Casting a Hidden .NET
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Windows 7 Operating Guide
Welcome to Windows 7 1 1 You told us what you wanted. We listened. This Windows® 7 Product Guide highlights the new and improved features that will help deliver the one thing you said you wanted the most: Your PC, simplified. 3 3 Contents INTRODUCTION TO WINDOWS 7 6 DESIGNING WINDOWS 7 8 Market Trends that Inspired Windows 7 9 WINDOWS 7 EDITIONS 10 Windows 7 Starter 11 Windows 7 Home Basic 11 Windows 7 Home Premium 12 Windows 7 Professional 12 Windows 7 Enterprise / Windows 7 Ultimate 13 Windows Anytime Upgrade 14 Microsoft Desktop Optimization Pack 14 Windows 7 Editions Comparison 15 GETTING STARTED WITH WINDOWS 7 16 Upgrading a PC to Windows 7 16 WHAT’S NEW IN WINDOWS 7 20 Top Features for You 20 Top Features for IT Professionals 22 Application and Device Compatibility 23 WINDOWS 7 FOR YOU 24 WINDOWS 7 FOR YOU: SIMPLIFIES EVERYDAY TASKS 28 Simple to Navigate 28 Easier to Find Things 35 Easy to Browse the Web 38 Easy to Connect PCs and Manage Devices 41 Easy to Communicate and Share 47 WINDOWS 7 FOR YOU: WORKS THE WAY YOU WANT 50 Speed, Reliability, and Responsiveness 50 More Secure 55 Compatible with You 62 Better Troubleshooting and Problem Solving 66 WINDOWS 7 FOR YOU: MAKES NEW THINGS POSSIBLE 70 Media the Way You Want It 70 Work Anywhere 81 New Ways to Engage 84 INTRODUCTION TO WINDOWS 7 6 WINDOWS 7 FOR IT PROFESSIONALS 88 DESIGNING WINDOWS 7 8 WINDOWS 7 FOR IT PROFESSIONALS: Market Trends that Inspired Windows 7 9 MAKE PEOPLE PRODUCTIVE ANYWHERE 92 WINDOWS 7 EDITIONS 10 Remove Barriers to Information 92 Windows 7 Starter 11 Access -

Introduction to Windows 7
[Not for Circulation] Introduction to Windows 7 This document provides a basic overview of the new and enhanced features of Windows 7 as well as instructions for how to request an upgrade. Windows 7 at UIS Windows 7 is Microsoft’s latest operating system. Beginning in the fall of 2010, UIS will upgrade all classroom and lab PCs to Windows 7. Any new PC that is ordered will automatically come installed with Windows 7. To request an upgrade, contact the Technology Support Center (TSC) at 217/206-6000 or [email protected]. The TSC will evaluate your machine to see if it’s capable of running Windows 7. (Your computer needs a dual core processor and at least 2 GB of RAM.) Please note that University licensing does NOT cover distribution of Windows 7 for personally owned computers. However, it is available for a discounted price via the WebStore at http://webstore.illinois.edu. What to Consider Before Upgrading There is no direct upgrade path from Windows XP to Windows 7. Therefore, the TSC will take your computer, save your files, and install Windows 7 on a clean hard drive. Please budget a couple days for this process. In some cases, you may have older devices that will not work with Windows 7. While many vendors are providing and will continue to provide drivers for their hardware, in some cases, printers, scanners, and other devices that are more than 5 years old may have issues running on Windows 7. To check the compatibility of your devices with Windows 7, visit the Microsoft Windows 7 Compatibility Center at http://www.microsoft.com/windows/compatibility/windows-7/en-us/default.aspx. -
Performing a Windows 7 Upgrade from Windows Vista
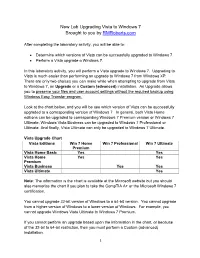
New Lab Upgrading Vista to Windows 7 Brought to you by RMRoberts.com After completing the laboratory activity, you will be able to: Determine which versions of Vista can be successfully upgraded to Windows 7. Perform a Vista upgrade o Windows 7. In this laboratory activity, you will perform a Vista upgrade to Windows 7. Upgrading to Vista is much easier than performing an upgrade to Windows 7 from Windows XP. There are only two choices you can make while when attempting to upgrade from Vista to Windows 7, an Upgrade or a Custom (advanced) installation. An Upgrade allows you to preserve your files and user account settings without the required backup using Windows Easy Transfer program. Look at the chart below, and you will be see which version of Vista can be successfully upgraded to a corresponding version of Windows 7. In general, both Vista Home editions can be upgraded to corresponding Windows 7 Premium version or Windows 7 Ultimate. Windows Vista Business can be upgraded to Windows 7 Professional or Ultimate. And finally, Vista Ultimate can only be upgraded to Windows 7 Ultimate. Vista Upgrade Chart Vista Editions Win 7 Home Win 7 Professional Win 7 Ultimate Premium Vista Home Basic Yes Yes Vista Home Yes Yes Premium Vista Business Yes Yes Vista Ultimate Yes Note: The information is the chart is available at the Microsoft website but you should also memorize the chart if you plan to take the CompTIA A+ or the Microsoft Windows 7 certification. You cannot upgrade 32-bit version of Windows to a 64-bit version. -
Intel® HD Graphics 5300 12 4.4 2.0 Yes Yes
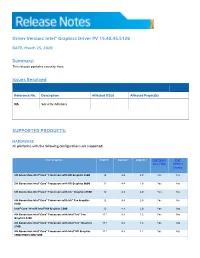
Driver Version: Intel® Graphics Driver PV 15.40.45.5126 DATE: March 25, 2020 Summary: This release contains security fixes. Issues Resolved Reference No. Description Affected OS(s) Affected Project(s) NA Security Advisory SUPPORTED PRODUCTS: HARDWARE All platforms with the following configurations are supported: Intel® Graphics1 DirectX*2 OpenGL* OpenCL* Intel® Quick Intel® Sync Video Wireless Display 5th Generation Intel® Core™ Processors with HD Graphics 5500 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with HD Graphics 6000 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with Iris™ Graphics 6100 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with Iris™ Pro Graphics 12 4.4 2.0 Yes Yes 6200 Intel® Core™ M with Intel® HD Graphics 5300 12 4.4 2.0 Yes Yes 4th Generation Intel® Core™ Processors with Intel® Iris™ Pro 11.1 4.3 1.2 Yes Yes Graphics 5200 4th Generation Intel® Core™ Processors with Intel® Iris™ Graphics 11.1 4.3 1.2 Yes Yes 5100 4th Generation Intel® Core™ Processors with Intel® HD Graphics 11.1 4.3 1.2 Yes Yes 5000/4600/4400/4200 Intel® Pentium® and Celeron® Processors with Intel® HD Graphics 11.1 4.3 1.2 Yes Yes based on 4th and 5th Generation Intel® Core™ Pentium®, Celeron®, and Atom™ processors based on Braswell and 12 4.3 2.0 Yes Yes CherryTrail. SOFTWARE On 4th Generation Intel Core processors and related Pentium/Celeron: • Microsoft Windows 10® 64-bit, 32-bit* *32-bit support is limited to particular SKU’s. -

Students,Faculty & Staff Guide for Windows 7
iM Students,Faculty & Staff Guide for Windows 7 Prepared by Information Technology Division Lehman College, CUNY March 22, 2014 This document was originally prepared by Dickinson College. It was modified and adapted for use at Lehman College with the permission of Dickinson College. Introduction to Windows 7 Table of Contents Windows 7 Taskbar ...................................................................................................................................... 2 Show Desktop ............................................................................................................................................... 2 Start Menu..................................................................................................................................................... 3 Pin ................................................................................................................................................................. 4 Jump Lists ..................................................................................................................................................... 4 Snap .............................................................................................................................................................. 5 Windows Search ........................................................................................................................................... 6 Library (the new My Documents area & more) ........................................................................................... -

Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability
Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Hernan Ochoa Agustin Azubel [email protected] [email protected] Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Presentation goals: ‣ Describe the vulnerability in detail ‣ Explain & demonstrate exploitation • Three different exploitation methods ‣ Clear up misconceptions ‣ Determine vulnerability scope, severity and impact ‣ Share Conclusions BlackHat USA 2010 Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Vulnerability Information ‣ Flaws in Windows’ implementation of NTLM - attackers can access SMB service as authorized user - leads to read/write access to files, SMB shared resources in general and remote code execution ‣ Published February 2010 ‣ CVE-2010-0231, BID 38085 ‣ Advisory with Exploit Code: • http://www.hexale.org/advisories/OCHOA-2010-0209.txt ‣ Addressed by MS10-012 BlackHat USA 2010 Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Why talk about this vulnerability? ‣ Major 14-year old vulnerability affecting Windows Authentication Mechanism! - Basically, all Windows versions were affected (NT4, 2000, XP, 2003, Vista, 2008, 7) - Windows NT 4 released in ∼1996 - Windows NT 3.1 released in ∼1993 (∼17 years ago) - All this time, we assumed it was working correctly.. but it wasn’t... - Flew under the radar... BlackHat USA 2010 Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Why talk about this vulnerability? ‣ Interesting vulnerability, not your common buffer overflow - Issues in the Pseudo-Random Number Generator (PRNG) - Challenge-response protocol implementation issues - Replay attacks - Attack to predict challenges is interesting BlackHat USA 2010 Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Why talk about this vulnerability? ‣ There’s a lesson to be learned.. -

Microsoft Windows 7 Has Reached Its End of Life Your Critical Operations Are at Risk of Costly Downtime Or Outage
— INDUSTRIAL AUTOMATION Microsoft Windows 7 has reached its End of Life Your critical operations are at risk of costly downtime or outage Beginning January 14, 2020, Microsoft will no longer support Windows 7, Windows Server 2008 and 2008 R2. As a result, many ABB products and services will be impacted. To keep your systems secure, you must invest in a plan to upgrade your control systems. Know what “End of Life” means Understand how it impacts you “End of Life” means Microsoft will discontinue all If you choose to continue using Windows 7, Windows support and will no longer provide software or Server 2008 and 2008 R2 even after support is security updates for Windows 7, Windows Server 2008 discontinued, the operating system will still work. and 2008 R2. The Windows 7 “End of Life” is similar to However, running unsupported operating systems that of previous Microsoft operating systems. will make ABB control systems vulnerable to cyber The lifecycle begins when a product is released and threats. Microsoft will no longer provide technical ends when it’s no longer supported. Knowing key support, software updates and security updates dates in this lifecycle helps you make informed needed to keep your systems secure. Purchasing and decisions about when to update, upgrade or make supporting replacement Windows 7 Workstations other changes to your software. and 2008 Server hardware will become challenging, and affected ABB distributed control systems software will move to the Limited Lifecycle Phase. Version End of support Comments Microsoft -

Upgrading to Windows 7
Upgrading to Windows 7 Windows 7 was designed to upgrade from Windows Vista and not from Windows XP. Additionally, Microsoft will only allow the following upgrade path to Vista users: • Windows Vista Home Premium to Windows 7 Home Premium • Windows Vista Business to Windows 7 Professional • Windows Vista Enterprise to Windows 7 Enterprise • Windows Vista Ultimate to Windows 7 Ultimate ***Any other upgrade path from Vista to Windows 7 will require a clean install*** ***Any upgrade from Windows XP to Windows 7 will require a clean install*** Before proceeding with an installation of Windows 7, you are strongly advised to run Windows 7 Upgrade Advisor. Windows 7 Upgrade Advisor will check the compatibility of your computer with Windows 7 and alert you to any issues that you should address before installing Windows 7. The download is available at http://www.microsoft.com/windows/windows‐7/get/upgrade‐advisor.aspx. 1. From the Microsoft website click on Download the Windows Upgrade Advisor Beta. 2. Click Download and then click Run. 3. A window will display that says “Do you want to run this software?” Click Run. 4. On the Setup Wizard screen, click Next. 5. Click I accept the license terms and click Next. 6. Click Install. When installation is complete, click Close. 7. When you see the screen below, click Start Check. 8. Windows Upgrade Advisor will start checking compatibility. 9. Once the scan is complete, Upgrade Advisor will display any issues that you should be aware of. 10. Click Close to exit Windows Upgrade Advisor. You will be unable to do an in-place upgrade in the following situations: 1. -

Windows 7 Winload OS Loader (Winload.Exe) Security Policy for FIPS 140-2 Validation
Winload OS Loader (winload.exe) Security Policy Windows 7 Winload OS Loader (winload.exe) Security Policy For FIPS 140-2 Validation v 4.3 08/31/11 1 INTRODUCTION .................................................................................................................. 2 1.1 Cryptographic Boundary for WINLOAD.EXE .............................................................................. 2 2 SECURITY POLICY .............................................................................................................. 2 2.1 WINLOAD.EXE Security Policy ..................................................................................................... 2 3 WINLOAD.EXE PORTS AND INTERFACES ....................................................................... 4 3.1 Control Input Interface ................................................................................................................. 4 3.2 Status Output Interface ................................................................................................................ 4 3.3 Data Output Interface ................................................................................................................... 5 3.4 Data Input Interface ...................................................................................................................... 5 4 SPECIFICATION OF ROLES ............................................................................................... 5 4.1 Maintenance Roles ........................................................................................................................ -
Qualifying Operating Systems
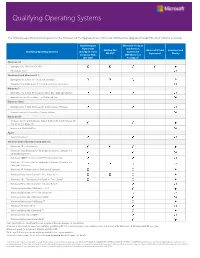
Qualifying Operating Systems The following operating systems qualify for the Windows 10 Pro Upgrade and/or Windows 10 Enterprise Upgrade through Microsoft Volume Licensing. New Enterprise Microsoft Products Agreement and Services Existing EA/ Microsoft Cloud Academic and Qualifying Operating Systems (EA)/Open Value Agreement OV-CW2 Agreement Charity Company-Wide (MPSA)/Select (OV-CW)1 Plus/Open3 Windows 10 4 Enterprise (N, KN) , Pro (N, KN) Education, Home Windows 8 and Windows 8.1 Enterprise (N, K, KN), Pro (N, K, KN, diskless) Windows 8 and Windows 8.1 (including Single Language) Windows 7 Enterprise (N, K, KN), Professional (N, K, KN, diskless), Ultimate Home Premium, Home Basic, or Starter Edition Windows Vista Enterprise (N, K, KN), Business (N, K, KN, Blade), Ultimate Home Premium, Home Basic, Starter Edition Windows XP Professional (N, K, KN, Blade), Tablet Edition (N, K, KN, Blade), XP Pro N, XP Pro Blade PC Home and Starter Edition Apple Apple Macintosh Windows Embedded Operating Systems Windows 10 IoT Enterprise Windows Vista Business for Embedded Systems, Ultimate for Embedded Systems Windows 2000 Professional for Embedded Systems Windows 7 Professional for Embedded Systems, Ultimate for Embedded Systems Windows XP Professional for Embedded Systems Windows Embedded 8 and 8.1 Pro, Industry Pro Windows 10 IoT Enterprise for Retail or Thin Clients5 5 Windows Embedded 8 and 8.1 Industry Retail Windows Embedded POSReady 7 Pro5 5 Windows Embedded for Point of Service Windows Embedded POSReady 20095 5 Windows Embedded POSReady 7 5 Windows XP Embedded Windows Embedded Standard 75 5 Windows Embedded 2009 5 Windows Embedded 8 Standard 1Also applicable to Qualified Devices acquired through merger or acquisition. -

Windows 10: Considered Harmful
Windows 10: Considered Harmful 26 August, 2016 Last Updated: 25 September 2016 Previously I made a series of articles against Windows 10, consisting of basic explanation, open letters, and even a long-winded chance.org petition. However, I have come to realize that these various things could be better as one page rather than fragments across my website. On this page I hope to explain why the Windows 10 system is evil and also include why Windows as a whole is Considered Harmful . Sources to unreferenced items in this article can be found in the various resource links on the bottom of the page. Information can also be found in the photographs shown and with a simple web search. The primary reason against the Windows 10 system is an obvious one. The system is designed to be a system that data-mines the user. This is proven time and time again. Using a tool such as wireshark, one can clearly see that it makes encrypted connections to a variety of Microsoft servers. This uses a very weak RSA encryption that can be broken in under a minute. When a user successfully decrypted the encrypted data, he simply converted the decrypted ``.bin'' extension to ``.png'' and opened them. The image files were screen- shots of him installing the RSA decryptor tool. This was in a VM and was a fresh install. In addition to this, another user in Australia also monitored the odd connection but did not decrypt it. He noticed this when he opened a photograph in the Windows Photo App. -

Download Deploying Windows 7, Essential Guidance
FROM THE Windows® 7 Resource Kit Mitch Tulloch, Tony Northrup, Jerry Honeycutt, Ed Wilson, and the Windows 7 Team at Microsoft I Chapter 3 Deployment Platform .............................................. 85 I Chapter 4 Planning Deployment ............................................ 113 I Chapter 5 Testing Application Compatability ........................... 139 I Chapter 6 Developing Disk Images ......................................... 179 I Chapter 7 Migrating User State Data ...................................... 223 I Chapter 8 Deploying Applications .......................................... 247 I Chapter 9 Preparing Windows PE ........................................... 273 I Chapter 10 Confi guring Windows Deployment Services .............. 293 I Chapter 11 Using Volume Activation ........................................ 335 I Chapter 12 Deploying with Microsoft Deployment Toolkit ........... 355 DEPLOYING WINDOWS 7 83 Chapter 3 Deployment Platform n Tools Introduction 85 n Windows 7 Deployment Terminology 87 n Platform Components 89 n Deployment Scenarios 99 n Understanding Setup 101 n Basic Deployment Process 105 n Microsoft Deployment Toolkit Process 107 n Summary 110 n Additional Resources 111 uilding on technology that the Windows Vista operating system introduced, Windows 7 Bdeployment technology has evolved significantly since Windows XP Professional . For example, it supports file-based disk imaging to make high-volume deployments quicker, more efficient, and more cost effective . The Windows 7 operating system also provides