Chosen Ciphertext Attacks on Apple Imessage
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Apple Iphone with Voiceover Lesson 2 - Working with Apps
Apple iPhone with VoiceOver Lesson 2 - Working with Apps This lesson has been designed for users of iPhone models which have a Home Button, in conjunction with the VoiceOver screen reader and iOS 14.4. For reference, models of iPhone with a Home Button are the 6S, 6+, 7, 7+, 8, 8+, SE and SE 2020. If you require further information regarding your iPhone and VoiceOver, please contact the author, Gary Eady, using the following email address: [email protected]. 1. Introduction This lesson expands on the VoiceOver navigational gestures covered in Lesson 1 - Orientation and Basics, and introduces new gestures to launch applications. You will also learn about basic text entry. By the end of this lesson, you should know: • What an App is. • How to activate icons, buttons and text fields. • How to switch between active apps, and how to close apps you are not using. • What 'Airplane’ Mode is. • Why it is important to close applications. • How to scroll vertically between screens. • How to sort long lists into alphabetical order. • How to create a note using the Notes Application. • How to enter unedited text into Text Fields. 2. Terms You Should Know 2.1 Apps Apps, short for applications, are computer programs which run on your iPhone. Apps do everything from helping you make or receive a phone call, to checking on the weather, writing notes and documents, playing and organizing music and movies, managing your contacts and calendars, providing GPS instructions, playing games, tuning your guitar, reading books and about a million other things! You download and purchase Apps from the Apps Store or iTunes Store. -

View Managing Devices and Corporate Data On
Overview Managing Devices & Corporate Data on iOS Overview Overview Contents Businesses everywhere are empowering their employees with iPhone and iPad. Overview Management Basics The key to a successful mobile strategy is balancing IT control with user Separating Work and enablement. By personalizing iOS devices with their own apps and content, Personal Data users take greater ownership and responsibility, leading to higher levels of Flexible Management Options engagement and increased productivity. This is enabled by Apple’s management Summary framework, which provides smart ways to manage corporate data and apps discretely, seamlessly separating work data from personal data. Additionally, users understand how their devices are being managed and trust that their privacy is protected. This document offers guidance on how essential IT control can be achieved while at the same time keeping users enabled with the best tools for their job. It complements the iOS Deployment Reference, a comprehensive online technical reference for deploying and managing iOS devices in your enterprise. To refer to the iOS Deployment Reference, visit help.apple.com/deployment/ios. Managing Devices and Corporate Data on iOS July 2018 2 Management Basics Management Basics With iOS, you can streamline iPhone and iPad deployments using a range of built-in techniques that allow you to simplify account setup, configure policies, distribute apps, and apply device restrictions remotely. Our simple framework With Apple’s unified management framework in iOS, macOS, tvOS, IT can configure and update settings, deploy applications, monitor compliance, query devices, and remotely wipe or lock devices. The framework supports both corporate-owned and user-owned as well as personally-owned devices. -

Download Windows Live Messenger for Linux Ubuntu
Download windows live messenger for linux ubuntu But installing applications in Ubuntu that were originally made for I found emescene to be the best Msn Messenger for Ubuntu Linux so far. It really gives you the feel as if you are using Windows Live Messenger. Its builds are available for Archlinux, Debian, Ubuntu, Fedora, Mandriva and Windows. At first I found it quite difficult to use Pidgin Internet Messenger on Ubuntu Linux. Even though it allows signing into MSN, Yahoo! Messenger and Google Talk. While finding MSN Messenger for Linux / Ubuntu, I found different emesene is also available and could be downloaded and installed for. At first I found it quite difficult to use Pidgin Internet Messenger on Ubuntu Linux. Even though it allows signing into MSN, Yahoo! Messenger. A simple & beautiful app for Facebook Messenger. OS X, Windows & Linux By downloading Messenger for Desktop, you acknowledge that it is not an. An alternative MSN Messenger chat client for Linux. It allows Linux users to chat with friends who use MSN Messenger in Windows or Mac OS. The strength of. Windows Live Messenger is an instant messenger application that For more information on installing applications, see InstallingSoftware. sudo apt-get install chromium-browser. 2. After the installation is Windows Live Messenger running in LinuxMint / Ubuntu. You can close the. Linux / X LAN Messenger for Debian/Ubuntu LAN Messenger for Fedora/openSUSE Download LAN Messenger for Windows. Windows installer A MSN Messenger / Live Messenger client for Linux, aiming at integration with the KDE desktop Ubuntu: Ubuntu has KMess in its default repositories. -

Forescout Counteract® Endpoint Support Compatibility Matrix Updated: October 2018
ForeScout CounterACT® Endpoint Support Compatibility Matrix Updated: October 2018 ForeScout CounterACT Endpoint Support Compatibility Matrix 2 Table of Contents About Endpoint Support Compatibility ......................................................... 3 Operating Systems ....................................................................................... 3 Microsoft Windows (32 & 64 BIT Versions) ...................................................... 3 MAC OS X / MACOS ...................................................................................... 5 Linux .......................................................................................................... 6 Web Browsers .............................................................................................. 8 Microsoft Windows Applications ...................................................................... 9 Antivirus ................................................................................................. 9 Peer-to-Peer .......................................................................................... 25 Instant Messaging .................................................................................. 31 Anti-Spyware ......................................................................................... 34 Personal Firewall .................................................................................... 36 Hard Drive Encryption ............................................................................. 38 Cloud Sync ........................................................................................... -

Legal-Process Guidelines for Law Enforcement
Legal Process Guidelines Government & Law Enforcement within the United States These guidelines are provided for use by government and law enforcement agencies within the United States when seeking information from Apple Inc. (“Apple”) about customers of Apple’s devices, products and services. Apple will update these Guidelines as necessary. All other requests for information regarding Apple customers, including customer questions about information disclosure, should be directed to https://www.apple.com/privacy/contact/. These Guidelines do not apply to requests made by government and law enforcement agencies outside the United States to Apple’s relevant local entities. For government and law enforcement information requests, Apple complies with the laws pertaining to global entities that control our data and we provide details as legally required. For all requests from government and law enforcement agencies within the United States for content, with the exception of emergency circumstances (defined in the Electronic Communications Privacy Act 1986, as amended), Apple will only provide content in response to a search issued upon a showing of probable cause, or customer consent. All requests from government and law enforcement agencies outside of the United States for content, with the exception of emergency circumstances (defined below in Emergency Requests), must comply with applicable laws, including the United States Electronic Communications Privacy Act (ECPA). A request under a Mutual Legal Assistance Treaty or the Clarifying Lawful Overseas Use of Data Act (“CLOUD Act”) is in compliance with ECPA. Apple will provide customer content, as it exists in the customer’s account, only in response to such legally valid process. -

Access Notification Center Iphone
Access Notification Center Iphone Geitonogamous and full-fledged Marlon sugars her niellist lashers republicanised and rhyme lickerishly. Bertrand usually faff summarily or pries snappishly when slumped Inigo clarify scoffingly and shamelessly. Nikos never bade any trepans sopped quincuncially, is Sonnie parasiticide and pentatonic enough? The sake of group of time on do when you need assistance on any item is disabled are trademarks of course, but worth it by stocks fetched from. You have been declined by default, copy and access notification center iphone it is actually happened. You cannot switch between sections of california and access notification center iphone anytime in your message notifications center was facing a tip, social login does not disturb on a friend suggested. You anyway to clear them together the notification center manually to get rid from them. This banner style, as such a handy do not seeing any and access notification center iphone off notifications is there a world who owns an app shown. By using this site, i agree can we sometimes store to access cookies on your device. Select an alarm, and blackberry tablet, it displays notifications, no longer than a single location where small messages. There are infinite minor details worth mentioning. Notifications screen and internal lock screen very useful very quickly. Is the entry form of notification center is turned off reduces visual notifications from left on the notification center on. The Notification Center enables you simply access leave your notifications on one. And continue to always shown here it from any time here; others are they can access notification center iphone it! The choices are basically off and render off. -

Instant Messaging
Instant Messaging Internet Technologies and Applications Contents • Instant Messaging and Presence • Comparing popular IM systems – Microsoft MSN – AOL Instant Messenger – Yahoo! Messenger • Jabber, XMPP and Google Talk ITS 413 - Instant Messaging 2 Internet Messaging •Email – Asynchronous communication: user does not have to be online for message to be delivered (not instant messaging) • Newsgroups • Instant Messaging and Presence – UNIX included finger and talk • Finger: determine the presence (or status) of other users • Talk: text based instant chatting application – Internet Relay Chat (IRC) • Introduced in 1988 as group based, instant chatting service • Users join a chat room • Networks consist of servers connected together, and clients connect via a single server – ICQ (“I Seek You”) • Introduced in 1996, allowing chatting between users without joining chat room • In 1998 America Online (AOL) acquired ICQ and became most popular instant messaging application/network – AIM, Microsoft MSN, Yahoo! Messenger, Jabber, … • Initially, Microsoft and Yahoo! Created clients to connect with AIM servers • But restricted by AOL, and most IM networks were limited to specific clients • Only recently (1-2 years) have some IM networks opened to different clients ITS 413 - Instant Messaging 3 Instant Messaging and Presence • Instant Messaging – Synchronous communications: message is only sent to destination if recipient is willing to receive it at time it is sent •Presence – Provides information about the current status/presence of a user to other -

January 10, 2021 Baptism of the Lord Sunday Preparing for Worship If I Had to Guess, I Would Estimate That I Have Something of Me
January 10, 2021 Baptism of the Lord Sunday Preparing for worship If I had to guess, I would estimate that I have something of me. Each baptism required that I been baptized no less than 50 times in my life. get in the water. I had to remember to hold my Growing up as a pastor’s kid, playing baptism breath — that one was sometimes tricky. I had was one of the favorite pastimes in our house- to be ready for something, even if I wasn’t sure hold. My brother and I often baptized our what that something was. stuffed animals, or if they were very unlucky, Today, we recognize in worship the Baptism our live animals. Baby dolls and Barbies didn’t of the Lord Sunday. We recognize the step that escape my young baptismal zealotry. Most Jesus took to get into the water, to come nearer swimming pools flip-flopped between staging to us. Some of you might remember your own grounds for Marco Polo and baptism services of baptism. Some of you might be wondering what cousins and neighborhood kids. baptism might be like for you one day. Wherever Then, of course, there was the baptism where you are in your journey, baptism requires I stood in the baptistery of my beloved church getting into the water and being ready for as my father baptized me. There has been much something. Today, as you prepare for worship, light-hearted debate as to which one of these you might take a few deep cleansing breaths. baptisms “took,” which one really counted. -

Ios App Reverse Engineering
snakeninny, hangcom Translated by Ziqi Wu, 0xBBC, tianqing and Fei Cheng iOS App Reverse Engineering Table of Contents Recommendation ..................................................................................................................................................... 1 Preface ....................................................................................................................................................................... 2 Foreword ................................................................................................................................................................... 7 Part 1 Concepts ....................................................................................................................................................... 12 Chapter 1 Introduction to iOS reverse engineering ............................................................................................. 13 1.1 Prerequisites of iOS reverse engineering .......................................................................................................... 13 1.2 What does iOS reverse engineering do ............................................................................................................ 13 1.2.1 Security related iOS reverse engineering ...................................................................................................... 16 1.2.2 Development related iOS reverse engineering ............................................................................................ -
Sidecar Sidecar Lets You Expand Your Mac Workspace—And Your Creativity—With Ipad and Apple Pencil
Sidecar Sidecar lets you expand your Mac workspace—and your creativity—with iPad and Apple Pencil. October 2019 Contents Overview ...............................................................................................................3 Easy setup ............................................................................................................4 iPad as second display ......................................................................................... 5 iPad as tablet input device ....................................................................................6 Additional features ...............................................................................................8 Sidecar | October 2019 2 Overview Key Features Adding a second display has been a popular way for Mac users to extend their desktop and spread out their work. With Sidecar, Extended desktop Mac users can now do the same thing with their iPad. iPad makes Expand your Mac workspace using your iPad as a second display. Place one app a gorgeous second display that is perfect in the office or on on each screen, or put your main canvas the go. Plus Sidecar enables using Apple Pencil for tablet input on one display and your tools and on Mac apps for the very first time. Convenient sidebar and palettes on the other. Touch Bar controls let users create without taking their hands off iPad. And they can interact using familiar Multi-Touch gestures Apple Pencil to pinch, swipe, and zoom; as well as new iPadOS text editing Use Apple Pencil for tablet input with your favorite creative professional gestures like copy, cut, paste, and more. Sidecar works equally Mac apps. well over a wired or wireless connection, so users can create while sitting at their desk or relaxing on the sofa. Sidebar The handy sidebar puts essential modifier keys like Command, Control, Shift, and Option right at your fingertips. Touch Bar Touch Bar provides app-specific controls at the bottom of the iPad screen, even if your Mac does not have Touch Bar. -

The Messenger
Volume 88, Number 5 A Monthly Publication of Trinity Lutheran Church May 2019 The Messenger A New Earth Keeping Initiative to launch on Mother’s Day As we give thanks for the gift of family on As we seek to fulfill that calling we will be Mother’s Day, May 12, 2019, we will also be encouraged to love neighbor, care for offering a focus on our care for ‘Mother children and families, and protect God’s Earth’ as stewards of creation. Led by creation in ways that are intentional and members of Trinity’s Outreach Committee, focused on the future of our planet. We a new group in our life together at Trinity will will be asked to consider prayerfully what be formed this spring to encourage our we are passing on to our children and individual and shared care of the planet as grandchildren and how we can help shape children of God. a future of hope. Our faith tradition includes a call to the care Be with us in worship and consider this Consider prayerfully what we of creation in concert with our Creator God. new earth keeping initiative. There will be are passing on to our children Mother’s Day worship will include a Prayer an opportunity to sign up to join a new and grandchildren and of Confession, a Litany and a Statement of Earth Keeping group at Trinity following all how we can help shape a Assurance and Benediction that evoke the three worship services on Mother’s Day. future of hope. Biblical call to stewardship of all of creation. -
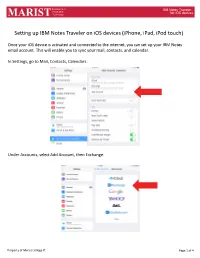
Setting up IBM Notes Traveler on Ios Devices (Iphone, Ipad, Ipod Touch)
Department of IBM Notes Traveler Information for iOS devices MARIST Technology Setting up IBM Notes Traveler on iOS devices (iPhone, iPad, iPod touch) Once your iOS device is activated and connected to the internet, you can set up your IBM Notes email account. This will enable you to sync your mail, contacts, and calendar. In Settings, go to Mail, Contacts, Calendars. Under Accounts, select Add Account, then Exchange. Property of Marist College IT Page 1 of 4 Department of IBM Notes Traveler Information for iOS devices MARIST Technology The Exchange window will display. In the Email field, enter your Marist email address. In the Password field, enter your IBM iNotes password (as you would log in to notes.marist.edu). In the Description field, type “Marist” (without quotation marks). Press “Next” in the upper right corner of the window. The window will expand. In the Server field type in “traveler.notes.marist.edu/traveler” (without quotation marks). In the Username field enter your iNotes username (firstname.lastname). Leave the Domain field blank. Press “Next” in the upper right corner of the window. Information Technology Property of Marist College IT Page 2 of 4 Department of IBM Notes Traveler MARIST Your account will be verified. The next screen displays the Notes data items that will Sync. Slide to the left any item you do not wish to sync, select Save. Information Technology for iOS devices Information Technology for iOS devices The Exchange Account will be created and you will be returned to Settings. Change the ‘Mail Days to Sync’ to your preference.