Show Off Your Oauth Joseph Henry, SAS Institute Inc
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Login with Amazon Developer Guide for Websites
Login with Amazon Developer Guide for Websites Login with Amazon: Developer Guide for Websites Copyright © 2017 Amazon Services, LLC or its affiliates. All rights reserved. Amazon and the Amazon logo are trademarks of Amazon.com, Inc. or its affiliates. All other trademarks not owned by Amazon are the property of their respective owners Contents Welcome .................................................................................................................................................. 2 How Do I...? .............................................................................................................................................. 2 Understanding Login with Amazon ........................................................................................................... 3 Login with Amazon Conceptual Overview ................................................................................................. 4 Single Sign-On (SSO) for Web ................................................................................................................. 6 Single Sign-On (SSO) for Mobile ............................................................................................................. 7 Access Token ............................................................................................................................................ 7 Authorization Code ................................................................................................................................... 7 Refresh Token .......................................................................................................................................... -

Vmware Workspace ONE Access 20.01 Managing User Authentication Methods in Vmware Workspace ONE Access
Managing User Authentication Methods in VMware Workspace ONE Access JAN 2020 VMware Workspace ONE Access 20.01 Managing User Authentication Methods in VMware Workspace ONE Access You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com © Copyright 2020 VMware, Inc. All rights reserved. Copyright and trademark information. VMware, Inc. 2 Contents 1 Configuring Authentication in VMware Workspace ONE Access 5 2 User Auth Service Authentication Methods in Workspace ONE Access 8 Configuring Password (Cloud) Authentication in Workspace ONE Access 9 Configure Password (Cloud) Authentication with Your Enterprise Directory 10 Configuring RSA SecurID (Cloud) For Workspace ONE Access 13 Prepare the RSA SecurID Server 13 Configure RSA SecurID Authentication in Workspace ONE Access 14 Configuring RADIUS for Workspace ONE Access 16 Prepare the RADIUS Server 16 Configure RADIUS Authentication in Workspace ONE Access 16 Enable User Auth Service Debug Logs In Workspace ONE Access Connector 19 3 Configuring Kerberos Authentication In Workspace ONE Access 21 Configure and Enable Kerberos Authentication in Workspace ONE Access 21 Configuring your Browser for Kerberos 23 Configure Internet Explorer to Access the Web Interface 23 Configure Firefox to Access the Web Interface 24 Configure the Chrome Browser to Access the Web Interface 25 Kerberos Initialization Error in Workspace ONE Access 26 4 Associate Workspace ONE Access Authentication Methods -

Adminstudio Inventory and Rationalization 2015 SP1 Installation Guide Legal Information
AdminStudio Inventory and Rationalization 2015 SP1 Installation Guide Legal Information Book Name: AdminStudio Inventory and Rationalization 2015 SP1 Installation Guide Part Number: ASRM-2015SP1-IG00 Product Release Date: 26 January 2016 Copyright Notice Copyright © 2016 Flexera Software LLC. All Rights Reserved. This publication contains proprietary and confidential information and creative works owned by Flexera Software LLC and its licensors, if any. Any use, copying, publication, distribution, display, modification, or transmission of such publication in whole or in part in any form or by any means without the prior express written permission of Flexera Software LLC is strictly prohibited. Except where expressly provided by Flexera Software LLC in writing, possession of this publication shall not be construed to confer any license or rights under any Flexera Software LLC intellectual property rights, whether by estoppel, implication, or otherwise. All copies of the technology and related information, if allowed by Flexera Software LLC, must display this notice of copyright and ownership in full. Intellectual Property For a list of trademarks and patents that are owned by Flexera Software, see http://www.flexerasoftware.com/intellectual-property. All other brand and product names mentioned in Flexera Software products, product documentation, and marketing materials are the trademarks and registered trademarks of their respective owners. Restricted Rights Legend The Software is commercial computer software. If the user or licensee of the Software is an agency, department, or other entity of the United States Government, the use, duplication, reproduction, release, modification, disclosure, or transfer of the Software, or any related documentation of any kind, including technical data and manuals, is restricted by a license agreement or by the terms of this Agreement in accordance with Federal Acquisition Regulation 12.212 for civilian purposes and Defense Federal Acquisition Regulation Supplement 227.7202 for military purposes. -

The Windows Operating System, Such As the Logon Process and the Session Manager
TTHEHE WWINDOWSINDOWS OOPERATINGPERATING SSYSTEMYSTEM William Stallings This document is an extract from Operating Systems: Internals and Design Principles, Fifth Edition Prentice Hall, 2005, ISBN 0-13-147954-7 Copyright 2005 William Stallings TTABLEABLE OFOF CCONTENTSONTENTS 2.5 MICROSOFT WINDOWS OVERVIEW...........................................................................3 History............................................................................................................................3 Single-User Multitasking...............................................................................................5 Architecture....................................................................................................................7 Operating System Organization.........................................................................7 User-Mode Processes.......................................................................................10 Client/Server Model.....................................................................................................11 Threads and SMP.........................................................................................................13 Windows Objects.........................................................................................................13 4.4 WINDOWS THREAD AND SMP MANAGEMENT.....................................................17 Process and Thread Objects.........................................................................................18 -

Measuring and Mitigating Oauth Access Token Abuse by Collusion Networks
Measuring and Mitigating OAuth Access Token Abuse by Collusion Networks Shehroze Farooqi Fareed Zafar The University of Iowa Lahore University of Management Sciences Nektarios Leontiadis Zubair Shafq Facebook The University of Iowa ABSTRACT 1 INTRODUCTION We uncover a thriving ecosystem of large-scale reputation manipu- Online social networks have become the primary way people con- lation services on Facebook that leverage the principle of collusion. nect and communicate with each other, consume information, and Collusion networks collect OAuth access tokens from colluding mem- form opinions. Reputation is a fundamental tenet of online social bers and abuse them to provide fake likes or comments to their networks. People trust the information that is posted by a reputable members. We carry out a comprehensive measurement study to social media account or is endorsed (e.g., liked) by a large number understand how these collusion networks exploit popular third- of accounts. Unfortunately, reputation fraud is prevalent in online party Facebook applications with weak security settings to retrieve social networks. A number of black-hat reputation manipulation OAuth access tokens. We infltrate popular collusion networks services target popular online social networks such as Facebook using honeypots and identify more than one million colluding Face- and Twitter [29, 53, 63]. These services rely on a large number of on- book accounts by “milking” these collusion networks. We disclose line social network accounts to conduct reputation manipulation at our fndings to Facebook and collaborate with them to implement a scale. To accomplish this goal, fraudsters purchase fake accounts in series of countermeasures that mitigate OAuth access token abuse bulk from underground marketplaces [55, 57], use infected accounts without sacrifcing application platform usability for third-party compromised by malware [51], or recruit users to join collusion developers. -

Roadmap for Section 4.3
Unit OS4: Scheduling and Dispatch 4.3. Windows Process and Thread Internals Windows Operating System Internals - by David A. Solomon and Mark E. Russinovich with Andreas Polze Roadmap for Section 4.3. Windows Process and Thread Internals Thread Block, Process Block Flow of Process Creation Thread Creation and Deletion Process Crashes Windows Error Reporting 2 1 Windows Process and Thread Internals Data Structures for each process/thread: Process environment Executive process block block (EPROCESS) Thread Executive thread block environment block (ETHREAD) Process address space Win32 process block System address space Process block Process environment block (EPROCESS) Win32 process block Thread environment block Handle table Thread block (ETHREAD) ... 3 Process Container for an address space and threads Associated User-mode Process Environment Block (PEB) Primary Access Token Quota, Debug port, Handle Table etc Unique process ID Queued to the Job, global process list and Session list MM structures like the WorkingSet, VAD tree, AWE etc 4 2 Thread Fundamental schedulable entity in the system Represented by ETHREAD that includes a KTHREAD Queued to the process (both E and K thread) IRP list Impersonation Access Token Unique thread ID Associated User-mode Thread Environment Block (TEB) User-mode stack Kernel-mode stack Processor Control Block (in KTHREAD) for CPU state when not running 5 Processes & Threads Internal Data Structures Access Token VAD VAD VAD Process Object Virtual Address Space Descriptors See kernel debugger Handle Table commands: object dt (see next slide) !process object !thread !token !handle !object Thread Thread Thread . Access Token 6 3 Process Block Layout Kernel Process Block (or PCB) Process ID Parent Process ID Dispatcher Header Exit Status Process Page Directory Create and Exit Time Kernel Time EPROCESS User Time Next Process Block Inwwap/Outswap List Entry Quota Block KTHREAD . -

Demystifying Tokens for Securing Enterprise Apis
DEVELOPING AND CONNECTING ISSA Demystifying Tokens for CYBERSECURITY LEADERS GLOBALLY Securing Enterprise APIs Demystifying Tokens for Securing Enterprise APIs By Sandeep Jayashankar – ISSA member Delaware Chapter and Subin Thayyile Kandy – ISSA member Delaware Chapter This article is mainly designed for a software architect to help understand the problems tokens tend to solve, with illustrations of different types of tokens in use. The authors also explain the token implementation methods for an enterprise API mechanism and provide security best practices to be taken care of when implementing the same. Abstract able products, both as a software and a service, to handle the authentication security controls. The security community has Tokens have been the de-facto means that support scalable striven to set many authentication policy definitions, such as and performance-focused security solutions in the current password policies, user lockout policies, captcha frameworks, technological environments. There are currently many op- and provided many scan engines to check the implemented tions and operation modes for anybody thinking of imple- authentication policies. Enterprise organizations have priori- menting a token-based security measure with support of tized their strategic plans concerning security by utilizing the cryptographic mechanisms. With the web-attack landscapes best products to support the applications’ authentication and changing to APIs, and with APIs managed as a decoupled password handling requirements. data handling entity, APIs need to have stringent authori- zation decision engines that ensure an authorized entity re- Implementing single sign-on with compulsory multi-factor quests each data retrieval. This article is mainly designed for authentication sequences has become a de facto for appli- a software architect to help understand the problems tokens cations and web components in an enterprise environment. -
![MS-DTYP]: Windows Data Types](https://docslib.b-cdn.net/cover/3780/ms-dtyp-windows-data-types-1873780.webp)
MS-DTYP]: Windows Data Types
[MS-DTYP]: Windows Data Types Intellectual Property Rights Notice for Open Specifications Documentation . Technical Documentation. Microsoft publishes Open Specifications documentation for protocols, file formats, languages, standards as well as overviews of the interaction among each of these technologies. Copyrights. This documentation is covered by Microsoft copyrights. Regardless of any other terms that are contained in the terms of use for the Microsoft website that hosts this documentation, you may make copies of it in order to develop implementations of the technologies described in the Open Specifications and may distribute portions of it in your implementations using these technologies or your documentation as necessary to properly document the implementation. You may also distribute in your implementation, with or without modification, any schema, IDL’s, or code samples that are included in the documentation. This permission also applies to any documents that are referenced in the Open Specifications. No Trade Secrets. Microsoft does not claim any trade secret rights in this documentation. Patents. Microsoft has patents that may cover your implementations of the technologies described in the Open Specifications. Neither this notice nor Microsoft's delivery of the documentation grants any licenses under those or any other Microsoft patents. However, a given Open Specification may be covered by Microsoft Open Specification Promise or the Community Promise. If you would prefer a written license, or if the technologies described in the Open Specifications are not covered by the Open Specifications Promise or Community Promise, as applicable, patent licenses are available by contacting [email protected]. Trademarks. The names of companies and products contained in this documentation may be covered by trademarks or similar intellectual property rights. -

Join-In Senior Citizens Overcoming Barriers by Joining Fun Activities
Join-In Senior Citizens Overcoming Barriers by Joining Fun Activities AAL Joint Programme: Project No. 031121 Deliverable: 4.2 Design and Implementation of the Join-In platform Date of deliverable: 31-10-12 / Version: 1.0 Lead contractor for this deliverable: Norut Contributors: PAS, HMGU, VAL, ITC, NST Dissemination Level: Public Project Duration: Nov. 2010 – Oct. 2013 Project co-founded by D4.2 Design and Implementation of the Join-In platform Page 2 of 63 Table of Content 1 About Join-In ................................................................................................................ 3 2 Introduction ................................................................................................................... 5 3 Join_in social networking architecture .......................................................................... 7 4 Social Network .............................................................................................................. 8 4.1 Functions ................................................................................................................ 9 4.1.1 Social Contacts ................................................................................................ 9 4.1.2 Calendar and activities ................................................................................... 12 4.1.3 Games and Exergames ................................................................................. 12 4.1.4 Avatar selection ............................................................................................. -
Access Token Created When a User Logs On, This Value Identifies the User and All of the User’S Group Memberships
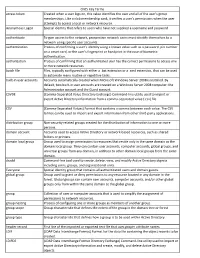
Ch05 Key Terms access token Created when a user logs on, this value identifies the user and all of the user’s group memberships. Like a club membership card, it verifies a user’s permissions when the user attempts to access a local or network resource. Anonymous Logon Special identity that refers to users who have not supplied a username and password. authenticate To gain access to the network, prospective network users must identify themselves to a network using specific user accounts. authentication Process of confirming a user’s identity using a known value such as a password, pin number on a smart card, or the user’s fingerprint or handprint in the case of biometric authentication. authorization Process of confirming that an authenticated user has the correct permissions to access one or more network resources. batch file Files, typically configured with either a .bat extension or a .cmd extension, that can be used to automate many routine or repetitive tasks. built-in user accounts Accounts automatically created when Microsoft Windows Server 2008 is installed. By default, two built-in user accounts are created on a Windows Server 2008 computer: the Administrator account and the Guest account. CSVDE (Comma-Separated Value Directory Exchange) Command-line utility used to import or export Active Directory information from a comma-separated value (.csv) file. CSV (Comma-Separated Values) Format that contains a comma between each value. The CSV format can be used to import and export information from other third-party applications. distribution group Non-security-related groups created for the distribution of information to one or more persons. -

Active Directory Token-Size Calculator User's Guide
Gold Finger Active Directory Token-size Calculator User’s Guide Copyright 2006 – 2019 Paramount Defenses Inc. All rights reserved. Paramount Defenses and Gold Finger are trademarks or registered trademarks of Paramount Defenses Inc. Microsoft, Windows, Windows Server, Azure and Active Directory are the trademarks of Microsoft Corporation. Gold Finger Active Directory Token-size Calculator Contents Introduction …………………………………………………………………………………………………………… 1 1. Installation …………………………………………………………………………………………………………….. 2 2. Getting Started ………………………………………………………………………………………………………. 2 3. Becoming Familiar with Gold Finger’s User-Interface ………………………………………….…. 3 4. Viewing the List of All SIDs Contained in a Domain Account’s Access Token …….….… 4 5. Computing Token-Sizes of All Domain Accounts in an Active Directory Domain …….. 5 6. Exporting Results and Generating PDF Reports ……………………………………………………… 6 7. Using Inbuilt Search ………………………………………………………………………………………………. 6 8. Using Basic Options ……………………………………………………………………………………………….. 7 9. Using Advanced Options ……………………………………………………………………………………….. 7 10. Understanding Domain Specific and Target-type Specific Access Tokens ……………….. 8 11. Obtaining Technical Support .………………..……………………………………………………….……... 9 Active Directory Token-size Calculator Introduction In Active Directory environments where domain user or computer accounts could belong to a large number (i.e. hundreds) of Active Directory security groups, there could be situations where the number of groups to which a domain account belongs exceeds the number of security identifiers (SIDs) that can fit in a Windows access token. In such situations, during logon, when Windows attempts to create an access token for the user, because the number of SIDs exceeds the number that fit in a Windows access token, the system is unable to successfully create an access token for the user, and as a result the user is unable to logon, resulting in an issue generally known as token-bloat. -

The Windows Operating System
T HE W INDOWS O PERATING S YSTEM William Stallings Copyright 2008 This document is an extract from Operating Systems: Internals and Design Principles, Sixth Edition William Stallings Prentice Hall 2008 ISBN-10: 0-13-600632-9 ISBN-13: 978-0-13-600632-9 http://williamstallings.com/OS/OS6e.html M02_STAL6329_06_SE_C02.QXD 2/22/08 7:02 PM Page 80 80 CHAPTER 2 / OPERATING SYSTEM OVERVIEW secondary memory, and other I/O modules. A distributed operating system provides the illusion of a single main memory space and a single secondary memory space, plus other unified access facilities, such as a distributed file system.Although clusters are becoming increasingly popular, and there are many cluster products on the mar- ket, the state of the art for distributed operating systems lags that of uniprocessor and SMP operating systems. We examine such systems in Part Eight. Another innovation in OS design is the use of object-oriented technologies. Object-oriented design lends discipline to the process of adding modular extensions to a small kernel.At the OS level, an object-based structure enables programmers to customize an OS without disrupting system integrity. Object orientation also eases the development of distributed tools and full-blown distributed operating systems. 2.5 MICROSOFT WINDOWS OVERVIEW History The story of Windows begins with a very different OS, developed by Microsoft for the first IBM personal computer and referred to as MS-DOS or PC-DOS. The ini- tial version, DOS 1.0, was released in August 1981. It consisted of 4000 lines of as- sembly language source code and ran in 8 Kbytes of memory using the Intel 8086 microprocessor.