On Positive Influence Dominating Sets in Social Networks✩
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Travelling Salesman Problem in Bounded Degree Graphs*
The Travelling Salesman Problem in Bounded Degree Graphs? Andreas Bj¨orklund1, Thore Husfeldt1, Petteri Kaski2, and Mikko Koivisto2 1 Lund University, Department of Computer Science, P.O.Box 118, SE-22100 Lund, Sweden, e-mail: [email protected], [email protected] 2 Helsinki Institute for Information Technology HIIT, Department of Computer Science, University of Helsinki, P.O.Box 68, FI-00014 University of Helsinki, Finland, e-mail: [email protected], Abstract. We show that the travelling salesman problem in bounded- degree graphs can be solved in time O((2 − )n), where > 0 depends only on the degree bound but not on the number of cities, n. The algo- rithm is a variant of the classical dynamic programming solution due to Bellman, and, independently, Held and Karp. In the case of bounded in- teger weights on the edges, we also present a polynomial-space algorithm with running time O((2 − )n) on bounded-degree graphs. 1 Introduction There is no faster algorithm known for the travelling salesman problem than the classical dynamic programming solution from the early 1960s, discovered by Bellman [2, 3], and, independently, Held and Karp [9]. It runs in time within a polynomial factor of 2n, where n is the number of cities. Despite the half a cen- tury of algorithmic development that has followed, it remains an open problem whether the travelling salesman problem can be solved in time O(1.999n) [15]. In this paper we provide such an upper bound for graphs with bounded maximum vertex degree. For this restricted graph class, previous attemps have succeeded to prove such bounds when the degree bound, ∆, is three or four. -

On Snarks That Are Far from Being 3-Edge Colorable
On snarks that are far from being 3-edge colorable Jonas H¨agglund Department of Mathematics and Mathematical Statistics Ume˚aUniversity SE-901 87 Ume˚a,Sweden [email protected] Submitted: Jun 4, 2013; Accepted: Mar 26, 2016; Published: Apr 15, 2016 Mathematics Subject Classifications: 05C38, 05C70 Abstract In this note we construct two infinite snark families which have high oddness and low circumference compared to the number of vertices. Using this construction, we also give a counterexample to a suggested strengthening of Fulkerson's conjecture by showing that the Petersen graph is not the only cyclically 4-edge connected cubic graph which require at least five perfect matchings to cover its edges. Furthermore the counterexample presented has the interesting property that no 2-factor can be part of a cycle double cover. 1 Introduction A cubic graph is said to be colorable if it has a 3-edge coloring and uncolorable otherwise. A snark is an uncolorable cubic cyclically 4-edge connected graph. It it well known that an edge minimal counterexample (if such exists) to some classical conjectures in graph theory, such as the cycle double cover conjecture [15, 18], Tutte's 5-flow conjecture [19] and Fulkerson's conjecture [4], must reside in this family of graphs. There are various ways of measuring how far a snark is from being colorable. One such measure which was introduced by Huck and Kochol [8] is the oddness. The oddness of a bridgeless cubic graph G is defined as the minimum number of odd components in any 2-factor in G and is denoted by o(G). -

Fast Dynamic Programming on Graph Decompositions
Fast Dynamic Programming on Graph Decompositions∗ Johan M. M. van Rooij† Hans L. Bodlaender† Erik Jan van Leeuwen‡ Peter Rossmanith§ Martin Vatshelle‡ June 6, 2018 Abstract In this paper, we consider three types of graph decompositions, namely tree decompo- sitions, branch decompositions, and clique decompositions. We improve the running time of dynamic programming algorithms on these graph decompositions for a large number of problems as a function of the treewidth, branchwidth, or cliquewidth, respectively. Such algorithms have many practical and theoretical applications. On tree decompositions of width k, we improve the running time for Dominating Set to O∗(3k). Hereafter, we give a generalisation of this result to [ρ,σ]-domination problems with finite or cofinite ρ and σ. For these problems, we give O∗(sk)-time algorithms. Here, s is the number of ‘states’ a vertex can have in a standard dynamic programming algorithm for such a problems. Furthermore, we give an O∗(2k)-time algorithm for counting the number of perfect matchings in a graph, and generalise this result to O∗(2k)-time algorithms for many clique covering, packing, and partitioning problems. On branch decompositions of width k, we give ∗ ω k ∗ ω k an O (3 2 )-time algorithm for Dominating Set, an O (2 2 )-time algorithm for counting ∗ ω k the number of perfect matchings, and O (s 2 )-time algorithms for [ρ,σ]-domination problems involving s states with finite or cofinite ρ and σ. Finally, on clique decompositions of width k, we give O∗(4k)-time algorithms for Dominating Set, Independent Dominating Set, and Total Dominating Set. -

Complexity and Approximation Results for the Connected Vertex Cover Problem in Graphs and Hypergraphs Bruno Escoffier, Laurent Gourvès, Jérôme Monnot
Complexity and approximation results for the connected vertex cover problem in graphs and hypergraphs Bruno Escoffier, Laurent Gourvès, Jérôme Monnot To cite this version: Bruno Escoffier, Laurent Gourvès, Jérôme Monnot. Complexity and approximation results forthe connected vertex cover problem in graphs and hypergraphs. 2007. hal-00178912 HAL Id: hal-00178912 https://hal.archives-ouvertes.fr/hal-00178912 Preprint submitted on 12 Oct 2007 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Laboratoire d'Analyse et Modélisation de Systèmes pour l'Aide à la Décision CNRS UMR 7024 CAHIER DU LAMSADE 262 Juillet 2007 Complexity and approximation results for the connected vertex cover problem in graphs and hypergraphs Bruno Escoffier, Laurent Gourvès, Jérôme Monnot Complexity and approximation results for the connected vertex cover problem in graphs and hypergraphs Bruno Escoffier∗ Laurent Gourv`es∗ J´erˆome Monnot∗ Abstract We study a variation of the vertex cover problem where it is required that the graph induced by the vertex cover is connected. We prove that this problem is polynomial in chordal graphs, has a PTAS in planar graphs, is APX-hard in bipartite graphs and is 5/3-approximable in any class of graphs where the vertex cover problem is polynomial (in particular in bipartite graphs). -

Total Domination on Some Graph Operators
mathematics Article Total Domination on Some Graph Operators José M. Sigarreta Faculty of Mathematics, Autonomous University of Guerrero, Carlos E. Adame 5, Col. La Garita, C. P. 39350 Acapulco, Mexico; [email protected]; Tel.: +52-744-159-2272 Abstract: Let G = (V, E) be a graph; a set D ⊆ V is a total dominating set if every vertex v 2 V has, at least, one neighbor in D. The total domination number gt(G) is the minimum cardinality among all total dominating sets. Given an arbitrary graph G, we consider some operators on this graph; S(G), R(G), and Q(G), and we give bounds or the exact value of the total domination number of these new graphs using some parameters in the original graph G. Keywords: domination theory; total domination; graph operators 1. Introduction The study of the mathematical and structural properties of operators in graphs was initiated in Reference [1]. This study is a current research topic, mainly because of its multiple theoretical and practical applications (see References [2–6]). Motivated by the previous investigations, we work here on the total domination number of some graph operators. Other important parameters have also been studied in this type of graphs (see References [7,8]). We denote by G = (V, E) a finite simple graph of order n = jVj and size m = jEj. For any two adjacent vertices u, v 2 V, uv denotes the corresponding edge, and we denote N(v) = fu 2 V : uv 2 Eg and N[v] = N(v) [ fvg. We denote by D, d the maximum and Citation: Sigarreta, J.M. -

Locating Domination in Bipartite Graphs and Their Complements
Locating domination in bipartite graphs and their complements C. Hernando∗ M. Moray I. M. Pelayoz Abstract A set S of vertices of a graph G is distinguishing if the sets of neighbors in S for every pair of vertices not in S are distinct. A locating-dominating set of G is a dominating distinguishing set. The location-domination number of G, λ(G), is the minimum cardinality of a locating-dominating set. In this work we study relationships between λ(G) and λ(G) for bipartite graphs. The main result is the characterization of all connected bipartite graphs G satisfying λ(G) = λ(G) + 1. To this aim, we define an edge-labeled graph GS associated with a distinguishing set S that turns out to be very helpful. Keywords: domination; location; distinguishing set; locating domination; complement graph; bipartite graph. AMS subject classification: 05C12, 05C35, 05C69. ∗Departament de Matem`atiques. Universitat Polit`ecnica de Catalunya, Barcelona, Spain, car- [email protected]. Partially supported by projects Gen. Cat. DGR 2017SGR1336 and MTM2015- arXiv:1711.01951v2 [math.CO] 18 Jul 2018 63791-R (MINECO/FEDER). yDepartament de Matem`atiques. Universitat Polit`ecnica de Catalunya, Barcelona, Spain, [email protected]. Partially supported by projects Gen. Cat. DGR 2017SGR1336, MTM2015-63791-R (MINECO/FEDER) and H2020-MSCA-RISE project 734922 - CONNECT. zDepartament de Matem`atiques. Universitat Polit`ecnica de Catalunya, Barcelona, Spain, ig- [email protected]. Partially supported by projects MINECO MTM2014-60127-P, igna- [email protected]. This project has received funding from the European Union's Horizon 2020 research and innovation programme under the Marie Sk lodowska-Curie grant agreement No 734922. -
![Switching 3-Edge-Colorings of Cubic Graphs Arxiv:2105.01363V1 [Math.CO] 4 May 2021](https://docslib.b-cdn.net/cover/2477/switching-3-edge-colorings-of-cubic-graphs-arxiv-2105-01363v1-math-co-4-may-2021-752477.webp)
Switching 3-Edge-Colorings of Cubic Graphs Arxiv:2105.01363V1 [Math.CO] 4 May 2021
Switching 3-Edge-Colorings of Cubic Graphs Jan Goedgebeur Department of Computer Science KU Leuven campus Kulak 8500 Kortrijk, Belgium and Department of Applied Mathematics, Computer Science and Statistics Ghent University 9000 Ghent, Belgium [email protected] Patric R. J. Osterg˚ard¨ Department of Communications and Networking Aalto University School of Electrical Engineering P.O. Box 15400, 00076 Aalto, Finland [email protected] In loving memory of Johan Robaey Abstract The chromatic index of a cubic graph is either 3 or 4. Edge- Kempe switching, which can be used to transform edge-colorings, is here considered for 3-edge-colorings of cubic graphs. Computational results for edge-Kempe switching of cubic graphs up to order 30 and bipartite cubic graphs up to order 36 are tabulated. Families of cubic graphs of orders 4n + 2 and 4n + 4 with 2n edge-Kempe equivalence classes are presented; it is conjectured that there are no cubic graphs arXiv:2105.01363v1 [math.CO] 4 May 2021 with more edge-Kempe equivalence classes. New families of nonplanar bipartite cubic graphs with exactly one edge-Kempe equivalence class are also obtained. Edge-Kempe switching is further connected to cycle switching of Steiner triple systems, for which an improvement of the established classification algorithm is presented. Keywords: chromatic index, cubic graph, edge-coloring, edge-Kempe switch- ing, one-factorization, Steiner triple system. 1 1 Introduction We consider simple finite undirected graphs without loops. For such a graph G = (V; E), the number of vertices jV j is the order of G and the number of edges jEj is the size of G. -

Bounded Treewidth
Algorithms for Graphs of (Locally) Bounded Treewidth by MohammadTaghi Hajiaghayi A thesis presented to the University of Waterloo in ful¯llment of the thesis requirement for the degree of Master of Mathematics in Computer Science Waterloo, Ontario, September 2001 c MohammadTaghi Hajiaghayi, 2001 ° I hereby declare that I am the sole author of this thesis. I authorize the University of Waterloo to lend this thesis to other institutions or individuals for the purpose of scholarly research. MohammadTaghi Hajiaghayi I further authorize the University of Waterloo to reproduce this thesis by photocopying or other means, in total or in part, at the request of other institutions or individuals for the purpose of scholarly research. MohammadTaghi Hajiaghayi ii The University of Waterloo requires the signatures of all persons using or photocopying this thesis. Please sign below, and give address and date. iii Abstract Many real-life problems can be modeled by graph-theoretic problems. These graph problems are usually NP-hard and hence there is no e±cient algorithm for solving them, unless P= NP. One way to overcome this hardness is to solve the problems when restricted to special graphs. Trees are one kind of graph for which several NP-complete problems can be solved in polynomial time. Graphs of bounded treewidth, which generalize trees, show good algorithmic properties similar to those of trees. Using ideas developed for tree algorithms, Arnborg and Proskurowski introduced a general dynamic programming approach which solves many problems such as dominating set, vertex cover and independent set. Others used this approach to solve other NP-hard problems. -

Snarks and Flow-Critical Graphs 1
Snarks and Flow-Critical Graphs 1 CˆandidaNunes da Silva a Lissa Pesci a Cl´audioL. Lucchesi b a DComp – CCTS – ufscar – Sorocaba, sp, Brazil b Faculty of Computing – facom-ufms – Campo Grande, ms, Brazil Abstract It is well-known that a 2-edge-connected cubic graph has a 3-edge-colouring if and only if it has a 4-flow. Snarks are usually regarded to be, in some sense, the minimal cubic graphs without a 3-edge-colouring. We defined the notion of 4-flow-critical graphs as an alternative concept towards minimal graphs. It turns out that every snark has a 4-flow-critical snark as a minor. We verify, surprisingly, that less than 5% of the snarks with up to 28 vertices are 4-flow-critical. On the other hand, there are infinitely many 4-flow-critical snarks, as every flower-snark is 4-flow-critical. These observations give some insight into a new research approach regarding Tutte’s Flow Conjectures. Keywords: nowhere-zero k-flows, Tutte’s Flow Conjectures, 3-edge-colouring, flow-critical graphs. 1 Nowhere-Zero Flows Let k > 1 be an integer, let G be a graph, let D be an orientation of G and let ϕ be a weight function that associates to each edge of G a positive integer in the set {1, 2, . , k − 1}. The pair (D, ϕ) is a (nowhere-zero) k-flow of G 1 Support by fapesp, capes and cnpq if every vertex v of G is balanced, i. e., the sum of the weights of all edges leaving v equals the sum of the weights of all edges entering v. -

Dominating Cliques in Graphs
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Elsevier - Publisher Connector Discrete Mathematics 86 (1990) 101-116 101 North-Holland DOMINATING CLIQUES IN GRAPHS Margaret B. COZZENS Mathematics Department, Northeastern University, Boston, MA 02115, USA Laura L. KELLEHER Massachusetts Maritime Academy, USA Received 2 December 1988 A set of vertices is a dominating set in a graph if every vertex not in the dominating set is adjacent to one or more vertices in the dominating set. A dominating clique is a dominating set that induces a complete subgraph. Forbidden subgraph conditions sufficient to imply the existence of a dominating clique are given. For certain classes of graphs, a polynomial algorithm is given for finding a dominating clique. A forbidden subgraph characterization is given for a class of graphs that have a connected dominating set of size three. Introduction A set of vertices in a simple, undirected graph is a dominating set if every vertex in the graph which is not in the dominating set is adjacent to one or more vertices in the dominating set. The domination number of a graph G is the minimum number of vertices in a dominating set. Several types of dominating sets have been investigated, including independent dominating sets, total dominating sets, and connected dominating sets, each of which has a corresponding domination number. Dominating sets have applications in a variety of fields, including communication theory and political science. For more background on dominating sets see [3, 5, 151 and other articles in this issue. For arbitrary graphs, the problem of finding the size of a minimum dominating set in the graph is an NP-complete problem [9]. -

The Bidimensionality Theory and Its Algorithmic
The Bidimensionality Theory and Its Algorithmic Applications by MohammadTaghi Hajiaghayi B.S., Sharif University of Technology, 2000 M.S., University of Waterloo, 2001 Submitted to the Department of Mathematics in partial ful¯llment of the requirements for the degree of DOCTOR OF PHILOSOPHY at the MASSACHUSETTS INSTITUTE OF TECHNOLOGY June 2005 °c MohammadTaghi Hajiaghayi, 2005. All rights reserved. The author hereby grants to MIT permission to reproduce and distribute publicly paper and electronic copies of this thesis document in whole or in part. Author.............................................................. Department of Mathematics April 29, 2005 Certi¯ed by. Erik D. Demaine Associate Professor of Electrical Engineering and Computer Science Thesis Supervisor Accepted by . Rodolfo Ruben Rosales Chairman, Applied Mathematics Committee Accepted by . Pavel I. Etingof Chairman, Department Committee on Graduate Students 2 The Bidimensionality Theory and Its Algorithmic Applications by MohammadTaghi Hajiaghayi Submitted to the Department of Mathematics on April 29, 2005, in partial ful¯llment of the requirements for the degree of DOCTOR OF PHILOSOPHY Abstract Our newly developing theory of bidimensional graph problems provides general techniques for designing e±cient ¯xed-parameter algorithms and approximation algorithms for NP- hard graph problems in broad classes of graphs. This theory applies to graph problems that are bidimensional in the sense that (1) the solution value for the k £ k grid graph (and similar graphs) grows with k, typically as (k2), and (2) the solution value goes down when contracting edges and optionally when deleting edges. Examples of such problems include feedback vertex set, vertex cover, minimum maximal matching, face cover, a series of vertex- removal parameters, dominating set, edge dominating set, r-dominating set, connected dominating set, connected edge dominating set, connected r-dominating set, and unweighted TSP tour (a walk in the graph visiting all vertices). -
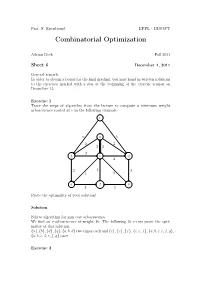
Combinatorial Optimization
Prof. F. Eisenbrand EPFL - DISOPT Combinatorial Optimization Adrian Bock Fall 2011 Sheet 6 December 1, 2011 General remark: In order to obtain a bonus for the final grading, you may hand in written solutions to the exercises marked with a star at the beginning of the exercise session on December 13. Exercise 1 Trace the steps of algorithm from the lecture to compute a minimum weight arborescence rooted at r in the following example. r 6 a 5 2 2 2 2 2 b c d 4 2 1 3 1 2 e f g 1 3 Prove the optimality of your solution! Solution Follow algorithm for min cost arborescence. We find an r-arborescence of weight 16. The following 16 r-cuts prove the opti- mality of this solution: {a}, {b}, {d}, {g}, {a, b, d} two times each and {c}, {e}, {f}, {c, e, f}, {a,b,c,e,f,g}, {a,b,c,d,e,f,g} once. Exercise 2 Let G = (A ∪ B, E) be a bipartite graph. We define two partition matroids M1 =(E, I1) and M2 =(E, I2) with I1 = {I ⊆ E : |I ∩ δ(a)| ≤ 1 for all a ∈ A} and I2 = {I ⊆ E : |I ∩ δ(b)| ≤ 1 for all b ∈ B}. What is a set I ∈ I1 ∩ I2 in terms of graph theory? Can you maximize a weight function w : E → R over the intersection? Remark: This is a special case of the optimization over the intersection of two matroids. It can be shown that all such matroid intersection problems can be solved efficiently.