Performance Analysis of the Preemption Mechanism in Tsn
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Alternatív Valóság Kovács Ákos Hálózatok 10+ Tb/S 6,4 Tb/S 1,6 Tb/S 1 Tb/S
Számítógép hálózatok Alternatív valóság Kovács Ákos Hálózatok 10+ Tb/s 6,4 Tb/s 1,6 Tb/s 1 Tb/s 800 Gb/s 400 Gb/s 2017? • A jelen és a jövő 200 Gb/s 2018-2020? • Egyre nagyobb informatikai átviteli 50 Gb/s sebesség kell, jó minőségben 100 Gb/s 2018-2020? 2010 • Switchek minden hálózat alapjai 25 Gb/s 40 Gb/s 2016? 2010 5 Gb/s 10 Gb/s 2016? 2002 2,5 Gb/s 2016? 1 Gb/s 1998 100 Mb/s 1995 10 Mb/s 1983 Switchek • Switch-ekről általában • HUB, Bridge, L2 Switch, L3 Switch, Router • 10/100/1000/10GE switch-ek 2,5GE, 5GE (multiGIG switchek) • Néhány fontosabb működési paraméter • Hátlap (backplane) sávszélesség (Gbps) • Csomag továbbítási sebesség (packet forwarding rate, Mpps) • Switch-elési módok (switching methods, forwarding modes) • Fast Forward (cut-through, fragment-free) • Store-and-Forward • Adaptive (intelligent) L2 Switchek • L2 kommunikációra • Csak a MAC cím alapján (lokális hálózatokhoz LAN) MAC cím (48 bit) 24 bit 24 bit Organizationally Unique Identifier A gyártó osztja ki (OUI) L2 Switchek • A switch nem kérdezi meg a MAC címeket, csak megjegyzi • Ha nem tudja merre kellene menni akkor jön a flood (minden portjára elküldi kivéve amin kapta) • Ha erre válaszolnak, akkor azt MAC-PORT párost megjegyzi L2 Switchek döntési lánca • Layer 2 • CAM Content Addressable memory MAC címek • TCAM (ACL, QoS táblák) 3 értéke lehet, 0,1,X ahol x a „don’t care” bit • Kérdések melyekre válaszolni kell: • Merre továbbítsam a csomagot? • Továbbítsam a csomagot? • Milyen QoS értékekkel továbbítsam a csomagot? • InLine sebesség (ASIC) L3 switchek • Más néven Multi-layer switchek • További döntési lehetőségek a magasabb rétegek alapján mint pl. -

Networking Tutorial
EDUCATION Ethernet Technology Allen Light, Broadcom Corp. SNIA Legal Notice EDUCATION • The material contained in this tutorial is copyrighted by the SNIA. • Member companies and individuals may use this material in presentations and literature under the following conditions: – Any slide or slides used must be reproduced without modification – The SNIA must be acknowledged as source of any material used in the body of any document containing material from these presentations. • This presentation is a project of the SNIA Education Committee. SNIA© 2007 Storage Networking Industry Association. All Rights Reserved. Ethernet Technology 2 Abstract EDUCATION Ethernet, the standard local area network (LAN) access method. A specification for "LAN," "LAN connection" or "network card" automatically implies Ethernet without saying so. This session provides an overview of Ethernet technology, with an emphasis on the evolution of the standards from the original implementation of Ethernet on coax cable to the latest 10Gb Ethernet implementations. SNIA© 2007 Storage Networking Industry Association. All Rights Reserved. Ethernet Technology 3 Agenda EDUCATION • The Original Standard • Evolution of Ethernet • Elements of Ethernet • The Frame / Addressing • Media Access Controller • Physical Media SNIA© 2007 Storage Networking Industry Association. All Rights Reserved. Ethernet Technology 4 'net-"w&rk EDUCATION • A system of computers, terminals, and databases connected by communications lines Local Area Network (LAN) • A network of personal computers in a small area (like an office) that are linked by cable, can communicate directly with other devices in the network and can share resources (from Merriam Webster) • So why is this guy talking about a LAN technology at a storage networking conference? SNIA© 2007 Storage Networking Industry Association. -

IEEE Std 802.3-2005, Section
IEEE Standard for Information technology— Telecommunications and information exchange between systems— Local and metropolitan area networks— Specific requirements Part 3: Carrier sense multiple access with collision detection (CSMA/CD) access method and physical layer specifications IEEE Computer Society Sponsored by the LAN/MAN Standards Committee I E E E IEEE Std 802.3™-2005 3 Park Avenue (Revision of IEEE Std 802.3-2002 New York, NY 10016-5997, USA including all approved amendments) 9 December 2005 IEEE Std 802.3™-2005 (Revision of IEEE Std 802.3-2002) IEEE Standard for Information technology— Telecommunications and information exchange between systems— Local and metropolitan area networks— Specific requirements Part 3: Carrier Sense Multiple Access with Collision Detection (CSMA/CD) Access Method and Physical Layer Specifications LAN/MAN Standards Committee of the IEEE Computer Society Approved 9 June 2005 IEEE-SA Standards Board Abstract: Ethernet local area network operation is specified for selected speeds of operation from 1 Mb/s to 10 Gb/s using a common media access control (MAC) specification, management infor- mation base (MIB), and capability for Link Aggregation of multiple physical links into a single logi- cal link. The Carrier Sense Multiple Access with Collision Detection (CSMA/CD) MAC protocol specifies shared medium (half duplex) operation, as well as full duplex operation. Speed specific Media Independent Interfaces (MIIs) allow use of selected physical layer (PHY) interfaces for operation over coxial, twisted pair or fiber optic cables. System considerations for multisegment shared access networks describe the use of Repeaters which are defined for operational speeds up to 1000 Mb/s. -
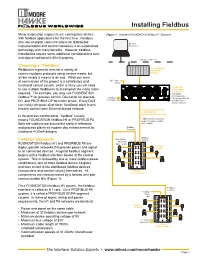
Installing Fieldbus Installing Fieldbus
Installing Fieldbus Installing Fieldbus Many automation engineers are coming face-to-face Figure 1. Standard FOUNDATION fi eldbus™ Segment. with fi eldbus applications for the fi rst time. Fieldbus (the use of digital communications for distributed Operator instrumentation and control networks) is an established Workstation technology with many benefi ts. However, fi eldbus installations require some additional considerations over and above traditional 4-20mA projects. High Speed Ethernet Choosing a “Fieldbus” Control System Fieldbus is a generic term for a variety of with H1/PA communications protocols using various media, but Interface all are simply a means to an end. What you want DC Power at commission of the project is a satisfactory and Input functional control system, and it is likely you will need Fieldbus DC to use multiple fi eldbuses to accomplish the many tasks Power Supply (Conditioner) required. For example, you may use FOUNDATION 350-500mA (Not Required for fi eldbus™ for process control, DeviceNet for discrete Fieldbus T PA Systems; May Be I/O, and PROFIBUS DP for motor drives. Every DCS Terminator with the Control System Interface) can easily integrate all of these functional plant buses into the control room Ethernet-based network. FOUNDATION fieldbus H1 or PROFIBUS PA In the process control world, “fi eldbus” usually Network (Twisted Wire Pair) 1,900m (6,233 ft) Maximum means FOUNDATION fi eldbus H1 or PROFIBUS PA. Segment Length Including Both are widely used around the world in refi neries Spur Lengths and process plants as modern day enhancements to Fieldbus Trunk Out traditional 4-20mA designs. -

Ethernet PHY Information Model
Ethernet PHY Information Model Version 1.0.0-2 7th of March 2019 ONF TR‑541 Ethernet PHY Information Model Version 1.0.0-12 ONF TR‑541 FebruaryMarch 2019 ONF Document Type: Technical Recommendation ONF Document Name: Ethernet PHY Information Model Version 1.0 Disclaimer THIS SPECIFICATION IS PROVIDED "AS IS" WITH NO WARRANTIES WHATSOEVER, INCLUDING ANY WARRANTY OF MERCHANTABILITY, NONINFRINGEMENT, FITNESS FOR ANY PARTICULAR PURPOSE, OR ANY WARRANTY OTHERW ISE ARISING OUT OF ANY PROPOSAL, SPECIFICATION OR SAMPLE. Any marks and brands contained herein are the property of their respective owners. Open Networking Foundation 1000 El Camino Real, Suite 100, Menlo Park, CA 94025 www.opennetworking.org ©2017 Open Networking Foundation. All rights reserved. Open Networking Foundation, the ONF symbol, and OpenFlow are registered trademarks of the Open Networking Foundation, in the United States and/or in other countries. All other brands, products, or service names are or may be trademarks or service marks of, and are used to identify, products or services of their respective owners. Page 2 of 64 © Open Networking Foundation Ethernet PHY Information Model Version 1.0.0-12 ONF TR‑541 FebruaryMarch 2019 Table of Contents Disclaimer .................................................................................................................................................... 2 Open Networking Foundation .................................................................................................................... 2 Table of Contents ....................................................................................................................................... -

Foundation Fieldbus Overview
FOUNDATIONTM Fieldbus Overview Foundation Fieldbus Overview January 2014 370729D-01 Support Worldwide Technical Support and Product Information ni.com Worldwide Offices Visit ni.com/niglobal to access the branch office Web sites, which provide up-to-date contact information, support phone numbers, email addresses, and current events. National Instruments Corporate Headquarters 11500 North Mopac Expressway Austin, Texas 78759-3504 USA Tel: 512 683 0100 For further support information, refer to the Technical Support and Professional Services appendix. To comment on National Instruments documentation, refer to the National Instruments website at ni.com/info and enter the Info Code feedback. © 2003–2014 National Instruments. All rights reserved. Legal Information Warranty NI devices are warranted against defects in materials and workmanship for a period of one year from the invoice date, as evidenced by receipts or other documentation. National Instruments will, at its option, repair or replace equipment that proves to be defective during the warranty period. This warranty includes parts and labor. The media on which you receive National Instruments software are warranted not to fail to execute programming instructions, due to defects in materials and workmanship, for a period of 90 days from the invoice date, as evidenced by receipts or other documentation. National Instruments will, at its option, repair or replace software media that do not execute programming instructions if National Instruments receives notice of such defects during the warranty period. National Instruments does not warrant that the operation of the software shall be uninterrupted or error free. A Return Material Authorization (RMA) number must be obtained from the factory and clearly marked on the outside of the package before any equipment will be accepted for warranty work. -

IEEE Std 802.3™-2012 New York, NY 10016-5997 (Revision of USA IEEE Std 802.3-2008)
IEEE Standard for Ethernet IEEE Computer Society Sponsored by the LAN/MAN Standards Committee IEEE 3 Park Avenue IEEE Std 802.3™-2012 New York, NY 10016-5997 (Revision of USA IEEE Std 802.3-2008) 28 December 2012 IEEE Std 802.3™-2012 (Revision of IEEE Std 802.3-2008) IEEE Standard for Ethernet Sponsor LAN/MAN Standards Committee of the IEEE Computer Society Approved 30 August 2012 IEEE-SA Standard Board Abstract: Ethernet local area network operation is specified for selected speeds of operation from 1 Mb/s to 100 Gb/s using a common media access control (MAC) specification and management information base (MIB). The Carrier Sense Multiple Access with Collision Detection (CSMA/CD) MAC protocol specifies shared medium (half duplex) operation, as well as full duplex operation. Speed specific Media Independent Interfaces (MIIs) allow use of selected Physical Layer devices (PHY) for operation over coaxial, twisted-pair or fiber optic cables. System considerations for multisegment shared access networks describe the use of Repeaters that are defined for operational speeds up to 1000 Mb/s. Local Area Network (LAN) operation is supported at all speeds. Other specified capabilities include various PHY types for access networks, PHYs suitable for metropolitan area network applications, and the provision of power over selected twisted-pair PHY types. Keywords: 10BASE; 100BASE; 1000BASE; 10GBASE; 40GBASE; 100GBASE; 10 Gigabit Ethernet; 40 Gigabit Ethernet; 100 Gigabit Ethernet; attachment unit interface; AUI; Auto Negotiation; Backplane Ethernet; data processing; DTE Power via the MDI; EPON; Ethernet; Ethernet in the First Mile; Ethernet passive optical network; Fast Ethernet; Gigabit Ethernet; GMII; information exchange; IEEE 802.3; local area network; management; medium dependent interface; media independent interface; MDI; MIB; MII; PHY; physical coding sublayer; Physical Layer; physical medium attachment; PMA; Power over Ethernet; repeater; type field; VLAN TAG; XGMII The Institute of Electrical and Electronics Engineers, Inc. -

FOUNDATION Fieldbus Design Considerations Reference Manual
Reference Manual PlantPAx Process Automation System: FOUNDATION Fieldbus Design Considerations Catalog Numbers 1757-FFLDx, 1757-FFLDCx Important User Information Solid-state equipment has operational characteristics differing from those of electromechanical equipment. Safety Guidelines for the Application, Installation and Maintenance of Solid State Controls (publication SGI-1.1 available from your local Rockwell Automation sales office or online at http://www.rockwellautomation.com/literature/) describes some important differences between solid-state equipment and hard-wired electromechanical devices. Because of this difference, and also because of the wide variety of uses for solid-state equipment, all persons responsible for applying this equipment must satisfy themselves that each intended application of this equipment is acceptable. In no event will Rockwell Automation, Inc. be responsible or liable for indirect or consequential damages resulting from the use or application of this equipment. The examples and diagrams in this manual are included solely for illustrative purposes. Because of the many variables and requirements associated with any particular installation, Rockwell Automation, Inc. cannot assume responsibility or liability for actual use based on the examples and diagrams. No patent liability is assumed by Rockwell Automation, Inc. with respect to use of information, circuits, equipment, or software described in this manual. Reproduction of the contents of this manual, in whole or in part, without written permission of Rockwell Automation, Inc., is prohibited. Throughout this manual, when necessary, we use notes to make you aware of safety considerations. WARNING: Identifies information about practices or circumstances that can cause an explosion in a hazardous environment, which may lead to personal injury or death, property damage, or economic loss. -

Industrial Ethernet
Industrial Ethernet Main Catalog 2008 Some errors can be really expensive. What good are the greatest technical inventions if you are going to save on the smallest details later? That man today is capable of great technical nowadays to ensure the greatest possible safety development is a sufficiently proven fact. Regard- and reliability for even the smallest system com- less of whether in production, process and traffic ponents. control technology or in building automation: from the packing industry and logistics through From the product quality through engineering conveyor and robot technology, assembly machines and the associated service. Hirschmann™ offers a and machine tools, presses and punching machines comprehensive package: with a high degree of right up to machine and system control. intelligence, they not only set the latest techni- cal standards but, with their high flexibility, When it’s a question of reliability, operating safe- ensure individual and absolutely reliable solutions ty and availability, the slightest errors count. And at the heart of the automation – in computer these can be very expensive in the worst case. and measuring technology. This minimizes risks Because, especially in economically difficult times, in the system and a high system availability is a trouble-free automation contributes considerably built in from the start. to productivity and competitiveness – and protects jobs in the long term. Safety at the press of button for us means leaving nothing to chance. Therefore every Hirschmann™ Therefore it is becoming increasingly important switch is rigorously tested before leaving the factory. 2 www.hirschmann.com After all, constantly rising transmission speed Switches from Hirschmann™ will certainly increase In this modern industrial age, with high clock frequencies demand appropriate the availability of your networks and guarantee one can no longer afford failures. -

Foundation Fieldbus Physical Medium, Cabling and Installation
smarwww.smar.com Specifications and information are subject to change without notice. Up-to-date address information is available on our website. web: www.smar.com/contactus.asp Introduction INTRODUCTION FOUNDATION™ fieldbus (FF) is an open architecture to integrate information, whose main objective is to interconnect control devices and industrial automation, distributing the control functions for the network and supplying information to all the layers of the system. The FOUNDATION™ fieldbus technology substitutes with advantages the 4-20mA + HART traditional, technology making possible the bi-directional communication among the devices in a more efficient way. This technology is much more than a protocol of digital communication or a local network to field instruments. It includes several technologies, such as distributed processing, advanced diagnosis and redundancy. A FOUNDATION™ fieldbus system is heterogeneous and distributed, composed by field devices, configuration and supervision software, communication interfaces, power supply and by its own physical network that interconnects them. One of the functions of the field devices is to execute the user application of control and supervision distributed by the network. This is the big difference between FOUNDATION™ fieldbus and other technologies that depend on a central controller to execute the algorithms. Compared to other systems, FOUNDATION™ fieldbus allows the access to many variables, not only related to the process, but also diagnostics of sensor and actuator, electronic components, -

Smart Instruments, Fieldbus, Ethernet and Industrial Wireless
SMART INSTRUMENTS, FIELDBUS, ETHERNET AND INDUSTRIAL WIRELESS www.eit.edu.au www.eit.edu.au Steve Mackay • Dean of Engineering • Worked for 30 years in Industrial Automation • 30 years experience in mining, oil and gas, electrical and manufacturing industries www.eit.edu.au RH Start recording! www.eit.edu.au The Nuts and Bolts of smart instrument standards www.eit.edu.au Some Additional Docs • Ethernet vs Fieldbus: the Right Network for the right application (Control Design 2016) • Guide to Implementing Foundation H1 Devices (Foundation Fieldbus) • Fieldbus Myths Busted (Foundation Fieldbus) www.eit.edu.au Digital Technologies- Summary Bus Ease Field Acceptance Knowledge Price Intelligence Base AS-I Devicenet Profibus DP Profibus PA FF HART Ethernet (Slide compliments of Emerson) www.eit.edu.au Generic Fieldbus Advantages: Let’s Take Off! • Wiring savings • Hardware savings - fewer devices (instruments barriers and I/O) • Documentation savings - Simpler layout and drawings • Reduced Engineering costs • footprint savings • Multi-variable field devices • Interoperability and freedom of choice • Reduced Commissioning and startup costs • Reduced downtime • Integrity improved • DCS future capacity savings www.eit.edu.au “Footprint” Space Savings Before- 256 I/O Fieldbus -4000 I/O (Slide Compliments of Emerson & Jim Russell) www.eit.edu.au Which fieldbus to Select? There is ONE RIGHT fieldbus for YOU Engineer must decide based on: Technical Profile, budget, NPV including LONG TERM COST OF OWNERSHIP Business Requirements DISCRETE - Bottling plant would be mainly discrete-most effective solution ASi- Same may be the case for building automation DISCRETE+CONTINUOUS-Motor Vehicle Manufacturing Plant or Electrical Motor Control Centre- Profibus DP CONTINUOUS PROCESS PLANT - Hybrid approach likely- MCC (Profibus DP), PLCs (Modbus) and CPP Foundation fieldbus or Profibus PA. -
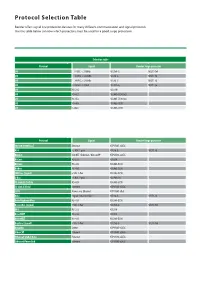
Protocol Selection Table
Protocol Selection Table Bender offers signal line protection devices for many different communication and signal protocols. Use the table below to know which protectors must be used for a good surge protection. Selection table Protocol Signal Bender Surge protector I/O ± 5 VDC, < 250kHz NSL7v5-G NSLT1-7v5 I/O ± 12 VDC, < 250kHz NSL18-G NSLT1-18 I/O ± 24 VDC, < 250kHz NSL36-G NSLT1-36 I/O 0-20mA / 4-20mA NSL420-G NSLT1-36 I/O RS-232 NSL-DH I/O RS-422 NSL485-EC90 (x2) I/O RS-452 NSL485-EC90 (x2) I/O RS-485 NSL485-EC90 I/O 1-Wire NSL485-EC90 Protocol Signal Bender Surge protector 10/100/1000BaseT Ethernet NTP-RJ45-xCAT6 AS-i 32 VDC 1-pair NSL36-G NSLT1-36 BACnet ARCNET / Ethernet / BACnet/IP NTP-RJ45-xCAT6 BACnet RS-232 NSL-DH BACnet RS-485 NSL485-EC90 BitBus RS-485 NSL485-EC90 CAN Bus (Signal) 5 VDC 1-Pair NSL485-EC90 C-Bus 36 VDC 1-pair NSSP6A-38 CC-Link/LT/Safety RS-485 NSL485-EC90 CC-Link IE Field Ethernet NTP-RJ45-xCAT6 CCTV Power over Ethernet NTP-RJ45-xPoE DALI Digital Serial Interface NSL36-G NSLT1-36 Data Highway/Plus RS-485 NSL485-EC90 DeviceNet (Signal) 5 VDC 1-Pair NSL7v5-G NSLT1-7v5 DF1 RS-232 NSL-DH DirectNET RS-232 NSL-DH DirectNET RS-485 NSL485-EC90 Dupline (Signal) 5 VDC 1-Pair NSL7v5-G NSLT1-7v5 Dynalite DyNet NTP-RJ45-xCAT6 EtherCAT Ethernet NTP-RJ45-xCAT6 Ethernet Global Data Ethernet NTP-RJ45-xCAT6 Ethernet Powerlink Ethernet NTP-RJ45-xCAT6 Protocol Signal Bender Surge protector FIP Bus RS-485 NSL485-EC90 FINS Ethernet NTP-RJ45-xCAT6 FINS RS-232 NSL-DH FINS DeviceNet (Signal) NSL7v5-G NSLT1-7v5 FOUNDATION Fieldbus H1