Deploying ESSO-LM with the Windows Authenticator Version 2 Release 11.1.1.2.0 E20410-01
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Security Target
Acronis SCS Acronis Cyber Backup 12.5 SCS Hardened Edition Server v12.5 Security Target Document Version: 0.14 Prepared for: Prepared by: Acronis SCS Corsec Security, Inc. 6370 E. Thomas Road, Suite 250 13921 Park Center Road, Suite 460 Scottsdale, AZ 85251 Herndon, VA 20171 United States of America United States of America Phone: +1 781 782 9000 Phone: +1 703 267 6050 www.acronisscs.com www.corsec.com Security Target, Version 0.14 August 19, 2020 Table of Contents 1. Introduction .......................................................................................................................................................4 1.1 Purpose .....................................................................................................................................................4 1.2 Security Target and TOE References .........................................................................................................4 1.3 Product Overview ......................................................................................................................................5 1.3.1 Product Components........................................................................................................................5 1.4 TOE Overview ............................................................................................................................................6 1.4.1 TOE Environment..............................................................................................................................7 1.5 -

Microsoft Windows Common Criteria Evaluation Security Target
Microsoft Common Criteria Security Target Microsoft Windows Common Criteria Evaluation Microsoft Windows 10 version 1809 (October 2018 Update) Microsoft Windows Server 2019 (October 2018 Update) Security Target Document Information Version Number 0.05 Updated On June 18, 2019 Microsoft © 2019 Page 1 of 126 Microsoft Common Criteria Security Target Version History Version Date Summary of changes 0.01 June 27, 2018 Initial draft 0.02 December 21, 2018 Updates from security target evaluation 0.03 February 21, 2019 Updates from evaluation 0.04 May 6, 2019 Updates from GPOS PP v4.2.1 0.05 June 18, 2019 Public version Microsoft © 2019 Page 2 of 126 Microsoft Common Criteria Security Target This is a preliminary document and may be changed substantially prior to final commercial release of the software described herein. The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs- NonCommercial License (which allows redistribution of the work). To view a copy of this license, visit http://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. -

Microsoft Windows Vista and Windows Server 2008 EAL1 Security Target
Microsoft Windows Vista and Windows Server 2008 EAL1 Security Target Version 1.0 August 14, 2008 Prepared For: Microsoft Corporation Corporate Headquarters One Microsoft Way Redmond, WA 98052-6399 Prepared By: Science Applications International Corporation Common Criteria Testing Laboratory 7125 Gateway Drive Columbia, MD 21046-2554 Version 1.0, 8/14/2008 This is a preliminary document and may be changed substantially prior to final commercial release of the software described herein. The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial License (which allows redistribution of the work). To view a copy of this license, visit http://creativecommons.org/licenses/by-nd- nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. -

Ways to a Better Password Management
St at e of IT Changes Survey Result s + Infographic Tips for a Bet t er Passw ord Securit y Policy Dat a Governance: The Key t o Com pliance Basic Rules How -t o: Ways t o a Bet t er Det ect ing Passw ord Changes in Act ive oPf aWsisnwdoowrds Server Direct ory SMecaunriatygem ent Contents Nine St eps t o a Bet t er Passw ord Managem ent 3 by Richard Muniz Why You Need t o Ensure Adm inist rat ors 5 Change Passw ords Regularly by Orin Thomas How t o St ore and Ret rieve Passw ords Securely 7 w it h Pow erShell by Adam Bertram 3 Ways t o Prot ect t he Keys t o Your Kingdom - 11 Dom ain Adm inist rat or Credent ials by Russell Smith June 2015 SysAdmin Magazine St at e of IT Changes Survey 2015: 13 Docum ent ing and Audit ing Dat a Governanm e: The Key t o Com pliance 16 by Deb Shinder Internet Usage Policy against Inappropriate 18 Content by Richard Muniz How to Detect Password Changes 20 in Active Directory June 2015 SysAdmin Magazine Nine Steps to a Better Passw ord Managem ent by Richard Muniz 20+ years in IT industry, a practicing systems administrator and a teacher Passwords remind me a bit of the Coyote. Not Monde and right on the background, taped to the one that chases the Road Runner, but the the wall, is a list of passwords (and you thought one that lives in my native South-West and howls you had it rough with people taping them under at the moon. -

Encryption Enterprise Advanced Installation Guide V10.0 Notes, Cautions, and Warnings
Dell Encryption Enterprise Advanced Installation Guide v10.0 Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you how to avoid the problem. WARNING: A WARNING indicates a potential for property damage, personal injury, or death. © 2012-2018 Dell Inc. All rights reserved. Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be trademarks of their respective owners.Registered trademarks and trademarks used in the Dell Encryption, Endpoint Security Suite Enterprise, and Data Guardian suite of documents: Dell™ and the Dell logo, Dell Precision™, OptiPlex™, ControlVault™, Latitude™, XPS®, and KACE™ are trademarks of Dell Inc. Cylance®, CylancePROTECT, and the Cylance logo are registered trademarks of Cylance, Inc. in the U.S. and other countries. McAfee® and the McAfee logo are trademarks or registered trademarks of McAfee, Inc. in the US and other countries. Intel®, Pentium®, Intel Core Inside Duo®, Itanium®, and Xeon® are registered trademarks of Intel Corporation in the U.S. and other countries. Adobe®, Acrobat®, and Flash® are registered trademarks of Adobe Systems Incorporated. Authen tec® and Eikon® are registered trademarks of Authen tec. AMD® is a registered trademark of Advanced Micro Devices, Inc. Microsoft®, Windows®, and Windows Server®, Internet Explorer®, Windows Vista®, Windows 7®, Windows 10®, Active Directory®, Access®, BitLocker®, BitLocker To Go®, Excel®, Hyper-V®, Outlook®, PowerPoint®, Word®, OneDrive®, SQL Server®, and Visual C++® are either trademarks or registered trademarks of Microsoft Corporation in the United States and/or other countries. -

Security Best Practices for Developing Windows Azure Applications
Security Best Practices For Developing Windows Azure Applications Authors Andrew Marshall (Senior Security Program Manager, Security Engineering) Michael Howard (Principal Security Program Manager, Security Engineering) Grant Bugher (Lead Security Program Manager, OSSC) Brian Harden (Security Architect, OSSC) Contributors Charlie Kaufman (Principal Architect) Martin Rues (Director, OSSC) Vittorio Bertocci (Senior Technical Evangelist, Developer and Platform Evangelism) June 2010 (REVISION 2) The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This White Paper is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), or for any purpose, without the express written permission of Microsoft Corporation. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights -

Smarx OS Compendium 2020 for the CRYPTO-BOX
2020 EDITION Smarx® Compendium d s p . ) r e v o C _ n a M x r a m S ( a s 2 1 v o N 7 2 - www.marx.com 0 2 We highly appreciate and value your comments and suggestions! Suggestions for improvements will be honored with: • Free Business Support for 6 months • Enrollment in our BE !" ester program Software security is a growing challenge and requires constant improving " be part of the process! $lease send sugestions and error report to: • $$%& software/hardware in general and documentation (including this Compendium*: support@mar,.com • WEB and online ordering system related: webmaster+mar,.com Smar, .S )ompendium November 2020 )opyright 1 2002, 2020 2!345 )ryptoTech 6$ 7 Table of Contents 8. What is this Compendium !bout?--------------------------------------------------------------------------------: 8-8. ;ntroduction--------------------------------------------------------------------------------------------------------: 8.2. What is /ew9-------------------------------------------------------------------------------------------------------: 8-7. What to Find Where in this )ompendium--------------------------------------------------------------< 8-=. $rofessional Software $rotection Secures 3evenue----------------------------------------------< 8->. he )3?$ ."BO45@ardware-----------------------------------------------------------------------------88 8->-8. )3?$ ."BOX 2odels--------------------------------------------------------------------------------88 8->.2. echnical Features of the )3?$ ."BO45----------------------------------------------------88 -

Invisimole: the Hidden Part of the Story Unearthing Invisimole’S Espionage Toolset and Strategic Cooperations
ESET Research white papers TLP: WHITE INVISIMOLE: THE HIDDEN PART OF THE STORY UNEARTHING INVISIMOLE’S ESPIONAGE TOOLSET AND STRATEGIC COOPERATIONS Authors: Zuzana Hromcová Anton Cherepanov TLP: WHITE 2 InvisiMole: The hidden part of the story CONTENTS 1 EXECUTIVE SUMMARY � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � 4 2 ATTACKS AND INVESTIGATION � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � 4 2.1 InvisiMole’s toolset ������������������������������������������������������������������������������������������������������������������������ 5 2.2 Cooperation between InvisiMole and Gamaredon . 5 3 BUILDING BLOCKS � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � 6 3.1 Structure ������������������������������������������������������������������������������������������������������������������������������������������6 3.1.1 InvisiMole blobs . 6 3.1.2 Execution guardrails with DPAPI ���������������������������������������������������������������������������������7 3.2 Payload ��������������������������������������������������������������������������������������������������������������������������������������������8 3.2.1 TCP downloader ��������������������������������������������������������������������������������������������������������������9 3.2.2 DNS downloader . 9 3.2.3 RC2CL backdoor �������������������������������������������������������������������������������������������������������������13 -

Dell Data Protection | Encryption Enterprise Edition Advanced Installation Guide V8.13 Notes, Cautions, and Warnings
Dell Data Protection | Encryption Enterprise Edition Advanced Installation Guide v8.13 Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you how to avoid the problem. WARNING: A WARNING indicates a potential for property damage, personal injury, or death. © 2017 Dell Inc. All rights reserved.Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be trademarks of their respective owners. Registered trademarks and trademarks used in the Dell Data Protection Encryption, Endpoint Security Suite, Endpoint Security Suite Enterprise, and Dell Data Guardian suite of documents: DellTM and the Dell logo, Dell PrecisionTM, OptiPlexTM, ControlVaultTM, LatitudeTM, XPS®, and KACETM are trademarks of Dell Inc. Cylance®, CylancePROTECT, and the Cylance logo are registered trademarks of Cylance, Inc. in the U.S. and other countries. McAfee® and the McAfee logo are trademarks or registered trademarks of McAfee, Inc. in the US and other countries. Intel®, Pentium®, Intel Core Inside Duo®, Itanium®, and Xeon® are registered trademarks of Intel Corporation in the U.S. and other countries. Adobe®, Acrobat®, and Flash® are registered trademarks of Adobe Systems Incorporated. Authen Tec® and Eikon® are registered trademarks of Authen Tec. AMD® is a registered trademark of Advanced Micro Devices, Inc. Microsoft®, Windows®, and Windows Server®, Internet Explorer®, MS-DOS®, Windows Vista®, MSN®, ActiveX®, Active Directory®, Access®, ActiveSync®, BitLocker®, BitLocker To Go®, Excel®, Hyper-V®, Silverlight®, Outlook®, PowerPoint®, OneDrive®, SQL Server®, and Visual C++® are either trademarks or registered trademarks of Microsoft Corporation in the United States and/or other countries. -

Sari Haj Hussein Master's Thesis
Double SSO – A Prudent and Lightweight SSO Scheme Master of Science Thesis in the Programme Secure and Dependable Computer Systems SARI HAJ HUSSEIN Chalmers University of Technology University of Gothenburg Department of Computer Science and Engineering Göteborg, Sweden, November 2010 The Author grants to Chalmers University of Technology and University of Gothenburg the non-exclusive right to publish the Work electronically and in a non-commercial purpose make it accessible on the Internet. The Author warrants that he/she is the author to the Work, and warrants that the Work does not contain text, pictures or other material that violates copyright law. The Author shall, when transferring the rights of the Work to a third party (for example a publisher or a company), acknowledge the third party about this agreement. If the Author has signed a copyright agreement with a third party regarding the Work, the Author warrants hereby that he/she has obtained any necessary permission from this third party to let Chalmers University of Technology and University of Gothenburg store the Work electronically and make it accessible on the Internet. Double SSO – A Prudent and Lightweight SSO Scheme SARI HAJ HUSSEIN © SARI HAJ HUSSEIN, November 2010. Examiner: DAVID SANDS Chalmers University of Technology University of Gothenburg Department of Computer Science and Engineering SE-412 96 Göteborg Sweden Telephone + 46 (0)31-772 1000 Cover: Stage A of Double SSO, see Chapter 5 Department of Computer Science and Engineering Göteborg, Sweden November 2010 Abstract User authentication means the verification of a user identity in a computer system. In a typical scenario, users in an organization have access to several independent services, each of them requires separate credentials (e.g., user name and password) for user authentication. -
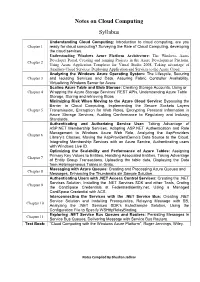
Notes on Cloud Computing Syllabus
Notes on Cloud Computing Syllabus Understanding Cloud Computing: Introduction to cloud computing, are you Chapter 1 ready for cloud computing? Surveying the Role of Cloud Computing, developing the cloud services. Understanding Windows Azure Platform Architecture: The Windows Azure Developer Portal, Creating and running Projects in the Azure Development Platform, Chapter 2 Using Azure Application Templates for Visual Studio 2008, Taking advantage of Auxiliary Cloud Services, Deploying Application and Services to the Azure Cloud. Analyzing the Windows Azure Operating System: The Lifecycle, Securing Chapter 3 and Isolating Services and Data, Assuring Fabric Controller Availability, Virtualizing Windows Server for Azure. Scaling Azure Table and Blob Storage: Creating Storage Accounts, Using or Chapter 4 Wrapping the Azure Storage Services’ REST APIs, Understanding Azure Table Storage, Storing and retrieving Blobs Minimizing Risk When Moving to the Azure Cloud Service: Bypassing the Barrier to Cloud Computing, Implementing the Secure Sockets Layers Chapter 5 Transmission, Encryption for Web Roles, Encrypting Personal Information in Azure Storage Services, Auditing Conformance to Regulatory and Industry Standards. Authenticating and Authorizing Service User: Taking Advantage of ASP.NET Membership Services, Adapting ASP.NET Authentication and Role Management to Windows Azure Web Role, Analyzing the AspProviders Chapter 6 Library’s Classes, Moving the AspProvidersDemo’s Data Source to the Cloud, Integrating Membership Services with an Azure Service, Authenticating users with Windows Live ID. Optimizing the Scalability and Performance of Azure Tables: Assigning Primary Key Values to Entities, Handling Associated Entities, Taking Advantage Chapter 7 of Entity Group Transactions, Uploading the table data, Displaying the Data from Heterogeneous Tables in Grids. Massaging with Azure Queues: Creating and Processing Azure Queues and Chapter 8 Messages, Enhancing the Thumbnails.sin Sample Solution. -

Security Policy for FIPS 140-2 Validation
Enhanced Cryptographic Provider Security Policy for FIPS 140‐2 Validation Microsoft Windows 8 Microsoft Windows Server 2012 Microsoft Windows RT Microsoft Surface Windows RT Microsoft Surface Windows 8 Pro Microsoft Windows Phone 8 Microsoft Windows Storage Server 2012 Enhanced Cryptographic Provider (RSAENH.DLL) DOCUMENT INFORMATION Version Number 1.2 Updated On December 17, 2014 © 2014 Microsoft. All Rights Reserved Page 1 of 25 This Security Policy is non‐proprietary and may be reproduced only in its original entirety (without revision). Enhanced Cryptographic Provider The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs- NonCommercial License (which allows redistribution of the work). To view a copy of this license, visit http://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property.