Automated Malware Analysis Report For
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -

Discontinued Browsers List
Discontinued Browsers List Look back into history at the fallen windows of yesteryear. Welcome to the dead pool. We include both officially discontinued, as well as those that have not updated. If you are interested in browsers that still work, try our big browser list. All links open in new windows. 1. Abaco (discontinued) http://lab-fgb.com/abaco 2. Acoo (last updated 2009) http://www.acoobrowser.com 3. Amaya (discontinued 2013) https://www.w3.org/Amaya 4. AOL Explorer (discontinued 2006) https://www.aol.com 5. AMosaic (discontinued in 2006) No website 6. Arachne (last updated 2013) http://www.glennmcc.org 7. Arena (discontinued in 1998) https://www.w3.org/Arena 8. Ariadna (discontinued in 1998) http://www.ariadna.ru 9. Arora (discontinued in 2011) https://github.com/Arora/arora 10. AWeb (last updated 2001) http://www.amitrix.com/aweb.html 11. Baidu (discontinued 2019) https://liulanqi.baidu.com 12. Beamrise (last updated 2014) http://www.sien.com 13. Beonex Communicator (discontinued in 2004) https://www.beonex.com 14. BlackHawk (last updated 2015) http://www.netgate.sk/blackhawk 15. Bolt (discontinued 2011) No website 16. Browse3d (last updated 2005) http://www.browse3d.com 17. Browzar (last updated 2013) http://www.browzar.com 18. Camino (discontinued in 2013) http://caminobrowser.org 19. Classilla (last updated 2014) https://www.floodgap.com/software/classilla 20. CometBird (discontinued 2015) http://www.cometbird.com 21. Conkeror (last updated 2016) http://conkeror.org 22. Crazy Browser (last updated 2013) No website 23. Deepnet Explorer (discontinued in 2006) http://www.deepnetexplorer.com 24. Enigma (last updated 2012) No website 25. -

Charles University in Prague
Vrije Universiteit Amsterdam Faculty of sciences MASTER THESIS Milan Slančík Advanced floor plan designer in Flex Department of computer science Supervisor: Prof dr Anton Æliëns Second reader: Dr Evert Wattel Study program: Informatics, Multimedia Computer Science Acknowledgements First of all, I wish to express my sincere gratitude and appreciation to my supervisor, Prof Dr Anton Æliëns, for his thoughtful guidance, his valuable suggestions, comments during discussions, prompt response to my emails and speedy feedback. My gratitude also goes to my second reader, Dr Evert Wattel for his ideas, willingness to read drafts and test the application in advance. Last, but not least, I would like to give my sincere thanks also to my parents, who have supported me throughout the writing process. Contents 1 INTRODUCTION ....................................................................................................................................................... 8 1.1 BACKGROUND ............................................................................................................................................................ 8 1.2 STRUCTURE OF THIS DOCUMENT ............................................................................................................................ 8 2 AIM OF THE WORK AND RESEARCH ISS UES ........................................................................................... 9 3 RELATED WORK................................................................................................................................................... -
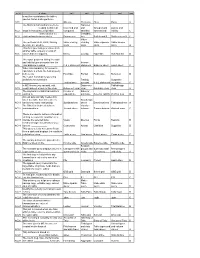
Q Id Q Desc Op1 Op2 Op3 Op4 Ans AC1 in an Access Database The
q_id q_desc op1 op2 op3 op4 ans In an Access database the tables, queries, forms and reports are AC1 ____________ Objects Elements Files Parts A The financial transactions are to be Sampled ____________ leading to different Collected and and Grouped and Assets and AC2 steps in Accounts Compilation. computed stratified summarized liability C ____________ is/are used to set Candidate AC3 relationships between tables. Primary key key Both A and B Neither A nor B C Value The methods LIFO, FIFO, Moving Value closing clearing Value expense Value income AC4 Average are used to ____________ stock stock stock stock A This data type field gets values from another table, a query or a list of AC5 values that are supplied. Memo Lookup Hyperlink AutoNumber B The report prepared taking the asset and liability type accounts from the Income AC6 Trial Balance is called ____________ P & L statement statement Balance sheet Asset sheet C When it is mandatory for a user to input data in a field ,the field property AC7 to be set is ____________ Field Size Format Field value Required D The report that depicts operating profit/loss for a period is Trading Suspense AC8 ____________ Trial balance account P & L statement accounts C In MS Access you can add, edit, Datamenu Tabledesign AC9 modify data of a table in this view. Datasheet view view Datatable view view A The day book contains transactions Income or Sales or AC10 relating to ____________ expenditure purchase Asset or liability Profit or loss B Access automatically creates this sheet in a table that is in a one-to- Datadesign AC11 one/one-to-many relationship. -

3.1 What Is the Restaurant Game?
Learning Plan Networks in Conversational Video Games by Jeffrey David Orkin B.S., Tufts University (1995) M.S., University of Washington (2003) Submitted-to the Program in Media Arts and Sciences in partial fulfillment of the requirements for the degree of Master of Science at the MASSACHUSETTS INSTITUTE OF TECHNOLOGY August 2007 © Massachusetts Institute of Technology 2007. All rights reserved. A uthor ........................... .............. Program in Media Arts and Sciences August 13, 2007 C ertified by ...................................... Associate Professor Thesis Supervisor Accepted by................................... Deb Roy 1 6lsimnhairperson, Departmental Committee on Graduate Students QF TECHNOLOGY SEP 14 2007 ROTCH LIBRARIES 2 Learning Plan Networks in Conversational Video Games by Jeffrey David Orkin Submitted to the Program in Media Arts and Sciences on August 13, 2007, in partial fulfillment of the requirements for the degree of Master of Science Abstract We look forward to a future where robots collaborate with humans in the home and workplace, and virtual agents collaborate with humans in games and training simulations. A representation of common ground for everyday scenarios is essential for these agents if they are to be effective collaborators and communicators. Effective collaborators can infer a partner's goals and predict future actions. Effective communicators can infer the meaning of utterances based on semantic context. This thesis introduces a computational cognitive model of common ground called a Plan Network. A Plan Network is a statistical model that provides representations of social roles, object affordances, and expected patterns of behavior and language. I describe a methodology for unsupervised learning of a Plan Network using a multiplayer video game, visualization of this network, and evaluation of the learned model with respect to human judgment of typical behavior. -

Programming-Javascri
www.allitebooks.com www.allitebooks.com Programming JavaScript Applications Eric Elliott www.allitebooks.com Programming JavaScript Applications by Eric Elliott Copyright © 2014 Eric Elliott. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (http://my.safaribooksonline.com). For more information, contact our corporate/ institutional sales department: 800-998-9938 or [email protected]. Editors: Simon St. Laurent and Meghan Blanchette Indexer: Lucie Haskins Production Editor: Kara Ebrahim Cover Designer: Randy Comer Copyeditor: Eliahu Sussman Interior Designer: David Futato Proofreader: Amanda Kersey Illustrator: Rebecca Demarest July 2014: First Edition Revision History for the First Edition: 2014-06-25: First release See http://oreilly.com/catalog/errata.csp?isbn=9781491950296 for release details. Nutshell Handbook, the Nutshell Handbook logo, and the O’Reilly logo are registered trademarks of O’Reilly Media, Inc. Programming JavaScript Applications, the image of an argali, and related trade dress are trade‐ marks of O’Reilly Media, Inc. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and O’Reilly Media, Inc. was aware of a trademark claim, the designations have been printed in caps or initial caps. While every precaution has been taken in the preparation of this book, the publisher and author assume no responsibility for errors or omissions, or for damages resulting from the use of the information contained herein. -
Documentation, 5.1 MB
MenuBox by Cloanto Corporation © 1998-2021 Cloanto Corporation The MenuBox software and documentation are Copyright © 1998-2021 Cloanto Corporation. All rights reserved. No part of this package may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated into any language or computer language, in any form or by any means, magnetic, memristive, optical, quantum mechanical, electronic, biological, chemical, mechanical, acoustic, manual or otherwise without the prior written permission of the copyright holders, or as indicated here or in the EULA. The use of this document is subject to the terms of the EULA that accompanies the MenuBox package. Cloanto may have copyrights, trademarks, patents, patent applications, and other intellectual property rights covering items contained in MenuBox and its documentation. Except as expressly provided in any written license agreement from Cloanto, the furnishing of this product and its documentation does not give you any license to these copyrights, trademarks, patents, or other intellectual property. Cloanto and MenuBox are either registered trademarks or trademarks of Cloanto Corporation in the United States and/or other countries. Microsoft, Windows, Windows Me, Windows NT, Windows XP, Windows Vista, Windows 7, Windows 8, Windows Server 2003, Windows Server 2008 and Windows Server 2012 are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. All other trademarks and service marks are the property of their respective owners. Contents Table of Contents Part 1 Introducing MenuBox 6 1 New.. .F..e..a..t.u..r.e..s.. .................................................................................................................. 7 Part 2 Getting Started 11 1 Ov.e..r.v..i.e..w.. -

Appwave™ Enterprise Store 4.1 Administrator Guide
Product Documentation AppWave™ Enterprise Administrator Guide Version 4.2 Published August, 2013 © 2013 Embarcadero Technologies, Inc. Embarcadero, the Embarcadero Technologies logos, and all other Embarcadero Technologies product or service names are trademarks or registered trademarks of Embarcadero Technologies, Inc. All other trademarks are property of their respective owners. Embarcadero Technologies, Inc. is a leading provider of award-winning tools for application developers and database professionals so they can design systems right, build them faster and run them better, regardless of their platform or programming language. Ninety of the Fortune 100 and an active community of more than three million users worldwide rely on Embarcadero products to increase productivity, reduce costs, simplify change management and compliance and accelerate innovation. The company's flagship tools include: Embarcadero® Change Manager™, CodeGear™ RAD Studio, DBArtisan®, Delphi®, ER/Studio®, JBuilder® and Rapid SQL®. Founded in 1993, Embarcadero is headquartered in San Francisco, with offices located around the world. Embarcadero is online at www.embarcadero.com. Contents Welcome to AppWave . 11 About This Document . .11 Introduction to AppWave Enterprise . .11 Additional Product Information. .13 Installation Information . 15 Installing AppWave . .15 Default Installation . 15 Custom Installation. 16 Upgrading AppWave from Previous Versions . .19 Providing Users with AppWave Browser. .20 Administrator Installing AppWave Browser . 20 Admin directly installs AppWave Browser on a machine for all users . 21 AppWave Configuration and Administration . 25 Using the Dashboard Commands. .26 Download AppWave Browser . 27 Services Status . 28 Set Up Embarcadero Licenses. 29 Download Applications . 31 Manage Mastering Plug-ins. 33 Import LDAP Users and Groups . 34 Examples . 37 Updating and Deleting LDAP Users . -

December 2003
DCU DUBLIN CITY UNIVERSITY SCHOOL OF ELECTRONIC ENGINEERING The YBox - A Front-E nd Processing Engine for W eb Com m unity based A pplications Liam Fraw ley December 2003 MASTER OF ENGINEERING IN ELECTRONIC SYSTEMS Supervised by Dr. D. M olloy The YBox - A Front-End Processing Engine for Web Community based Applications Acknowledgements I would like to thank my supervisor Dr. Derek Molloy for his guidance, enthusiasm and commitment to this project. I would also like to thank my family for their patience throughout the entire project Finally I would like to express my deep appreciation to Fiona for her support and understanding over the past two and a half years. The YBox - A Front-End Processing Engine for Web Community based Applications Declaration I hereby declare that, except where otherwise indicated, this document is entirely my own work and has not been submitted in whole or in part to any other university. Date: 2 .1 -0 2 - Ù3 iii The YBox - A Front-End Processing Engine for Web Community based Applications A b stract This document describes the YBox framework that enables web application developers to rapidly develop web applications for the Java 2 Enterprise Edition (J2EE) platform, The YBox is a fully implemented and tested framework that provides a “front-end” for Servlet Containers and contains functionality that all user- based web applications for virtual communities require. The YBox extends the functionality of the Servlet Container and the Servlet 2.3 API and is implemented in a platform independent manner, which means the YBox will run on any operating system or any Servlet Container. -

3500+ IMPORTANT QUESTIONS for ITT ONLINE EXAM ** by A.Amogh [email protected] 09666460051
** 3500+ IMPORTANT QUESTIONS FOR ITT ONLINE EXAM ** By A.Amogh [email protected] 09666460051 Amogh Ashtaputre @amoghashtaputre Amogh Ashtaputre Amogh Ashtaputre ** 3500+ IMPORTANT QUESTIONS FOR ITT ONLINE EXAM ** COMPILED BY A.AMOGH. FEEDBACK CAN BE SENT @ [email protected]. 09666460051. QUESTIONS A B C D ANS TALLY The ------ key can be used to select an existing F1 ALT+F1 CTRL+F1 None of the above A company from list of companies. Import and Export of data between Tally and Tally ODBC Tally IMP Tally INI None of the above A other programs is possible only through ---------- Program. The re-order point is the inventory quantity that TRUE false A triggers a stock replishment activity. A created company's detail can be modified F3 ALT+F3 CTRL+F3 None of the above B through keys A/An ------------- is the official notice that the firm Invoice Bill A or B None of the above C sends to its customers to advise then to the amount of money that is owed. In tally, all masters have ________main options Two Three Four Five B In tally, to create a new column in balance sheet Ctrl+C Alt+C Alt+Ctrl+C None of the above B press _______ In tally,the use of group behaves like a sub- TRUE FALSE A ledger, option is that we can summarize many ledger accounts into one line statements In tally, we can alter ledger details using either TRUE FALSE A single or multiple modes but not able to delete a ledger from multiple modes. In tally,a group company is marked with an * $ & ^ A ______________ The systems that work together to order, receive, Purchasing and Purchasing and Accounts payable and Purchasing, D and pay for replenishment of stock are --------------- Accounts Receiving Receiving Receiving and payable Accounts payable Tally allows deleting a ledger from --------- Single Multiple A or B none of the above A alteration mode. -

Web User Profiling Based on Browsing Behavior Analysis Xiao-Xi Fan, Kam-Pui Chow, Fei Xu
Web User Profiling Based on Browsing Behavior Analysis Xiao-Xi Fan, Kam-Pui Chow, Fei Xu To cite this version: Xiao-Xi Fan, Kam-Pui Chow, Fei Xu. Web User Profiling Based on Browsing Behavior Analysis. 10th IFIP International Conference on Digital Forensics (DF), Jan 2014, Vienna, Austria. pp.57-71, 10.1007/978-3-662-44952-3_5. hal-01393760 HAL Id: hal-01393760 https://hal.inria.fr/hal-01393760 Submitted on 8 Nov 2016 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Distributed under a Creative Commons Attribution| 4.0 International License Chapter 5 WEB USER PROFILING BASED ON BROWSING BEHAVIOR ANALYSIS Xiao-Xi Fan, Kam-Pui Chow and Fei Xu Abstract Determining the source of criminal activity requires a reliable means to estimate a criminal’s identity. One way to do this is to use web browsing history to build a profile of an anonymous user. Since an individual’s web use is unique, matching the web use profile to known samples pro- vides a means to identify an unknown user. This paper describes a model for web user profiling and identification. Two aspects of brows- ing behavior are examined to construct a user profile, the user’s page view number and page view time for each domain. -

Le Livre Du Pegasos » Compilation of Articles on the Pegasos Volume 3 : Morphos
The Pegasos book « Le livre du Pegasos » Compilation of articles on the Pegasos Volume 3 : MorphOS May 2007 edition - By Geoffrey CHARRA (V2.3) Translated from french by Geoffrey CHARRA (December 2007), With the help of Eric WALTER, Thibault JEANSON, Denis HILLIARD (translation) and Fulvio PERUGGI (corrections) Sponsored by The Pegasos book – Volume 3 : MorphOS Contents 1 Presentation of MorphOS .............................................................................................. 6 2 Installation of MorphOS ............................................................................................... 8 2.1 Preparation ........................................................................................................... 8 2.2 Booting from CD .................................................................................................... 8 2.3 Installing the Hard Drive ........................................................................................ 9 2.3.1 Partition 0 (boot) ............................................................................................ 9 2.3.2 Partition 1 (system) ...................................................................................... 10 2.3.3 Partition 2 to N (data) ................................................................................... 11 2.3.4 Save of partition table and check ..................................................................... 11 2.4 Format the Partitions ..........................................................................................