ICS 153 Introduction to Computer Networks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Findings of a Comparison of Five Filing Protocols
Rochester Institute of Technology RIT Scholar Works Theses 1991 Findings of a comparison of five filing protocols R. Elayne McFaul Follow this and additional works at: https://scholarworks.rit.edu/theses Recommended Citation McFaul, R. Elayne, "Findings of a comparison of five filing protocols" (1991). Thesis. Rochester Institute of Technology. Accessed from This Thesis is brought to you for free and open access by RIT Scholar Works. It has been accepted for inclusion in Theses by an authorized administrator of RIT Scholar Works. For more information, please contact [email protected]. Rochester Institute of Technology School of Computer Science and Technology Findings of a Comparison of Five Filing Protocols May 1991 R. Elayne McFaul A thesis, submitted to the Faculty of the School of Computer Science and Technology, in partial fulfillment of the requirements for the degree of Master of Science in Computer Science. Approved by: Susan M. Armstrong Peter A. Crean James Heliotis Charles H. Russell I, Elayne McFaul, prefer to be contacted each time a request for reproduction of this thesis is made. I can be reached in one of the following ways: Xerox Corporation 800 Phillips Road 128-53E Webster, NY 14580 716-422-4328 mcfaul.wbstl [email protected] Table of Contents Abstract Key Words and Phrases Computing Review Subject Codes 1. Introduction 1 1.1 Literature Review 4 1.2 Thesis Goal Statement 6 2. General Protocol Descriptions 2.1 FTAM 7 2.2 FTP 11 2.3 UNIX rep 13 2.4 XNS Filing 16 2.5 NFS 19 3. Protocol Design Descriptions 23 3.1 Exported Interface 24 3.2 Concurrency Control 36 3.3 Access Control 40 3.4 Error Recovery 45 3.5 Performance 48 4. -

Xerox 4890 Highlight Color Laser Printing System Product Reference
XEROX Xerox 4890 HighLight Color Laser Printing System Product Reference Version 5.0 November 1994 720P93720 Xerox Corporation 701 South Aviation Boulevard El Segundo, California 90245 ©1991, 1992, 1993, 1994 by Xerox Corporation. All rights reserved. Copyright protection claimed includes all forms and matters of copyrightable material and information now allowed by statutory or judicial law or hereinafter granted, including without limitation, material generated from the software programs which are displayed on the screen such as icons, screen displays, looks, etc. November 1994 Printed in the United States of America. Publication number: 721P82591 Xerox® and all Xerox products mentioned in this publication are trademarks of Xerox Corporation. Products and trademarks of other companies are also acknowledged. Changes are periodically made to this document. Changes, technical inaccuracies, and typographic errors will be corrected in subsequent editions. This book was produced using the Xerox 6085 Professional Computer System. The typefaces used are Optima, Terminal, and monospace. Table of contents 1. LPS fundamentals 1-1 Electronic printing 1-1 Advantages 1-1 Highlight color 1-2 Uses for highlight color in your documents 1-2 How highlight color is created 1-2 Specifying 4890 colors 1-3 Color-related software considerations 1-4 Adding color to line printer and LCDS data streams 1-4 Adding color to Interpress and PostScript data streams 1-5 Adding color to forms 1-6 Fonts 1-8 Acquiring and loading fonts 1-9 LPS production process overview 1-9 Ink referencing 1-10 Unformatted data 1-10 Formatted data 1-11 4890 HighLight Color LPS major features 1-11 4890 feature reference 1-12 LPS connection options 1-12 System controller 1-13 Optional peripheral cabinet 1-13 Printer 1-13 Paper handling 1-14 Forms 1-15 Fonts 1-15 Printed format 1-15 Highlight color 1-16 Types of output 1-16 DFA/Segment Management 1-16 SCSI System Disk/Floppy Disk 1-18 Color Enhancements 1-18 XEROX 4890 HIGHLIGHT COLOR LPS PRODUCT REFERENCE iii TABLE OF CONTENTS 2. -

Teach Yourself TCP/IP in 14 Days, Second Edition
Teach Yourself TCP/IP in 14 Days Second Edition Preface to Second Edition About the Author Overview Introduction 1. Open Systems, Standards, and Protocols 2. TCP/IP and the Internet 3. The Internet Protocol (IP) 4. TCP and UDP 5. Gateway and Routing Protocols 6. Telnet and FTP 7. TCP/IP Configuration and Administration Basics 8. TCP/IP and Networks 9. Setting Up a Sample TCP/IP Network: Servers 10. Setting Up a Sample TCP/IP Network: DOS and Windows Clients 11. Domain Name Service 12. Network File System and Network Information Service 13. Managing and Troubleshooting TCP/IP 14. The Socket Programming Interface Appendix A: Acronyms and Abbreviations Appendix B: Glossary Appendix C: Commands Appendix D: Well-Known Port Numbers Appendix E: RFCs Appendix F: Answers to Quizzes This document was produced using a BETA version of HTML Transit 2 Teach Yourself TCP/IP in 14 Days, Second Edition The second edition of Teach Yourself TCP/IP in 14 Days expands on the very popular first edition, bringing the information up-to-date and adding new topics to complete the coverage of TCP/IP. The book has been reorganized to make reading and learning easier, as well as to provide a more logical approach to the subject. New material in this edition deals with installing, configuring, and testing a TCP/IP network of servers and clients. You will see how to easily set up UNIX, Linux, and Windows NT servers for all popular TCP/IP services, including Telnet, FTP, DNS, NIS, and NFS. On the client side, you will see how to set up DOS, Windows, Windows 95, and WinSock to interact with a server. -

Cisco IOS Software Feature Removal
Cisco IOS Software Feature Removal Feature Overview The Cisco IOS Software Feature Removal feature is an engineering project to permanently remove selected legacy features (or components) from the IOS code. These features will not be available in future releases of Cisco IOS software. The legacy features that have been removed as of Release 12.2(13)T are as follows: • AppleTalk EIGRP • Apollo Domain • Banyan VINES • Exterior Gateway Protocol • HP Probe • Interior Gateway Routing Protocol • Next Hop Resolution Protocol for IPX • Novell Link-State Protocol • Simple Multicast Routing Protocol for AppleTalk • Xerox Network Systems The legacy features that have been removed as of Release 12.2(15)T are as follows: • LAN Extension • Netware Asychronous Services Interface Protocol • Xremote This feature module lists the commands that have been removed from or modified in Cisco IOS software with the removal of a specified feature. Note Commands that have been modified may not all be listed in this document. Americas Headquarters: Cisco Systems, Inc., 170 West Tasman Drive, San Jose, CA 95134-1706 USA Cisco IOS Software Feature Removal Feature Overview AppleTalk EIGRP The following commands have been removed from or modified in Cisco IOS software with the removal of the AppleTalk EIGRP feature. Please note that not all commands that may have been modified are listed here: • appletalk eigrp active-time • appletalk eigrp-bandwidth-percentage • appletalk eigrp log-neighbor-changes • appletalk eigrp-splithorizon • appletalk eigrp-timers • appletalk -

The Networker's Guide to Appletalk, IPX, and Netbios
03 9777 CH03 5/21/01 3:42 PM Page 85 3 The Networker’s Guide to AppleTalk, IPX, and NetBIOS UNTIL THE EARLY 1990S,TCP/IP WAS REALLY ONLY PREVALENT in large govern- ment and research facilities where UNIX and other supercomputing operating systems used it as a common network communications protocol.When PCs came into the picture, they were not networked. Rather, they were used either as front-ends to big micro or mainframe systems (IBM was a big fan of this approach) or as standalone sys- tems. In the early 1980s, as PCs grew in number and in performance, three strategies emerged to provide PCs with networking services:AppleTalk, Novell NetWare, and IBM’s NetBIOS. The goal of this chapter is to give you an understanding of the various protocols that make up the protocol suites and the roles they perform. It is not intended to explain how to design, set up, and manage a network. Chapter 7,“Introduction to Cisco Routers,” and Chapter 10,“Configuring IP Routing Protocols on Cisco Routers,” discuss configuration issues for these protocols. Because NetBIOS is a ses- sion layer protocol rather than a protocol suite, it will be described in the context of its operational behaviors at the end of this chapter. 03 9777 CH03 5/21/01 3:42 PM Page 86 86 Chapter 3 The Networker’s Guide to AppleTalk, IPX, and NetBIOS AppleTalk AppleTalk was an outgrowth of the Apple Macintosh computing platform. First intro- duced in 1984 and updated in 1989, it was designed to provide the Macintosh with a cohesive distributed client/server networking environment.AppleTalk, -

Cabletron Systems Ethernet Technology Guide
Cabletron Systems ETHERNET TECHNOLOGY GUIDE Notice Cabletron Systems reserves the right to make changes in specifications and other information contained in this document without prior notice. The reader should in all cases consult Cabletron Systems to determine whether any such changes have been made. The hardware, firmware, or software described in this manual is subject to change without notice. IN NO EVENT SHALL CABLETRON SYSTEMS BE LIABLE FOR ANY INCIDENTAL, INDIRECT, SPECIAL, OR CONSEQUENTIAL DAMAGES WHATSOEVER (INCLUDING BUT NOT LIMITED TO LOST PROFITS) ARISING OUT OF OR RELATED TO THIS MANUAL OR THE INFORMATION CONTAINED IN IT, EVEN IF CABLETRON SYSTEMS HAS BEEN ADVISED OF, KNOWN, OR SHOULD HAVE KNOWN, THE POSSIBILITY OF SUCH DAMAGES. Copyright 1997 by Cabletron Systems, Inc. All rights reserved. Printed in the United States of America. Order Number: 9031913-01 April 1997 Cabletron Systems, Inc. P.O. Box 5005 Rochester, NH 03866-5005 Cabletron Systems, SPECTRUM, BRIM, DNI, FNB, INA, Integrated Network Architecture, LANVIEW, LANVIEW Secure, Multi Media Access Center, and MicroMMAC are registered trademarks, and Bridge/Router Interface Modules, BRIM-A100, CXRMIM, Desktop Network Interface, Distributed LAN Monitoring, Distributed Network Server, DLM, EFDMIM, EMM-E6, EMME, EPIM, EPIM-3PS, EPIM-A, EPIM-C, EPIM-F1, EPIM-F2, EPIM-F3, EPIM-T, EPIM-T1, EPIM-X, ESXMIM, ETSMIM, ETWMIM, FDCMIM-04, FDCMIM-08, FDMMIM, FDMMIM-04, Flexible Network Bus, FOMIM, FORMIM, HubSTACK, IRBM, IRM, IRM-2, IRM-3, Media Interface Module, MIM, MMAC, MMAC-3, MMAC-3FNB, MMAC-5, MMAC-5FNB, MMAC-8, MMAC-8FNB, MMAC-M8FNB, MMAC-Plus, MRX, MRXI, MRXI-24, MultiChannel, NB20E, NB25E, NB30, NB35, NBR-220/420/620, RMIM, SecureFast Switching, SecureFast Packet Switching, SFPS, SPECTRUM Element Manager, SPECTRUM for Open Systems, TPMIM, TPMIM-22, TPMIM-T1, TPRMIM, TPRMIM-36, TPT-T, TRBMIM, TRMM-2, and TRMMIM are trademarks of Cabletron Systems, Inc. -

Computer Networking : Principles, Protocols and Practice Release 0.25
Computer Networking : Principles, Protocols and Practice Release 0.25 Olivier Bonaventure October 30, 2011 Saylor URL: http://www.saylor.org/courses/cs402/ The Saylor Foundation Saylor URL: http://www.saylor.org/courses/cs402/ The Saylor Foundation Contents 1 Preface 3 2 Introduction 5 2.1 Services and protocols........................................ 11 2.2 The reference models ........................................ 20 2.3 Organisation of the book ....................................... 25 3 The application Layer 27 3.1 Principles ............................................... 27 3.2 Application-level protocols ..................................... 32 3.3 Writing simple networked applications ............................... 55 3.4 Summary ............................................... 61 3.5 Exercises ............................................... 61 4 The transport layer 67 4.1 Principles of a reliable transport protocol .............................. 67 4.2 The User Datagram Protocol ..................................... 87 4.3 The Transmission Control Protocol ................................. 89 4.4 Summary ...............................................113 4.5 Exercises ...............................................114 5 The network layer 127 5.1 Principles ...............................................127 5.2 Internet Protocol ...........................................140 5.3 Routing in IP networks ........................................170 5.4 Summary ...............................................195 5.5 Exercises ...............................................195 -

Xerox Network Systems
CHAPTER33 Chapter Goals • Introduce the XNS protocol, used primarily by numerous networking vendors. • Discuss the structures and functioning of this protocol, from its introduction in the late 1970s to its current form. Xerox Network Systems Background The Xerox Network Systems (XNS) protocols were created by the Xerox Corporation in the late 1970s and early 1980s. They were designed to be used across a variety of communication media, processors, and office applications. Several XNS protocols resemble the Internet Protocol (IP) and Transmission Control Protocol (TCP) entities developed by the Defense Advanced Research Projects Agency (DARPA) for the U.S. Department of Defense (DoD). Because of its availability and early entry into the market, XNS was adopted by most of the early LAN companies, including Novell, Inc.; Ungermann-Bass, Inc. (now a part of Tandem Computers); and 3Com Corporation. Each of these companies has since made various changes to the XNS protocols. Novell added the Service Advertisement Protocol (SAP) to permit resource advertisement and modified the OSI Layer 3 protocols (which Novell renamed IPX, for Internetwork Packet Exchange) to run on IEEE 802.3 rather than Ethernet networks. Ungermann-Bass modified RIP to support delay as well as hop count, and made other small changes. Over time, the XNS implementations for PC networking have become more popular than XNS as it was designed by Xerox. This chapter presents a summary of the XNS protocol stack in the context of the OSI reference model. XNS Hierarchy Overview Although the XNS design objectives are the same as those for the OSI reference model, the XNS concept of a protocol hierarchy is somewhat different from that provided by the OSI reference model, as Figure 33-1 illustrates. -

Chapter1 Routing XNS 1
Chapter1 Routing XNS 1 This chapter describes how to configure your router to perform routing for packets following the Xerox Network Systems (XNS) stack of protocols. You will find information about the following topics and tasks: ■ How to configure a routing process for XNS routing. This includes information on the principal XNS protocols, XNS addressing, how to configure your router to route XNS traffic, managing security issues, and maximizing performance. ■ How to configure helper addresses for broadcast traffic. ■ How to set up routes, including setting metrics. ■ How to configure options for access lists and filters. ■ Configuration restrictions and requirements for encapsulation of all important lower layer protocols, including Token Ring, FDDI, Ethernet, and others. This chapter also contains configuration information on Ungermann-Bass’ and 3Com’s XNS-derived protocols. The section “XNS Configuration Examples” later in this chapter includes examples of actual configurations for working XNS networks, including Ungermann-Bass and 3Com. For additional information on configuring access lists in 3Com networks, please consult the Application Note titled A Detailed Look at Access Lists in 3Com XNS. Cisco’s Implementation of XNS Cisco provides a subset of the XNS protocol stack to support XNS routing on its routers. The same Cisco routers that route XNS can also route another protocol stack like TCP/IP or DECnet. At the physical and data link layers, XNS traffic can be routed over Ethernets, FDDI, Token Rings, or point-to-point serial lines running HDLC or LAPB. DECnet In previous releases of Cisco’s routing software, it was not possible to run DECnet Phase IV and any of the XNS family of protocols simultaneously in a router that included both Ethernet and Token Ring interfaces. -
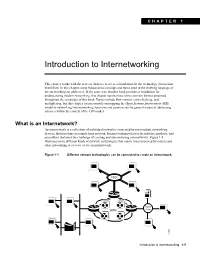
Introduction to Internetworking
CHAPTER 1 Introduction to Internetworking This chapter works with the next six chapters to act as a foundation for the technology discussions that follow. In this chapter, some fundamental concepts and terms used in the evolving language of internetworking are addressed. In the same way that this book provides a foundation for understanding modern networking, this chapter summarizes some common themes presented throughout the remainder of this book. Topics include flow control, error checking, and multiplexing, but this chapter focuses mainly on mapping the Open Systems Interconnect (OSI) model to networking/internetworking functions and summarizes the general nature of addressing schemes within the context of the OSI model. What is an Internetwork? An internetwork is a collection of individual networks, connected by intermediate networking devices, that functions as a single large network. Internetworking refers to the industry, products, and procedures that meet the challenge of creating and administering internetworks. Figure 1-1 illustrates some different kinds of network technologies that can be interconnected by routers and other networking devices to create an internetwork: Figure 1-1 Different network technologies can be connected to create an internetwork. FDDI Token WAN Ring 12308 Introduction to Internetworking 1-5 Open Systems Interconnection (OSI) Reference Model History of Internetworking The first networks were time-sharing networks that used mainframes and attached terminals. Such environments were implemented by both IBM’s System Network Architecture (SNA) and Digital’s network architecture. Local area networks (LANs) evolved around the PC revolution. LANs enabled multiple users in a relatively small geographical area to exchange files and messages, as well as access shared resources such as file servers. -

XNS Ethernet Connections for the IBM PC XT
DOCID: 3928803 XNS Ethernet Connectionsfor the IBM PC XT STATUTORILY EXEMPT The IBMPC XT andthe Xerox Network Systems (XNS) Ethernet are both well established in the data processing environment at NSA. This paper explores three different alternatives for connecting these two components. These alternatives offer a variety of functions at various interconnection costs. One of these connection alternatives has recently been announced and was tested in R5 during a ft-test of the latest version ofthe XNS software (O.S.5.0). 1. INTRODUCTION The Xerox 8000 Network System (XNS) environment has evolved into a diverse family of resources that users of non-Xerox personal computers have repeatedly attempted to tap. Prohibitive costs, lack ofsoftware, and a fear ofthe supposed excessive complexity involved have limited the personal computer to a remote user capacity with restricted access to network resources. However, recent developments in very large scale integration (VLSI) data-link controllers have made possible an affordable connection that allows the personal computer to access network services as a fully privileged network citizen. Although networking is no longer a new idea, the ability to access the high quality and rather costly services available on the Agency's several XNS Ethernet environments with the Agency standard terminaVworkstation, the IBM PC XT, is an important development. This paper documents testing and subsequent evaluation of three different connections for the IBM PC XT to the XNS Ethernet environment. The three connections to be discussed are (a) a direct physical connection to an 8000 communications processor, (b) a logical connection to the same processing capabilities via an 873 Communication Interface Unit (CIU) physically connected to the Ethernet coaxial cable, and (c) the recently announced method ofdirectly connecting the IBM PC XT to the Ethernet coaxial cable as a fully privileged network citizen. -

Internetworking Technology Overview
CISC SYS TEMS nternetworking Technoogy Overview Corporate Headquarters P.O Box 3075 1525 OBrien Drive Menlo Park CA 94026 415 326-1941 800 553-NETS Customer Order Number DOC-ITO9.2 Cisco Document Assembly Number 83-0127-01 Text Part Number 18-1249-01 in this manual to The products and specifications configurations and other technical information regarding the products contained are subject change without notice All statements technical information and recommendations contained in this manual are believed to be accurate and reliable but are in this presented without warranty of any kind express or implied and users must take full responsibility for their application of any products specified manual warranties Some states do not allow limitation or exclusion of liability for consequential or incidental damages or limitation on how long implied last so the above limitations or exclusions may not apply to you This warranty gives Customers specific legal rights and you may also have other rights that vary from state to state This equipment generates uses and can radiate radio frequency energy and if not installed and used in accordance with the instruction manual may cause interference to radio communications This equipment has been tested and found to comply with the limits for Class computing device pursuant to Subpart of Part 15 of FCC Rules which are designed to provide reasonable protection against such interfecence when operated in commercial environment Operation of this equipment in residential area is likely to cause interference in