Blockchain Consensus: an Overview of Alternative Protocols
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Peer Co-Movement in Crypto Markets
Peer Co-Movement in Crypto Markets G. Schwenkler and H. Zheng∗ February 4, 2021y Abstract We show that peer linkages induce significant price co-movement in crypto markets in excess of common risk factors and correlated demand shocks. When large abnormal return shocks hit one crypto, its peers experience unusually large abnormal returns of the opposite sign. These effects are primarily concentrated among smaller peers and revert after several weeks, resulting in predictable returns. We develop trading strategies that exploit this rever- sal, and show that they are profitable even after accounting for trading fees and frictions. We establish our results by identifying crypto peers through co-mentions in online news using novel natural language processing technologies. Keywords: Cryptocurrencies, peers, co-movement, competition, natural language pro- cessing. JEL codes: G12, G14, C82. ∗Schwenkler is at the Department of Finance, Santa Clara University Leavey School of Business. Zheng is at the Department of Finance, Boston University Questrom School of Business. Schwenkler is corresponding author. Email: [email protected], web: http://www.gustavo-schwenkler.com. yThis is a revision of a previous paper by the two authors called \Competition or Contagion: Evidence from Cryptocurrency Markets." We are grateful to Jawad Addoum (discussant), Daniele Bianchi (discussant), Will Cong, Tony Cookson, Sanjiv Das, Seoyoung Kim, Andreas Neuhierl, Farzad Saidi, and Antoinette Schoar, seminar participants at Boston University and the Society for Financial Econometrics, and the participants at the 2020 Finance in the Cloud III Virtual Conference, the 2020 MFA Annual Meeting, the 3rd UWA Blockchain, Cryptocurrency and FinTech Conference, and the 2020 INFORMS Annual Meeting for useful comments and suggestions. -

The Advantages and Disadvantages of Bitcoin Payments in the New Economy Carina-Elena Stegăroiu, Lecturer Phd, „Constantin Br
Annals of the „Constantin Brâncuşi” University of Târgu Jiu, Economy Series, Issue 1/2018 THE ADVANTAGES AND DISADVANTAGES OF BITCOIN PAYMENTS IN THE NEW ECONOMY CARINA-ELENA STEGĂROIU, LECTURER PHD, „CONSTANTIN BRÂNCUŞI” UNIVERSITY, TÂRGU JIU, ROMANIA [email protected] Abstract In the Internet economy, with the help of cryptography, a branch of mathematics dealing with the security of information, as well as authentication and restriction of access to a computer system, a new digital coin as an alternative to national currencies appeared. In accomplishing this, using both mathematical methods (taking advantage of, for example, the difficulty of factorizing very large numbers), and quantum encryption methods. Throughout the world, information technology companies are focusing on information protection, inventing day-to-day methods with greater durability. In the horizon of Information Security, Quantum Cryptography has emerged, generating new possibilities in that field, hoping that data will be better protected and that the digital currency will resist over time and eventually evolve in the future, although Kurzweil, Bitcoin's pioneering technology is unlikely to be used in this respect. The idea of virtual alternatives to national currencies is not new, with advantages and disadvantages. The advantages of this coin are high payment freedom, transparency of information, high security, reduced risks for traders. Among the disadvantages we highlight the risk and volatility, the lack of notification and understanding, with incomplete functions, but which are developing, so Bitcoin is not perfect. Keywords: bitcoin, criptografie, methodology, economic growth, economic agent, branch production, virtual economy, monedă digitală Classification JEL: F60, F61. F62, F63 1. Introduction The idea of virtual alternatives to national currencies is not a new one, Iceland being a country that in April issued its own virtual modular Auroracoin, distributing it to the population. -

Realizing the Potential of Blockchain Technologies in Genomics
Downloaded from genome.cshlp.org on September 29, 2021 - Published by Cold Spring Harbor Laboratory Press Perspective Realizing the potential of blockchain technologies in genomics Halil Ibrahim Ozercan,1 Atalay Mert Ileri,2 Erman Ayday,1 and Can Alkan1 1Department of Computer Engineering, Bilkent University, Ankara 06800, Turkey; 2Department of Electrical Engineering and Computer Science, Massachusetts Institute of Technology, Cambridge, Massachusetts 02139, USA Genomics data introduce a substantial computational burden as well as data privacy and ownership issues. Data sets generated by high-throughput sequencing platforms require immense amounts of computational resources to align to reference ge- nomes and to call and annotate genomic variants. This problem is even more pronounced if reanalysis is needed for new ver- sions of reference genomes, which may impose high loads to existing computational infrastructures. Additionally, after the compute-intensive analyses are completed, the results are either kept in centralized repositories with access control, or dis- tributed among stakeholders using standard file transfer protocols. This imposes two main problems: (1) Centralized servers become gatekeepers of the data, essentially acting as an unnecessary mediator between the actual data owners and data users; and (2) servers may create single points of failure both in terms of service availability and data privacy. Therefore, there is a need for secure and decentralized platforms for data distribution with user-level data governance. A new technology, block- chain, may help ameliorate some of these problems. In broad terms, the blockchain technology enables decentralized, im- mutable, incorruptible public ledgers. In this Perspective, we aim to introduce current developments toward using blockchain to address several problems in omics, and to provide an outlook of possible future implications of the blockchain technology to life sciences. -

YEUNG-DOCUMENT-2019.Pdf (478.1Kb)
Useful Computation on the Block Chain The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citation Yeung, Fuk. 2019. Useful Computation on the Block Chain. Master's thesis, Harvard Extension School. Citable link https://nrs.harvard.edu/URN-3:HUL.INSTREPOS:37364565 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Other Posted Material, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#LAA 111 Useful Computation on the Block Chain Fuk Yeung A Thesis in the Field of Information Technology for the Degree of Master of Liberal Arts in Extension Studies Harvard University November 2019 Copyright 2019 [Fuk Yeung] Abstract The recent growth of blockchain technology and its usage has increased the size of cryptocurrency networks. However, this increase has come at the cost of high energy consumption due to the processing power needed to maintain large cryptocurrency networks. In the largest networks, this processing power is attributed to wasted computations centered around solving a Proof of Work algorithm. There have been several attempts to address this problem and it is an area of continuing improvement. We will present a summary of proposed solutions as well as an in-depth look at a promising alternative algorithm known as Proof of Useful Work. This solution will redirect wasted computation towards useful work. We will show that this is a viable alternative to Proof of Work. Dedication Thank you to everyone who has supported me throughout the process of writing this piece. -

Chia Proof of Space Construction
Chia Proof of Space Construction Introduction In order to create a secure blockchain consensus algorithm using disk space, a Proof of Space is scheme is necessary. This document describes a practical contruction of Proofs of Space, based on Beyond Hellman’s Time- Memory Trade-Offs with Applications to Proofs of Space [1]. We use the techniques laid out in that paper, extend it from 2 to 7 tables, and tweak it to make it efficient and secure, for use in the Chia Blockchain. The document is divided into three main sections: What (mathematical definition of a proof of space), How (how to implement proof of space), and Why (motivation and explanation of the construction) sections. The Beyond Hellman paper can be read first for more mathematical background. Chia Proof of Space Construction Introduction What is Proof of Space? Definitions Proof format Proof Quality String Definition of parameters, and M, f, A, C functions: Parameters: f functions: Matching function M: A′ function: At function: Collation function C: How do we implement Proof of Space? Plotting Plotting Tables (Concepts) Tables Table Positions Compressing Entry Data Delta Format ANS Encoding of Delta Formatted Points Stub and Small Deltas Parks Checkpoint Tables Plotting Algorithm Final Disk Format Full algorithm Phase 1: Forward Propagation Phase 2: Backpropagation Phase 3: Compression Phase 4: Checkpoints Sort on Disk Plotting Performance Space Required Proving Proof ordering vs Plot ordering Proof Retrieval Quality String Retrieval Proving Performance Verification Construction -

Pow, Pos, & Hybrid Protocols: a Matter of Complexity?
PoW, PoS, & Hybrid protocols: A Matter of Complexity? Renato P. dos Santos Blockchain Researcher at ULBRA – The Lutheran University of Brazil [email protected]. Melanie Swan Technology Theorist and Founder at Institute for Blockchain Studies [email protected] Abstract In a previous paper, it was discussed whether Bitcoin and/or its blockchain could be considered a complex system and, if so, whether a chaotic one, a positive response raising concerns about the likelihood of Bitcoin/blockchain entering a chaotic regime, with catastrophic consequences for financial systems based on it. This paper intends to simplify and extend that analysis to other PoW, PoS, and hybrid protocol-based cryptocurrencies. As before, this study was carried out with the help of Information Theory of Complex Systems, in general, and Crutchfield’s Statistical Complexity measure, in particular. This paper is a work-in-progress. Whereas PoW consensus was shown to be highly non-complex, the Nxt PoS consensus method studied shows an outstandingly higher measure of complexity, which is undesirable because it introduces unnecessary complexity into what should be a simple computational system. This paper is a work-in-progress and undoubtedly prone to incorrectness as a few cryptocurrencies may have changed their consensus algorithms. As next step, we intend to uncover some other measures that capture the qualitative notion of complexity of systems that can be applied to these cryptocurrencies to compare with the results here obtained. As a final thought, however, considering that a certain amount of chaoticity may have been potentially introduced in the Bitcoin market by the presence of the capital gains-seekers, one could wonder whether the recent surge of blockchain technology-based start-ups, even discounting all the scam cases, could not help to reduce non-linearity and prevent chaos. -

Blockchain in an Internet-Of-Things Network Based on User Participation
Blockchain in an Internet-of-Things Network Based on User Participation Robert Ljungblad Computer Science and Engineering, bachelor's level 2019 Luleå University of Technology Department of Computer Science, Electrical and Space Engineering ABSTRACT The internet-of-things is the relatively new and rapidly growing concept of connecting everyday devices to the internet. Every day more and more devices are added to the internet-of-things and it is not showing any signs of slowing down. In addition, advancements in new technologies such as blockchains, artificial intelligence, virtual reality and machine learning are made practically every day. However, there are still much to learn about these technologies. This thesis explores the possibilities of blockchain technology by applying it to an internet-of-things network based on user participation. More specifically, it is applied to a use case derived from Luleå Kommun’s wishes to easier keep track of how full the city’s trash cans are. The goal of the thesis is to learn more about how blockchains can help an internet-of-things network as well as what issues can arise. The method takes an exploratory approach to the problem by partaking in a workshop with Luleå Kommun and by performing a literature study. It also takes a qualitative approach by creating a proof-of-concept solution to experience the technology firsthand. The final proof-of-concept as well as issues that arose during the project are analysed with the help of information gathered and experience gained throughout the project. It is concluded that blockchain technology can help communication in an internet-of-things network based on user participation. -

IFRS: Accounting for Crypto-Assets
IFRS (#) Accounting for crypto-assets Contents 1. Introduction 1 2. What are crypto-assets? 2 2.1. Cryptocurrencies 3 2.2. Tokens (crypto-assets other than cryptocurrencies) 5 3. Accounting for crypto-assets 10 3.1. Selected activities of standard setters 10 3.2. Special situations 13 3.3. Conclusion 15 4. Supporting details 16 5. Contacts 21 1 Introduction Crypto-assets experienced a breakout year in 2017. Cryptocurrencies, such as bitcoin and ether, have seen their prices surge as the public’s YoYj]f]kk`Ykaf[j]Yk]\$Yf\ÕfYf[aYdeYjc]lhYjla[ahYflk`Yn]l`mk af[j]Ykaf_dqlmjf]\l`]ajYll]flagflgl`]h`]fge]fgf&KaemdlYf]gmkdq$ a wave of new crypto-asset issuance has been sweeping the start-up fundraising world, sparking the interest of regulators in the process. 9[[gmflYflk`Yn]l`mk^YjZ]]ffglYZd]Zql`]ajj]dYlan]YZk]f[]^jge l`YlfYjjYlan]&H]j`Yhk$egklfglYZd]akl`]^Y[ll`Yll`]9mkljYdaYf 9[[gmflaf_KlYf\Yj\k:gYj\ 99K:!`YkkmZeall]\Y\ak[mkkagfhYh]j gfÉ\a_alYd[mjj]f[a]kÊlgl`]Afl]jfYlagfYd9[[gmflaf_KlYf\Yj\k :gYj\ A9K:!$Yf\l`]9[[gmflaf_KlYf\Yj\k:gYj\g^BYhYf 9K:B! `Ykakkm]\Yf]phgkmj]\jY^l^gjhmZda[[gee]flgfY[[gmflaf_^gj “virtual currencies”.1AfY\\alagf$l`]A9K:\ak[mkk]\[]jlYaf^]Ylmj]kg^ ljYfkY[lagfkafngdnaf_\a_alYd[mjj]f[a]k\mjaf_alke]]laf_afBYfmYjq *()0$Yf\oadd\ak[mkkaf^mlmj]o`]l`]jlg[gee]f[]Yj]k]Yj[`hjgb][l in this area.1 L`akYdkg`a_`da_`lkl`]dY[cg^YklYf\Yj\ar]\[jqhlg%Ykk]llYpgfgeq$ o`a[`eYc]kal\a^Õ[mdllg\]l]jeaf]l`]Yhhda[YZadalqg^klYf\Yj\k]ll]jkÌ hmZdak`]\h]jkh][lan]k&>mjl`]jegj]$\m]lgl`]\an]jkalqYf\hY[]g^ affgnYlagfYkkg[aYl]\oal`[jqhlg%Ykk]lk$l`]^Y[lkYf\[aj[meklYf[]k g^]Y[`af\ana\mYd[Yk]oadd\a^^]j$eYcaf_al\a^Õ[mdllg\jYo_]f]jYd [gf[dmkagfkgfl`]Y[[gmflaf_lj]Yle]fl& <]khal]l`]eYjc]lÌkaf[j]Ykaf_dqmj_]flf]]\^gjY[[gmflaf__ma\Yf[]$ l`]j]`Yn]Z]]ffg^gjeYdhjgfgmf[]e]flkgfl`aklgha[lg\Yl]& Afl`akj]hgjl$o]YaelgÕjklZja]Öqafljg\m[][jqhlg[mjj]f[a]kYf\ gl`]jlqh]kg^[jqhlg%Ykk]lk&L`]f$o]\ak[mkkkge]g^l`]j][]fl activities by accounting standard setters in relation to crypto-assets. -

GJR-GARCH Volatility Modeling Under NIG and ANN for Predicting Top Cryptocurrencies
Journal of Risk and Financial Management Article GJR-GARCH Volatility Modeling under NIG and ANN for Predicting Top Cryptocurrencies Fahad Mostafa 1,* , Pritam Saha 2, Mohammad Rafiqul Islam 3 and Nguyet Nguyen 4,* 1 Department of Mathematics and Statistics, Texas Tech University, Lubbock, TX 79409, USA 2 Rawls College of Business, Texas Tech University, Lubbock, TX 79409, USA; [email protected] 3 Department of Mathematics, Florida State University, Tallahassee, FL 32306, USA; [email protected] 4 Department of Mathematics and Statistics, Youngstown State University, Youngstown, OH 44555, USA * Correspondence: [email protected] (F.M.); [email protected] (N.N.) Abstract: Cryptocurrencies are currently traded worldwide, with hundreds of different currencies in existence and even more on the way. This study implements some statistical and machine learning approaches for cryptocurrency investments. First, we implement GJR-GARCH over the GARCH model to estimate the volatility of ten popular cryptocurrencies based on market capitalization: Bitcoin, Bitcoin Cash, Bitcoin SV, Chainlink, EOS, Ethereum, Litecoin, TETHER, Tezos, and XRP. Then, we use Monte Carlo simulations to generate the conditional variance of the cryptocurrencies using the GJR-GARCH model, and calculate the value at risk (VaR) of the simulations. We also estimate the tail-risk using VaR backtesting. Finally, we use an artificial neural network (ANN) for predicting the prices of the ten cryptocurrencies. The graphical analysis and mean square errors (MSEs) from the ANN models confirmed that the predicted prices are close to the market prices. For some cryptocurrencies, the ANN models perform better than traditional ARIMA models. Citation: Mostafa, Fahad, Pritam Saha, Mohammad Rafiqul Islam, and Keywords: artificial neural network; cryptocurrency; GJR-GARCH; NIG; Monte Carlo simulation; Nguyet Nguyen. -

IPFS and Friends: a Qualitative Comparison of Next Generation Peer-To-Peer Data Networks Erik Daniel and Florian Tschorsch
1 IPFS and Friends: A Qualitative Comparison of Next Generation Peer-to-Peer Data Networks Erik Daniel and Florian Tschorsch Abstract—Decentralized, distributed storage offers a way to types of files [1]. Napster and Gnutella marked the beginning reduce the impact of data silos as often fostered by centralized and were followed by many other P2P networks focusing on cloud storage. While the intentions of this trend are not new, the specialized application areas or novel network structures. For topic gained traction due to technological advancements, most notably blockchain networks. As a consequence, we observe that example, Freenet [2] realizes anonymous storage and retrieval. a new generation of peer-to-peer data networks emerges. In this Chord [3], CAN [4], and Pastry [5] provide protocols to survey paper, we therefore provide a technical overview of the maintain a structured overlay network topology. In particular, next generation data networks. We use select data networks to BitTorrent [6] received a lot of attention from both users and introduce general concepts and to emphasize new developments. the research community. BitTorrent introduced an incentive Specifically, we provide a deeper outline of the Interplanetary File System and a general overview of Swarm, the Hypercore Pro- mechanism to achieve Pareto efficiency, trying to improve tocol, SAFE, Storj, and Arweave. We identify common building network utilization achieving a higher level of robustness. We blocks and provide a qualitative comparison. From the overview, consider networks such as Napster, Gnutella, Freenet, BitTor- we derive future challenges and research goals concerning data rent, and many more as first generation P2P data networks, networks. -
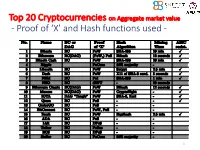
Proof of 'X' and Hash Functions Used
Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 1 ISI Kolkata BlockChain Workshop, Nov 30th, 2017 CRYPTOGRAPHY with BlockChain - Hash Functions, Signatures and Anonymization - Hiroaki ANADA*1, Kouichi SAKURAI*2 *1: University of Nagasaki, *2: Kyushu University Acknowledgements: This work is supported by: Grants-in-Aid for Scientific Research of Japan Society for the Promotion of Science; Research Project Number: JP15H02711 Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 3 Table of Contents 1. Cryptographic Primitives in Blockchains 2. Hash Functions a. Roles b. Various Hash functions used for Proof of ‘X’ 3. Signatures a. Standard Signatures (ECDSA) b. Ring Signatures c. One-Time Signatures (Winternitz) 4. Anonymization Techniques a. Mixing (CoinJoin) b. Zero-Knowledge proofs (zk-SNARK) 5. Conclusion 4 Brief History of Proof of ‘X’ 1992: “Pricing via Processing or Combatting Junk Mail” Dwork, C. and Naor, M., CRYPTO ’92 Pricing Functions 2003: “Moderately Hard Functions: From Complexity to Spam Fighting” Naor, M., Foundations of Soft. Tech. and Theoretical Comp. Sci. 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 5 Brief History of Proof of ‘X’ 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 2012: “Peercoin” Proof of Stake (& Proof of Work) ~ : Delegated Proof of Stake, Proof of Storage, Proof of Importance, Proof of Reserves, Proof of Consensus, ... 6 Proofs of ‘X’ 1. Proof of Work 2. Proof of Stake Hash-based Proof of ‘X’ 3. Delegated Proof of Stake 4. Proof of Importance 5. -

PWC and Elwood
2020 Crypto Hedge Fund Report Contents Introduction to Crypto Hedge Fund Report 3 Key Takeaways 4 Survey Data 5 Investment Data 6 Strategy Insights 6 Market Analysis 7 Assets Under Management (AuM) 8 Fund performance 9 Fees 10 Cryptocurrencies 11 Derivatives and Leverage 12 Non-Investment Data 13 Team Expertise 13 Custody and Counterparty Risk 15 Governance 16 Valuation and Fund Administration 16 Liquidity and Lock-ups 17 Legal and Regulatory 18 Tax 19 Survey Respondents 20 About PwC & Elwood 21 Introduction to Crypto Hedge Fund report In this report we provide an overview of the global crypto hedge fund landscape and offer insights into both quantitative elements (such as liquidity terms, trading of cryptocurrencies and performance) and qualitative aspects, such as best practice with respect to custody and governance. By sharing these insights with the broader crypto industry, our goal is to encourage the adoption of sound practices by market participants as the ecosystem matures. The data contained in this report comes from research that was conducted in Q1 2020 across the largest global crypto hedge funds by assets under management (AuM). This report specifically focuses on crypto hedge funds and excludes data from crypto index/tracking/passive funds and crypto venture capital funds. 3 | 2020 Crypto Hedge Fund Report Key Takeaways: Size of the Market and AuM: Performance and Fees: • We estimate that the total AuM of crypto hedge funds • The median crypto hedge fund returned +30% in 2019 (vs - globally increased to over US$2 billion in 2019 from US$1 46% in 2018). billion the previous year.