaptor Buy: www.ValinOnline.com | Phone 844-385-3099 | Email: [email protected] Low-frequency max. ReaD/wRIte DIstances technoLogy Read/write module Read/write module Read/write module Read/write module RLS-1180-000 / RLS-1300-000 / Transponders RLS-1181-000 RLS-1301-000 RLS-1182-001 RLS 1302-001 RTP-0201-000 13 mm 20 mm 18 mm 25 mm RTP-0301-000 17 mm 26 mm 23 mm 33 mm RTP-0501-000 20 mm 33 mm 28 mm 42 mm RTM-0100-000 / RTL-0102-001 8 mm 13 mm 9 mm 17 mm RTM-0160-000 / RTL-0162-001 11 mm 17 mm 12 mm 23 mm RTM-0260-000 / RTL-0262-001 13 mm 20 mm 16 mm 30 mm RTM-2160-000 / RTL-2162-001 7 mm 11 mm --- 16 mm RTM-2300-000 / RTL-2302-001 9 mm 13 mm 10 mm 20 mm RTF-1300-000 / RTL-1302-001 11 mm 19 mm 15 mm 28 mm Buy: www.ValinOnline.com | Phone 844-385-3099 | Email: [email protected] ® Low-frequency conIDent RFID system technoLogy As a general rule, a Contrinex radio frequency identification (ConIdent®) system comprises: − a transponder consisting of an integrated circuit connected to an antenna, − a read/write module, − an interface device, which establishes the connection between a field bus and several read/write modules, − software: configuration and test, programming libraries. -

Nbs Technical Note 674 National Bureau of Standards
NBS TECHNICAL NOTE 674 NATIONAL BUREAU OF STANDARDS The National Bureau of Standards' was established by an act of Congress March 3, ,1901. The Bureau's overall goal is to strengthen and advance the Nation's science and technology and facilitate their effective application for public benefit. To this end, the Bureau conducts research and provides: (1) a basis for the Nation's physical measurement system, (2) scientific and technological services for industry and government, (3) a technical basis for equity in trade, and (4) technical services to promote public safety. The Bureau consists of the Institute for Basic Standards, the Institute for Materials Research, the Institute for Applied Technology, the Institute for Computer Sciences and Technology, and the Office for Information Programs. THE INSTITUTE FOR BASIC STANDARDS provides the central basis within the United States of a complete and consistent system of physical measurement; coordinates that system with measurement systems of other nations; and furnishes essential services leading to accurate and uniform physical measurements throughout the Nation's scientific community, industry, and commerce. The Institute consists of the Office of Measurement Services, the Office of Radiation Measurement and the following Center and divisions: Applied Mathematics - Electricity - Mechanics - Heat - Optical Physics - Center for Radiation Research: Nuclear Sciences; Applied Radiation - Laboratory Astrophysics * - Cryogenics ' - Electromagnetics - Time and Frequency *. THE INSTITUTE FOR MATERIALS RESEARCH conducts materials research leading to improved methods of measurement, standards, and data on the properties of well-characterized materials needed by industry, commerce, educational institutions, and Government; provides advisory and research services to other Government agencies; and develops, produces, and distributes standard reference materials. -

RWM Business Plan 2020-23
Annex to RWM Annual Review Working together to protect the future Business Plan Doing 2020-23 The Right Thing 1 Annual Report and Accounts 2018-19 Contents Contents Cia denimin ihiliae praes nonsequatus reptatibus, natur, aliquis quate peribus The Plan .................................................................................................................5 aperrup tatioreribus dolorum dem fugitates dendele ssimus. Key Priority 1: Deliver Community Partnerships Ci to ipsam, sequunt vid ea eum rerum for a GDF and prepare for site selection ............................................6 voluptate quis assum, cum is niatiatur restinitecus dolor magnatenimi, explab ipis The GDF Development Phase ...........................................................................8 aborum a que net ex experciae peliquas et accum quo eum fugiatis arum, asperuptati Key Priority 2: Deliver waste management solutions nimusda num, aperiat. to support the UK nuclear estate ...........................................................10 At aut esequi quam quiatiam venis ut etur si blamusa perfernatur archiliquide alique Key Priority 3: Transform our organisation for optaturitiae quunt vidipsant. safe and effective delivery .........................................................................13 Hendaeperis alitas simus eariberum de dest estiusam ipsaperuptat dolorep eroreptae How are we going to deliver? ............................................................................13 ne nullabo. Itassit volorest re porerehenis et alique re, te sequis -

Pupil Premium Report and Strategy Statement
Hogarth Academy Pupil Premium Report and Strategy Statement In Hogarth Academy we endeavour to fulfil the Pupil Premium Policy set out by the L.E.A.D Academy Trust by deploying the following Trust strategies to diminish the difference in attainment for pupils in receipt of the Pupil Premium funding. • clear, responsive leadership • having a whole-school ethos of attainment for all • addressing behaviours for learning and conduct behaviours that prevent pupils form learning • monitoring and addressing low attendance • facilitating high quality teaching for all through continued professional development of staff. • meeting individual learning needs including those pupils who are the most-able and seemingly need no support • deploying staff effectively, both teaching and support staff • using pupil progress data to inform the planning of interventions and provision. Each Academy reviews the barriers and outcomes for the pupils in receipt of Pupil Premium to understand the strategies that they to use to raise attainment. Each Academy explains their rationale for choosing the strategies and provides a cost breakdown. If you wish this statement to be explained, then please ask to speak with Pupil Premium Leader via the main office. If you wish to find out more about the DfE policy for Pupil Premium then follow this link: https://www.gov.uk/guidance/pupil-premium-information-for-schools-and-alternative-provision-settings 1 Hogarth Academy 1. Summary information for 2019-20 Academy Hogarth Academy Pupil Premium Ms S Lee Leader Academic Year 2019/20