Two Types of Bit String Generating Functions
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Multipermutations 1.1. Generating Functions
CORE Metadata, citation and similar papers at core.ac.uk Provided by Elsevier - Publisher Connector JOURNALOF COMBINATORIALTHEORY, Series A 67, 44-71 (1994) The r- Multipermutations SEUNGKYUNG PARK Department of Mathematics, Yonsei University, Seoul 120-749, Korea Communicated by Gian-Carlo Rota Received October 1, 1992 In this paper we study permutations of the multiset {lr, 2r,...,nr}, which generalizes Gesse| and Stanley's work (J. Combin. Theory Ser. A 24 (1978), 24-33) on certain permutations on the multiset {12, 22..... n2}. Various formulas counting the permutations by inversions, descents, left-right minima, and major index are derived. © 1994 AcademicPress, Inc. 1. THE r-MULTIPERMUTATIONS 1.1. Generating Functions A multiset is defined as an ordered pair (S, f) where S is a set and f is a function from S to the set of nonnegative integers. If S = {ml ..... mr}, we write {m f(mD, .... m f(mr)r } for (S, f). Intuitively, a multiset is a set with possibly repeated elements. Let us begin by considering permutations of multisets (S, f), which are words in which each letter belongs to the set S and for each m e S the total number of appearances of m in the word is f(m). Thus 1223231 is a permutation of the multiset {12, 2 3, 32}. In this paper we consider a special set of permutations of the multiset [n](r) = {1 r, ..., nr}, which is defined as follows. DEFINITION 1.1. An r-multipermutation of the set {ml ..... ran} is a permutation al ""am of the multiset {m~ .... -

40 Chapter 6 the BINOMIAL THEOREM in Chapter 1 We Defined
Chapter 6 THE BINOMIAL THEOREM n In Chapter 1 we defined as the coefficient of an-rbr in the expansion of (a + b)n, and r tabulated these coefficients in the arrangement of the Pascal Triangle: n Coefficients of (a + b)n 0 1 1 1 1 2 1 2 1 3 1 3 3 1 4 1 4 6 4 1 5 1 5 10 10 5 1 6 1 6 15 20 15 6 1 ... n n We then observed that this array is bordered with 1's; that is, ' 1 and ' 1 for n = 0 n 0, 1, 2, ... We also noted that each number inside the border of 1's is the sum of the two closest numbers on the previous line. This property may be expressed in the form n n n%1 (1) % ' . r&1 r r This formula provides an efficient method of generating successive lines of the Pascal Triangle, but the method is not the best one if we want only the value of a single binomial coefficient for a 100 large n, such as . We therefore seek a more direct approach. 3 It is clear that the binomial coefficients in a diagonal adjacent to a diagonal of 1's are the 40 n numbers 1, 2, 3, ... ; that is, ' n. Now let us consider the ratios of binomial coefficients 1 to the previous ones on the same row. For n = 4, these ratios are: (2) 4/1, 6/4 = 3/2, 4/6 = 2/3, 1/4. For n = 5, they are (3) 5/1, 10/5 = 2, 10/10 = 1, 5/10 = 1/2, 1/5. -

Q-Combinatorics
q-combinatorics February 7, 2019 1 q-binomial coefficients n n Definition. For natural numbers n; k,the q-binomial coefficient k q (or just k if there no ambi- guity on q) is defined as the following rational function of the variable q: (qn − 1)(qn−1 − 1) ··· (q − 1) : (1.1) (qk − 1)(qk−1 − 1) ··· (q − 1) · (qn−k − 1)(qn−k−1 − 1) ··· (q − 1) For n = 0, k = 0, or n = k, we interpret the corresponding products 1, as the value of the empty product. If we exclude certain roots of unity from the domain of q, (1.1) is equal to (qn − 1)(qn−1 − 1) ··· (qn−k+1 − 1) (1.2) (qk − 1)(qk−1 − 1) ··· (q − 1) · 1 (qn−1 + ::: + q + 1) ··· (q2 + q + 1)(q + 1) · 1 = : (qk−1 + ::: + q + 1) ··· (q2 + q + 1)(q + 1) · 1(qn−k−1 + ::: + q + 1) ··· (q2 + q + 1)(q + 1) · 1 As the notation starts to be overwhelming, we introduce to q-analogue of the positive integer n, n−1 denoted by [n] or [n]q, as q + ::: + q + 1; and the q-analogue of the factorial of the positive integer n, denoted by [n]! or [n]q!, as [n]q! = [1]q · [2]q ··· [n]q. With this additional notation, we also can say n [n] ! = q ; (1.3) k q [k]q![n − k]q! when we avoid certain roots of unity with q. It is easy too see from (1.1) that n n = = 1 0 q n q and that for every 0 ≤ k ≤ n the symmetry rule n n = k q n − k q holds. -

The Binomial Theorem and Combinatorial Proofs Shagnik Das
The Binomial Theorem and Combinatorial Proofs Shagnik Das Introduction As we live our lives, we are faced with innumerable decisions on a daily basis1. Can I get away with wearing these clothes again before I have to wash them? Which frozen pizza should I have for dinner tonight? What excuse should I use for skipping the gym today? While it may at times seem tiring to be faced with all these choices on a regular basis, it is this exercise of free will that separates us from the machines we live with.2 This multitude of choices, then, provides some measure of our own vitality | the more options we have, the more alive we truly are. What, then, could be more important than being able to count how many options one actually has?4 As we have already seen during our first week of lectures, one of the main protagonists in these counting problems is the binomial coefficient, whose definition is given below. n Definition 1. Given non-negative integers n and k, the binomial coefficient k denotes the number of subsets of size k of a set of n elements. Equivalently, it is the number of unordered choices of k distinct elements from a set of n elements. However, the binomial coefficient leads a double life. Not only does it have the above definition, but also the formula below, which we proved in lecture. Proposition 2. For non-negative integers n and k, n nk n(n − 1)(n − 2) ::: (n − k + 1) n! = = = : k k! k! k!(n − k)! In this note, we will prove several more facts about this most fascinating of creatures. -

Chapter 3.3, 4.1, 4.3. Binomial Coefficient Identities
Chapter 3.3, 4.1, 4.3. Binomial Coefficient Identities Prof. Tesler Math 184A Winter 2019 Prof. Tesler Binomial Coefficient Identities Math 184A / Winter 2019 1 / 36 Table of binomial coefficients n k k = 0 k = 1 k = 2 k = 3 k = 4 k = 5 k = 6 n = 0 1 0 0 0 0 0 0 n = 1 1 1 0 0 0 0 0 n = 2 1 2 1 0 0 0 0 n = 3 1 3 3 1 0 0 0 n = 4 1 4 6 4 1 0 0 n = 5 1 5 10 10 5 1 0 n = 6 1 6 15 20 15 6 1 n n! Compute a table of binomial coefficients using = . k k! (n - k)! We’ll look at several patterns. First, the nonzero entries of each row are symmetric; e.g., row n = 4 is 4 4 4 4 4 0 , 1 , 2 , 3 , 4 = 1, 4, 6, 4, 1 , n n which reads the same in reverse. Conjecture: k = n-k . Prof. Tesler Binomial Coefficient Identities Math 184A / Winter 2019 2 / 36 A binomial coefficient identity Theorem For nonegative integers k 6 n, n n n n = including = = 1 k n - k 0 n First proof: Expand using factorials: n n! n n! = = k k! (n - k)! n - k (n - k)! k! These are equal. Prof. Tesler Binomial Coefficient Identities Math 184A / Winter 2019 3 / 36 Theorem For nonegative integers k 6 n, n n n n = including = = 1 k n - k 0 n Second proof: A bijective proof. We’ll give a bijection between two sets, one counted by the left n n side, k , and the other by the right side, n-k . -

8.6 the BINOMIAL THEOREM We Remake Nature by the Act of Discovery, in the Poem Or in the Theorem
pg476 [V] G2 5-36058 / HCG / Cannon & Elich cr 11-30-95 MP1 476 Chapter 8 Discrete Mathematics: Functions on the Set of Natural Numbers (b) Based on your results for (a), guess the minimum number of handshakes. See Exercise 19, page 469. number of moves required if you start with an arbi- Show trary number of n disks. (Hint: Tohelpseeapat- n~n 2 1! tern,add1tothenumberofmovesforn51, 2, 3, f ~n! 5 for every positive integer n. 4.) 2 (c) A legend claims that monks in a remote monastery 56. Suppose n is an odd positive integer not divisible by 3. areworkingtomoveasetof64disks,andthatthe Show that n 2 2 1 is divisible by 24. (Hint: Consider the world will end when they complete their sacred three consecutive integers n 2 1, n, n 1 1. Explain task. Moving one disk per second without error, 24 why the product ~n 2 1!~n 1 1! must be divisible by 3 hours a day, 365 days a year, how long would it take andby8.) to move all 64 disks? 57. Finding Patterns If an 5 Ï24n 1 1, (a) write out 55. Number of Handshakes Suppose there are n people the first five terms of the sequence $an%. (b) What odd at a party and that each person shakes hands with every integers occur in $an%? (c) Explain why $an% contains all other person exactly once. Let f~n! denote the total primes greater than 3. (Hint: UseExercise56.) 8.6 THE BINOMIAL THEOREM We remake nature by the act of discovery, in the poem or in the theorem. -

Discrete Math for Computer Science Students
Discrete Math for Computer Science Students Cliff Stein Ken Bogart Scot Drysdale Dept. of Industrial Engineering Dept. of Mathematics Dept. of Computer Science and Operations Research Dartmouth College Dartmouth College Columbia University ii c Kenneth P. Bogart, Scot Drysdale, and Cliff Stein, 2004 Contents 1 Counting 1 1.1 Basic Counting . 1 The Sum Principle . 1 Abstraction . 2 Summing Consecutive Integers . 3 The Product Principle . 3 Two element subsets . 5 Important Concepts, Formulas, and Theorems . 6 Problems . 7 1.2 Counting Lists, Permutations, and Subsets. 9 Using the Sum and Product Principles . 9 Lists and functions . 10 The Bijection Principle . 12 k-element permutations of a set . 13 Counting subsets of a set . 13 Important Concepts, Formulas, and Theorems . 15 Problems . 16 1.3 Binomial Coefficients . 19 Pascal’s Triangle . 19 A proof using the Sum Principle . 20 The Binomial Theorem . 22 Labeling and trinomial coefficients . 23 Important Concepts, Formulas, and Theorems . 24 Problems . 25 1.4 Equivalence Relations and Counting (Optional) . 27 The Symmetry Principle . 27 iii iv CONTENTS Equivalence Relations . 28 The Quotient Principle . 29 Equivalence class counting . 30 Multisets . 31 The bookcase arrangement problem. 32 The number of k-element multisets of an n-element set. 33 Using the quotient principle to explain a quotient . 34 Important Concepts, Formulas, and Theorems . 34 Problems . 35 2 Cryptography and Number Theory 39 2.1 Cryptography and Modular Arithmetic . 39 Introduction to Cryptography . 39 Private Key Cryptography . 40 Public-key Cryptosystems . 42 Arithmetic modulo n .................................. 43 Cryptography using multiplication mod n ...................... 47 Important Concepts, Formulas, and Theorems . 48 Problems . 49 2.2 Inverses and GCDs . -

Combinatorial Proofs of Fibonomial Identities 1
COMBINATORIAL PROOFS OF FIBONOMIAL IDENTITIES ARTHUR T. BENJAMIN AND ELIZABETH REILAND Abstract. Fibonomial coefficients are defined like binomial coefficients, with integers re- placed by their respective Fibonacci numbers. For example, 10 = F10F9F8 . Remarkably, 3 F F3F2F1 n is always an integer. In 2010, Bruce Sagan and Carla Savage derived two very nice k F combinatorial interpretations of Fibonomial coefficients in terms of tilings created by lattice paths. We believe that these interpretations should lead to combinatorial proofs of Fibonomial identities. We provide a list of simple looking identities that are still in need of combinatorial proof. 1. Introduction What do you get when you cross Fibonacci numbers with binomial coefficients? Fibono- mial coefficients, of course! Fibonomial coefficients are defined like binomial coefficients, with integers replaced by their respective Fibonacci numbers. Specifically, for n ≥ k ≥ 1, n F F ··· F = n n−1 n−k+1 k F F1F2 ··· Fk For example, 10 = F10F9F8 = 55·34·21 = 19;635. Fibonomial coefficients resemble binomial 3 F F3F2F1 1·1·2 n coefficients in many ways. Analogous to the Pascal Triangle boundary conditions 1 = n and n n n n n = 1, we have 1 F = Fn and n F = 1. We also define 0 F = 1. n n−1 n−1 Since Fn = Fk+(n−k) = Fk+1Fn−k + FkFn−k−1, Pascal's recurrence k = k + k−1 has the following analog. Identity 1.1. For n ≥ 2, n n − 1 n − 1 = Fk+1 + Fn−k−1 : k F k F k − 1 F n As an immediate corollary, it follows that for all n ≥ k ≥ 1, k F is an integer. -

Some Identities Involving Polynomial Coefficients
Some identities involving polynomial coefficients Nour-Eddine Fahssi Department of Mathematics, FSTM, Hassan Second University of Casablanca, BP 146, Mohammedia, Morocco. [email protected] Abstract By polynomial (or extended binomial) coefficients, we mean the coefficients in the ex- pansion of integral powers, positive and negative, of the polynomial 1 + t + + tm; m 1 being a fixed integer. We will establish several identities and summation formulæ· · · parallel≥ to those of the usual binomial coefficients. 2010 AMS Classification Numbers: 11B65, 05A10, 05A19. 1 Introduction and preliminaries Definition 1.1. Let m 1 be an integer and let p (t)=1+ t + + tm. The coefficients ≥ m · · · defined by 1 k n n def [t ] (p (t)) , if k Z , n Z = m ∈ ≥ ∈ (1.1) k 0, if k Z≥ or k >mn whenever n Z>, !m ( 6∈ ∈ are called polynomial coefficients [10] or extended binomial coefficients. When the rows are indexed by n and the columns by k, the polynomial coefficients form an array called polynomial array of degree m and denoted by Tm. The sub-array corresponding to positive n is termed T+ extended Pascal triangle of degree m, or Pascal-De Moivre triangle, and denoted by m. For instance, the array T3 begins as shown in Table 1. arXiv:1507.07968v2 [math.NT] 30 Mar 2016 T+ The study of the coefficients of m is an old problem. Its history dates back at least to De Moivre [4, 11] and Euler [14]. In modern times, they have been studied in many papers, including several in The Fibonacci Quarterly. See [16] for a systematic treatise on the subject and an extensive bibliography. -
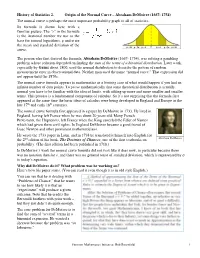
History of Statistics 2. Origin of the Normal Curve – Abraham Demoivre
History of Statistics 2. Origin of the Normal Curve – Abraham DeMoivre (1667- 1754) The normal curve is perhaps the most important probability graph in all of statistics. Its formula is shown here with a familiar picture. The “ e” in the formula is the irrational number we use as the base for natural logarithms. μ and σ are the mean and standard deviation of the curve. The person who first derived the formula, Abraham DeMoivre (1667- 1754), was solving a gambling problem whose solution depended on finding the sum of the terms of a binomial distribution. Later work, especially by Gauss about 1800, used the normal distribution to describe the pattern of random measurement error in observational data. Neither man used the name “normal curve.” That expression did not appear until the 1870s. The normal curve formula appears in mathematics as a limiting case of what would happen if you had an infinite number of data points. To prove mathematically that some theoretical distribution is actually normal you have to be familiar with the idea of limits, with adding up more and more smaller and smaller terms. This process is a fundamental component of calculus. So it’s not surprising that the formula first appeared at the same time the basic ideas of calculus were being developed in England and Europe in the late 17 th and early 18 th centuries. The normal curve formula first appeared in a paper by DeMoivre in 1733. He lived in England, having left France when he was about 20 years old. Many French Protestants, the Huguenots, left France when the King canceled the Edict of Nantes which had given them civil rights. -

Enumerative Combinatorics 5: Q-Analogues
Enumerative Combinatorics 5: q-analogues Peter J. Cameron Autumn 2013 In a sense, a q-analogue of a combinatorial formula is simply another formula involving a variable q which has the property that, as q ! 1, the second formula becomes the first. Of course there is more to it than that; some q-analogues are more important than others. What follows is nothing like a complete treatment; I will concentrate on a particularly important case, the Gaussian or q-binomial coefficients, which are, in the above sense, q-analogues of binomial coefficients. 5.1 Definition of Gaussian coefficients The Gaussian (or q-binomial) coefficient is defined for non-negative integers n and k as n (qn − 1)(qn−1 − 1) ··· (qn−k+1 − 1) = k k−1 : k q (q − 1)(q − 1) ··· (q − 1) In other words, in the formula for the binomial coefficient, we replace each factor r by qr − 1. Note that this is zero if k > n; so we may assume that k ≤ n. qr − 1 Now observe that lim = r. This follows from l'H^opital's rule: both q!1 q − 1 numerator and denominator tend to 0, and their derivatives are rqr−1 and 1, whose ratio tends to r. Alternatively, use the fact that qr − 1 = 1 + q + ··· + qr−1; q − 1 and we can now harmlessly substitute q = 1 in the right-hand side; each of the r terms becomes 1. 1 Hence if we replace each factor (qr − 1) in the definition of the Gaussian coefficient by (qr − 1)=(q − 1), then the factors (q − 1) in numerator and denominator cancel, so the expression is unchanged; and now it is clear that n n lim = : q!1 k q k 5.2 Interpretations Quantum calculus The letter q stands for \quantum", and the q-binomial coefficients do play a role in \quantum calculus" similar to that of the ordi- nary binomial coefficients in ordinary calculus. -

IB Math SL Summer Assignment and Formula Booklet.Pdf
IB Math SL Summer Assignment 2019-2020 The IB Math SL curriculum covers six different mathematical topics (algebra, functions, trigonometry, vectors, statistics, and calculus). Three of these six topics were thoroughly covered in your Pre-Calculus class (algebra, functions, and trigonometry). In an effort to best prepare you for the IB paper exams at the end of the year, three topics need to be reviewed during the summer. This will leave the class with more time during the school year to focus on statistics and calculus. The summer assignment will be broken up into three sections in which I have written a suggested timeline in which they should be completed: Topic 1: Algebra- finish by June 22nd Topic 2: Functions- finish by July 13th Topic 3: Trigonometry- finish by July 31st Every topic should be turned in by the first day of class. Please complete all work in sequential order on separate paper and write your final answers on the actual assignment. The summer assignment will be worth a quiz grade and there will be a test over this material within the first three weeks of the school year. To assist you in each topic, here are links to video tutorials: https://sites.google.com/a/roundrockisd.org/kyle-bell/ib-math-sl-summer-assignment https://osc-ib.com/ib-revision-videos I also suggest using notes from your previous Pre-Calculus course along with the attached formula booklet for reference. This formula booklet is what you will be allowed to use on the paper exam. If you have any questions, you can email me at [email protected] and I will return your email as soon as I can.