Using Linux the CLI Way - Cheat Sheet
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

At—At, Batch—Execute Commands at a Later Time
at—at, batch—execute commands at a later time at [–csm] [–f script] [–qqueue] time [date] [+ increment] at –l [ job...] at –r job... batch at and batch read commands from standard input to be executed at a later time. at allows you to specify when the commands should be executed, while jobs queued with batch will execute when system load level permits. Executes commands read from stdin or a file at some later time. Unless redirected, the output is mailed to the user. Example A.1 1 at 6:30am Dec 12 < program 2 at noon tomorrow < program 3 at 1945 pm August 9 < program 4 at now + 3 hours < program 5 at 8:30am Jan 4 < program 6 at -r 83883555320.a EXPLANATION 1. At 6:30 in the morning on December 12th, start the job. 2. At noon tomorrow start the job. 3. At 7:45 in the evening on August 9th, start the job. 4. In three hours start the job. 5. At 8:30 in the morning of January 4th, start the job. 6. Removes previously scheduled job 83883555320.a. awk—pattern scanning and processing language awk [ –fprogram–file ] [ –Fc ] [ prog ] [ parameters ] [ filename...] awk scans each input filename for lines that match any of a set of patterns specified in prog. Example A.2 1 awk '{print $1, $2}' file 2 awk '/John/{print $3, $4}' file 3 awk -F: '{print $3}' /etc/passwd 4 date | awk '{print $6}' EXPLANATION 1. Prints the first two fields of file where fields are separated by whitespace. 2. Prints fields 3 and 4 if the pattern John is found. -

TDS) EDEN PG MV® Pigment Ink for Textile
Technical Data Sheet (TDS) EDEN PG MV® Pigment Ink for Textile Product Description: Applications: EDEN PG MV water based pigment Ink is ideal for high-speed direct digital printing on all standard fabrics available on the market. The ink prints on all types of fabrics with equal quality and coverage without color shifts or patches. EDEN PG MV Pigment Ink may be used on cotton, cotton blends, polyester, polyamide (nylon) and treated & untreated fabrics. EDEN PG MV is ideal for a wide range of applications including sportswear, footwear, fashion, home décor and home textile and is designed for indoor and outdoor applications. This ink is manufactured using cutting edge technology and • Home textile • Bags • Indoor furnishing high-performance pigments, for optimal ink fluidity and • Décor • Sport apparel • Fashion & apparel printability through piezo printheads without bleeding or • Footwear migration. Compatible Print Head Technology: Ricoh Gen 4 & Gen 5 Industrial print heads based printers. Pre-treatment: The use of Bordeaux EDEN PG™ OS® (pretreatment liquid) is Product Line: recommended in order to achieve higher chemical attributes (see table below for comparison). The pretreatment process for fabrics is done offline using a standard textile padder. Red Cleaning Print procedure: Cyan Magenta Yellow Black Magenta Liquid The printing process can be done either inline or in individual segments. Inline printing allows the printed fabric to be fed Material Compatibility: through a standard textile dryer directly. Alternatively, if the printing stage is separated from the drying stage, drying is • Cotton required before rolling the fabric. • Viscose • Polyester • Lycra Drying Working Parameters: • Silk Recommended drying time: 3 minutes • Polyamide Recommended temperature: 150°C (302°F) • Leather • Synthetic leather Post-treatment: No chemical post treatment is needed. -

ISDN TA PC Card User Manual INTRODUCTION the ISDN TA PC Card Brings the Latest in Mobile Communication Technology with Flexibility and Convenience
ISDN TA PC Card User Manual INTRODUCTION The ISDN TA PC Card brings the latest in mobile communication technology with flexibility and convenience. With the wide range ISDN signaling protocols switches supports, mobile experts may enjoy the mobile communication across the world and the high speed digital service. System Requirements Pentium 75 or above At least 30MB free hard disk space At least 16MB RAM PCMCIA Type II/III slot PCMCIA Card Services and Socket Services v.2.1 or higher pre-installed Windows 95/98/2000 or Windows NT pre-installed Specifications Standard PCMCIA 2.1 & JEIDA 4.1 compliant ISDN standards Basic Rate Access (2B+D) S/T-Interface: Compliant with ITU-T I.430 D-channel: ITU-T Q.921, Q.931 ETSI NET3 B-channel: V.120, V.110, X.75/T.70NL/ISO8208 Async-to-Sync PPP conversion Multilink PPP, 56 K Modem (CAPI only) G3 fax (CAPI only) - 1 - Voice (CAPI only) Line Rate 64/56 Kbps on 1 B-channel 128/112 Kbps on 2 B-channel (PPP/MP) 64/56Kbps on 1 B-channel 16Kbps on D-channel ISDN Network & Switch Compatibility National ISDN-1 (NI-1) AT&T 5ESS Custom Northen Telecom DMS-100 Custom DSS1 (Euro-ISDN) INS-Net 64 Application Program Interface Supported VCOMM WinISDN CAPI 2.0 NDIS WAN Operating System Supported Windows 95 and OSR2 Windows 98 Windows 2000 Windows NT 4.0 Physical Specifications RJ-45 ISDN line interface Dimension: 85.6 x 54 x 5 (mm) PCMCIA Type II - 2 - Parts Names 15-pin PC Card Connector ISDN Network Connection Cable - 3 - HARDWARE INSTALLATION If you are using the ISDN TA PC Card under Windows 95/98/2000, Do NOT insert the PCMCIA card until after the software installation is completed. -

Relational Constraint Driven Test Case Synthesis for Web Applications
Relational Constraint Driven Test Case Synthesis for Web Applications Xiang Fu Hofstra University Hempstead, NY 11549 [email protected] This paper proposes a relational constraint driven technique that synthesizes test cases automatically for web applications. Using a static analysis, servlets can be modeled as relational transducers, which manipulate backend databases. We present a synthesis algorithm that generates a sequence of HTTP requests for simulating a user session. The algorithm relies on backward symbolic image computation for reaching a certain database state, given a code coverage objective. With a slight adaptation, the technique can be used for discovering workflow attacks on web applications. 1 Introduction Modern web applications usually rely on backend database systems for storing important system infor- mation or supporting business decisions. The complexity of database queries, however, often complicates the task of thoroughly testing a web application. To manually design test cases involves labor intensive initialization of database systems, even with the help of unit testing tools such as SQLUnit [25] and DBUnit [8]. It is desirable to automatically synthesize test cases for web applications. There has been a strong interest recently in testing database driven applications and database man- agement systems (see e.g., [12, 4, 20]). Many of them are query aware, i.e., given a SQL query, an initial database (DB) instance is generated to make that query satisfiable. The DB instance is fed to the target web application as input, so that a certain code coverage goal is achieved. The problem we are trying to tackle is one step further – it is a synthesis problem: given a certain database state (or a relational constraint), a call sequence of web servlets is synthesized to reach the given DB state. -
LINUX INTERNALS LABORATORY III. Understand Process
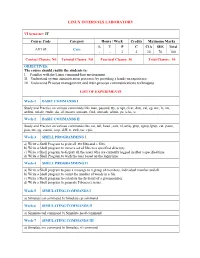
LINUX INTERNALS LABORATORY VI Semester: IT Course Code Category Hours / Week Credits Maximum Marks L T P C CIA SEE Total AIT105 Core - - 3 2 30 70 100 Contact Classes: Nil Tutorial Classes: Nil Practical Classes: 36 Total Classes: 36 OBJECTIVES: The course should enable the students to: I. Familiar with the Linux command-line environment. II. Understand system administration processes by providing a hands-on experience. III. Understand Process management and inter-process communications techniques. LIST OF EXPERIMENTS Week-1 BASIC COMMANDS I Study and Practice on various commands like man, passwd, tty, script, clear, date, cal, cp, mv, ln, rm, unlink, mkdir, rmdir, du, df, mount, umount, find, unmask, ulimit, ps, who, w. Week-2 BASIC COMMANDS II Study and Practice on various commands like cat, tail, head , sort, nl, uniq, grep, egrep,fgrep, cut, paste, join, tee, pg, comm, cmp, diff, tr, awk, tar, cpio. Week-3 SHELL PROGRAMMING I a) Write a Shell Program to print all .txt files and .c files. b) Write a Shell program to move a set of files to a specified directory. c) Write a Shell program to display all the users who are currently logged in after a specified time. d) Write a Shell Program to wish the user based on the login time. Week-4 SHELL PROGRAMMING II a) Write a Shell program to pass a message to a group of members, individual member and all. b) Write a Shell program to count the number of words in a file. c) Write a Shell program to calculate the factorial of a given number. -

Front Matter + Functional
Infortrend External RAID Controller & Subsystem Generic Operation Manual Revision 1.62 Firmware Version: 3.31h Asia Pacific Americas (International headquarter) Infortrend Technology, Inc. Infortrend Corporation 8F, No. 102 Chung-Shan Rd., Sec. 3 3150 Coronado Drive, Unit C Chung-Ho City, Taipei Hsien, Taiwan Santa Clara, CA 95054, USA Tel: (886)-2-2226-0126 Tel: (408) 988-5088 Fax: (886)-2-2226-0020 Fax: (408) 988-6288 [email protected] [email protected] [email protected] [email protected] www.infortrend.com.tw www.infortrend.com China Europe (EMEA) Infortrend Technology, Limited Infortrend Europe Limited Room 1210, West Wing, Tower One, 5 Elmwood, Crockford Lane Junefield Plaza, No. 6 Xuanwumen Street, Chineham Business Park Xuanwu District, Beijing, China. Basingstoke, Hampshire Post code: 100052 RG24 8WG, UK Tel: 8610-63106168 Tel: +44-1256-70-77-00 Fax: 8610-63106188 Fax:+44-1256-70-78-89 [email protected] [email protected] [email protected] [email protected] www.infortrend.com.cn www.infortrend-europe.com Copyright © 2003 This Edition First Published 2003 All rights reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated into any language or computer language, in any form or by any means, electronic, mechanical, magnetic, optical, chemical, manual or otherwise, without the prior written consent of Infortrend Technology, Inc. Disclaimer Infortrend Technology makes no representations or warranties with respect to the contents hereof and specifically disclaims any implied warranties of merchantability or fitness for any particular purpose. Furthermore, Infortrend Technology reserves the right to revise this publication and to make changes from time to time in the content hereof without oblig- ation to notify any person of such revisions or changes. -

Unix Programming
P.G DEPARTMENT OF COMPUTER APPLICATIONS 18PMC532 UNIX PROGRAMMING K1 QUESTIONS WITH ANSWERS UNIT- 1 1) Define unix. Unix was originally written in assembler, but it was rewritten in 1973 in c, which was principally authored by Dennis Ritchie ( c is based on the b language developed by kenThompson. 2) Discuss the Communication. Excellent communication with users, network User can easily exchange mail,dta,pgms in the network 3) Discuss Security Login Names Passwords Access Rights File Level (R W X) File Encryption 4) Define PORTABILITY UNIX run on any type of Hardware and configuration Flexibility credits goes to Dennis Ritchie( c pgms) Ported with IBM PC to GRAY 2 5) Define OPEN SYSTEM Everything in unix is treated as file(source pgm, Floppy disk,printer, terminal etc., Modification of the system is easy because the Source code is always available 6) The file system breaks the disk in to four segements The boot block The super block The Inode table Data block 7) Command used to find out the block size on your file $cmchk BSIZE=1024 8) Define Boot Block Generally the first block number 0 is called the BOOT BLOCK. It consists of Hardware specific boot program that loads the file known as kernal of the system. 9) Define super block It describes the state of the file system ie how large it is and how many maximum Files can it accommodate This is the 2nd block and is number 1 used to control the allocation of disk blocks 10) Define inode table The third segment includes block number 2 to n of the file system is called Inode Table. -

Products for Totally Integrated Automation
ST70_2015_en_Kap01.book Seite 1 Mittwoch, 20. Mai 2015 12:16 12 © Siemens AG 2015 Introduction 1 1/2 LOGO! logic module 1/3 SIMATIC basic controller 1/3 SIMATIC S7-1200 1/4 SIMATIC advanced controller 1/4 SIMATIC S7-1500 1/5 SIMATIC S7-300 1/7 SIMATIC S7-400 1/9 SIMATIC distributed controllers 1/11 SIMATIC software controllers 1/12 SIMATIC WinAC RTX (F) 1/12 SIMATIC programming devices 1/12 SIMATIC Field PG M4 1/13 SIMATIC Industrial PCs 1/14 SIMATIC software 1/15 SIMATIC ET 200 1/16 SIMATIC HMI 1/17 SIMATIC PCS 7 1/18 SIMATIC NET Brochures For brochures serving as selection guides for SIMATIC products refer to: www.siemens.com/simatic/ printmaterial Siemens ST 70 · 2015 ST70_2015_en_Kap01.book Seite 2 Mittwoch, 20. Mai 2015 12:16 12 © Siemens AG 2015 Introduction LOGO! LOGO! logic module 1 ■ Overview LOGO!: Easy-to-use technology with a future The compact, easy-to-use and low-cost solution for simple control tasks. Universally applicable in industry, and in functional or residential buildings. Replaces wiring by linking functions. Operates in a similar way to a programmable logic controller. With integrated operating and display unit for direct input on the device and display of message texts/variables, or as a version without display or keys. Simple operation: • Interconnection of functions by mouse click on the PC or at the press of a button on the device Minimum time requirements: • Wiring solely of the inputs and outputs • Parallel creation of circuit diagram and assembly of control cabinet Reduced costs: • Many integral functions of switching technology High level of flexibility: • Simple modification of functionality at the press of a button • Versions for different operating voltages • Modular design, therefore expandable at any time For further information, refer to: LOGO! 8 versions: www.siemens.com/logo • Ethernet interface for programming and communication with SIMATIC Controllers, SIMATIC Panels and PCs • Networking of max. -

The PC Weasel PCI
The PC Weasel PCI Making servers run headless since 1999 User Documentation - Version 1.01 PC Weasel PCI Table of Contents Section . .Page Contact Information . 3 Documentation Revision History . 3 Introduction . 5 Installation Guide . 7 PC Weasel User Guide . 11 Loading the PC Weasel firmware . 29 Application notes . 33 Appendix 1: Motorola Format . 39 Copyright 2002 Middle Digital Incorporated 1 PC Weasel PCI User Documentation - Version 1.01 Blank page alert. 2 Copyright 2002 Middle Digital Incorporated User Documentation - Version 1.01 PC Weasel PCI Contact Information Web Page http://www.realweasel.com/ FTP Server ftp://ftp.realweasel.com/pub/realweasel/ Demo System PCI: telnet://pci-demo.realweasel.com ISA: telnet://isa-demo.realweasel.com Technical Support [email protected] Sales [email protected] Documentation [email protected] (for comments & corrections) Mailing Address Middle Digital Incorporated PO Box 2621, Station M Calgary, Alberta, Canada T2P 3C1 Address for Courier Service Middle Digital Incorporated not Post 238 11th Avenue SE Calgary, Alberta, Canada T2G 0X8 Vox 403-705-2025 Fax 403-705-2026 Documentation Revision History First release: 1.00 (somewhat premature) December 15th, 2001. Second release: 1.01 (minor corrections) March 4th, 2002. Copyright 2002 Middle Digital Incorporated 3 PC Weasel PCI User Documentation - Version 1.01 Blank page test. 4 Copyright 2002 Middle Digital Incorporated User Documentation - Version 1.01 PC Weasel PCI 1. Introduction The PC Weasel PCI is the mutant bastard child of Big Blue, open-source computing, and an inbred mass-murdering hillbilly. Depending on your point of view, it's either: a) a video board with serial output instead of a monitor and a keyboard with serial input instead of keys, or b) a serial board that emulates a video board and a keyboard. -

PG8952 89C51/89C52/89C55 Programmer - Intel Hex Serial ELECTRONICS
V1.01 ELECTRONICS PG8952 89C51/89C52/89C55 Programmer - Intel Hex serial ELECTRONICS DISTINCTIVE CHARACTERISTICS • Erases, Programs & Verifies Atmel 40 pin micros • Green/Red Indicator LEDs • 89C51/52 Devices use FLASH program memory • Programs Security bits, if required - Can be reprogrammed 1000 times per chip - Dipswitch selectable - 10ms electronic erasure, vs. 30 minute UV • One Step program operation, as set by dipswitch • Programmer interface is PC serial compatible - Download starts Test/Erase/Program/Verify - 9600 Baud, 8 data, 2 stop bits, no parity • No special PC software required - Accepts standard Intel Hex files • Programs 89C51, 89C52, 89C55, 89LV51, - Programs on the fly - during serial download 89LV52, 89C55 • Stand-alone test switch • Fast operation - programs 4kbytes in 12 sec (typ) - Allows chip operating test without PC download • Powered by DC plug pack (supplied) - Tests for blank chip without PC download - Reads & Verifies chip data against last checksum GENERAL DESCRIPTION The PG8952 is a development programmer for the ATMEL indicates Tested, Blank and Verified checksum conditions. AT89C51 family, - Referred to as the 89C51. References made here to the 89C51 apply equally to the 89C52/55. In normal use device programming consists of: The PG8952 allows testing, erasure, programming, verifi- • Insert an 89C51 (Manual Test if desired) cation and security protection of 89C51 devices. The • Download intel hex file (Causes programming) programmer is fast, small and simple to use. • Watch LEDs (Indicates success or failure) The Programmer may be connected to a PC or other host The speed of programming is limited by the speed of by a serial cable. The data to be downloaded to the download, and for a 4 kilobyte file - the capacity of the programmer is transmitted in Intel Hex format. -

Front Matter + Functional
Infortrend External RAID Controller & Subsystem Generic Operation Manual Revision 1.61 Firmware Version: 3.31 Asia Pacific Americas (International headquarter) Infortrend Technology, Inc. Infortrend Corporation 8F, No. 102 Chung-Shan Rd., Sec. 3 3150 Coronado Drive, Unit C Chung-Ho City, Taipei Hsien, Taiwan Santa Clara, CA 95054, USA Tel: (886)-2-2226-0126 Tel: (408) 988-5088 Fax: (886)-2-2226-0020 Fax: (408) 988-6288 [email protected] [email protected] [email protected] [email protected] www.infortrend.com.tw www.infortrend.com China Europe Infortrend Technology, Limited Infortrend Europe Limited Room 1236 Tower C Corporate Square Ground Floor, Chancery House No. 35 Financial Street Xicheng District St. Nicholas Way, Sutton, Beijing China 100032 Surrey, SM1 1JB, United Kingdom Tel: (86)-10-88091540 Tel:+44-(0)20 8770 1838 Fax: (86)-10-88092126 Fax:+44-(0)20 8770 7409 [email protected] [email protected] [email protected] [email protected] www.infortrend.com.cn www.infortrend-europe.com Copyright © 2003 This Edition First Published 2003 All rights reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated into any language or computer language, in any form or by any means, electronic, mechanical, magnetic, optical, chemical, manual or otherwise, without the prior written consent of Infortrend Technology, Inc. Disclaimer Infortrend Technology makes no representations or warranties with respect to the contents hereof and specifically disclaims any implied warranties of merchantability or fitness for any particular purpose. Furthermore, Infortrend Technology reserves the right to revise this publication and to make changes from time to time in the content hereof without oblig- ation to notify any person of such revisions or changes. -

PUBLIC NOTICE Us* - FEDERAL COMMUNICATIONS COMMISSION 1919 M STREET N.W
PUBLIC NOTICE us* - FEDERAL COMMUNICATIONS COMMISSION 1919 M STREET N.W. WASHINGTON, D.C. 20554 News media information 202/4184500 Recorded listing of releases and texts 202/418-2222. DA 96-588 April 15,1996 CORRECTION TO PUBLIC NOTICE DA 96-586 "FCC Announces Winning Bidders in the Auction of 1,020 Licenses to Provide 900 MHz SMR in Major Trading Areas" FCC Form 159 For the "License No." designation in Block 18 of FCC Form 159, winning bidders should list the "License No." as it appears in Attachment C of the Bidder Information Package, e.g. YSMO51A. Examples of Down Payment Calculations Example 1 Upfront Payment Amount $5,000 Withdrawal Payment Amount $0 Amount of Upfront to be Counted Towards Down Payment $5,000 Small Business Status Small business under the $15 million definition High Bid Net High Down ProRata% Amtfrom Balance Amount BidAmt Payment ofDown Upfront Due Amount Payment Payment Lie. A $80,000 $72,000 $3,600 25% $1,250 $2350 Lic.B $100,000 $90,000 $4,500 75% $3,750 $750 (100%) 18636 Attachment D- Electronic Filing The Commission recently implemented a remote access system which will allow applicants to submit their FCC applications electronically. FCC applications that are filed electronically using this remote access system must be submitted and confirmed by April 29, 1996. An FCC application may be submitted only once; no changes will be permitted after the submission of an FCC application. More detailed filing instructions will be provided in the Help facility and in the Readme.txt file associated with the FCC Electronic Filing/Application Review Software.