Securing Mobile Devices on Converged Networks White Paper
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Anticircumvention Rulemaking, 2006: Post-Hearing Questions and Replies
LIBRARY OF CONGRESS ______________________________ UNITED STATES COPYRIGHT OFFICE ______________________________ EXEMPTION TO PROHIBITION ON CIRCUMVENTION OF COPYRIGHT PROTECTION SYSTEMS FOR ACCESS CONTROL TECHNOLOGIES _______________________________ 37 CFR Part 201 Docket No. RM 2005-11 _______________________________ PETITION FOR CONSIDERATION AND ENTRY OF REPLY COMMENTS OF TRACFONE WIRELESS, INC. Represented by: James B. Baldinger, Esq. Lance D. Reich, Esq. CARLTON FIELDS, P.A. CARLTON FIELDS, P.A. 222 Lakeview Avenue, Suite 1400 1201 West Peachtree Street, Suite 3000 West Palm Beach, FL 33401-6149 Atlanta, GA 30309-3455 Telephone: (561) 659-7070 Telephone: (404) 815-3400 Facsimile: (561) 659-7368 Facsimile: (404) 815-3415 e-mail: [email protected] e-mail: [email protected] TABLE OF CONTENTS I. Introduction and Summary . 1 II. Statement Regarding TracFone Wireless, Inc. 2 III. Petition for Consideration of Reply Comments . 3 A. TracFone only recently learned of the proposed exemption in its current form . 3 B. The proposed exemption was narrowed after the Public Hearing from a general class to a narrow exemption for “software locks” that would specifically harm TracFone . 3 C. The proposed exemption, as currently contemplated, would have a significant adverse impact particularly on TracFone’s business model . 4 IV. Opposition to Proposed Exemption from Section 1201(a)(1) for “Computer programs that operate wireless telecommunications handsets” . 5 A. Proposed Exemption for “Computer programs that operate wireless telecommunications handsets” . 5 B. Summary of the Argument in Opposition . 5 C. Factual Basis Supporting the Opposition . 5 i. The TracFone Prepaid Handsets . 5 ii. Cellular Telecommunication Carriers and Their Network Locks . 9 iii. Unlocked Cellphones are Available to the Public . -

Motorola Announces Record Third-Quarter Sales and Earnings
Ed Gams, SVP & Director Mike Ferraro, Director Investor Relations Investor Relations 847-576-6873 847-576-4995 Motorola Announces Record Third-Quarter Sales and Earnings Third-Quarter 2005 Financial Highlights • Sales up 26 percent: Record sales of $9.42 billion, compared to third-quarter 2004 sales of $7.50 billion • Earnings from continuing operations of $.69 per share, including earnings of $.39 per share from significant items discussed below • Global mobile device market share up 5.5 percentage points: Achieved an estimated global market share of approximately 19 percent, an increase of approximately 5.5 percentage points versus the year-ago quarter and approximately 1 percentage point versus the second quarter of 2005 • Record Mobile Device shipments of 38.7 million units • Positive operating cash flow of $1.1 billion SCHAUMBURG, Ill. – October 18, 2005 – Motorola, Inc. (NYSE: MOT) today reported record sales and earnings from continuing operations as shown below. Third Quarter % 2005 2004 Increase Sales $9.42B $7.50B 26% EPS $0.69 $0.18 283% Third-quarter 2005 earnings from continuing operations include income of $.39 per share from the items shown below. Third-Quarter 2005 EPS Impact Gain on Nextel stock and related hedge adjustments $ 0.32 Tax benefits related to the repatriation of cash and the divestiture of a business 0.13 Debt retirement costs (0.03) Reorganization of businesses (0.03) Total EPS Impact $ 0.39 During the quarter, the company continued to strengthen its balance sheet. The company generated operating cash flow of $1.1 billion, its 19th consecutive quarter of positive operating cash flow. -

Motorola Razr2 V8 User Manual
Guidebooks Motorola razr2 v8 user manual Motorola razr2 v8 user manual . Download: Motorola razr2 v8 user manual and user guide is also related with Motorola Razr2 V9 Service Manual, include : Motorola Razr2. V9x Manual, Motorola Razr2 V8 Manual, Motorola Razr2 V9m. Motorola RAZR2 V8 Manual Online: Return A Call, Caller Id. Motorola RAZR V8 / User Manual - Page 4. Introducing your new MOTORAZR2 V8 GSM wireless phone. Heres a quick anatomy lesson. Charge Indicator Light. Read Online and Download PDF Ebook motorola razr xt912 user manual. PDF Ebook styles motorola razr2 v8 user manual, Discover unlimited ebooks. This MOTO RAZR2 V8 is a new factory refurbished model. bx41, motorola charger and motorola General user manual with motorola refurbish packing box. You can download the file by clicking the following link razr v3c user manual flip for motorola v3 v3c v3i v3m v3t v8 v9 w490 w755 samsung: a900 d820 d807. Motorola Fv700 User Manual from our library is free resource for public. Motorola Fv700 User Manual is available through our online libraries and we offer online MOTOROLA V8 USER MANUAL MOTOROLA RAZR2 V9 USER MANUAL. We have ebooks for every subject motorola razr xt912 user manual, Discover unlimited ebooks from our database related with motorola razr2 v8 user manual. Motorola RAZR2 V8 Unlocked Phone with 2 MP Camera, and MP3/Video charger, mini-to-micro USB adapter, Quick Start Guide and User Manual They sent a Motorola RAZR2 V9x Black Phone, an original American supported (AT&T). and user guide is also related with Motorola Razr2 V9 Service Manual, include : Motorola Razr2. -

We've Got Christmas Wrapped
November 2005 Press Release We’ve got Christmas wrapped up! Whatever you’re into for Christmas, everyone loves a new mobile phone. It’s the one thing, along with your keys and wallet that you never leave home without - making it the perfect present! The Carphone Warehouse has got more exciting and stylish handsets than ever before – all at amazingly low prices – keeping your friends and family merry this Christmas. With pre-pay handsets from an incredible £19.99 (plus £10 top up) Christmas has never been easier. For a truly unique gift this year, take advantage of the new Golden Ticket initiative exclusively from The Carphone Warehouse. This is the ultimate Christmas idea that keeps friends and family talking all year round. It gives you the chance to buy one of the latest handsets with line rental paid up front for a whole year making it easy for them to stay in touch while saving money at the same time. And get your hands on the number one must have for all fashion fans this Christmas – the Motorola Pink Razr – available exclusively at The Carphone Warehouse for a limited period. Spread festive joy under the Christmas tree – with the best fashion phones, music phones cameraphones and mobile accessories for all your family and friends. See below for the latest Christmas present ideas at the most competitive prices on the high-street…. Best value buys for Christmas - The Motorola C139 and Nokia 1100 for JUST £19.99 The Carphone Warehouse is the ultimate destination for the best priced phones this Christmas. -

Integration & Consolidation
Pan-Europe Semiconductors (Citi) Industry Focus 29 November 2007 72 pages Integration & consolidation The roadmap for wireless semiconductors 1 Wireless matters in Europe — Our chip company coverage universe has a material Paraag Amin, CFA exposure to the >US$40 billion handset semiconductor market, ranging from 17% +44-20-7986-4080 [email protected] to 65% of revenues. Timothy Shaw1 Moderating handset growth to impact the sector — As emerging market volume +44-20-7986-4199 growth moderates, we expect volume growth for the handset market to move from [email protected] 23% in 2006 to 9% in 2009. We expect this to increase competition in the Katherine Thompson1 handset sector, which in turn will increase pressure on chip prices. +44-20-7986-4240 Integration the driving force — The trend towards integration of baseband and [email protected] radio functions onto one chip started a couple of years ago and is gathering pace. Christopher I Vagg1 We see this as a vital skill for chip makers and see Infineon as best placed within [email protected] our coverage. Further consolidation likely — With a large number of chip suppliers fighting over the Top 5 handset OEMs, we expect further consolidation. We see ST as a potential acquirer (of RF integration expertise) and CSR as a potential target (for its non-cellular RF expertise). Longer-term trends to consider (1) — The move from 3G to 4G cellular technologies will provide a new opportunity for chip makers. Three standards are currently in the running: LTE, UMB and WiMAX. We expect most chip makers to focus on developing LTE solutions, as this is a natural evolution from HSPA. -
How Cell Phones Work" Page 1 of 6
Howstuffworks "How Cell Phones Work" Page 1 of 6 Make HowStuffWorks your home page! Mobil Travel Guide | Consumer Guide Pr Search HowStuffWorks and the Auto Stuff Science Stuff Health Stuff Entertainment Stuff Travel Stu Computer Stuff Electronics Stuff Home Stuff Money Stuff People Stuff S Main > Electronics > Telecommunications Related Ad Categories > Cell Phone Verizon How Cell Phones Work > Buying Mobile Phone by Julia Layton and Marshall Brain and Jeff Tyson > GSM Cellular Phone > TDMA Phone > Camera Phone Table of Contents Introduction to How Cell Phones Work Cell Phone Codes Along Comes Digital Millions of people in the United States and around the world use cellular phones. They are such great gadgets -- with a cell phone, you can talk to anyone on the planet from just about anywhere! These days, cell phones provide an incredible array of functions, and new ones are being added at a breakneck pace. Depending on the cell-phone model, you can: Digital cell phone from Nokia z Store contact information z Make task or to-do lists z Keep track of appointments and set reminders z Use the built-in calculator for simple math z Send or receive e-mail z Get information (news, entertainment, stock quotes) from the Internet z Play simple games. z Integrate other devices such as PDAs, MP3 players and GPS receivers But have you ever wondered how a cell phone works? What makes it different from a regular phone? What do all those terms like PCS, Sponsored By: http://electronics.howstuffworks.com/cell-phone.htm 11/24/2006 Howstuffworks "How Cell Phones Work" Page 2 of 6 GSM, CDMA and TDMA mean? In this article, we will discuss the technology behind cell phones so that you can see how amazing they really are. -

Equipment Brief Motorola SLVR L7 – Launch Announcement LAUNCH
Equipment Brief Motorola SLVR L7 – Launch Announcement LAUNCH DETAILS Cingular is excited to launch the Motorola SLVR L7 on January 31, 2006. The SLVR L7 is considered an “Exclusive Product”, under Cingular’s exclusive distribution policy and therefore distribution will be limited to Cingular-direct channels and indirect partners that fulfill our exclusive distribution parameters. PHONE DETAILS The new ultra-sleek phone with iTunes only at Cingular. The Motorola SLVR L7 is exclusive to Cingular Wireless. This bladelike, RAZR influenced, super-slim device can store and play iTunes music for a combined music experience in a trendy form factor. Features of the Motorola SLVR L7 include the following: Motorola SLVR L7 Device Overview Refer to local market · iTunes music player: accessed via right soft-key pricing for pricing details · 850/900/1800/1900 MHz – Quad band · GPRS class 10 · Talk time: 6.3 hours · Standby time: 420 hours/17 days · Removable memory: Micro SD card included · Camera: VGA with 4x zoom, video capture · Messaging: SMS/MMS · IM: AOL, Yahoo!, and ICQ · POP3/IMAP4 email · Bluetooth class 2 (range up to 100 feet for voice only) · 262k colors · 176 x 220 TFT screen KEY SELLING POINTS – THE CINGULAR ADVANTAGE · Play iTunes music by playlist, artist, albums, songs and shuffle–and it stores about 7 hours of music (up to 100 songs) on the included 512MB Micro SD extended memory card. · Customers can personalize their phone with downloads including games and graphics and Music Tone ringtones. · Stay in touch with friends and family with AOL, Yahoo! or ICQ Instant Messenger. · Capture those special moments with built in VGA camera and video record. -

Executive Summary
Executive Summary The Charger Team, sponsored by Jarden Consumer Solutions, is responsible for developing a mobile device charger to be used by guests in hotels nationwide. The primary end-user target is the business traveler who has a strong need to be connected to work/personal life while on travel. From a market research perspective, the team was charged to verify the consumer needs, as well which specific models and devices to focus on. From a technical engineering perspective, the team was asked to build a prototype of the said mobile device charger without infringing any current patents files with the US Patent Office. The team has decided to proceed with development of a charger comprised of a Universal Power Supply, an attachment with an adaptor for each mobile device connected through USB port and cable. As of December 6, 2006 the Charger team has made significant progress towards the completion of the project. In order to successfully deliver the mobile device charger, the team was required to complete extensive research. Having been equipped with the necessary knowledge, the team has moved towards development of circuit design and prototype. Tangible results towards prototype build will occur during January. Charger_SLDR Created on 12/1/2006 Team Charger Revised on 12/13/2006 1 Table of Contents EXECUTIVE SUMMARY ................................................................................................................. 1 INTRODUCTION........................................................................................................................ -

(12) Patent Application Publication (10) Pub. No.: US 2011/0111729 A1 Poltorak Et Al
US 2011 011 1729A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0111729 A1 POltorak et al. (43) Pub. Date: May 12, 2011 (54) MULTI-TIER QUALITY OF SERVICE (52) U.S. Cl. ....................... 455/406; 455/435.1:455/424 WIRELESS COMMUNICATIONS NETWORKS (76) Inventors: Alexander Poltorak, Monsey, NY (US); Vladimir Kaminsky, (57) ABSTRACT Washington, NJ (US) The present invention pertains to improved communication quality of service (QoS) in cellular communication networks (21) Appl. No.: 12/989,859 (10) and the like. A customer has the option to pay different 1-1. fees for different tiers of service relating to voice quality and (22) PCT Filed: Apr. 29, 2009 bandwidth access (S102). Higher service tiers may guarantee (86). PCT No.: PCT/US09/02676 that a specific vocoder O bit rate is used; they may also guarantee that communication is Supported by Such param S371 (c)(1), eters as maximum allowed dropped calls rate, maximum (2), (4) Date: Jan. 13, 2011 worktly availabilityR mayAs be guaranteedattery as per 'sService E.Leve Related U.S. Application Data Agreements that are the part of the contract between a Sub scriber and a service provider. Different tiers may be associ (60) Provisional application No. 61/125,971, filed on Apr. ated with customers’ records (208) for billing purposes. The R o, proys, applit, N. R network (200) may also afford high end cellular phones ed. On Apr. 3, proV1S1onal appl1cauon No. higher voice quality by comparing a given high end phone to 61/167,580, filed on Apr. 8, 2009. -

2008Ipod + Iphone
MENU 2008 IPOD + IPHONE BUYERS’ GUIDE FROM ILOUNGE.COM 1500 PRODUCTS RATED SNEAK PEEKS AT UPCOMING ADD-ONS NEW + USED HARDWARE BUYING TIPS THE BEST ACCESSORIES OF THE YEAR IPHONE + IPOD CONTEST WINNERS © 2007 ILOUNGE INC. Apple TV for HDTV Fox’s Hotel Chevalier, Debuted on iTunes max 1280 x 720 | 1.78:1 pixels 480 x 320 | 1.5:1 Music inspires. It fueled the first iPods. Now, iPods play videos, photos, and games. Apple released the original iPod nano 204ppi iPod in 2001. No one thought that a luxury music player would become a design icon, or spawn a 100 million- pixels 320 x 240 | 1.33:1 selling family in five years. But thanks to a borderless 2001 iPod 80ppi love for music, continued refinement and better prices, the iPod family has grown in both power and ubiquity. pixels 160 x 128 | 1.25:1 iPhone 163ppi iPod touch 163ppi iPod classic 163ppi pixels 480 x 320 | 1.5:1 pixels 320 x 240 | 1.33:1 Now, iPods play videos, photos, and games. iPods are today the world’s most popular music and video players. Apple has sold over 119 million of them. Even $149 models can play videos and games. They do more than 2001’s $399 iPod. As we enter the 2007 holiday season, the devices and their accessories remain amongst the most desired gifts. Recently, iPhones replaced full-sized iPods as the family’s unobtainable luxuries. With more Apple and third-party options than ever, how are your dollars best spent in 2008? 4-5 Video: Disney’s Meet the Robinsons Welcome to iLounge.com’s 2008 iPod + iPhone Buyers’ Guide. -

Hefty: Motorola Dynatac 8000X (1982) in 1973, Motorola Showed Off a Prototype of the World's First Portable Cellular Telephone
Hefty: Motorola DynaTAC 8000X (1982) In 1973, Motorola showed off a prototype of the world's first portable cellular telephone. That phone, which measured more than a foot long, weighed almost 2 pounds, and cost $3995, ultimately became commercial available in 1983. Known as the Motorola DynaTAC 8000X, its battery could provide 1 hour of talk time, and its memory could store 30 phone numbers. It may not have been pretty, but it did let you talk while on the go--if you could lift it, that is. Heftier: Nokia Mobira Senator (1982) It may look more like a boombox than a portable phone, but this boxy, bulky device was actually Nokia's first mobile (if you can call it that) phone. Introduced in 1982, the Nokia Mobira Senator was designed for use in cars. After all, you wouldn't want to use this phone while walking: It weighed about 21 pounds. Pre-iPhone: BellSouth/IBM Simon Personal Communicator (1993) A cell phone with added PDA functions isn't news today. But in 1993, it was a novel idea. The Simon Personal Communicator, jointly marketed by IBM and BellSouth, was the first mobile phone to add PDA features. It was a phone, pager, calculator, address book, fax machine, and e-mail device in one package, albeit a 20-ounce package that cost $900. Ahead of Its Time: Motorola StarTAC (1996) Before the Motorola StarTAC was introduced in 1996, cell phones were more about function than fashion. But this tiny, lightweight phone ushered in the concept that style was just as important, ultimately paving the way for today's sleek-looking phones like the Motorola Razr. -
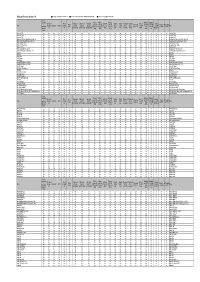
Bluetooth Firmware Version 1.43 Yes = Feature Is Supported and Confirmed
Bluetooth firmware Version 1.43 yes = Feature is supported and confirmed. no = Feature is not supported by the Kenwood Bluetooth Module. n/a = Feature is not supported by the Phone. Phone connection Pick-up Refuse Hang-up Enable to Enable to Pick-up and Reject Phonebook SIM contacts Call register Switch call Display Display Phonebook Phonebook Enable to Enable to to Private second call second call active call Phonebook use AVRCP read SMS Enable to Notify about Phone hang-up a Dial number Redial incoming automatic automatic automatic in three way battery network transfer - transfer - use A2DP read SMS Phone KENWOOD mode in three way in three way in three way transfer - all Target from SIM send SMS new SMS call call synchronisation synchronisation synchronisation calling level level one by one selection profile from phone Bluetooth calling calling calling profile card Model Blackberry 7105t yes yes yes yes yes yes yes yes yes no n/a no no yes yes n/a n/a n/a n/a n/a no no no no Blackberry 7105t Blackberry 7130g yes yes yes yes yes yes yes n/a n/a no yes no no yes yes n/a n/a n/a n/a n/a no no no no Blackberry 7130g Blackberry 7290 yes yes yes yes yes yes no n/a n/a no yes no no yes yes n/a n/a n/a n/a n/a no no no no Blackberry 7290 Blackberry 8100 Pearl - Tmobile /Rom Ver.4.2.0.42 yes yes yes yes yes no yes yes yes no yes no no yes yes yes yes yes n/a n/a no no no no Blackberry 8100 Pearl - Tmobile /Rom Ver.4.2.0.42 Blackberry 8100 Pearl AT&T /Rom Ver.4.2.1.96 yes yes yes yes yes yes yes yes yes no yes no no yes yes yes yes yes n/a n/a