Windows CMD Command Syntax | SS64.Com
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Užitečné Postupy Pro Windows a Office Nepublikované V Oficiální Literatuře Artur Cimbálník
UNIVERZITA PARDUBICE Fakulta elektrotechniky a informatiky Užitečné postupy pro Windows a Office nepublikované v oficiální literatuře Artur Cimbálník Bakalářská práce 2011 Prohlášení autora Prohlašuji, ţe jsem tuto práci vypracoval samostatně. Veškeré literární prameny a informace, které jsem v práci vyuţil, jsou uvedeny v seznamu pouţité literatury. Byl jsem seznámen s tím, ţe se na moji práci vztahují práva a povinnosti vyplývající ze zákona č. 121/2000 Sb., autorský zákon, zejména se skutečností, ţe Univerzita Pardubice má právo na uzavření licenční smlouvy o uţití této práce jako školního díla podle § 60 odst. 1 autorského zákona, a s tím, ţe pokud dojde k uţití této práce mnou nebo bude poskytnuta licence o uţití jinému subjektu, je Univerzita Pardubice oprávněna ode mne poţadovat přiměřený příspěvek na úhradu nákladů, které na vytvoření díla vynaloţila, a to podle okolností aţ do jejich skutečné výše. Souhlasím s prezenčním zpřístupněním své práce v Univerzitní knihovně. V Pardubicích dne 29. 04. 2011 Artur Cimbálník Poděkování Tímto bych chtěl poděkovat doc. Ing Milanu Javůrkovi, CSc., vedoucímu mé bakalářské práce za pomoc při shánění materiálu a jeho rady při psaní tohoto textu. Anotace Práce se zabývá testováním postupů racionalizujících práci ve Windows a programech Microsoft Office. Jsou zde popsány jednotlivé pracovní postupy doplněné grafickými obrazovkami a popisem dané problematiky. Dále hodnotí jednotlivé verze kancelářských balíků Microsoft Office. Klíčová slova Office, Word, Excel, Windows, tipy, postupy, rady Title Useful procedures for Windows and Office unpublished in the official literature. Annotation Bachelor thesis deals with the testing of procedures rationalizing work in Windows and Microsoft Office. There are describing individual work procedures with graphic screens. -

Windows 7 Operating Guide
Welcome to Windows 7 1 1 You told us what you wanted. We listened. This Windows® 7 Product Guide highlights the new and improved features that will help deliver the one thing you said you wanted the most: Your PC, simplified. 3 3 Contents INTRODUCTION TO WINDOWS 7 6 DESIGNING WINDOWS 7 8 Market Trends that Inspired Windows 7 9 WINDOWS 7 EDITIONS 10 Windows 7 Starter 11 Windows 7 Home Basic 11 Windows 7 Home Premium 12 Windows 7 Professional 12 Windows 7 Enterprise / Windows 7 Ultimate 13 Windows Anytime Upgrade 14 Microsoft Desktop Optimization Pack 14 Windows 7 Editions Comparison 15 GETTING STARTED WITH WINDOWS 7 16 Upgrading a PC to Windows 7 16 WHAT’S NEW IN WINDOWS 7 20 Top Features for You 20 Top Features for IT Professionals 22 Application and Device Compatibility 23 WINDOWS 7 FOR YOU 24 WINDOWS 7 FOR YOU: SIMPLIFIES EVERYDAY TASKS 28 Simple to Navigate 28 Easier to Find Things 35 Easy to Browse the Web 38 Easy to Connect PCs and Manage Devices 41 Easy to Communicate and Share 47 WINDOWS 7 FOR YOU: WORKS THE WAY YOU WANT 50 Speed, Reliability, and Responsiveness 50 More Secure 55 Compatible with You 62 Better Troubleshooting and Problem Solving 66 WINDOWS 7 FOR YOU: MAKES NEW THINGS POSSIBLE 70 Media the Way You Want It 70 Work Anywhere 81 New Ways to Engage 84 INTRODUCTION TO WINDOWS 7 6 WINDOWS 7 FOR IT PROFESSIONALS 88 DESIGNING WINDOWS 7 8 WINDOWS 7 FOR IT PROFESSIONALS: Market Trends that Inspired Windows 7 9 MAKE PEOPLE PRODUCTIVE ANYWHERE 92 WINDOWS 7 EDITIONS 10 Remove Barriers to Information 92 Windows 7 Starter 11 Access -

Bulk Data Migration Using Robocopy
Bulk Data Migration Using Robocopy Created by: Nasuni Support Last update: 6/14/2011 Contents Overview...................................................................................................................................................................... 2 Using Robocopy to copy data to the Nasuni Filer....................................................................................... 2 2011 © Nasuni Corporation. All Rights Reserved Resizing the Cache and Snapshots Disks in Nasuni Filer v2.7 Robocopy and the Nasuni Filer cache ............................................................................................................. 2 Conclusion ................................................................................................................................................................... 3 Overview The information in this document applies to Nasuni Filer 2.x versions. It explains how to use Robocopy, a Microsoft Windows tool, to migrate data from a Windows file server to the Nasuni Filer. Robocopy has been bundled with Windows operating systems since Vista and Server 2008. Using Robocopy to copy data to the Nasuni Filer Robocopy is a Windows command line tool. To migrate data to the Nasuni Filer using Robocopy follow the steps below. 1. Identify the data set you want to migrate to the Nasuni Filer 2. Create/locate a share on the Nasuni Filer to write your data set to 3. Run cmd.exe 4. Run the command below from the source server’s command line. robocopy (path to source data) (path to Filer share) -

Mining of Massive Datasets
Mining of Massive Datasets Anand Rajaraman Kosmix, Inc. Jeffrey D. Ullman Stanford Univ. Copyright c 2010, 2011 Anand Rajaraman and Jeffrey D. Ullman ii Preface This book evolved from material developed over several years by Anand Raja- raman and Jeff Ullman for a one-quarter course at Stanford. The course CS345A, titled “Web Mining,” was designed as an advanced graduate course, although it has become accessible and interesting to advanced undergraduates. What the Book Is About At the highest level of description, this book is about data mining. However, it focuses on data mining of very large amounts of data, that is, data so large it does not fit in main memory. Because of the emphasis on size, many of our examples are about the Web or data derived from the Web. Further, the book takes an algorithmic point of view: data mining is about applying algorithms to data, rather than using data to “train” a machine-learning engine of some sort. The principal topics covered are: 1. Distributed file systems and map-reduce as a tool for creating parallel algorithms that succeed on very large amounts of data. 2. Similarity search, including the key techniques of minhashing and locality- sensitive hashing. 3. Data-stream processing and specialized algorithms for dealing with data that arrives so fast it must be processed immediately or lost. 4. The technology of search engines, including Google’s PageRank, link-spam detection, and the hubs-and-authorities approach. 5. Frequent-itemset mining, including association rules, market-baskets, the A-Priori Algorithm and its improvements. 6. -

Run-Commands-Windows-10.Pdf
Run Commands Windows 10 by Bettertechtips.com Command Action Command Action documents Open Documents Folder devicepairingwizard Device Pairing Wizard videos Open Videos Folder msdt Diagnostics Troubleshooting Wizard downloads Open Downloads Folder tabcal Digitizer Calibration Tool favorites Open Favorites Folder dxdiag DirectX Diagnostic Tool recent Open Recent Folder cleanmgr Disk Cleanup pictures Open Pictures Folder dfrgui Optimie Drive devicepairingwizard Add a new Device diskmgmt.msc Disk Management winver About Windows dialog dpiscaling Display Setting hdwwiz Add Hardware Wizard dccw Display Color Calibration netplwiz User Accounts verifier Driver Verifier Manager azman.msc Authorization Manager utilman Ease of Access Center sdclt Backup and Restore rekeywiz Encryption File System Wizard fsquirt fsquirt eventvwr.msc Event Viewer calc Calculator fxscover Fax Cover Page Editor certmgr.msc Certificates sigverif File Signature Verification systempropertiesperformance Performance Options joy.cpl Game Controllers printui Printer User Interface iexpress IExpress Wizard charmap Character Map iexplore Internet Explorer cttune ClearType text Tuner inetcpl.cpl Internet Properties colorcpl Color Management iscsicpl iSCSI Initiator Configuration Tool cmd Command Prompt lpksetup Language Pack Installer comexp.msc Component Services gpedit.msc Local Group Policy Editor compmgmt.msc Computer Management secpol.msc Local Security Policy: displayswitch Connect to a Projector lusrmgr.msc Local Users and Groups control Control Panel magnify Magnifier -

Linux Administrators Security Guide LASG - 0.1.1
Linux Administrators Security Guide LASG - 0.1.1 By Kurt Seifried ([email protected]) copyright 1999, All rights reserved. Available at: https://www.seifried.org/lasg/. This document is free for most non commercial uses, the license follows the table of contents, please read it if you have any concerns. If you have any questions email [email protected]. A mailing list is available, send an email to [email protected], with "subscribe lasg-announce" in the body (no quotes) and you will be automatically added. 1 Table of contents License Preface Forward by the author Contributing What this guide is and isn't How to determine what to secure and how to secure it Safe installation of Linux Choosing your install media It ain't over 'til... General concepts, server verses workstations, etc Physical / Boot security Physical access The computer BIOS LILO The Linux kernel Upgrading and compiling the kernel Kernel versions Administrative tools Access Telnet SSH LSH REXEC NSH Slush SSL Telnet Fsh secsh Local YaST sudo Super Remote Webmin Linuxconf COAS 2 System Files /etc/passwd /etc/shadow /etc/groups /etc/gshadow /etc/login.defs /etc/shells /etc/securetty Log files and other forms of monitoring General log security sysklogd / klogd secure-syslog next generation syslog Log monitoring logcheck colorlogs WOTS swatch Kernel logging auditd Shell logging bash Shadow passwords Cracking passwords John the ripper Crack Saltine cracker VCU PAM Software Management RPM dpkg tarballs / tgz Checking file integrity RPM dpkg PGP MD5 Automatic -

Profileunity Release Notes
Release Notes ProfileUnity™ and ProfileUnity FlexApp™ Change Log/Release Notes Version Table V 6.8.4.7654, RELEASED DECEMBER 16TH, 2020 .................................................................................................. 2 V 6.8.4.7647, RELEASED DECEMBER 9TH, 2020 .................................................................................................... 6 V 6.8.3.7468 R2, RELEASED JUNE 17 TH, 2020 .................................................................................................. 17 V 6.8.3.7311, RELEASED JANUARY 8TH, 2020 .................................................................................................... 25 V 6.8.2.7074, RELEASED MAY 17TH, 2019 ........................................................................................................ 35 V 6.8.1.7044, RELEASED APRIL 17TH, 2019 ....................................................................................................... 40 V 6.8.0.6886, RELEASED NOVEMBER 28TH, 2018 ............................................................................................... 48 V 6.7.7.6701, RELEASED MAY 8TH, 2018 ........................................................................................................... 57 V 6.7.6.6684, RELEASED APRIL 23RD, 2018 ....................................................................................................... 61 V 6.7.5.6663, RELEASED APRIL 4TH, 2018 ......................................................................................................... 65 V 6.7.0.6422, -

Preparation of Papers in Two-Column Format
Protecting Media Production Companies against Ransomware Rob Gonsalves Avid Technology, Inc. Burlington Massachusetts [email protected] Abstract - Ransomware, a type of malicious software designed to block access to digital assets until a sum of money is paid, represents a growing threat for media production companies, as digital media assets are a valued target for hackers. To protect their media assets and mitigate the risk of these types of attacks, companies can implement a set of security policies, procedures and systems. Deploying and operating Disaster Recovery (DR) systems with specific safeguards against ransomware will help companies retrieve valuable files without having to pay FIGURE 1 - INITIAL RANSOMWARE ATTACK cyber-criminals. This paper will discuss the growing threat of ransomware to media companies and cover the key The initial attack often comes when a user inadvertently concepts for understanding and building security and DR downloads and installs malware from a website. After systems with specific safeguards against ransomware. installation, the ransomware quietly searches for and Using these techniques, critical business functions can encrypts files. Its goal is to stay below the radar until it can continue in the event of an attack. find and encrypt all of the files that could be of value to the user. By the time the company is presented with the RANSOMWARE malware’s message with the ransom demand, the damage has already been done [2]. Ransomware is a form of malware that encrypts data files and holds these files for ransom. After the initial infection, the malware begins encrypting files on local drives, shared storage, and potentially other computers on the network. -

ETS4P4 Terminal Server
ETS4P4 Terminal Server Installation Guide Thank you for purchasing this Lantronix ETS Ethernet Terminal Server. As the newest addition to our successful Ethernet terminal server family, the ETS uses software for multiprotocol Ethernet connections that has over 5 years of real-world feedback and de- velopment behind it. Lantronix is constantly improving the capabilities of our prod- ucts, and we encourage you to take advantage of new features through our FREE software upgrades (available via ftp over the Internet or BBS.) Our Flash ROM products, including this ETS, provide the sim- plest means for upgrades and installation. I hope you find this manual easy to use, and thorough in its explanation of the power- ful features you can now access on your network. Brad Freeburg President Contents 1 Introduction Overview...........................................................................1-1 Configuration ................................................1-1 Software ..........................................................1-2 About the Manuals ..........................................................1-2 2 Installation Overview...........................................................................2-1 ETS Components..............................................................2-1 Installation ........................................................................2-2 Selecting a Location for the ETS ..................2-2 Connecting to the Ethernet...........................2-2 Connecting a Terminal..................................2-3 -

Program Name Run Command About Windows Winver Add a Device
List of Run Commands in Win7/8 to Windows Managment By Shree Krishna Maharjan in some commands need to use .msc Program Name Run Command About Windows winver Add a Device devicepairingwizard Add Hardware Wizard hdwwiz Advanced User Accounts netplwiz Authorization Manager azman Backup and Restore sdclt Bluetooth File Transfer fsquirt Calculator calc Certificates certmgr Change Computer Performance Settings systempropertiesperformance Change Data Execution Prevention Settings systempropertiesdataexecutionprevention Change Printer Settings printui Character Map charmap ClearType Tuner cttune Color Management colorcpl Command Prompt cmd Component Services comexp Component Services dcomcnfg Computer Management compmgmt.msc Computer Management compmgmtlauncher Connect to a Network Projector netproj Connect to a Projector displayswitch Control Panel control Create A Shared Folder Wizard shrpubw Create a System Repair Disc recdisc Credential Backup and Restore Wizard credwiz Data Execution Prevention systempropertiesdataexecutionprevention Default Location locationnotifications Device Manager devmgmt.msc Device Pairing Wizard devicepairingwizard Diagnostics Troubleshooting Wizard msdt Digitizer Calibration Tool tabcal DirectX Diagnostic Tool dxdiag Disk Cleanup cleanmgr Disk Defragmenter dfrgui Disk Management diskmgmt.msc Display dpiscaling Display Color Calibration dccw Display Switch displayswitch DPAPI Key Migration Wizard dpapimig Driver Verifier Manager verifier Ease of Access Center utilman EFS REKEY Wizard rekeywiz Encrypting File System -
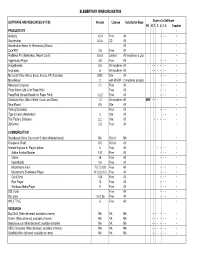
Elementary Windows Matrix
ELEMENTARY WINDOWS MATRIX SOFTWARE AND RESOURCES 8/17/05 Version License Installation Base Access to Software PK K 1 2 3 4 5 Teacher PRODUCTIVITY • Audacity 1.2.4 Free All • • • • Boardmaker 5.3.6 CD All • Boardmaker Addon for Elementary Schools All • Cute PDF 2.6 Free All • FileMaker Pro (Networked, Report Cards) 5.0v3 Limited AV machines & Lab • Hyperstudio Player 4.5 Free All • • • • ImageBlender 2.5 All machines All • • • • • • • • Inspiration 8 All machines All • • • • • • • Microsoft Office (Word, Excel, Access, PP, Publisher) 2000 Site All • • • • MovieMaker 2 with WinXP 2 machines on carts • Netscape Composer 7.1 Free All • • • • Photo Album add-in for PowerPoint Free All • • • • PowerTalk (Screen Reader for Power Point) 1.2.2 Free All • • • • Scholastic Keys (Max's Write, Count, and Show) 1.2 All machines All MW • • • • SmartBoard 9.5 Site All • Talking Calculator Free All • • • • Type to Learn (Networked) 3 Site All • • • Tool Factory Database 2.2 Site All • • • • • • ZipCentral 2.6 Free All • COMMUNICATION Blackboard Online Classroom Builder (Web-delivered) NA District NA • Groupwise Client 6.5 District All • Internet Explorer w. Plugins below: 6 Free All • • • • • Adobe Acrobat Reader 7.07 Free All • • • • Chime v6 Free All • • • • HyperStudio 4.5 Free All Macromedia Flash 7 (7.0.19.0) Free All • • • • Macromedia Shockwave Player 10 (0.0.21.0) Free All • • • • QuickTime 7.04 Free All • • • • Real Player 10 Free All • • • • Windows Media Player 9 Free All • • • • SOL Fonts Free All • • • • Sun Java 1.5.0_06 Free All • • • • -

RTL-To-Gates Synthesis Using Synopsys Design Compiler
RTL-to-Gates Synthesis using Synopsys Design Compiler CS250 Tutorial 5 (Version 091210b) September 12, 2010 Yunsup Lee In this tutorial you will gain experience using Synopsys Design Compiler (DC) to perform hardware synthesis. A synthesis tool takes an RTL hardware description and a standard cell library as input and produces a gate-level netlist as output. The resulting gate-level netlist is a completely structural description with standard cells only at the leaves of the design. Internally, a synthesis tool performs many steps including high-level RTL optimizations, RTL to unoptimized boolean logic, technology independent optimizations, and finally technology mapping to the available standard cells. Good RTL designers will familiarize themselves with the target standard cell library so that they can develop an intuition on how their RTL will be synthesized into gates. In this tutorial you will use Synopsys Design Compiler to elaborate RTL, set optimization constraints, synthesize to gates, and prepare various area and timing reports. You will also learn how to read the various DC text reports and how to use the graphical Synopsys Design Vision tool to visualize the synthesized design. Synopsys provides a library called Design Ware which includes highly optimized RTL for arithmetic building blocks. DC can automatically determine when to use Design Ware components and it can then efficiently synthesize these components into gate-level implementations. In this tutorial you will learn more about what Design Ware components are available and how to best encourage DC to use them. The following documentation is located in the course locker (~cs250/manuals) and provides ad- ditional information about Design Compiler, Design Vision, the Design Ware libraries, and the Synopsys 90nm Standard Cell Library.