20132012 in Retrospect Internet & Jurisdiction Project Case Collection Volume 2
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Anonsocialmix: Anonymous P2P File Sharing Over Social Networks
AnonSocialMix: Anonymous P2P File Sharing Over Social Networks Student Name: Rajdeep Mukherjee IIIT-D-MTech-CS-GEN-MT15051 July, 2017 Indraprastha Institute of Information Technology New Delhi Thesis Committee Dr. Sambuddho Chakravarty, IIIT Delhi (Advisor) Dr. Tanmoy Chakraborty, IIIT Delhi (Internal Examiner) Dr. Vinay Joseph Ribeiro, IIT Delhi (External Examiner) Submitted in partial fulfillment of the requirements for the Degree of M.Tech. in Computer Science, in Information Security Category ©2017 IIIT-D MTech-CS-GEN-17-MT15051 All rights reserved Certificate This is to certify that the thesis titled “AnonSocialMix: Anonymous P2P File Sharing Over Social Networks" submitted by Rajdeep Mukherjee for the partial fulfillment of the requirements for the degree of Master of Technology in Computer Science & Engineering is a record of the bonafide work carried out by him under my guidance and supervision in the Security and Privacy group at Indraprastha Institute of Information Technology, Delhi. This work has not been submitted anywhere else for the reward of any other degree. Dr.Sambuddho Chakravarty Indraprastha Institute of Information Technology, New Delhi 2 Abstract Peer-to-peer (P2P) file sharing accounts for one of the major sources of the Internet traffic. As privacy and anonymity issues continue to grow due to constant censorship and network surveil- lance, more and more Internet users are getting attracted towards the facilities for anonymous communication. Extensive research has been conducted over the years towards the design and development of several anonymous P2P file sharing protocols and systems. Size of the Anonymity Set plays a crucial role in determining the degree of anonymity being provided by such networks. -

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

Testimony of Authors Guild President Scott Turow Before the Senate
My name is Scott Turow. I’m the president of the Authors Guild, the largest society of published authors in the U.S., representing more than 8,500 book authors and freelance writers. Our members represent the broad sweep of American authorship, including literary and genre fiction, nonfiction, trade, academic, and children’s book authors, textbook authors, freelance journalists and poets.1 Guild members have won countless honors and all major literary awards, including the Nobel Prize for Literature.2 The Authors Guild promotes the professional interests of authors: we’re advocates for effective copyright protection, fair contracts, and free expression. It’s a pleasure and an honor to be here this morning. I’d like especially to thank this committee for recognizing the severity of the problem we all face and getting the ball rolling with COICA in the fall, which recognized this central and unavoidable truth: any serious attempt to address online piracy must address the third-party enablers of infringement. Anything that doesn’t address those enablers is, frankly, a pretend solution to a real problem. Our Copyright Policy Inadvertently Encourages Investments in Technologies and Services That Promote Trafficking in Stolen Books, Music, and Movies After 300 years as one of history's greatest public policy successes, copyright is coming undone. As we meet here this morning, our well-intended policy toward copyright online is 1 The Guild had its beginnings as the Authors League of America, which was founded in 1912 by a group of book authors (including Theodore Roosevelt, who served as the League’s founding vice president), short story writers, freelance journalists and a smattering of dramatists. -

NOTICE by Hotfile Corp., Anton Titov Defendants' Notice of Filing The
Disney Enterprises, Inc. et al v. Hotfile Corp. et al Doc. 391 Att. 1 EXHIBIT A Dockets.Justia.com PUBLIC VERSION UNITED STATES DISTRICT COURT SOUTHERN DISTRICT OF FLORIDA CASE NO.: 11-CIV-20427-WILLIAMS/TURNOFF DISNEY ENTERPRISES, INC., TWENTIETH CENTURY FOX FILM CORPORATION, UNIVERSAL CITY STUDIOS PRODUCTIONS LLLP, COLUMBIA PICTURES INDUSTRIES, INC., and WARNER BROS. ENTERTAINMENT INC., Plaintiffs, v. HOTFILE CORP., ANTON TITOV, and DOES 1-10. Defendants. / HOTFILE CORP., Counterclaimant, v. WARNER BROS. ENTERTAINMENT INC., Counter-Defendant. / [REDACTED] DECLARATION OF PROFESSOR JAMES BOYLE IN SUPPORT OF DEFENDANTS’ OPPOSITION TO PLAINTIFFS’ MOTION FOR SUMMARY JUDGMENT AND EXHIBITS THERETO FILED UNDER SEAL CASE NO.: 11-CIV-20427-WILLIAMS/TURNOFF I, JAMES BOYLE, declare as follows: 1. I am currently the William Neal Reynolds Professor of Law at Duke University, and have been retained by Farella, Braun + Martel LLP on behalf of the Defendants in this action as an expert witness. 2. I received an LL.B. (Hons) from Glasgow University (1980), and an LL.M. (1981) and S.J.D. (1986) from Harvard Law School. I have been a law professor since 1982, teaching at American University, and at the Universities of Pennsylvania, Harvard and Yale as a Visiting Professor. In 2000 I joined the law faculty at Duke. 3. My academic research is mainly in the areas of intellectual property and communication policy, with a focus on the Internet. I have written and edited numerous articles and books on these subjects. In general, my research and scholarship has focused on: i) Copyright law, particularly in the digital arena. I have published extensively on copyright in law journals, monographs, and edited collections of essays; a full list is available in the attached curriculum vitae. -

Doing Business in Canada 2019
Doing Business in Canada A disciplined, team-driven approach focused squarely on the success of your business. Lawyers in offices across Canada, the United States, Europe and China — Toronto, Calgary, Vancouver, Montréal, Ottawa, New York, London and Beijing. Among the world’s most respected corporate law firms, with expertise in virtually every area of business law. When it comes to dealmaking, Blakes Means Business. Blakes Guide to Doing Business in Canada Doing Business in Canada is intended as an introductory summary. Specific advice should be sought in connection with particular transactions. If you have any questions with respect to Doing Business in Canada, please contact our Firm Chair, Brock Gibson by email at [email protected]. Blake, Cassels & Graydon LLP produces regular reports and special publications on Canadian legal developments. For further information about these reports and publications, please contact the Blakes Client Relations & Marketing Department at [email protected]. Contents I. Introduction ............................................................................................................... 1 II. Government and Legal System ............................................................................... 2 1. Brief Canadian History ............................................................................................. 2 2. Federal Government ................................................................................................. 3 3. Provincial and Territorial Governments -

Volition and Copyright Infringement
DENICOLA.37.4.3 (Do Not Delete) 4/3/2016 1:45 PM VOLITION AND COPYRIGHT INFRINGEMENT Robert C. Denicola† TABLE OF CONTENTS INTRODUCTION .............................................................................................................. 1259 I. VOLITION AND CAUSATION IN TORT LAW .......................................................... 1262 A. It Isn’t Actually an Issue of “Volition” ..................................................... 1262 B. It Isn’t Actually an Issue of “Causation” Either ...................................... 1268 II. VOLITION IN COPYRIGHT LAW ............................................................................. 1270 A. Volition and the Defendant’s Relationship to the Infringed Work....... 1270 B. A Duty to Police ......................................................................................... 1276 C. Secondary Liability .................................................................................... 1283 III. VOLITION APPLIED ................................................................................................. 1284 A. Cloud Storage ............................................................................................. 1284 B. Search Engines ............................................................................................ 1287 C. Cartoon Network and the Remote Storage DVR ................................... 1290 D. Aereo and Its Tiny Antennae ................................................................... 1293 CONCLUSION.................................................................................................................. -

Experiences of Internet Traffic Monitoring with Tstat
1 Experiences of Internet Traffic Monitoring with Tstat A. Finamore M. Mellia M. Meo M. M. Munaf`o D. Rossi 1Politecnico di Torino 2TELECOM ParisTech email: {[email protected]} email: [email protected] Abstract—Since the early days of the Internet, network traffic Internet monitoring tools are based on active probing, ranging monitoring has always played a strategic role in understanding from simple operation management or network tomography and characterize users’ activities. In this paper, we present our via ping or traceroute, to more complex delay and capac- experience in engineering and deploying Tstat, an open source passive monitoring tool that has been developed in the past ten ity estimation via capprobe or pathchar. Finally, large and years. Started as a scalable tool to continuously monitor packets controlled testbeds can be easily setup using tools like netem that flow on a link, Tstat has evolved into a complex application or dummynet. For the passive approach pure observations are that gives to network researchers and operators the possibility to performed by means of dedicated tools, named sniffers by derive extended and complex measurements thanks to advanced the Internet metrology community, that simply observe and traffic classifiers. After discussing Tstat capabilities and internal design, we analyze the traffic that flows on links. Several passive mea- present some examples of measurements collected deploying surement tools are available. Some tools, such as tcpdump or Tstat at the edge of several ISP networks in the past years. Wireshark, are designed to let researchers interactively analyze While other works report a continuous decline of P2P traffic the captured packets. -
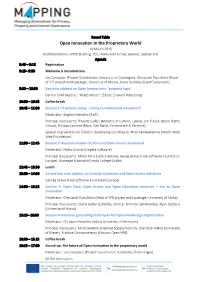
Open Innovation in the Proprietary World
Round Table Open Innovation in the Proprietary World 19 March 2015 DiploFoundation, WMO Building, 7bis, Avenue de la Paix, Geneva, Switzerland Agenda 8:45 – 9:15 Registration 9:15– 9:30 Welcome & Introductions Joe Cannataci (Project Coordinator; University of Groningen), Oleksandr Pastukhov (Head of IPR project work package; University of Malta), Jovan Kurbalija (DiploFoundation) 9:30 – 10:30 Key-note address on Open Innovation v. ‘property logic’ Darren Todd (Author, “Pirate Nation”; Editor, Evolved Publishing) 10:30 – 10:45 Coffee break 10:45 – 11:30 Session 1: IP policies today – failing to understand innovation? Moderator: Bogdan Manolea (ApTI) Principal discussants: Rihards Gulbis (Ministry of Culture, Latvia), Jim Killock (Open Rights Group), Philippe Laurent (Marx, Van Ranst, Vermeersch & Partners) Special intervention on F/OSS in developing countries by Nnenna Nwakanma (World Wide Web Foundation) 11:30 – 12:45 Session 2: Business models for the Free/Open Source movement Moderator: Pedro Gomez (Hoplite Software) Principal discussants: Mario Pena (Safe Creative), Georg Greve (Free Software Foundation Europe), Giuseppe Mazziotti (Trinity College Dublin) 12:45 – 13:30 Lunch 13:30 – 14:30 Second key-note address on Creative Commons and Open Access initiatives George Greve (Free Software Foundation Europe) 14:30 – 15:15 Session 3: Open Data, Open Access and Open Education resources – key to Open Innovation Moderator: Oleksandr Pastukhov (Head of IPR project work package; University of Malta) Principal discussants: Claire Gallon (Libertic), -

Edition No. 3 March 2019
GDPR Today Edition No. 3 March 2019 European Commission urged to investigate Romanian GDPR implementation GDPR loopholes facilitate data exploitation by political parties Uber drivers demand their data After Brexit, the EU must decide if UK data protection is adequate 2 GDPR in Numbers 6 European Commission urged to investigate Romanian GDPR implementation 8 Spain: DPA limits the use of data in political campaigning 10 Netherlands: DPA rules websites must allow people to refuse tracking cookies 12 GDPR loopholes facilitate data exploitation by political parties 14 Privacy policies for Internet of Things devices must comply with GDPR 15 Uber drivers demand their data New evidence in AdTech complaint 15 EDPB: e-Privacy and GDPR work together 16 to protect people’s data 18 German competition regulator demands changes to Facebook’s use of personal data 20 After Brexit, the EU must decide if UK data protection is adequate 22 EDPS 2018 Annual Report highlights the power and limitation of data protection 24 GDPR Tools 25 EU National Data Protection Authority Contact Details Editorial Welcome to GDPR Today – your online hub for staying Not all is positive progress. It is disappointing that the tuned to the (real) life of EU data protection law. As you European Commission has still not yet taken action to know, every two months we publish statistics showing how ensure that Romania properly implements the GDPR. the GDPR is being applied across Europe. We also share There are also several countries which have yet to relevant news, from legal guidelines and decisions to publish any GDPR data. -

Regulation of the Internet a Technological Perspective
Regulation of the Internet A Technological Perspective "As we surge toward a new millennium, the Internet has become more than the overwhelming reality of the technology industry's current existence. It is the foundation for the Information Age, the environment in which we will all be living before long."1 Gerry Miller Gerri Sinclair David Sutherland Julie Zilber March, 1999 1 Dan Gillmor, San Jose Mercury News, December 19,1998, http://www7.mercurycenter.com/business/top/069597.htm Table of Contents PREFACE ...................................................................................................... IV INTRODUCTION............................................................................................. 1 SUMMARY OF CONCLUSIONS .................................................................... 3 PART 1 SETTING THE CONTEXT................................................................. 7 1. An Internet Primer.......................................................................................................................7 1.1 What is it?...............................................................................................................................7 1.2 Who owns it?...........................................................................................................................7 1.3 How does it work? ..................................................................................................................7 1.4 Who governs the Internet? .....................................................................................................8 -

The Role of Civil Society Organizations in the Net Neutrality Debate in Canada and the United States
THE ROLE OF CIVIL SOCIETY ORGANIZATIONS IN THE NET NEUTRALITY DEBATE IN CANADA AND THE UNITED STATES By Bruce Thomas Harpham A thesis submitted in conformity with the requirements for the degree of Master of Information Studies Graduate Department of the Faculty of Information University of Toronto © Copyright by Bruce Thomas Harpham (2009) Thesis title: The role of civil society organizations in the net neutrality debate in Canada and the United States Degree: Master of Information Studies (2009) Author: Bruce Thomas Harpham Graduate Department: Faculty of Information Institution: University of Toronto Abstract: This thesis investigates the policy frames employed by civil society organizations (CSOs) in the network neutrality debate in Canada and the United States. Network neutrality is defined as restrictions on Internet Service Providers (ISPs) to respect freedom of expression on the Internet and not seek to prevent innovative competition nor control the services or content available to users. The primary question under investigation is the policy frames of CSOs in the debate. The second question is whether CSOs have influenced policy outcomes in either legislation or regulation. The focus of the analysis is on regulatory agencies (CRTC and FCC); proposed legislation in Parliament and Congress is also analyzed as well. By examining the arguments advanced by various policy participants (government, ISPs, and CSOs), common points can be identified that may help the participants come to agreement. ii Acknowledgements Over the months of research and writing the thesis, I have greatly benefited from the comments and suggestions from my supervisors, Professors Andrew Clement and Nadia Caidi. Their contributions have allowed me to develop my argument in greater detail and have pointed out errors and other problems. -

Piracy Versus Privacy: an Analysis of Values Encoded in the Piratebrowser
International Journal of Communication 9(2015), 818–838 1932–8036/20150005 Piracy Versus Privacy: An Analysis of Values Encoded in the PirateBrowser BALÁZS BODÓ University of Amsterdam, Institute for Information Law The Netherlands The PirateBrowser is a Web browser that uses Tor privacy-enhancing technology to circumvent nationally implemented Internet filters blocking access to The Pirate Bay. This article analyzes the possible consequences of a mass influx of copyright pirates into the privacy domain. The article addresses the effects of the uptake of strong privacy technologies by pirates on copyright enforcement and on free speech and privacy technology domains. Also discussed are the norms and values reflected in the specific design choices taken by the developers of the PirateBrowser. Keywords: piracy, privacy, Tor, privacy-enhancing technologies, policy Introduction Tor (The Onion Router), “endorsed by Egyptian activists, WikiLeaks, NSA, GCHQ, Chelsea Manning, Snowden” (Dingledine & Appelbaum, 2013), is a volunteer network of computers that relays Web traffic through itself to provide anonymous, unobserved, and uncensored access to the Internet. It has about 4,000 relays and about 1,000 exit nodes. Tor users connect to the network, and their Web traffic is channeled through the internal relays to reach its final destination through one of the exit nodes. This arrangement makes the identification and surveillance of Tor users difficult. Anonymity is promised by the difficulty of tracing the Web traffic that appears on the exit node back to the individual who initiated the traffic, as long as there is a sufficient number of internal hops in between. Protection from surveillance is granted by the fact that each link in the communication chain is encrypted.