Academic Council: 26/07/2019
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

"SOLIZE India Technologies Private Limited" 56553102 .FABRIC 34354648 @Fentures B.V
Erkende referenten / Recognised sponsors Arbeid Regulier en Kennismigranten / Regular labour and Highly skilled migrants Naam bedrijf/organisatie Inschrijfnummer KvK Name company/organisation Registration number Chamber of Commerce "@1" special projects payroll B.V. 70880565 "SOLIZE India Technologies Private Limited" 56553102 .FABRIC 34354648 @Fentures B.V. 82701695 01-10 Architecten B.V. 24257403 100 Grams B.V. 69299544 10X Genomics B.V. 68933223 12Connect B.V. 20122308 180 Amsterdam BV 34117849 1908 Acquisition B.V. 60844868 2 Getthere Holding B.V. 30225996 20Face B.V. 69220085 21 Markets B.V. 59575417 247TailorSteel B.V. 9163645 24sessions.com B.V. 64312100 2525 Ventures B.V. 63661438 2-B Energy Holding 8156456 2M Engineering Limited 17172882 30MHz B.V. 61677817 360KAS B.V. 66831148 365Werk Contracting B.V. 67524524 3D Hubs B.V. 57883424 3DUniversum B.V. 60891831 3esi Netherlands B.V. 71974210 3M Nederland B.V. 28020725 3P Project Services B.V. 20132450 4DotNet B.V. 4079637 4People Zuid B.V. 50131907 4PS Development B.V. 55280404 4WEB EU B.V. 59251778 50five B.V. 66605938 5CA B.V. 30277579 5Hands Metaal B.V. 56889143 72andSunny NL B.V. 34257945 83Design Inc. Europe Representative Office 66864844 A. Hak Drillcon B.V. 30276754 A.A.B. International B.V. 30148836 A.C.E. Ingenieurs en Adviesbureau, Werktuigbouw en Electrotechniek B.V. 17071306 A.M. Best (EU) Rating Services B.V. 71592717 A.M.P.C. Associated Medical Project Consultants B.V. 11023272 A.N.T. International B.V. 6089432 A.S. Watson (Health & Beauty Continental Europe) B.V. 31035585 A.T. Kearney B.V. -

Quarterly Enterprise Software Market Review 1Q 2019
Quarterly Enterprise Software Market Review 1Q 2019 Boston San Francisco 200 Clarendon Street, Floor 45 601 Montgomery Street, Suite 2010 Boston, MA 02116 San Francisco, CA 94111 Peter M. Falvey Michael H.M. Shea Christopher J. Pingpank Michael S. Barker Managing Director Managing Director Managing Director Managing Director 617.896.2251 617.896.2255 617.896.2218 415.762.8101 [email protected] [email protected] [email protected] [email protected] Jeffrey G. Cook Brad E. McCarthy Misha Cvetkovic Principal Principal Vice President 617.896.2252 617.896.2245 415.762.8104 [email protected] [email protected] [email protected] www.shea-co.com Member FINRA & SIPC Copyright ©2019 Shea & Company Overview People ▪ Industry Expertise ▪ Process Excellence 1 2 24 15+ >70 Firm focused exclusively Offices in Boston and San Professionals focused on Years of experience Transactions completed on enterprise software Francisco the software industry amongst our senior representing billions of bankers dollars in value Mergers & Acquisitions Private Placements & Capital Raising Corporate Strategy ■ Sell-side and buy-side M&A advisory ■ Late-stage venture, growth equity and buyouts ■ Corporate development advisory ■ Divestitures ■ Recapitalizations ■ Balance sheet and capital structure review ■ Restructuring ■ IPO advisory ■ Fairness opinions has received an investment from has received an investment from Superior Outcomes has been acquired by has acquired Shea & Company has advised on important transactions representing billions of dollars in -

Cloud Native Go
Cloud Native Go Building Web Applications and Microservices for the Cloud with Go and React Kevin Hoffman Dan Nemeth AAddison-Wesley Boston • Columbus • Indianapolis • New York • San Francisco • Amsterdam • Cape Town Dubai • London • Madrid • Milan • Munich • Paris • Montreal • Toronto • Delhi Mexico City • Sao Paulo • Sidney • Hong Kong • Seoul • Singapore • Taipei • Tokyo Contents at a Glance 1 The Way of the Cloud 1 2 Getting Started ll 3 Go Primer 17 4 Delivering Continuously 35 5 Building Microservices in Go 53 6 Using Backing Services 71 7 Creating a Data Service 95 8 Event Sourcing and CQRS 113 9 Building a Web Application with Go 137 10 Security in the Cloud 151 11 Working with WebSockets 167 12 Building Web Views with React 177 13 Creating Ills that Scale with Flux 195 14 Creating a Full Application—World of FluxCraft 209 15 Conclusion 223 A Troubleshooting Cloud Applications 227 Index 231 NOTE: To register this product and gain access to bonus content, go to www.informit.com/register to sign in and enter the ISBN. After you register the product, a link to the additional content will be listed on your Account page, under Registered Products. Contents 1 The Way of the Cloud 1 The Virtues of the Way of the Cloud 2 Favor Simplicity 2 Test First, Test Everything 3 Release Early, Release Often 5 Automate Everything 6 Build Service Ecosystems 7 Why Use Go? 8 Simplicity 8 Open Source 8 Easy Automation and IDE Freedom 9 Summary 9 2 Getting Started 11 The Right Tools for the Job 11 Setting Up Git 12 Installing Homebrew 12 Installing the -

Syllabus for M.Sc. Part I (Semester I and II) Programme: M.Sc
Academic Council: 26/07/2019 Item No: 4.76 UNIVERSITY OF MUMBAI Syllabus for M.Sc. Part I (Semester I and II) Programme: M.Sc. Subject: Information Technology (Choice Based Credit System with effect from the academic year 2019 – 2020) Semester – I Course Code Course Title Credits PSIT101 Research in Computing 4 PSIT102 Data Science 4 PSIT103 Cloud Computing 4 PSIT104 Soft Computing Techniques 4 PSIT1P1 Research in Computing Practical 2 PSIT1P2 Data Science Practical 2 PSIT1P3 Cloud Computing Practical 2 PSIT1P4 Soft Computing Techniques Practical 2 Total Credits 24 Semester – II Course Code Course Title Credits PSIT201 Big Data Analytics 4 PSIT202 Modern Networking 4 PSIT203 Microservices Architecture 4 PSIT204 Image Processing 4 PSIT2P1 Big Data Analytics Practical 2 PSIT2P2 Modern Networking Practical 2 PSIT2P3 Microservices Architecture Practical 2 PSIT2P4 Image Processing Practical 2 Total Credits 24 2 Program Specific Outcomes PSO1: Ability to apply the knowledge of Information Technology with recent trends alignedwith research and industry. PSO2: Ability to apply IT in the field of Computational Research, Soft Computing, Big Data Analytics, Data Science, Image Processing, Artificial Intelligence, Networking and Cloud Computing. PSO3: Ability to provide socially acceptable technical solutions in the domains of Information Security, Machine Learning, Internet of Things and Embedded System, Infrastructure Services as specializations. PSO4: Ability to apply the knowledge of Intellectual Property Rights, Cyber Laws and Cyber Forensics and various standards in interest of National Security and Integrity along with IT Industry. PSO5: Ability to write effective project reports, research publications and content development and to work in multidisciplinary environment in the context of changing technologies. -

Choosing the Right Vendor for Application Development
Choosing the Right Vendor for Application Development Customer Experiences with Amazon, Oracle, and Pivotal Cloud Services August 2018 THE DEVELOPMENT OF THIS WHITE PAPER WAS SPONSORED BY ORACLE. THE UNDERLYING RESEARCH AND ANALYSIS WERE EXECUTED INDEPENDENTLY BY PIQUE SOLUTIONS. 795 Folsom Street, 1st Floor | San Francisco, CA 94107 | Tel.: 415.685.3392 | www.piquesolutions.com Application Development in the Cloud Contents Executive Summary ........................................................................................................................ 1 Introduction .................................................................................................................................... 3 Cloud Providers Take Different Approaches ............................................................................... 4 Amazon ................................................................................................................................... 4 Oracle ...................................................................................................................................... 4 Pivotal ..................................................................................................................................... 4 Study Approach ............................................................................................................................... 5 Methodology ............................................................................................................................... 5 AppDev -

Oracle Application Development in the Cloud
Oracle Cloud DevOps Enrique Martin Casado Presales Director Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | Agenda • Oracle & DevOpc • Tools – Developer Cloud Service – Wercker (CI/CD) • Container Native Cloud Service • Database in CI/CD Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | Oracle & Open Source and Community for Container Native • Oracle’s participation in open source community Active Community Participation – Active Participation – Cloud Native Compute Foundation and Kubernetes – No forked code – straight from the source • Lead by example Innovate in Open Source – Oracle software on Docker Store – Kubernetes engineering in CNCF • Innovate in open source OpenJDK 4 Containers Kubernetes – Container utilities like smith, railcar, crashcart Open Sourcing Docker Utilities • Sponsor & contribute to key conferences – DockerCon, Kubecon, CoreOS Fest smith crashcart railcar Copyright © 2015 Oracle and/or its affiliates. All rights reserved. | 3 Active Open Source Contribution of Container Based Solutions from Oracle Development smith railcar crashcart A simple command line utility Alternative Docker A simple command line for building runtime implemented utility that lets you side load microcontainers from rpm in Rust following the an image with linux binaries packages or oci images. Open Container Initiative into an existing container. OCI-Runtime Spec Facilitates easier debugging Copyright © 2015 Oracle and/or its affiliates. All rights reserved. | 4 Oracle in Docker Store 1 of 8 results for Oracle. Clear search Copyright © 2015 Oracle and/or its affiliates. All rights reserved. | 5 DevOps • DevOps is a culture, movement or Plan practice that emphasizes the Monitor Code collaboration and communication of both software developers and other information-technology (IT) professionals while automating the process of software delivery and infrastructure changes. -
Disrupting Devops Infographic
How Containers are Disrupting DevOps DevOps is implemented through continuous delivery software pipeline. Continuous delivery encompasses continuous development, integration and deployment. With the rapid adoption of containers we asked ourselves, “How do containers redefine DevOps?” CONTAINERS MAKE CONTAINERS MAKE ENVIRONMENTS CONSISTENT TOOLING CONSISTENT Containers provide a common set of building blocks Containers provide a disposable, reusable unit that can that can be reused in any stage of development to execute a segment of a delivery pipeline. Critical code recreate identical environments for development, quality, analysis, build, and test functions can be testing, staging, and production. Containers extend consistently reused within developer workspaces, the idea of write once; deploy anywhere, to an continuous integration systems, and release management infrastructure abstraction that application tools. Service injection into containers allows developers developers can easily consume and operations to code more productively and tooling vendors to provide professionals can predictably manage. value throughout the pipeline. CODE & IMAGE LIFECYCLE WITH CONTAINERS Containers defined by recipes allow developers to edit, version and commit changes in the same way they do code leading to a similar (and sometimes dependent) image lifecycle. THE CODE LIFECYCLE THE IMAGE LIFECYCLE 1 CLONE 1 CLONE 2 EDIT 2 EDIT 3 ANALYZE 4 BUILD DEPENDENCY 3 BUILD ARTIFACTS AND 5 PACKAGE SOURCE INJECTED 6 RUN 7 DEBUG 8 COMMIT 4 LABEL 9 PUSH 5 PUSH CONTINUOUS -
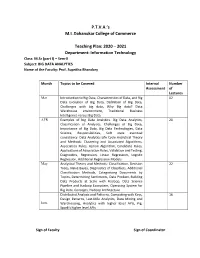
2020 – 2021 Department: Information Technology Class: M.Sc (Part I) – Sem-II Subject: BIG DATA ANALYTICS Name of the Faculty: Prof
P.T.V.A.’s M.L.Dahanukar College of Commerce Teaching Plan: 2020 – 2021 Department: Information Technology Class: M.Sc (part I) – Sem-II Subject: BIG DATA ANALYTICS Name of the Faculty: Prof. Supritha Bhandary Month Topics to be Covered Internal Number Assessment of Lectures Mar Introduction to Big Data, Characteristics of Data, and Big 02 Data Evolution of Big Data, Definition of Big Data, Challenges with big data, Why Big data? Data Warehouse environment, Traditional Business Intelligence versus Big Data. APR Examples of big Data Analytics. Big Data Analytics, 20 Classification of Analytics, Challenges of Big Data, Importance of Big Data, Big Data Technologies, Data Science, Responsibilities, Soft state eventual consistency. Data Analytics Life Cycle Analytical Theory and Methods: Clustering and Associated Algorithms, Association Rules, Apriori Algorithm, Candidate Rules, Applications of Association Rules, Validation and Testing, Diagnostics, Regression, Linear Regression, Logistic Regression, Additional Regression Models May Analytical Theory and Methods: Classification, Decision 22 Trees, Naïve Bayes, Diagnostics of Classifiers, Additional Classification Methods, Categorizing Documents by Topics, Determining Sentiments, Data Product, Building Data Products at Scale with Hadoop, Data Science Pipeline and Hadoop Ecosystem, Operating System for Big Data, Concepts, Hadoop Architecture Distributed Analysis and Patterns, Computing with Keys, 16 Design Patterns, Last-Mile Analytics, Data Mining and June Warehousing, Analytics with higher -

Improving Resource Efficiency of Container-Instance Clusters On
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by St Andrews Research Repository Improving Resource Efficiency of Container-instance Clusters on Clouds Uchechukwu Awada and Adam Barker School of Computer Science University of St Andrews St Andrews, Scotland, UK Email: fua5, [email protected] Abstract—Cloud computing providers such as Amazon and a typical Docker use case involves running five containers per Google have recently begun offering container-instances, which host, but that many organisations run 10 or more. provide an efficient route to application deployment within a Efficiently deploying and orchestrating containerised ap- lightweight, isolated and well-defined execution environment. Cloud providers currently offer Container Service Platforms plications across distributed clouds is important to both de- (CSPs), which orchestrate containerised applications. velopers and cloud providers. Cloud providers (i.e., AWS3, Existing CSP frameworks do not offer any form of intel- Google Compute Engine4) currently offer Container Service ligent resource scheduling: applications are usually scheduled Platforms (CSPs)5;6, which support the flexible orchestration individually, rather than taking a holistic view of all registered of containerised applications. applications and available resources in the cloud. This can result in increased execution times for applications, resource wastage Existing CSP frameworks do not offer any form of intelli- through underutilised container-instances, and a reduction in the gent resource scheduling: applications are usually scheduled number of applications that can be deployed, given the available individually, rather than taking a holistic view of all regis- resources. tered applications and available resources in the cloud. -

Guide to the Open Cloud Current Trends and Open Source Projects
Guide to the Open Cloud Current trends and open source projects November 2016 AUTHORS Libby Clark and Mark Hinkle The Linux Foundation www.linuxfoundation.org Contents Introduction 3 What is the Open Cloud Today, Why It’s Important, and How It’s Advancing 5 Emerging Trends 6 Cloud Native Applications 6 Containers 7 Unikernels 7 Why is the Open Cloud Important? 7 Profile Methodology 9 Profiles 11 Infrastructure as a Service (IaaS) 11 Platform as a Service (PaaS) 12 Virtualization, Containers and Cloud Operating Systems 13 Micro or Minimalist OSes 13 Virtualization 14 Management and Automation 15 Unikernels 17 DevOps CI/CD 19 Complete CI/CD cycle 19 Configuration management 20 Logging and Monitoring 21 Software-Defined Networking (SDN) 22 Networking for containers 23 Software-Defined Storage 24 2 Guide to the Open Cloud: Current trends and open source projects Introduction This third annual Guide to the Open Cloud aims to help companies stay informed on the latest open source cloud technologies and trends. The Linux Foundation’s cloud experts have curated a list of the most useful, influential, and promising open source projects with which IT managers and practitioners can build, manage, and monitor their current and future mission-critical cloud resources. In doing so, we’re also helping companies identify projects they can best leverage for external R&D through strategic open source participation. Contributing knowledge and code to open source projects not only helps companies meet their business objectives, but it creates thriving communities that keep projects strong and relevant over time, advances the technology, and benefits the entire open source cloud ecosystem. -

Ebook-Monitoring-Docker-Containers
vol.5 MONITORING & MANAGEMENT WITH DOCKER & CONTAINERS EDITED & CURATED BY ALEX WILLIAMS The New Stack: The Docker and Container Ecosystem Ebook Series Alex Williams, Founder & Editor-in-Chief Benjamin Ball, Technical Editor & Producer Gabriel Hoang Dinh, Creative Director Lawrence Hecht, Data Research Director Contributors: Judy Williams, Copy Editor Luke Lefler, Audio Engineer Norris Deajon, Audio Engineer v 5.2 TABLE OF CONTENTS Sponsors ...........................................................................................................................4 Introduction .....................................................................................................................5 MONITORING & MANAGEMENT WITH DOCKER & CONTAINERS Monitoring Reset for Containers...................................................................................8 IBM: Creating Analytics-Driven Solutions for Operational Visibility ....................23 Classes of Container Monitoring ................................................................................24 Docker: Building On Docker’s Native Monitoring Functionality ...........................40 Identifying and Collecting Container Data ...............................................................41 Sysdig: The Importance of Having Visibility Into Containers ................................55 The Right Tool for the Job: Picking a Monitoring Solution ...................................56 Cisco: Understanding the Application Pattern for Effective Monitoring ............63 Managing Intentional -

Oracle and the Modern Age of Microservices
Von Java EE zu Cloud Native und Microservices Peter Doschkinow Software Architekt und Sales Consultant ORACLE Deutschland B.V. & Co. KG November 2017 Copyright © 2017, Oracle and/or its affiliates. All rights reserved. Safe Harbor Statement The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon in making purchasing decisions. The development, release, and timing of any features or functionality described for Oracle’s products remains at the sole discretion of Oracle. Copyright © 2017, Oracle and/or its affiliates. All rights reserved. 3 Agenda • Demo App – realtime collaborative drawing web application: github.com/doschkinow – Implemented as a classic Java EE 7 based monolitic app, deployed in Java Cloud Service – Migrating to a lightweight cloud native app – Decomposing into two microservices with different implementations – Java and Node.js • with deployment on Application Container Cloud Service – Factoring out the app state in a third microservice, using In-Memory Data-Grid • with deployment in Kubernetes Cluster • with deployment in a Docker Swarm • Showcasing – Java Cloud Service (JCS) – Application Container Cloud Service (ACCS) – Developer Cloud Service (DevCS), Wercker Container Native Pipelines – Oracle Container Native App Platform Copyright © 2017, Oracle and/or its affiliates. All rights reserved. Drawing Board Demo: HTML5 Java EE App • Collaborative realtime drawing • Two-page application – CRUD for a list of drawings – Single drawing • Demonstrating – Server-side • Java EE 7: JAX-RS, WebSocket, JSON-P • Jersey specific, but standardized in Java EE 8: SSE, JSON-B – Client-side: AngularJS or JavaFX Copyright © 2017, Oracle and/or its affiliates.