Defeating Pass-The-Hash
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
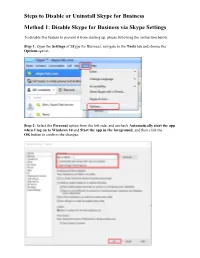
Steps to Disable Or Uninstall Skype for Business Method 1: Disable Skype for Business Via Skype Settings
Steps to Disable or Uninstall Skype for Business Method 1: Disable Skype for Business via Skype Settings To disable this feature to prevent it from starting up, please following the instruction below. Step 1: Open the Settings of Skype for Business, navigate to the Tools tab and choose the Options option. Step 2: Select the Personal option from the left side, and uncheck Automatically start the app when I log on to Windows 10 and Start the app in the foreground, and then click the OK button to confirm the changes. Step 3: Click the Settings button again on the Skype for Business interface and choose File then Exit. After the three steps, you have successfully disabled Skype for Business from your PC and you will no longer see it although it is still on your computer. Method 2: Uninstall Skype for Business via Control Panel This method requires you to clear all your profile cache for the Skype for Business account and then uninstall it from Windows 10 via Control Panel. Here is the detailed tutorial on uninstalling Skype for Business. Step 1: Open your Skype for business and then sign out of this application. Step 2: In the Sign in interface, please click the Delete my sign-in info option. Note: This step will clear all your profile cache for the Skype for Business account and will disable the auto sign-in when the application opens. Step 3: Close Skype for Business. Step 4: You should uninstall Skype for Business like any other software on your computer. Click on the Windows button in the bottom left of your screen and type Control Panel. -
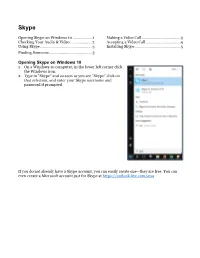
Opening Skype on Windows 10
Skype Opening Skype on Windows 10 ................... 1 Making a Video Call ..................................... 3 Checking Your Audio & Video .................... 2 Accepting a Video Call .................................4 Using Skype ................................................. 3 Installing Skype ........................................... 5 Finding Someone ........................................ 3 Opening Skype on Windows 10 1. On a Windows 10 computer, in the lower left corner click the Windows icon. 2. Type in “Skype” and as soon as you see “Skype” click on that selection, and enter your Skype username and password if prompted. If you do not already have a Skype account, you can easily create one—they are free. You can even create a Microsoft account just for Skype at https://outlook.live.com/owa Checking Your Audio & Video 1. Open Skype. 2. In the left pane, in the top right corner, click on the ellipse (…). 3. Your Settings open. 4. In the left pane, select Audio & Video. 5. In the Camera section your live picture should appear. If it does not, see if there is an option above your picture, and try selecting a different web camera. 6. Scroll down until you see the Audio section. Test your microphone and speakers and adjust the volume as needed. 7. Close the dialog box by clicking the X in the top left corner. Using Skype Once you open Skype, you will select someone to call from the left pane. You have some important options there: Search, Chats, Contacts The first couple times you use Skype you may need to search for your friends and family. You can search by name or email address associated with their Skype account. -

Microsoft Windows 10 Update Hello, Microsoft Has Begun
Subject Line: Microsoft Windows 10 Update Hello, Microsoft has begun pushing a warning message to Windows 10 computers that a critical security update must be performed. Several clients have informed us that they are seeing the warning message. It will appear as a generic blue screen after your computer has been powered up, and it states that after April 10, 2018 Microsoft will no longer support your version of Windows 10 until the critical security update has been performed. Please note if your UAN computer has not been recently connected to the internet, you would not have received this message. UAN has confirmed that the warning message is a genuine message from Microsoft, and UAN strongly encourages all clients to perform this critical security update as soon as possible. Please note: ‐ This update is a Microsoft requirement and UAN cannot stop or delay its roll out. To perform the critical security updated select the ‘Download update’ button located within the warning message. ‐ This update is very large, for those clients that have metered internet usage at their home may want to perform the update at a different location with unmetered high speed internet, perhaps at another family member’s home. ‐ Several UAN staff members have performed the critical security update on their home computers, and the process took more than an hour to complete. To check that your computer has been updated or to force the update at a time that is convenient to you, go to the windows Start button and click on Settings (the icon that looks like a gear above the Start button) > Update and Security > Windows Update > Check for Updates and then follow the instructions on the screen. -
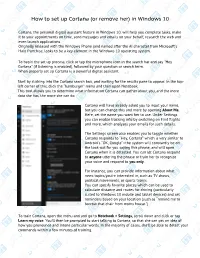
How to Set up Cortana (Or Remove Her) in Windows 10
How to set up Cortana (or remove her) in Windows 10 Cortana, the personal digital assistant feature in Windows 10, will help you complete tasks, make it to your appointments on time, send messages and emails on your behalf, research the web and even launch applications. Orignally released with the Windows Phone (and named after the AI character from Microsoft's Halo franchise, looks to be a key element in the Windows 10 operating system. To begin the set up process, click or tap the microphone icon in the search bar and say "Hey Cortana" (if listening is enabled), followed by your question or search term. When properly set up Cortana is a powerful digital assistant. Start by clicking into the Cortana search box, and waiting for the results pane to appear. In the top- left corner of this, click the “hamburger” menu and then open Notebook. This tool allows you to determine what information Cortana can gather about you, and the more data she has, the more she can do. Cortana will have already asked you to input your name, but you can change this and more by opening About Me. Here, set the name you want her to use. Under Settings you can enable tracking info by switching on Find flights and more, which analyses your emails for such details. The Settings screen also enables you to toggle whether Cortana responds to “Hey, Cortana” which is very similar to Android’s “OK, Google“–the system will constantly be on the look-out for you saying this phrase, and will open Cortana when it is detected. -

Guide to Hardening Windows 10 Technical Guide
NOVEMBER 2020 Guide to Hardening Windows 10 For Administrators, Developers and Office Workers TABLE OF CONTENTS Introduction .......................................................................................................................... 4 Prerequisites ............................................................................................................................ 4 User roles ................................................................................................................................. 4 EFI (BIOS) Configuration ...................................................................................................... 5 To be enabled: ......................................................................................................................... 5 To be disabled: ......................................................................................................................... 5 Windows Defender Firewall .................................................................................................. 6 Enable logging of dropped packets ............................................................................................. 6 Disable enforcement of local rules and disable notifications .......................................................... 7 Block outbound connections by default ....................................................................................... 8 Secure potentially vulnerable protocols ...................................................................................... -

Implementing Remote Credential Guard and Remote Admin Mode on Domain-Joined Windows 10 Clients
INF258x: Implementing Remote Credential Guard and Remote Admin mode on Domain-joined Windows 10 Clients Estimated Time: 30 minutes You have a domain-joined Windows 10 client computer. You plan to take advantage of the Remote Desktop Credential Guard and Restrict Admin mode to protect credentials during Remote Desktop sessions between Windows 10 client and Windows Server 2016 computers. Objectives After completing this lab, students will be able to: • Implement Remote Credential Guard. • Implement the Restricted Admin mode. • Verify functionality of Remote Credential Guard and the Restricted Admin mode. Lab environment The lab consists of the following computers: • LON-DC1 – a Windows Server 2016 domain controller in the adatum.com single-domain forest. • LON-SVR1 – a Windows Server 2016 domain member server • LON-CL1 – a Windows 10 Pro or Enterprise version 1607 (or newer) domain member computer with Remote Server Administration Tools for Windows 10 All computers have Windows PowerShell Remoting enabled and have Internet connectivity Remote Desktop connections protected with Credential Guard have the following characteristics: • Require Windows 10 version 1607 (or newer) or Windows Server 2016 • Enforce of Kerberos authentication (NTLM is not allowed). • Require that both computers (a Remote Desktop client and a Remote Desktop host) are members of the same Active Directory domain or trusted Active Directory domains (Kerberos is enforced) • Support connecting with non-Administrative credentials (as a member of the Remote Desktop Users group) -

Windows 10 Enterprise E3 in CSP - Windows Deployment | Microsoft Docs
07/01/2020 Windows 10 Enterprise E3 in CSP - Windows Deployment | Microsoft Docs Windows 10 Enterprise E3 in CSP 08/23/2017 • 16 minutes to read • +5 In this article Compare Windows 10 Pro and Enterprise editions Deployment of Windows 10 Enterprise E3 licenses Deploy Windows 10 Enterprise features Related topics Windows 10 Enterprise E3 launched in the Cloud Solution Provider (CSP) channel on September 1, 2016. Windows 10 Enterprise E3 in CSP is a new offering that delivers, by subscription, exclusive features reserved for Windows 10 Enterprise edition. This offering is available through the Cloud Solution Provider (CSP) channel via the Partner Center as an online service. Windows 10 Enterprise E3 in CSP provides a flexible, per- user subscription for small- and medium-sized organizations (from one to hundreds of users). To take advantage of this offering, you must have the following: Windows 10 Pro, version 1607 (Windows 10 Anniversary Update) or later, installed and activated, on the devices to be upgraded Azure Active Directory (Azure AD) available for identity management Starting with Windows 10, version 1607 (Windows 10 Anniversary Update), you can move from Windows 10 Pro to Windows 10 Enterprise more easily than ever before— no keys and no reboots. After one of your users enters the Azure AD credentials associated with a Windows 10 Enterprise E3 license, the operating system turns from Windows 10 Pro to Windows 10 Enterprise and all the appropriate Windows 10 Enterprise features are unlocked. When a subscription license expires or is transferred to another user, the Windows 10 Enterprise device seamlessly steps back down to Windows 10 Pro. -
Quick Guide Page | 1
Quick Guide Page | 1 Contents Welcome to Windows 10 ................................................................................................................................................................................................... 3 Key innovations ...................................................................................................................................................................................................................... 3 Cortana ................................................................................................................................................................................................................................. 3 Microsoft Edge .................................................................................................................................................................................................................. 4 Gaming & Xbox ................................................................................................................................................................................................................ 5 Built-in apps ....................................................................................................................................................................................................................... 7 Enterprise-grade secure and fast ................................................................................................................................................................................... -

Feature Description
NTLM Feature Description UPDATED: 19 March 2021 NTLM Copyright Notices Copyright © 2002-2021 Kemp Technologies, Inc. All rights reserved. Kemp Technologies and the Kemp Technologies logo are registered trademarks of Kemp Technologies, Inc. Kemp Technologies, Inc. reserves all ownership rights for the LoadMaster and Kemp 360 product line including software and documentation. Used, under license, U.S. Patent Nos. 6,473,802, 6,374,300, 8,392,563, 8,103,770, 7,831,712, 7,606,912, 7,346,695, 7,287,084 and 6,970,933 kemp.ax 2 Copyright 2002-2021, Kemp Technologies, All Rights Reserved NTLM Table of Contents 1 Introduction 4 1.1 Document Purpose 6 1.2 Intended Audience 6 1.3 Related Firmware Version 6 2 Configure NTLM Authentication 7 2.1 Configure Internet Options on the Client Machine 7 2.2 Configure the LoadMaster 11 2.2.1 Enable NTLM Proxy Mode 13 2.2.2 Configure the Server Side SSO Domain 13 2.2.3 Configure the Client Side SSO Domain 15 2.2.4 Configure the Virtual Service 15 2.3 Configure Firefox to Allow NTLM (if needed) 17 2.4 Troubleshooting 18 References 19 Last Updated Date 20 kemp.ax 3 Copyright 2002-2021, Kemp Technologies, All Rights Reserved NTLM 1 Introduction 1 Introduction NT LAN Manager (NTLM) is a Windows Challenge/Response authentication protocol that is often used on networks that include systems running the Windows operating system and Active Directory. Kerberos authentication adds greater security than NTLM systems on a network and provides Windows-based systems with an integrated single sign-on (SSO) mechanism. -

Web Server IIS Deployment
https://www.halvorsen.blog ASP.NET Core Web Server IIS Deployment Hans-Petter Halvorsen Introduction • Introduction to IIS deployment • If you have never used ASP.NET Core, I suggest the following Videos: – ASP.NET Core - Hello World https://youtu.be/lcQsWYgQXK4 – ASP.NET Core – Introduction https://youtu.be/zkOtiBcwo8s 2 Scenario Development Environment Test/Production Environment Local PC with Windows 10 Windows 10/Windows Server ASP.NET Core IIS Web Application SQL Server Visual Studio ASP.NET Core SQL Server Express Web Application Visual Studio Web Server • A web server is server software that can satisfy client requests on the World Wide Web. • A web server can contain one or more websites. • A web server processes incoming network requests over HTTP and several other related protocols. • The primary function of a web server is to store, process and deliver web pages to clients. • The communication between client and server takes place using the Hypertext Transfer Protocol (HTTP). • Pages delivered are most frequently HTML documents, which may include images, style sheets and scripts in addition to the text content. https://en.wikipedia.org/wiki/Web_server 4 Web Pages and Web Applications Web Server Client Web Server software, e.g., Internet Information Services (IIS) Request Web Browser, (URL) e.g., Edge, Internet Chrome, Safari, or Local etc. Response Network (LAN) Data- (HTML) base Operating System, e.g., Windows Server PC with Windows 10, macOS or Linux Smartphone with Android or iOS, etc. Web Server Software PHP (pronounced "engine x") Internet Information Services - Has become very popular lately ASP.NET Cross-platform: UNIX, Linux, OS X, Windows, .. -

Implementing Microsoft Credential Guard for Iso 27001, Pci, and Fedramp
IMPLEMENTING MICROSOFT CREDENTIAL GUARD FOR ISO 27001, PCI, AND FEDRAMP North America | Latin America | Europe 877.224.8077 | [email protected] | coalfire.com Coalfiresm and CoalfireOnesm are registered service marks of Coalfire Systems, Inc. All rights reserved. INTRODUCTION The threat of a cyber-attack is a constant factor all organizations must consider when developing their information security posture. A particular area of concern is the exploitation of information system derived domain credentials and credential artifacts, which present attackers the opportunity to pass-the-hash or pass-the-ticket with derived domain credentials such as NTLM password hashes or Kerberos tickets. Credential Guard is a set of new security features for Windows Server 2016 and the Windows 10 operating system which helps organizations prevent derived credentials from being compromised by advanced attacks or from being exposed during certain authentication workflows. In order to help customers implement this new capability for compliance with ISO, PCI, or FedRAMP, Microsoft worked closely with Coalfire, a recognized third-party IT compliance firm, to define each security and compliance objective in relation to the capabilities of Credential Guard. In addition, Appendix A contains mappings between Credential Guard and the security control requirements present in ISO 27001, PCI DSS, and FedRAMP. OVERVIEW OF CREDENTIAL GUARD Credential Guard provides robust protections against local pass-the-hash or pass-the-ticket attacks on derived credentials by providing advanced virtualization-based isolation for certain authentication workflows within normal Windows system operation. Previously, during authentication workflows that required NTLM or Kerberos authentication, Windows stored derived credentials in process memory associated with the Local Security Authority (LSA). -

UI Developers' Guide - Installation
UI Developers' Guide - Installation This section outlines the steps necessary to download, configure, build, and run the Ed-Fi Dashboard UI on a development machine. UI Developers' Guide The Ed-Fi Dashboards configuration described in this document has been tested with the following Contents software configuration: Read more about the UI Developers' Windows 8.1 Professional (64-bit) and Enterprise (64-bit); Windows 10 Professional (64-bit) Guide: and Enterprise (64-bit). Windows Server 2012 and Windows Server 2008 R2 (Windows Server 2008 releases before R2 are not supported). Internet Information Services (IIS) 8.0 and IIS 10.0. Microsoft SQL Server 2012 – with Service Pack 3 or higher (Standard Edition, Developer Edition, or Enterprise Edition. Note that Express Edition is not supported). Configure SQL Server with the following features: Database Engine Services (replication/text search not required). Management Tools (complete). Use the default instance (MSSQLSERVER). Choose Mixed Mode security (the application uses a SQL login). Specify a password for the sa account. In the “Specify SQL Server administrator” click on Add Current User. Visual Studio 2013 or 2015 (Professional Edition or higher). .NET Framework 4.5.2. Preparing a development environment to run the dashboards can be summarized as follows: Step 1. Download and Extract the Dashboard Source Code The Ed-Fi Dashboards source code is contained in one repository that can be downloaded using git clone or as a ZIP archive from the Ed-Fi Alliance source code repository in GitHub at https://github.com /Ed-Fi-Alliance/Ed-Fi-Dashboard. The links to the latest stable and development code versions are located in the section Getting Started - Downloading the Code.