Secrecy in the Bush Administration
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Southeast Clean Energy Resource Team Strategic Energy Plan
Southeast Clean Energy Resource Team Strategic Energy Plan CERTS PARTNERS: Minnesota Department of Commerce The Minnesota Project University of Minnesota Regional Sustainable Development Partnerships Rural Minnesota Energy Board Metropolitan Counties Energy Task Force Resource Conservation and Development Councils FUNDED BY: The Legislative Commission on Minnesota Resources from the U.S. Department of Energy Oil Overcharge Money The Carolyn Foundation The Blandin Foundation Minnesota Department of Commerce U.S. Department of Energy Community Assistantship Program, University of Minnesota, with financial sup- port from the Otto Bremer Foundation and Regional Sustainable Development Partnerships Program University of Minnesota Initiative for Renewable Energy and the Environment University of Minnesota Regional Sustainable Development Partnerships FINAL REPORT Energy Use, Renewable Energy Resources and Potential for Meeting the Energy Needs of the Fifteen Counties in SE/SC MN from Local Renewable Energy Resources and Energy Efficiency From the Citizens on the THE SE/SC CLEAN ENERGY RESOURCE TEAM Representing 15 Counties in SE/SC Minnesota: Blue Earth, Dodge, Faribault, Fillmore, Freeborn, Goodhue, Houston, Le Sueur, Mower, Olmsted, Rice, Steele, Wabasha, Waseca, Winona JUNE 2005 Dedicated to Dick Broeker, 1942 - 2004 The SE/SC Clean Energy Resource Team (CERT) dedicates this report to the memory of Dick Broeker. As Director of the Experiment in Rural Cooperation in SE Minnesota, Dick was involved in establishing the CERTs Project. When the Clean Energy Resources Teams were formed in regions around the state in December 2003, Dick was instrumental in organizing our team and helping us with our work through June 2004, when he retired. During this time, we completed a Strategic Plan to guide our work and an Inventory and Assessment of the people, infrastructure and resources in our area. -

Rethinking Presidential Power—The Unitary Executive and the George W
Rethinking Presidential Power—The Unitary Executive and the George W. Bush Presidency. Paper prepared for the 63rd Annual Meeting of the Midwest Political Science Association April 7-10, 2005 Chicago, IL Christopher S. Kelley, Ph.D. Department of Political Science Miami University Oxford, OH [email protected] Abstract: Since the Nixon administration, modern presidents have had a difficult time relying upon the traditional powers of bargaining and persuading offered by the “Modern Presidency” theory of presidential power. As a result, presidents have relied on numerous unilateral actions in order to protect the prerogative of the office and to advance the president’s policy preferences by controlling the executive branch. The “unitary executive” theory offers such an explanation of presidential behavior that some regard as “imperial.” In this paper, I explain what the unitary executive theory is, how it has developed, and how the current Bush administration has fully embraced the theory in helping it govern since the very first day of office in 2001. I will focus on the use of signing statements, executive orders, and the OIRA to advance the administration’s objectives. Keywords: Unitary Executive, Signing Statements, Executive Orders, OMB, OIRA Dana Milbank, the former White House reporter for the “Washington Post,” wrote in an October 11, 2004 column profiling David Addington, Vice-President Cheney’s counsel, about an obscure theory of presidential power that permeated the Bush White House. The article described the detail to which Cheney and Addington had paid to preserving presidential power, from the now-famous “torture” memo to international law governing torture to withholding information about the energy task force formed in 2001 to deal with the country’s energy problem. -

USA V. Leandro Aragoncillo
2005R00881/INDICTMENT/KHB UNITED STATES DISTRICT COURT DISTRICT OF NEW JERSEY UNITED STATES OF AMERICA : Hon. William H. Walls v. : Criminal No. 06- LEANDRO ARAGONCILLO, : 18 U.S.C. §§ 794(a) and (c) a/k/a “Juan Miguel” 18 U.S.C. § 793(e) 18 U.S.C. § 1030(a)(1) 18 U.S.C. § 2 I N D I C T M E N T The Grand Jury in and for the District of New Jersey, sitting at Newark, charges: COUNT 1 (Conspiracy to Transmit National Defense Information) The Defendant 1. At all times material to the allegations contained in this Indictment: a. Defendant LEANDRO ARAGONCILLO was enlisted in the United States Marine Corps from on or about September 30, 1983 through in or about June 2004, retiring at the rank of Gunnery Sergeant. From on or about July 26, 1999 through on or about February 13, 2002, defendant ARAGONCILLO served as a Staff Assistant to the Vice President’s Military Advisers in the Office of the Vice President (“OVP”) of the United States. b. After retiring from the Marine Corps, defendant ARAGONCILLO was employed as an Intelligence Analyst of the Federal Bureau of Investigation (“FBI”) at the Fort Monmouth Information Technology Center (“FMITC”) located in Oceanport, New Jersey, from on or about July 11, 2004 through in or about September 2005. c. In his capacity as a Staff Assistant in the OVP, and as an Intelligence Analyst at the FMITC, defendant ARAGONCILLO received security clearances in order to have access to classified documents and information. Defendant ARAGONCILLO received a “Top Secret” security clearance on or about July 23, 1999, and maintained that clearance throughout his term of service with the OVP. -

Administration of Barack H. Obama, 2009
Administration of Barack H. Obama, 2009 Executive Order 13526—Classified National Security Information December 29, 2009 This order prescribes a uniform system for classifying, safeguarding, and declassifying national security information, including information relating to defense against transnational terrorism. Our democratic principles require that the American people be informed of the activities of their Government. Also, our Nation's progress depends on the free flow of information both within the Government and to the American people. Nevertheless, throughout our history, the national defense has required that certain information be maintained in confidence in order to protect our citizens, our democratic institutions, our homeland security, and our interactions with foreign nations. Protecting information critical to our Nation's security and demonstrating our commitment to open Government through accurate and accountable application of classification standards and routine, secure, and effective declassification are equally important priorities. Now, Therefore, I, Barack Obama, by the authority vested in me as President by the Constitution and the laws of the United States of America, it is hereby ordered as follows: PART 1—ORIGINAL CLASSIFICATION Section 1.1. Classification Standards. (a) Information may be originally classified under the terms of this order only if all of the following conditions are met: (1) an original classification authority is classifying the information; (2) the information is owned by, produced by or for, or is under the control of the United States Government; (3) the information falls within one or more of the categories of information listed in section 1.4 of this order; and (4) the original classification authority determines that the unauthorized disclosure of the information reasonably could be expected to result in damage to the national security, which includes defense against transnational terrorism, and the original classification authority is able to identify or describe the damage. -

1 Intervenor-Defendant American Petroleum Institute's Objections And
Case 6:15-cv-01517-TC Document 131-1 Filed 04/03/17 Page 1 of 37 C. Marie Eckert, OSB No. 883490 Marie.eckert@millernash Suzanne C. Lacampagne, OSB No. 951705 [email protected] MILLER NASH GRAHAM & DUNN LLP 3400 U.S. Bancorp Tower 111 S.W. Fifth Avenue Portland, Oregon 97204 Telephone: (503) 224-5858 Facsimile: (503) 224-0155 Frank R. Volpe [email protected] Benjamin E. Tannen [email protected] SIDLEY AUSTIN LLP 1501 K Street, N.W. Washington, D.C. 20005 Telephone: (202) 736-8000 Facsimile: (202) 736-8711 Attorneys for Intervenor-Defendants The National Association of Manufacturers, American Fuel & Petrochemical Manufacturers, and American Petroleum Institute UNITED STATES DISTRICT COURT DISTRICT OF OREGON EUGENE DIVISION KELSEY CASCADIA ROSE JULIANA, et al., Case No. 6:15-cv-01517-TC Plaintiffs, INTERVENOR-DEFENDANT v. AMERICAN PETROLEUM INSTITUTE’S OBJECTIONS AND UNITED STATES OF AMERICA, et al., RESPONSES TO PLAINTIFFS’ REQUEST FOR PRODUCTION OF Defendants. DOCUMENTS __________________________________________ Intervenor-Defendant the American Petroleum Institute (“API”), pursuant to Federal Rules of Civil Procedure 26 and 34, hereby respectfully submits the following Objections and 1 Intervenor-Defendant American Petroleum Institute’s Objections and Responses to Plaintiffs’ Request for Production of Documents Case 6:15-cv-01517-TC Document 131-1 Filed 04/03/17 Page 2 of 37 Responses to Plaintiffs’ Requests for Production of Documents to Intervenor-Defendant American Petroleum Institute (“Requests”), submitted February 17, 2017, and states as follows: GENERAL OBJECTIONS 1. API objects to the Requests to the extent that they seek information and documents which are not relevant to the claims or defenses of any party or proportional to the needs of the case, per Federal Rule of Civil Procedure 26(b)(1). -

Government Information Availability and Secrecy. Rhonda E
Eastern Michigan University DigitalCommons@EMU University Library Faculty Scholarship University Library Summer 2007 I've Got a Secret: Government Information Availability and Secrecy. Rhonda E. Fowler Eastern Michigan University, [email protected] Follow this and additional works at: http://commons.emich.edu/lib_sch Part of the Library and Information Science Commons Recommended Citation Fowler, Rhonda E., "I've Got a Secret: Government Information Availability and Secrecy." (2007). University Library Faculty Scholarship. Paper 3. http://commons.emich.edu/lib_sch/3 This Article is brought to you for free and open access by the University Library at DigitalCommons@EMU. It has been accepted for inclusion in University Library Faculty Scholarship by an authorized administrator of DigitalCommons@EMU. For more information, please contact lib- [email protected]. I’ve Got a Secret Government Information Availability and Secrecy Rhonda E. Fowler “The United States has the most open government in the world, but it also has the most secretive government in the world, if you measure it by the production of new secrets.”—Steven Aftergood, director of the Project on Government Secrecy at the Federation of American Scientists1 ecrets and information, what do they have in com- accessible, the public’s right to know is jeopardized. But mon? A secret is something you don’t want anyone just how concerned is the public? A poll conducted in 2000 Sto know, something you keep to yourself or those by the Center for Survey Research and Analysis at the Uni- you trust. “Knowledge obtained from investigation” is the versity of Connecticut asked the question: “Government definition of information, according to Webster’s Dictionary. -

Reining in the Imperial Presidency
REINING IN THE IMPERIAL PRESIDENCY VerDate Nov 24 2008 23:13 Apr 07, 2009 Jkt 048026 PO 00000 Frm 00001 Fmt 6019 Sfmt 6019 E:\HR\OC\G026A.XXX G026A hsrobinson on PROD1PC76 with HEARING with PROD1PC76 on hsrobinson VerDate Nov 24 2008 23:13 Apr 07, 2009 Jkt 048026 PO 00000 Frm 00002 Fmt 6019 Sfmt 6019 E:\HR\OC\G026A.XXX G026A hsrobinson on PROD1PC76 with HEARING Reining in the Imperial Presidency: Lessons and Recommendations Relating to the Presidency of George W. Bush C O N T E N T S Page Foreword ................................................................................................................ 1 Executive Summary ............................................................................................. 9 Preface: Deconstructing the Imperial Presidency ...................................... 17 I. The September 25, 2001 War Powers Memorandum .................................... 20 II. Critique of John Yoo’s Flawed Theory of Presidential Supremacy .............. 25 III. The Need for a Judiciary Committee Staff Report ........................................ 32 Section 1—Politicization of the Department of Justice ............................. 33 I. Politicization of the Prosecution Function ...................................................... 35 A. Hiring and Firing of U.S. Attorneys and other Department Personnel ......................................................................................... 35 B. Selective Prosecution ............................................................................ 42 II. Politicization -
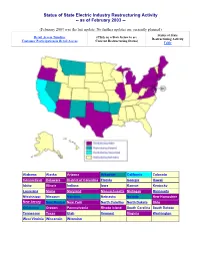
Status of State Electric Industry Restructuring Activity -- As of February 2003
Status of State Electric Industry Restructuring Activity -- as of February 2003 -- (February 2003 was the last update. No further updates are currently planned) Status of State Retail Access Timeline (Click on a State below to see Restructuring Activity Customer Participation in Retail Access Current Restructuring Status) Table Alabama Alaska Arizona Arkansas California Colorado Connecticut Delaware District of Columbia Florida Georgia Hawaii Idaho Illinois Indiana Iowa Kansas Kentucky Louisiana Maine Maryland Massachusetts Michigan Minnesota Mississippi Missouri Montana Nebraska Nevada New Hampshire New Jersey New Mexico New York North Carolina North Dakota Ohio Oklahoma Oregon Pennsylvania Rhode Island South Carolina South Dakota Tennessee Texas Utah Vermont Virginia Washington West Virginia Wisconsin Wyoming This site provides an overview of the status of electric industry restructuring in each state. Twenty-four states and the District of Columbia have either enacted enabling legislation or issued a regulatory order to implement retail access. The local distribution company continues to provide transmission and distribution (delivery of energy) services. Retail access allows customers to choose their own supplier of generation energy services, but each state's retail access schedule varies according to the legislative mandates or regulatory orders. The information in the “Status of State Electric Industry Restructuring Activity Map” was gathered from state public utility commissions, state legislatures, and utility company web pages. The state activity map is coded by color to indicate each state's restructuring progress. Purple colored states are active in the restructuring process, and these states have either enacted enabling legislation or issued a regulatory order to implement retail access. Retail access is either currently available to all or some customers or will soon be available. -

Security Classification Policy and Procedure: E.O. 12958, As Amended
Security Classification Policy and Procedure: E.O. 12958, as Amended Kevin R. Kosar Analyst in American National Government June 4, 2009 Congressional Research Service 7-5700 www.crs.gov 97-771 CRS Report for Congress Prepared for Members and Committees of Congress Security Classification Policy and Procedure: E.O. 12958, as Amended Summary Largely prescribed in a series of successive presidential executive orders issued over the past 50 years, security classification policy and procedure provide the rationale and arrangements for designating information officially secret for reasons of national security, and for its declassification as well. President Franklin D. Roosevelt issued the first executive order (E.O. 8381) in 1940. Current security classification policy may be found in Executive Order 12958, which was signed by President William Clinton on April 17, 1995. It “prescribes a uniform system for classifying, safeguarding, and declassifying national security information.” As issued, E.O. 12958 declared, “If there is significant doubt about the need to classify information, it shall not be classified.” Additionally, the order stated “If there is significant doubt about the appropriate level of classification, it shall be classified at the lower level.” President George W. Bush amended Executive Order 12958 via Executive Order 13292 on March 25, 2003. E.O. 13292 made many changes to E.O. 12958, and eliminated both of the aforementioned “significant doubt” provisions. On May 27, 2009, President Barack Obama ordered a review of E.O. 12958. The assistant to the President for National Security Affairs (commonly known as the National Security Advisor) is required to submit to the President “recommendations and proposed revisions” to E.O. -

Ocean Energy Task Force Final Report, 2009
Final Report of the Ocean Energy Task Force to Governor John E. Baldacci December 2009 Photo credits (clockwise from top center): Solberg/Statoil; Maine Coastal Program; Ocean Renewable Power Company; Principle Power; Blue H. Center photo: Global Marine Systems, Ltd. Final Report of the Ocean Energy Task Force to Governor John E. Baldacci December 2009 Financial assistance for this document was provided by a grant from the Maine Coastal Program at the Maine State Planning Office, through funding provided by the U.S. Department of Commerce, Office of Ocean and Coastal Resource Management under the Coastal Zone Management Act of 1972, as amended. Additional financial assistance was provided by the Efficiency Maine Trust (Efficiency Maine Trust is a statewide effort to promote the more efficient use of electricity, help Maine residents and businesses reduce energy costs, and improve Maine’s environment), and by the American Recovery and Reinvestment Act of 2009. This publication was produced under appropriation number 020-07B-008205 Final Report of the Ocean Energy Task Force TABLE OF CONTENTS Acknowledgements.....................................................................................................................................ii Executive Summary ...................................................................................................................................iii Summary of Recommendations..............................................................................................................vii Overview -

03-475, Cheney V. United States Dist. Court for D. C
Cite as: 541 U. S. ____ (2004) 1 Memorandum of SCALIA, J. SUPREME COURT OF THE UNITED STATES RICHARD B. CHENEY, VICE PRESIDENT OF THE UNITED STATES, ET AL. v. UNITED STATES DISTRICT COURT FOR THE DISTRICT OF COLUMBIA ET AL. ON PETITION FOR WRIT OF CERTIORARI TO THE UNITED STATES COURT OF APPEALS FOR THE DISTRICT OF COLUMBIA CIRCUIT No. 03–475. Decided March 18, 2004. Memorandum of JUSTICE SCALIA. I have before me a motion to recuse in these cases con- solidated below. The motion is filed on behalf of respon- dent Sierra Club. The other private respondent, Judicial Watch, Inc., does not join the motion and has publicly stated that it “does not believe the presently-known facts about the hunting trip satisfy the legal standards requir- ing recusal.” Judicial Watch Statement 2 (Feb. 13, 2004) (available in Clerk of Court’s case file). (The District Court, a nominal party in this mandamus action, has of course made no appearance.) Since the cases have been consolidated, however, recusal in the one would entail recusal in the other. I The decision whether a judge’s impartiality can “‘reasonably be questioned’ ” is to be made in light of the facts as they existed, and not as they were surmised or reported. See Microsoft Corp. v. United States, 530 U. S. 1301, 1302 (2000) (REHNQUIST, C. J.) (opinion respecting recusal). The facts here were as follows: For five years or so, I have been going to Louisiana during the Court’s long December-January recess, to the duck-hunting camp of a friend whom I met through two hunting companions from Baton Rouge, one a dentist and 2 CHENEYv. -

Nist Sp 800-59
Guideline for Identifying an Information System as a National Security System NIST Special Publication 800-59 Guideline for Identifying an Information System as a National Security System William C. Barker I N F O R M A T I O N S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 August 2003 U.S. Department of Commerce Donald L. Evans, Secretary Technology Administration Phillip J. Bond, Under Secretary of Commerce for Technology National Institute of Standards and Technology Arden L. Bement, Jr., Director Guideline for Identifying an Information System as a National Security System Reports on Computer Systems Technology The Information Technology Laboratory (ITL) at the National Institute of Standards (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the Nation’s measurement and standards infrastructure for information technology. ITL develops tests, test methods, reference data, proof of concept implementations and technical analyses to advance the development and productive use of information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in federal computer systems. This Special Publication 800 series reports on ITL’s research, guidance, and outreach efforts in computer security, and its collaborative activities with industry,