Lp Quasi-Norm Minimization
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

On Quasi Norm Attaining Operators Between Banach Spaces
ON QUASI NORM ATTAINING OPERATORS BETWEEN BANACH SPACES GEUNSU CHOI, YUN SUNG CHOI, MINGU JUNG, AND MIGUEL MART´IN Abstract. We provide a characterization of the Radon-Nikod´ymproperty in terms of the denseness of bounded linear operators which attain their norm in a weak sense, which complement the one given by Bourgain and Huff in the 1970's. To this end, we introduce the following notion: an operator T : X ÝÑ Y between the Banach spaces X and Y is quasi norm attaining if there is a sequence pxnq of norm one elements in X such that pT xnq converges to some u P Y with }u}“}T }. Norm attaining operators in the usual (or strong) sense (i.e. operators for which there is a point in the unit ball where the norm of its image equals the norm of the operator) and also compact operators satisfy this definition. We prove that strong Radon-Nikod´ymoperators can be approximated by quasi norm attaining operators, a result which does not hold for norm attaining operators in the strong sense. This shows that this new notion of quasi norm attainment allows to characterize the Radon-Nikod´ymproperty in terms of denseness of quasi norm attaining operators for both domain and range spaces, completing thus a characterization by Bourgain and Huff in terms of norm attaining operators which is only valid for domain spaces and it is actually false for range spaces (due to a celebrated example by Gowers of 1990). A number of other related results are also included in the paper: we give some positive results on the denseness of norm attaining Lipschitz maps, norm attaining multilinear maps and norm attaining polynomials, characterize both finite dimensionality and reflexivity in terms of quasi norm attaining operators, discuss conditions to obtain that quasi norm attaining operators are actually norm attaining, study the relationship with the norm attainment of the adjoint operator and, finally, present some stability results. -
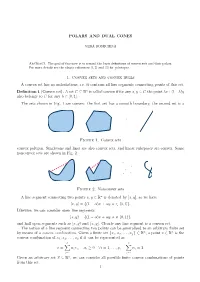
POLARS and DUAL CONES 1. Convex Sets
POLARS AND DUAL CONES VERA ROSHCHINA Abstract. The goal of this note is to remind the basic definitions of convex sets and their polars. For more details see the classic references [1, 2] and [3] for polytopes. 1. Convex sets and convex hulls A convex set has no indentations, i.e. it contains all line segments connecting points of this set. Definition 1 (Convex set). A set C ⊆ Rn is called convex if for any x; y 2 C the point λx+(1−λ)y also belongs to C for any λ 2 [0; 1]. The sets shown in Fig. 1 are convex: the first set has a smooth boundary, the second set is a Figure 1. Convex sets convex polygon. Singletons and lines are also convex sets, and linear subspaces are convex. Some nonconvex sets are shown in Fig. 2. Figure 2. Nonconvex sets A line segment connecting two points x; y 2 Rn is denoted by [x; y], so we have [x; y] = f(1 − α)x + αy; α 2 [0; 1]g: Likewise, we can consider open line segments (x; y) = f(1 − α)x + αy; α 2 (0; 1)g: and half open segments such as [x; y) and (x; y]. Clearly any line segment is a convex set. The notion of a line segment connecting two points can be generalised to an arbitrary finite set n n by means of a convex combination. Given a finite set fx1; x2; : : : ; xpg ⊂ R , a point x 2 R is the convex combination of x1; x2; : : : ; xp if it can be represented as p p X X x = αixi; αi ≥ 0 8i = 1; : : : ; p; αi = 1: i=1 i=1 Given an arbitrary set S ⊆ Rn, we can consider all possible finite convex combinations of points from this set. -

On the Ekeland Variational Principle with Applications and Detours
Lectures on The Ekeland Variational Principle with Applications and Detours By D. G. De Figueiredo Tata Institute of Fundamental Research, Bombay 1989 Author D. G. De Figueiredo Departmento de Mathematica Universidade de Brasilia 70.910 – Brasilia-DF BRAZIL c Tata Institute of Fundamental Research, 1989 ISBN 3-540- 51179-2-Springer-Verlag, Berlin, Heidelberg. New York. Tokyo ISBN 0-387- 51179-2-Springer-Verlag, New York. Heidelberg. Berlin. Tokyo No part of this book may be reproduced in any form by print, microfilm or any other means with- out written permission from the Tata Institute of Fundamental Research, Colaba, Bombay 400 005 Printed by INSDOC Regional Centre, Indian Institute of Science Campus, Bangalore 560012 and published by H. Goetze, Springer-Verlag, Heidelberg, West Germany PRINTED IN INDIA Preface Since its appearance in 1972 the variational principle of Ekeland has found many applications in different fields in Analysis. The best refer- ences for those are by Ekeland himself: his survey article [23] and his book with J.-P. Aubin [2]. Not all material presented here appears in those places. Some are scattered around and there lies my motivation in writing these notes. Since they are intended to students I included a lot of related material. Those are the detours. A chapter on Nemyt- skii mappings may sound strange. However I believe it is useful, since their properties so often used are seldom proved. We always say to the students: go and look in Krasnoselskii or Vainberg! I think some of the proofs presented here are more straightforward. There are two chapters on applications to PDE. -

The Ekeland Variational Principle, the Bishop-Phelps Theorem, and The
The Ekeland Variational Principle, the Bishop-Phelps Theorem, and the Brøndsted-Rockafellar Theorem Our aim is to prove the Ekeland Variational Principle which is an abstract result that found numerous applications in various fields of Mathematics. As its application to Convex Analysis, we provide a proof of the famous Bishop- Phelps Theorem and some related results. Let us recall that the epigraph and the hypograph of a function f : X ! [−∞; +1] (where X is a set) are the following subsets of X × R: epi f = f(x; t) 2 X × R : t ≥ f(x)g ; hyp f = f(x; t) 2 X × R : t ≤ f(x)g : Notice that, if f > −∞ on X then epi f 6= ; if and only if f is proper, that is, f is finite at at least one point. 0.1. The Ekeland Variational Principle. In what follows, (X; d) is a metric space. Given λ > 0 and (x; t) 2 X × R, we define the set Kλ(x; t) = f(y; s): s ≤ t − λd(x; y)g = f(y; s): λd(x; y) ≤ t − sg ⊂ X × R: Notice that Kλ(x; t) = hyp[t − λ(x; ·)]. Let us state some useful properties of these sets. Lemma 0.1. (a) Kλ(x; t) is closed and contains (x; t). (b) If (¯x; t¯) 2 Kλ(x; t) then Kλ(¯x; t¯) ⊂ Kλ(x; t). (c) If (xn; tn) ! (x; t) and (xn+1; tn+1) 2 Kλ(xn; tn) (n 2 N), then \ Kλ(x; t) = Kλ(xn; tn) : n2N Proof. (a) is quite easy. -

Chapter 5 Convex Optimization in Function Space 5.1 Foundations of Convex Analysis
Chapter 5 Convex Optimization in Function Space 5.1 Foundations of Convex Analysis Let V be a vector space over lR and k ¢ k : V ! lR be a norm on V . We recall that (V; k ¢ k) is called a Banach space, if it is complete, i.e., if any Cauchy sequence fvkglN of elements vk 2 V; k 2 lN; converges to an element v 2 V (kvk ¡ vk ! 0 as k ! 1). Examples: Let be a domain in lRd; d 2 lN. Then, the space C() of continuous functions on is a Banach space with the norm kukC() := sup ju(x)j : x2 The spaces Lp(); 1 · p < 1; of (in the Lebesgue sense) p-integrable functions are Banach spaces with the norms Z ³ ´1=p p kukLp() := ju(x)j dx : The space L1() of essentially bounded functions on is a Banach space with the norm kukL1() := ess sup ju(x)j : x2 The (topologically and algebraically) dual space V ¤ is the space of all bounded linear functionals ¹ : V ! lR. Given ¹ 2 V ¤, for ¹(v) we often write h¹; vi with h¢; ¢i denoting the dual product between V ¤ and V . We note that V ¤ is a Banach space equipped with the norm j h¹; vi j k¹k := sup : v2V nf0g kvk Examples: The dual of C() is the space M() of Radon measures ¹ with Z h¹; vi := v d¹ ; v 2 C() : The dual of L1() is the space L1(). The dual of Lp(); 1 < p < 1; is the space Lq() with q being conjugate to p, i.e., 1=p + 1=q = 1. -

Non-Linear Inner Structure of Topological Vector Spaces
mathematics Article Non-Linear Inner Structure of Topological Vector Spaces Francisco Javier García-Pacheco 1,*,† , Soledad Moreno-Pulido 1,† , Enrique Naranjo-Guerra 1,† and Alberto Sánchez-Alzola 2,† 1 Department of Mathematics, College of Engineering, University of Cadiz, 11519 Puerto Real, CA, Spain; [email protected] (S.M.-P.); [email protected] (E.N.-G.) 2 Department of Statistics and Operation Research, College of Engineering, University of Cadiz, 11519 Puerto Real (CA), Spain; [email protected] * Correspondence: [email protected] † These authors contributed equally to this work. Abstract: Inner structure appeared in the literature of topological vector spaces as a tool to charac- terize the extremal structure of convex sets. For instance, in recent years, inner structure has been used to provide a solution to The Faceless Problem and to characterize the finest locally convex vector topology on a real vector space. This manuscript goes one step further by settling the bases for studying the inner structure of non-convex sets. In first place, we observe that the well behaviour of the extremal structure of convex sets with respect to the inner structure does not transport to non-convex sets in the following sense: it has been already proved that if a face of a convex set intersects the inner points, then the face is the whole convex set; however, in the non-convex setting, we find an example of a non-convex set with a proper extremal subset that intersects the inner points. On the opposite, we prove that if a extremal subset of a non-necessarily convex set intersects the affine internal points, then the extremal subset coincides with the whole set. -

Convex Sets and Convex Functions 1 Convex Sets
Convex Sets and Convex Functions 1 Convex Sets, In this section, we introduce one of the most important ideas in economic modelling, in the theory of optimization and, indeed in much of modern analysis and computatyional mathematics: that of a convex set. Almost every situation we will meet will depend on this geometric idea. As an independent idea, the notion of convexity appeared at the end of the 19th century, particularly in the works of Minkowski who is supposed to have said: \Everything that is convex interests me." We discuss other ideas which stem from the basic definition, and in particular, the notion of a convex and concave functions which which are so prevalent in economic models. The geometric definition, as we will see, makes sense in any vector space. Since, for the most of our work we deal only with Rn, the definitions will be stated in that context. The interested student may, however, reformulate the definitions either, in an ab stract setting or in some concrete vector space as, for example, C([0; 1]; R)1. Intuitively if we think of R2 or R3, a convex set of vectors is a set that contains all the points of any line segment joining two points of the set (see the next figure). Here is the definition. Definition 1.1 Let u; v 2 V . Then the set of all convex combinations of u and v is the set of points fwλ 2 V : wλ = (1 − λ)u + λv; 0 ≤ λ ≤ 1g: (1.1) In, say, R2 or R3, this set is exactly the line segment joining the two points u and v. -

The Krein–Milman Theorem a Project in Functional Analysis
The Krein{Milman Theorem A Project in Functional Analysis Samuel Pettersson November 29, 2016 2. Extreme points 3. The Krein{Milman theorem 4. An application Outline 1. An informal example 3. The Krein{Milman theorem 4. An application Outline 1. An informal example 2. Extreme points 4. An application Outline 1. An informal example 2. Extreme points 3. The Krein{Milman theorem Outline 1. An informal example 2. Extreme points 3. The Krein{Milman theorem 4. An application Outline 1. An informal example 2. Extreme points 3. The Krein{Milman theorem 4. An application Convex sets and their \corners" Observation Some convex sets are the convex hulls of their \corners". Convex sets and their \corners" Observation Some convex sets are the convex hulls of their \corners". kxk1≤ 1 Convex sets and their \corners" Observation Some convex sets are the convex hulls of their \corners". kxk1≤ 1 Convex sets and their \corners" Observation Some convex sets are the convex hulls of their \corners". kxk1≤ 1 kxk2≤ 1 Convex sets and their \corners" Observation Some convex sets are the convex hulls of their \corners". kxk1≤ 1 kxk2≤ 1 Convex sets and their \corners" Observation Some convex sets are the convex hulls of their \corners". kxk1≤ 1 kxk2≤ 1 kxk1≤ 1 Convex sets and their \corners" Observation Some convex sets are the convex hulls of their \corners". kxk1≤ 1 kxk2≤ 1 kxk1≤ 1 x1; x2 ≥ 0 Convex sets and their \corners" Observation Some convex sets are not the convex hulls of their \corners". Convex sets and their \corners" Observation Some convex sets are not the convex hulls of their \corners". -

On the Variational Principle
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Elsevier - Publisher Connector JOURNAL OF MATHEMATICAL ANALYSIS AND APPLICATIONS 47, 324-353 (1974) On the Variational Principle I. EKELAND UER Mathe’matiques de la DC&ion, Waiver& Paris IX, 75775 Paris 16, France Submitted by J. L. Lions The variational principle states that if a differentiable functional F attains its minimum at some point zi, then F’(C) = 0; it has proved a valuable tool for studying partial differential equations. This paper shows that if a differentiable function F has a finite lower bound (although it need not attain it), then, for every E > 0, there exists some point u( where 11F’(uJj* < l , i.e., its derivative can be made arbitrarily small. Applications are given to Plateau’s problem, to partial differential equations, to nonlinear eigenvalues, to geodesics on infi- nite-dimensional manifolds, and to control theory. 1. A GENERAL RFNJLT Let V be a complete metric space, the distance of two points u, z, E V being denoted by d(u, v). Let F: I’ -+ 08u {+ co} be a lower semicontinuous function, not identically + 00. In other words, + oo is allowed as a value for F, but at some point w,, , F(Q) is finite. Suppose now F is bounded from below: infF > --co. (l-1) As no compacity assumptions are made, there need be no point where this infimum is attained. But of course, for every E > 0, there is some point u E V such that: infF <F(u) < infF + E. -

Convex Sets, Functions, and Problems
Convex Sets, Functions, and Problems Nick Henderson, AJ Friend (Stanford University) Kevin Carlberg (Sandia National Laboratories) August 13, 2019 1 Convex optimization Theory, methods, and software for problems exihibiting the characteristics below I Convexity: I convex : local solutions are global I non-convex: local solutions are not global I Optimization-variable type: I continuous : gradients facilitate computing the solution I discrete: cannot compute gradients, NP-hard I Constraints: I unconstrained : simpler algorithms I constrained : more complex algorithms; must consider feasibility I Number of optimization variables: I low-dimensional : can solve even without gradients I high-dimensional : requires gradients to be solvable in practice 2 Set Notation Set Notation 3 Outline Set Notation Convexity Why Convexity? Convex Sets Convex Functions Convex Optimization Problems Set Notation 4 Set Notation I Rn: set of n-dimensional real vectors I x ∈ C: the point x is an element of set C I C ⊆ Rn: C is a subset of Rn, i.e., elements of C are n-vectors I can describe set elements explicitly: 1 ∈ {3, "cat", 1} I set builder notation C = {x | P (x)} gives the points for which property P (x) is true n I R+ = {x | xi ≥ 0 for all i}: n-vectors with all nonnegative elements I set intersection N \ C = Ci i=1 is the set of points which are simultaneously present in each Ci Set Notation 5 Convexity Convexity 6 Outline Set Notation Convexity Why Convexity? Convex Sets Convex Functions Convex Optimization Problems Convexity 7 Convex Sets I C ⊆ Rn is -

Some Characterizations and Properties of the \Distance
SOME CHARACTERIZATIONS AND PROPERTIES OF THE DISTANCE TO ILLPOSEDNESS AND THE CONDITION MEASURE OF A CONIC LINEAR SYSTEM Rob ert M Freund MIT Jorge R Vera Catholic University of Chile Octob er Revised June Revised June Abstract A conic linear system is a system of the form P d nd x that solves b Ax C x C Y X where C and C are closed convex cones and the data for the system is d A b This system X Y iswellposed to the extent that small changes in the data A b do not alter the status of the system the system remains solvable or not Renegar dened the distance to illp osedness d to b e the smallest change in the data d A b for which the system P d d is illp osed ie d d is in the intersection of the closure of feasible and infeasible instances d A b of P Renegar also dened the condition measure of the data instance d as C d kdkd and showed that this measure is a natural extension of the familiar condition measure asso ciated with systems of linear equations This study presents two categories of results related to d the distance to illp osedness and C d the condition measure of d The rst category of results involves the approximation of d as the optimal value of certain mathematical programs We present ten dierent mathematical programs each of whose optimal values provides an approximation of d to within certain constants dep ending on whether P d is feasible or not and where the constants dep end on prop erties of the cones and the norms used The second category of results involves the existence of certain inscrib ed -

ECE 586: Vector Space Methods Lecture 22: Projection Onto Convex Sets
ECE 586: Vector Space Methods Lecture 22: Projection onto Convex Sets Henry D. Pfister Duke University 5.3: Convexity Convexity is a useful property defined for sets, spaces, and functionals that simplifies analysis and optimization. Definition (convex set) Let V be a vector space over R. The subset A ⊆ V is called a convex set if, for all a1; a2 2 A and λ 2 (0; 1), we have λa1 + (1 − λ)a2 2 A. It is strictly convex if, for all ◦ a1; a2 2 A and λ 2 (0; 1), λa1 + (1 − λ)a2 2 A . Definition (convex function) Let V be a vector space, A ⊆ V be a convex set, and 1 f : V ! R be a functional. The functional f is called convex on A if, for all a1; a2 2 A and λ 2 (0; 1), −1 1 2 f (λa1 + (1 − λ)a2) ≤ λf (a1) + (1 − λ)f (a2): −1 It is strictly convex if equality implies a = a . 1 2 1 / 5 5.3: Convex Optimization Definition Let (X ; k · k) be a normed vector space. Then, a real functional f : X ! R achieves a local minimum value at x 0 2 X if: there is an > 0 such that, for all x 2 X satisfying kx − x 0k < , we have f (x) ≥ f (x 0). If this lower bound holds for all x 2 X , then the local minimum is also a global minimum value. Theorem Let (X ; k · k) be a normed vector space, A ⊆ X be a convex set, and f : X ! R be a convex functional on A.