Workshop Program
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Product Engine for Energy-Efficient Execution of Binary Neural Networks Using Resistive Memories
A Product Engine for Energy-Efficient Execution of Binary Neural Networks Using Resistive Memories Joao˜ Vieira∗, Edouard Giacomin∗, Yasir Qureshiy, Marina Zapatery, Xifan Tang∗, Shahar Kvatinskyz, David Atienzay, and Pierre-Emmanuel Gaillardon∗ ∗LNIS, University of Utah, USA yESL, Swiss Federal Institute of Technology Lausanne (EPFL), Switzerland zAndrew and Erna Viterbi Faculty of Electrical Engineering, Technion - Israel Institute of Technology, Israel Abstract—The need for running complex Machine Learning [5], [6] and offloading workload to near-data accelerators [7], (ML) algorithms, such as Convolutional Neural Networks (CNNs), [8]. However, most of these solutions do not comply with the in edge devices, which are highly constrained in terms of limitations of edge devices since they require a significant computing power and energy, makes it important to execute such applications efficiently. The situation has led to the popularization amount of hardware resources to be implemented, which of Binary Neural Networks (BNNs), which significantly reduce is hardly feasible in the context of such energy- and cost- execution time and memory requirements by representing the constrained systems. Furthermore, accelerators do not provide weights (and possibly the data being operated) using only one bit. performance benefits whenever the workload associated to Because approximately 90% of the operations executed by CNNs the dataset is not enough to overcome the communication and BNNs are convolutions, a significant part of the memory transfers consists of fetching the convolutional kernels. Such overhead with main memory [9]. For that, the datasets have to kernels are usually small (e.g., 3×3 operands), and particularly be significantly big, and since edge devices are usually used in BNNs redundancy is expected. -

Connecting Artificial Intelligence (AI) to Internet of Things (Iot) November 11 to 13, 2020
www.formation-continue-unil-epfl.ch 3-day course Connecting Artificial Intelligence (AI) to Internet of Things (IoT) November 11 to 13, 2020 Target audience Organization Top and middle managers wanting • Embedded Systems Laboratory (ESL), Institute of Electrical to learn the fundamentals and Engineering, Ecole Polytechnique Fédérale de Lausanne (EPFL) understand the latest trends of IoT technologies - including edge Overview AI computing - and their industrial applications. Nowadays, every organization needs to understand the opportunities and challenges offered by smart machine Requirements learning devices and IoT connected technologies. High-tech advances in miniaturized, ultra-low power embedded systems, The course will be given in English. in communication protocols and in AI techniques are leading Dates and schedule to disruptive innovations. Established industries are deeply modified. Smart cities, eHealth or Industry 4.0 are part of the • Wednesday, November 11, 2020 new revolution created by Internet of Things (IoT), which now • Thursday, November 12, 2020 includes smart intelligent sensors (also called edge AI computing). • Friday, November 13, 2020 This 3-day course will cover three main themes: Smart machine learning devices that enable edge AI in cloud-based IoT from 9 am to 6 pm (hardware and software designs, AI technologies and power/ energy requirements), Communication for IoT (latest protocols Certification and standards) and complete examples of Industry 4.0, smart A certificate of attendance will be homes and wearable -

Ecocloud E-Newsletter in This Issue: Welcome Message from the Executive Committee in the News 2017 Ecocloud Annual Event Around
EcoCloud e-newsletter May 2017 In this issue: Welcome Message In the News Visiting Scholars New Projects Awards Publications Welcome Message from the Executive Committee Welcome to the 2017 edition of our newsletter. In this edition we bring to you a snapshot of our latest activities and accomplishments by our community members. We started 2017 with the same enthusiasm, energy and momentum we had at the end of 2016 with many new funded projects, sponsored events on campus, two visiting scholars, and a rousing line-up of industry speakers for our upcoming annual event. We look forward to seeing you at the annual event. In the News 2017 EcoCloud Annual Event Around the Corner Please join industry experts from HP Enterprise, Google, IBM, Microsoft, and Xilinx and EcoCloud researchers to share insights on future data and cloud computing platforms on June 12th and 13th, 2017 at the sixth EcoCloud annual event at the Royal Savoy Hotel in Lausanne, Switzerland. You can find more information on the event including agenda and speakers’ information here. ByzCoin to Accelerate Bitcoin Transactions Bryan Ford has developed an innovative and effective solution to counter delays, inconsistencies and attacks encountered by users of the increasingly popular virtual currency Bitcoin. Dubbed ByzCoin, the solution is inspired by protocols such as Practical Byzantine Fault Tolerance (PBFT). It is based on the idea that an active group of Bitcoin miners using novel cryptographic algorithms work collectively on the transaction blocks that, once verified, are added to the ecocloud.ch EcoCloud e-newsletter May 2017 1 blockchain – the Bitcoin network’s public ledger. -

Iccad 2020 Virtual Event
ICCAD 2020 VIRTUAL EVENT NOVEMBER 2 – 5, 2020 ICCAD.COM In cooperation with: special interest group on design automation WELCOME TO THE 39TH ICCAD FROM YUAN XIE ICCAD GENERAL CHAIR Welcome to the 39th edition of the International Conference on Computer- Aided Design! This year, due to the global COVID-19 pandemic, many conferences are forced to make the event work in the online world. Consequently, the ICCAD 2020 Executive Committee decided to move forward with a Virtual Conference due to the continued uncertainty surrounding the COVID-19 situation. Nevertheless, we are very excited to test out this new online edition for the first time in ICCAD’s 39-year history. Even though the virtual events lack the kind of interpersonal communications attendees get from in-person events, a much lower registration fee with no travel overheads may boost the number of participants. A carefully tuned schedule with a virtual platform can make it a true “global” event for anyone around the world to attend ICCAD. We hope you will enjoy this unique virtual experience with the first-ever online ICCAD. Jointly sponsored by IEEE and ACM, ICCAD is the premier forum to explore emerging technology challenges in electronic design automation, present leading-edge R&D solutions, and identify future roadmaps for design automation research areas. The members of the executive committee, the technical program committee, and numerous volunteers have spent the past several months preparing an exciting program for you! This was another strong year for ICCAD in terms of the number of regular paper submissions. We received more than 470 regular paper submissions. -

Adressing Thermal Issues in 3D Stacks in the Nano-Tera CMOSAIC Project
MARCH 2009 fluids offer significant advantages in addressing heat re- Adressing Thermal Issues in 3D Stacks in moval challenges leading to practical 3D systems. CMO- SAIC aims at developing the engineering science base the Nano-Tera CMOSAIC Project that will enable a new state of the art in high density Contributed by Jose L. Ayala (Complutense University of Madrid) electronics cooling. Continuous technical advances are fueling the trend to- Specifically, this project brings together internationally ward more sophisticated and high-performance chip de- recognized experts of leading Swiss universities and in- signs, increasing functionality and clock rates while dustry (EPFL, ETH Zurich and IBM Research Labora- shrinking the feature sizes. Interconnects have not fol- tory in Rüschlikon) to thoroughly investigate this inter- lowed the same scaling curve as transistors, hence they disciplinary problem at different levels (architecture, mi- have become a limiting factor in performance and power crofabrication, liquid cooling, two-phase cooling, nano- consumption. fluids). These experts are joining forces to research the related physics and to develop the necessary ther- One solution to the problem of the rising power con- mal/electronic computational tools/methods. The pro- sumption in interconnects is 3D stacking, which reduces ject includes an intensive experimental program, consist- the length of the communication lines through vertical ing of challenging flow visualizations and heat transfer integration of circuit blocks. However, 3D stacking sub- measurements in microchannel systems of hydraulic di- stantially increases power density due to the placement of ameter often comparable to or smaller than that of a computational units on top of each other. -

Opening Session & Award Presentations
MONDAY, NOVEMBER 18 - 8:30 - 9:00am Opening Session & Award Presentations Room: Almaden 1 & 2 Opening Remarks - IEEE CEDA Early Career Award Jörg Henkel ‑ General Chair ‑ Karlsruhe Institute of Technology (KIT) David Atienza, Assistant Professor of Electrical Engineering and Director of the Embedded Systems Laboratory at EPFL For sustained and outstanding contributions to design methods and tools for Award Presentations multi-processor systems-on-chip (MPSoC), particularly for work on thermal-aware IEEE/ACM William J. McCalla ICCAD Best Paper Award design, low-power architectures and on-chip interconnects synthesis. This award is given in memory of William J. McCalla for his contribution to ICCAD and his CAD technical work throughout his career. IEEE CEDA Early Career Award Front End Zhuo Li, IBM T. J. Watson Research Center 2B.1 Improved SAT-based ATPG: More Constraints, Better Compaction For essential and outstanding contributions to algorithms, methodologies, and soft- Stephan Eggersglüß, Robert Wille, Rolf Drechsler - Univ. of Bremen / DFKI ware for interconnect optimization, physical synthesis, parasitic extraction, testing and simulation. Back End 5B.2 Methodology for Standard Cell Compliance and IEEE CEDA Outstanding Service Contribution Detailed Placement for Triple Patterning Lithography Alan Hu, Univ. of British Columbia Bei Yu, Xiaoqing Xu, Jhih-Rong Gao and David Z. Pan - Univ. of Texas at Austin For significant service to the EDA community as the 2012 ICCAD General Chair ICCAD Ten Year Retrospective Most Influential Paper Award 2013 SIGDA Pioneering Achievement Award This award is being given to the paper judged to be the most influential on research Donald E. Thomas, Dept. of Electrical and Computer Engineering, and industrial practice in computer-aided design of integrated circuits over the ten Carnegie Mellon Univ. -

Temperature-Aware Design and Management for 3D Multi-Core Architectures
Full text available at: http://dx.doi.org/10.1561/1000000032 Temperature-Aware Design and Management for 3D Multi-Core Architectures Mohamed M. Sabry and David Atienza Embedded Systems Lab (ESL) Ecole Polytechnique Fédérale de Lausanne (EPFL) 1015, Lausanne, Switzerland mohamed.sabry@epfl.ch, david.atienza@epfl.ch Boston — Delft Full text available at: http://dx.doi.org/10.1561/1000000032 R Foundations and Trends in Electronic Design Automation Published, sold and distributed by: now Publishers Inc. PO Box 1024 Hanover, MA 02339 United States Tel. +1-781-985-4510 www.nowpublishers.com [email protected] Outside North America: now Publishers Inc. PO Box 179 2600 AD Delft The Netherlands Tel. +31-6-51115274 The preferred citation for this publication is M. M. Sabry and D. Atienza. Temperature-Aware Design and Management for 3D Multi-Core Architectures. Foundations and Trends R in Electronic Design Automation, vol. 8, no. 2, pp. 117–197, 2014. R This Foundations and Trends issue was typeset in LATEX using a class file designed by Neal Parikh. Printed on acid-free paper. ISBN: 978-1-60198-775-4 c 2014 M. M. Sabry and D. Atienza All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, mechanical, photocopying, recording or otherwise, without prior written permission of the publishers. Photocopying. In the USA: This journal is registered at the Copyright Clearance Cen- ter, Inc., 222 Rosewood Drive, Danvers, MA 01923. Authorization to photocopy items for internal or personal use, or the internal or personal use of specific clients, is granted by now Publishers Inc for users registered with the Copyright Clearance Center (CCC). -

PRESS RELEASE DATE 2017 Event Highlights Electronics for the Internet of Things Era and Wearable and Smart Medical Devices
PRESS RELEASE DATE 2017 Event Highlights Electronics for the Internet of Things Era and Wearable and Smart Medical Devices 2017/02/27 DATE 2017 opens doors on March 27 at the SwissTech Convention Center in Lausanne, Switzerland 2017 is a special year for the world’s favourite electronic systems design and test conference, as we celebrate its 20th edition and it will be held for the first time in Switzerland, at the SwissTech Convention Center on the EPFL campus in Lausanne, from March 27 to 31, 2017. On Tuesday, the conference will be opened by the plenary keynote speakers Dr. Arvind Krishna from IBM who will talk about “Design Automation in the Era of AI and IoT: Challenges and Pitfalls” and Dr. Doug Burger from Microsoft to talk about “A New Era of Hardware Microservices in the Cloud”. In addition, a keynote lecture from Prof. Giovanni De Micheli (Professor at EPFL and Director of Nano-Tera.ch) will be given on Tuesday on "Distributed Systems for Health and Environmental Monitoring" within the Nano- Tera.ch initiative. On the same day, the Executive Track, including one Executive Panel Session and three Innovative Technologies & Applications (IT&A) Sessions, offers a series of business panels discussing hot topics. Executive speakers from companies leading the design and automation industry will address some of the complexity issues in electronics design and discuss about the advanced technology challenges and opportunities. A special session is dedicated to Ralph Otten, pioneer of physical design, who prematurely died in an accident. Two Special Days in the programme will focus on areas bringing new challenges to the system design community: Designing Electronics for the Internet of Things Era and Designing Wearable and Smart Medical Devices, each having a full programme of keynotes, panels, tutorials and technical presentations. -

A Semi-Analytical Thermal Modeling Framework for Liquid-Cooled Ics Arvind Sridhar, Member, IEEE,Mohamedm.Sabry,Member, IEEE, and David Atienza, Senior Member, IEEE
IEEE TRANSACTIONS ON COMPUTER-AIDED DESIGN OF INTEGRATED CIRCUITS AND SYSTEMS, VOL. 33, NO. 8, AUGUST 2014 1145 A Semi-Analytical Thermal Modeling Framework for Liquid-Cooled ICs Arvind Sridhar, Member, IEEE,MohamedM.Sabry,Member, IEEE, and David Atienza, Senior Member, IEEE Abstract—With the development of liquid-cooled integrated than conventional air-cooling, liquid cooling also possesses the circuits (ICs) using silicon microchannels, the study of heat potential to increase cooling efficiency and enable energy har- transfer and thermal modeling in liquid-cooled heat sinks has vesting when utilized in the large-scale datacenters. Hence, it is gained interest in the last five years. As a consequence, several touted as a long-term green energy solution for next-generation methodologies on the thermally-aware design of liquid-cooled 2-D/3-D ICs and multiprocessor system-on-chips (MPSoCs) have datacenters [6]. appeared in the literature. A key component in such methodolo- Prototypes of 2-D and 3-D stacked ICs with microchan- gies is a fast and accurate thermal modeling technique that can nel liquid cooling have been built by various research groups be easily interfaced with design optimization tools. Conventional around the world with promising results [3], [7], [8]. An exam- fully numerical techniques, such as finite-element methods, do ple from IBM is shown in Fig. 1, where they have developed a not render themselves to enable such an easy interfacing with 3-D IC emulator with interlayer liquid cooling. Further devel- design tools and their order of complexity is too large for fast opment of this technology and its large-scale use are strongly simulations. -
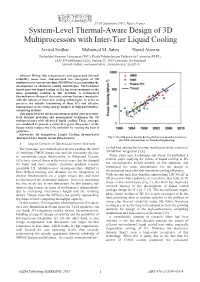
System-Level Thermal-Aware Design of 3D Multiprocessors with Inter-Tier Liquid Cooling
27-29 September 2011, Paris, France System-Level Thermal-Aware Design of 3D Multiprocessors with Inter-Tier Liquid Cooling Arvind Sridhar Mohamed M. Sabry David Atienza Embedded Systems Laboratory (ESL), École Polytechnique Fédérale de Lausanne (EPFL), ELG 130 (Bâtiment ELG), Station 11, 1015 Lausanne, Switzerland. {arvind.sridhar, mohamed.sabry, david.atienza} @epfl.ch Abstract- Rising chip temperatures and aggravated thermal reliability issues have characterized the emergence of 3D multiprocessor system-on-chips (3D-MPSoCs), necessitating the development of advanced cooling technologies. Microchannel based inter-tier liquid cooling of ICs has been envisaged as the most promising solution to this problem. A system-level thermal-aware design of electronic systems becomes imperative with the advent of these new cooling technologies, in order to preserve the reliable functioning of these ICs and effective management of the rising energy budgets of high-performance computing systems. This paper reviews the recent advances in the area of system- level thermal modeling and management techniques for 3D multiprocessors with advanced liquid cooling. These concepts are combined to present a vision of a green data-center of the future which reduces the CO2 emissions by reusing the heat it generates. Keywords- 3D Integration, Liquid Cooling, System-Level Thermal Aware Design, Green Data-Centers. Fig. 1: On chip power density during the last two decades (Courtesy: [6], IEEE Special Issue on Thermal Engineering) I. LIQUID COOLING OF MICROELECTRONIC SYSTEMS The economic and technological drivers pushing the trend cooled heat sinking has become insufficient in the context of of shrinking CMOS feature size and the increasing die size 3D-MPSoC integration [3,4]. -

Ayse Kivilcim Coskun
Ayse K. Coskun Boston University, Electrical and Computer Engineering Department 8 Saint Mary’s Street, Boston, MA 02215 USA -- Phone: 617-358-3641 -- E-mail: [email protected] Web: Personal Website, Research Group (PeacLab), Google Scholar Education PhD Computer Science and Engineering, University of California, San Diego 2009 MS Computer Science and Engineering, University of California, San Diego 2006 BS Microelectronics Engineering, Minor Degree in Physics, Sabanci University, Turkey 2003 Research Interests Energy-efficient computing, power and thermal management of computing systems, novel computer architectures (e.g., enabled by 3D stacking or on-chip silicon photonics), embedded system design, cloud and HPC analytics with applied machine learning methods, data center resource and energy management. Work Experience Boston University, Boston, MA Associate Professor in Electrical and Computer Engineering Department May 2015-Present Assistant Professor September 2009-May 2015 Classes taught: Introduction to Embedded Systems (EC535), Introduction to Software Engineering (EC327), Advanced Computing Systems & Architecture (EC700). 7 PhD alumni, currently advising 9 PhD students. Hosted and advised 20+ undergraduate researchers and 9 high school students at the Performance and Energy Aware Computing Laboratory (PeacLab). University of California San Diego, San Diego, CA Graduate Student Researcher in Computer Science and Engineering Department 2003-2009 Advisor: Prof. Tajana Simunic Rosing PhD thesis: “Efficient Thermal Management for Multiprocessor Systems”. Sun Microsystems, San Diego, CA (now Oracle) Intern in Systems Dynamics Characterization and Control Team 2006-2009 Supervisor: Dr. Kenny C. Gross Conducted research on temperature and reliability modeling / management methods, monitoring real-time system behavior, and runtime analysis. Co-authored 6 US patents. Awards and Honors Participant at the National Academy of Engineering’s Frontiers of Engineering Symposium, September 2019. -

CEDA Standards Committee Nominations Requested for EDA
AUGUST 200 8 Dr. Robert K. Brayton, Cadence Distinguished Professor CEDA Standards Committee of Electrical Engineering and Computer Science at the The Council of EDA Standards Committee (C-EDA SC) University of California at Berkeley, was the 2007 award is to promote the development of Standards in the EDA winner. Prof. Brayton won the Phil Kaufman Award for industry. Such standards are beneficial to the IC design- his demonstrable impact on the field of electronic design ers and developers and users of automation tools in this through contributions in Electronic Design Automation industry since they provide a mechanism for defining (EDA). common semantics. This committee will be represented The Kaufman Award, jointly sponsored by CEDA and by EDA, Consortiums, Semiconductor Companies and the EDA Consortium, honors individuals who have associated standards groups. The C-EDA SC acts as the made a demonstrable impact on the field of EDA in administrator for the Working Groups under it which business, industry direction and promotion, technology develop and maintain Standards. and engineering, or education and mentoring. It was The C-EDA SC is governed by a chairman and a steering established in 1994 in honor of deceased EDA industry committee. The steering committee is composed of the pioneer Phil Kaufman, who turned innovative technolo- chair-persons of the Working Groups under the C-EDA gies like silicon compilation and emulation into business- SC plus explicitly voted in members to include senior es that have benefited electronic designers. management in EDA, representatives from consortiums, Please, visit http://www.edac.org/about_kaufman_award.jsp or representative from DASC and/or other interested par- http://www.ieee-ceda.org/awards.