LIV Business Letter
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Declan Clausen [email protected] I Was
Declan Clausen [email protected] I was privileged to have recently attended the 13th annual Science Meets Parliament conference (SmP) held in Canberra as the recipient of a generous APESMA Scholarship. SmP is organised by scientific lobby group Science and Technology Australia, brings together more than 150 of Australia’s preeminent industrial and research scientists and engineers. The goal of SmP is to allow participants to discuss science with other scientists, the media, influential public servants and parliamentarians. I currently study Environmental Engineering full time at the University of Newcastle, and work part time at the Hunter Water Corporation as an Industry Scholar. Outside of University and work, I am incredibly passionate about politics and policy creation, making SmP a near perfect match for my current skills, qualifications and interest. The first day of SmP began with members of the delegation working in small groups to put together a web outlining the influences on science, politics and public policy. The remainder of the first day was spent discussing these contributing influences including discussions with a media panel, a budget officer from the Commonwealth Treasury, the Deputy Secretary of the Department of Innovation, and with a team from the Centre for Public Awareness who specialise in social media and demonstrated how the new media influences science. These activities provided a detailed insight which would provide participants with knowledge that would set the scene for the rest of the conference. The first day of SmP ended in a spectacular fashion with a formal dinner held in the Great Hall of Parliament House. -

What Will a Labor Government Mean for Defence Industry in Australia?
What will a Labor Government mean for Defence Industry in Australia? Hon Greg Combet AM Opinion polls suggest a change of government in the Australian Federal election in (expected) May 2019. An incoming Labor Government led by Bill Shorten will likely feature Richard Marles as Minister for Defence and Mike Kelly as Assisting Minister for Defence Industry and Support. Jason Clare, a former Minister for Defence Matériel, would likely have influence upon the defence industry portfolio in his potential role as Minister for Trade and Investment. Under a Labor Government, it is possible Shorten would appoint a new Minister for Defence Matériel (as has been an established practice for many years) given the magnitude of expenditure and complexity of the portfolio. Shorten and Marles have been associates since university and have been closely aligned during their trade union and political careers. With extensive practical experience of the Australian industry, Shorten and Marles have a record of working constructively with business leadership. Both have a sound understanding of the role and the significance of defence industry in Australia. Marles, in particular, has a greater interest in national security and strategic issues and would likely concentrate on these in the portfolio and delegate aspects of defence industry to a ministerial colleague. Labor’s defence industry policy was reviewed and adopted during the December 2018 Party National Conference. The policy is consistent with Labor’s approach when it was last in government, reiterating support for: • an Australian defence industry that provides the Australian Defence Force with the necessary capabilities; • sovereign industrial capability where required, specifically identifying naval shipbuilding; • an export focus; • the maximisation of the participation of small-to-medium enterprises (SMEs) in defence projects; and • initiatives to develop workforce skills. -

Senate Official Hansard No
COMMONWEALTH OF AUSTRALIA PARLIAMENTARY DEBATES Senate Official Hansard No. 2, 2011 Wednesday, 2 March 2011 FORTY-THIRD PARLIAMENT FIRST SESSION—SECOND PERIOD BY AUTHORITY OF THE SENATE INTERNET The Journals for the Senate are available at http://www.aph.gov.au/senate/work/journals/index.htm Proof and Official Hansards for the House of Representatives, the Senate and committee hearings are available at http://www.aph.gov.au/hansard For searching purposes use http://parlinfo.aph.gov.au SITTING DAYS—2011 Month Date February 8, 9, 10, 28 March 1, 2, 3, 21, 22, 23, 24 May 10, 11, 12 June 14, 15, 16, 20, 21 22, 23 July 4, 5, 6, 7 August 16, 17, 18, 22, 23, 24, 25 September 12, 13, 14, 15, 19, 20, 21, 22 October 11, 12, 13, 31 November 1, 2, 3, 21, 22, 23, 24 RADIO BROADCASTS Broadcasts of proceedings of the Parliament can be heard on ABC NewsRadio in the capital cities on: ADELAIDE 972AM BRISBANE 936AM CANBERRA 103.9FM DARWIN 102.5FM HOBART 747AM MELBOURNE 1026AM PERTH 585AM SYDNEY 630AM For information regarding frequencies in other locations please visit http://www.abc.net.au/newsradio/listen/frequencies.htm FORTY-THIRD PARLIAMENT FIRST SESSION—SECOND PERIOD Governor-General Her Excellency Ms Quentin Bryce, Companion of the Order of Australia Senate Officeholders President—Senator Hon. John Joseph Hogg Deputy President and Chair of Committees—Senator Hon. Alan Baird Ferguson Temporary Chairs of Committees—Senators Guy Barnett, Thomas Mark Bishop, Suzanne Kay Boyce, Patricia Margaret Crossin, Mary Jo Fisher, Michael George Forshaw, Annette Kay Hurley, Stephen Patrick Hutchins, Helen Evelyn Kroger, Scott Ludlam, Gavin Mark Marshall, Julian John James McGauran, Claire Mary Moore, Louise Clare Pratt, Hon. -

List of Members 46Th Parliament Volume 01 - 20 June 2019
The Parliament of the Commonwealth of Australia House of Representatives List of Members 46th Parliament Volume 01 - 20 June 2019 No. Name Electorate & Party Electorate office address, telephone, facsimile Parliament House telephone & State / Territory numbers and email address facsimile numbers 1. Albanese, The Hon Anthony Norman Grayndler, ALP 334A Marrickville Road, Marrickville NSW 2204 Tel: (02) 6277 4022 Leader of the Opposition NSW Tel : (02) 9564 3588, Fax : (02) 9564 1734 Fax: (02) 6277 8562 E-mail: [email protected] 2. Alexander, Mr John Gilbert OAM Bennelong, LP 32 Beecroft Road, Epping NSW 2121 Tel: (02) 6277 4804 NSW (PO Box 872, Epping NSW 2121) Fax: (02) 6277 8581 Tel : (02) 9869 4288, Fax : (02) 9869 4833 E-mail: [email protected] 3. Allen, Dr Katie Jane Higgins, LP 1/1343 Malvern Road, Malvern VIC 3144 Tel: (02) 6277 4100 VIC Tel : (03) 9822 4422 Fax: (02) 6277 8408 E-mail: [email protected] 4. Aly, Dr Anne Cowan, ALP Shop 3, Kingsway Shopping Centre, 168 Tel: (02) 6277 4876 WA Wanneroo Road, Madeley WA 6065 Fax: (02) 6277 8526 (PO Box 219, Kingsway WA 6065) Tel : (08) 9409 4517, Fax : (08) 9409 9361 E-mail: [email protected] 5. Andrews, The Hon Karen Lesley McPherson, LNP Ground Floor The Point 47 Watts Drive, Varsity Tel: (02) 6277 7070 Minister for Industry, Science and Technology QLD Lakes QLD 4227 Fax: (02) N/A (PO Box 409, Varsity Lakes QLD 4227) Tel : (07) 5580 9111, Fax : (07) 5580 9700 E-mail: [email protected] 6. -

Local Adaptation Pathways Program Forum Report
Local Adaptation Pathways Program Forum Report ‘from risk to action’ Looking Backward: Evaluation Looking Forward: Implementation June 2011 Report prepared by: ICLEI – Local Governments for Sustainability by: Martin Brennan, Wayne Wescott and Hazen Cleary ICLEI – Local Governments for Sustainability ICLEI – Local Governments for Sustainability (ICLEI) is an international association of local governments and national and regional local government organisations that have made a commitment to sustainable development. More than 1200 cities, towns, counties and their associations worldwide comprise ICLEI’s membership. ICLEI Oceania ICLEI Oceania is the secretariat for the Oceania region. Its Melbourne head office is hosted by the City of Melbourne and which was established in 1999. ICLEI Oceania’s focus is to work predominantly with local governments in Australia and New Zealand. The Oceania office has been active in the Asia region with work undertaken on climate change action in support of local government in Indonesia, China, Korea and Taiwan. ICLEI Oceania undertakes collaborative work with Federal and State government departments and agencies, where that work builds the capacity of local governments to achieve sustainable communities, and supports those departments and agencies to progress their sustainable outcomes in partnership with the local government sector. We acknowledge the contribution of the Department of Climate Change and Energy Efficiency: Colin Steele Sharon Larkin Cate Coddington Huong Vu Funded by the Australian Government -

Federal Labor Shadow Ministry January 2021
Federal Labor Shadow Ministry January 2021 Portfolio Minister Leader of the Opposition The Hon Anthony Albanese MP Shadow Cabinet Secretary Senator Jenny McAllister Deputy Leader of the Opposition The Hon Richard Marles MP Shadow Minister for National Reconstruction, Employment, Skills and Small Business Shadow Minister for Science Shadow Minister Assisting for Small Business Matt Keogh MP Shadow Assistant Minister for Employment and Skills Senator Louise Pratt Leader of the Opposition in the Senate Senator the Hon Penny Wong Shadow Minister for Foreign Affairs Shadow Minister for International Development and the Pacific Pat Conroy MP Shadow Assistant Minister to the Leader of the Opposition in the Senate Senator Jenny McAllister Leader of the Opposition in the Senate Senator the Hon Kristina Keneally Shadow Minister for Home Affairs Shadow Minister for Immigration and Citizenship Shadow Minister for Government Accountability Shadow Minister for Multicultural Affairs Andrew Giles MP Shadow Minister Assisting for Immigration and Citizenship Shadow Minister for Disaster and Emergency Management Senator Murray Watt Shadow Minister Assisting on Government Accountability Pat Conroy MP Shadow Minister for Industrial Relations The Hon Tony Burke MP Shadow Minister for the Arts Manager of Opposition Business in the House of Representatives Shadow Special Minister of State Senator the Hon Don Farrell Shadow Minister for Sport and Tourism Shadow Minister Assisting the Leader of the Opposition Shadow Treasurer Dr Jim Chalmers MP Shadow Assistant -

Assembly Weekly Book 15 Dec 2006-Jun
PARLIAMENT OF VICTORIA PARLIAMENTARY DEBATES (HANSARD) LEGISLATIVE ASSEMBLY FIFTY-SIXTH PARLIAMENT FIRST SESSION Wednesday, 31 October 2007 (Extract from book 15) Internet: www.parliament.vic.gov.au/downloadhansard By authority of the Victorian Government Printer The Governor Professor DAVID de KRETSER, AC The Lieutenant-Governor The Honourable Justice MARILYN WARREN, AC The ministry Premier, Minister for Veterans’ Affairs and Minister for Multicultural Affairs....................................................... The Hon. J. M. Brumby, MP Deputy Premier, Attorney-General, Minister for Industrial Relations and Minister for Racing........................................ The Hon. R. J. Hulls, MP Treasurer....................................................... The Hon. J. Lenders, MLC Minister for Regional and Rural Development, and Minister for Skills and Workforce Participation............................... The Hon. J. M. Allan, MP Minister for Health............................................... The Hon. D. M. Andrews, MP Minister for Community Development and Minister for Energy and Resources.................................................... The Hon. P. Batchelor, MP Minister for Police and Emergency Services, and Minister for Corrections................................................... The Hon. R. G. Cameron, MP Minister for Agriculture and Minister for Small Business.............. The Hon. J. Helper, MP Minister for Finance, WorkCover and the Transport Accident Commission, Minister for Water and Minister for Tourism and Major -

Book 2 23, 24 and 25 February 2010
PARLIAMENT OF VICTORIA PARLIAMENTARY DEBATES (HANSARD) LEGISLATIVE ASSEMBLY FIFTY-SIXTH PARLIAMENT FIRST SESSION Book 2 23, 24 and 25 February 2010 Internet: www.parliament.vic.gov.au/downloadhansard By authority of the Victorian Government Printer The Governor Professor DAVID de KRETSER, AC The Lieutenant-Governor The Honourable Justice MARILYN WARREN, AC The ministry Premier, Minister for Veterans’ Affairs and Minister for Multicultural Affairs....................................................... The Hon. J. M. Brumby, MP Deputy Premier, Attorney-General and Minister for Racing............ The Hon. R. J. Hulls, MP Treasurer, Minister for Information and Communication Technology, and Minister for Financial Services.............................. The Hon. J. Lenders, MLC Minister for Regional and Rural Development, and Minister for Industry and Trade............................................. The Hon. J. M. Allan, MP Minister for Health............................................... The Hon. D. M. Andrews, MP Minister for Energy and Resources, and Minister for the Arts........... The Hon. P. Batchelor, MP Minister for Police and Emergency Services, and Minister for Corrections................................................... The Hon. R. G. Cameron, MP Minister for Community Development.............................. The Hon. L. D’Ambrosio, MP Minister for Agriculture and Minister for Small Business.............. The Hon. J. Helper, MP Minister for Finance, WorkCover and the Transport Accident Commission, Minister for Water and Minister -

Striking a Different Note LAW and ORDER in the HOUSE
Striking a different note LAW AND ORDER IN THE HOUSE wasn’t quite sure what to expect from the Member Were you interested in practising MARK for Isaacs, Mark Dreyfus. Would he dominate the law from a young age? DREYFUS Iconver sation with talk of Labor policies and initia- tives with the view to generating positive PR for his Both my parents are musicians (his father is noted AGREED TO party in this federal election year? composer George Dreyfus) and are still working in music in their 70s and 80s. Growing up, I had It seems a particularly cynical view, as I found in TAKE TIME an interest in writing and reading and ended up Mr Dreyfus a genuineness and honesty that is rare studying arts/law at the University of Melbourne OUT OF among any professional nowadays, let alone in a largely because I had the entry score to do so. I never politician. HIS BUSY really expected to practise law. Of course, Mr Dreyfus did touch briefly on Labor’s SCHEDULE AS “Closing the Gap” policies, speaking of the personal How did you get your start in satisfaction he felt when, on his first working day in the legal profession? A FEDERAL Canberra, Prime Minister Rudd offered an historic MP TO BE apology to Indigenous Australians. But it was more I graduated in 1979 and went to work as a to draw attention to how that particular experience field officer for the Northern Land Council, INTER highlighted the direct intersection between his new an organisation which represents Aboriginal VIEWED FOR career as a politician and his earlier work as both traditional owners in the Northern Territory. -
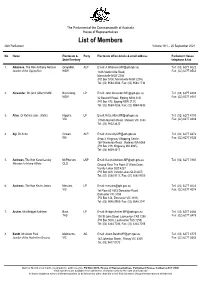
List of Senators
The Parliament of the Commonwealth of Australia House of Representatives List of Members 46th Parliament Volume 19.1 – 20 September 2021 No. Name Electorate & Party Electorate office details & email address Parliament House State/Territory telephone & fax 1. Albanese, The Hon Anthony Norman Grayndler, ALP Email: [email protected] Tel: (02) 6277 4022 Leader of the Opposition NSW 334A Marrickville Road, Fax: (02) 6277 8562 Marrickville NSW 2204 (PO Box 5100, Marrickville NSW 2204) Tel: (02) 9564 3588, Fax: (02) 9564 1734 2. Alexander, Mr John Gilbert OAM Bennelong, LP Email: [email protected] Tel: (02) 6277 4804 NSW 32 Beecroft Road, Epping NSW 2121 Fax: (02) 6277 8581 (PO Box 872, Epping NSW 2121) Tel: (02) 9869 4288, Fax: (02) 9869 4833 3. Allen, Dr Katrina Jane (Katie) Higgins, LP Email: [email protected] Tel: (02) 6277 4100 VIC 1/1343 Malvern Road, Malvern VIC 3144 Fax: (02) 6277 8408 Tel: (03) 9822 4422 4. Aly, Dr Anne Cowan, ALP Email: [email protected] Tel: (02) 6277 4876 WA Shop 3, Kingsway Shopping Centre, Fax: (02) 6277 8526 168 Wanneroo Road, Madeley WA 6065 (PO Box 219, Kingsway WA 6065) Tel: (08) 9409 4517 5. Andrews, The Hon Karen Lesley McPherson, LNP Email: [email protected] Tel: (02) 6277 7860 Minister for Home Affairs QLD Ground Floor The Point 47 Watts Drive, Varsity Lakes QLD 4227 (PO Box 409, Varsity Lakes QLD 4227) Tel: (07) 5580 9111, Fax: (07) 5580 9700 6. Andrews, The Hon Kevin James Menzies, LP Email: [email protected] Tel: (02) 6277 4023 VIC 1st Floor 651-653 Doncaster Road, Fax: (02) 6277 4074 Doncaster VIC 3108 (PO Box 124, Doncaster VIC 3108) Tel: (03) 9848 9900, Fax: (03) 9848 2741 7. -

Parliamentary Debates (Hansard)
PARLIAMENT OF VICTORIA PARLIAMENTARY DEBATES (HANSARD) LEGISLATIVE ASSEMBLY FIFTY-NINTH PARLIAMENT FIRST SESSION WEDNESDAY, 20 MARCH 2019 Internet: www.parliament.vic.gov.au/downloadhansard By authority of the Victorian Government Printer The Governor The Honourable LINDA DESSAU, AC The Lieutenant-Governor The Honourable KEN LAY, AO, APM The ministry Premier ........................................................ The Hon. DM Andrews, MP Deputy Premier and Minister for Education ......................... The Hon. JA Merlino, MP Treasurer, Minister for Economic Development and Minister for Industrial Relations ........................................... The Hon. TH Pallas, MP Minister for Transport Infrastructure ............................... The Hon. JM Allan, MP Minister for Crime Prevention, Minister for Corrections, Minister for Youth Justice and Minister for Victim Support .................... The Hon. BA Carroll, MP Minister for Energy, Environment and Climate Change, and Minister for Solar Homes ................................................. The Hon. L D’Ambrosio, MP Minister for Child Protection and Minister for Disability, Ageing and Carers ....................................................... The Hon. LA Donnellan, MP Minister for Mental Health, Minister for Equality and Minister for Creative Industries ............................................ The Hon. MP Foley, MP Attorney-General and Minister for Workplace Safety ................. The Hon. J Hennessy, MP Minister for Public Transport and Minister for Ports and Freight -
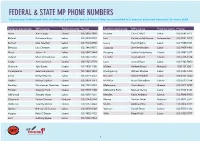
Federal & State Mp Phone Numbers
FEDERAL & STATE MP PHONE NUMBERS Contact your federal and state members of parliament and ask them if they are committed to 2 years of preschool education for every child. Federal electorate MP’s name Political party Phone Federal electorate MP’s name Political party Phone Aston Alan Tudge Liberal (03) 9887 3890 Hotham Clare O’Neil Labor (03) 9545 6211 Ballarat Catherine King Labor (03) 5338 8123 Indi Catherine McGowan Independent (03) 5721 7077 Batman Ged Kearney Labor (03) 9416 8690 Isaacs Mark Dreyfus Labor (03) 9580 4651 Bendigo Lisa Chesters Labor (03) 5443 9055 Jagajaga Jennifer Macklin Labor (03) 9459 1411 Bruce Julian Hill Labor (03) 9547 1444 Kooyong Joshua Frydenberg Liberal (03) 9882 3677 Calwell Maria Vamvakinou Labor (03) 9367 5216 La Trobe Jason Wood Liberal (03) 9768 9164 Casey Anthony Smith Liberal (03) 9727 0799 Lalor Joanne Ryan Labor (03) 9742 5800 Chisholm Julia Banks Liberal (03) 9808 3188 Mallee Andrew Broad National 1300 131 620 Corangamite Sarah Henderson Liberal (03) 5243 1444 Maribyrnong William Shorten Labor (03) 9326 1300 Corio Richard Marles Labor (03) 5221 3033 McEwen Robert Mitchell Labor (03) 9333 0440 Deakin Michael Sukkar Liberal (03) 9874 1711 McMillan Russell Broadbent Liberal (03) 5623 2064 Dunkley Christopher Crewther Liberal (03) 9781 2333 Melbourne Adam Bandt Greens (03) 9417 0759 Flinders Gregory Hunt Liberal (03) 5979 3188 Melbourne Ports Michael Danby Labor (03) 9534 8126 Gellibrand Timothy Watts Labor (03) 9687 7661 Menzies Kevin Andrews Liberal (03) 9848 9900 Gippsland Darren Chester National