Introducing Microsoft® Windows Vista™
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

When Using the Wireless Function with a Windows Vista Computer 3. Computer Network Settings 1. Projector Settings 2. Computer IP
2. Computer IP address settings When using the wireless function with a Windows Vista computer 1 Select [Start] → [Network]. “Wireless Manager mobile edition 3.0”, which is stored on the CD-ROM that is provided, does not work when using the wireless function with a Windows Vista computer. “Wireless Manager mobile edition 3.0a” is a version that is compatible with Windows Vista. Use this version by downloading and installing it from the URL below. However, please be aware it will still not be possible to use the functions described below. URL: http://panasonic.co.jp/pavc/global/projector/download/ 2 Select [Network and Sharing Center]. Functions that cannot be used: • Easy wireless set up (automatic set up of the wireless network) • Sound transmission • Wireless prompter (secondary display transmission) • Selective area transmission • Check with your system administrator before performing the network settings with the procedures below. Select [Manage network connections]. If network settings have already been made for using the computer in a wireless 3 environment for a different purpose, and after changing the settings as described in these instructions you want to go back to using the computer for the original purpose, then remember to return the network settings to their previous condition. • See “Wireless Function Edition”, the Operating Instructions in the provided CD-ROM, for details on the projector network settings and the wireless function. 1. Projector settings 4 Right click the mouse and open the Select [MENU] → [WIRELESS] → [NETWORK], and change to [USER1]. Wireless Network Connection Properties. Default settings of USER1 DHCP OFF IP ADDRESS 192.168.10.100 SUBNETMASK 255.255.255.0 SSID Panasonic Projector MODE ADHOC Enter [TCP/IPv4] as the setting and press 5 [OK]. -

Windows 7 Operating Guide
Welcome to Windows 7 1 1 You told us what you wanted. We listened. This Windows® 7 Product Guide highlights the new and improved features that will help deliver the one thing you said you wanted the most: Your PC, simplified. 3 3 Contents INTRODUCTION TO WINDOWS 7 6 DESIGNING WINDOWS 7 8 Market Trends that Inspired Windows 7 9 WINDOWS 7 EDITIONS 10 Windows 7 Starter 11 Windows 7 Home Basic 11 Windows 7 Home Premium 12 Windows 7 Professional 12 Windows 7 Enterprise / Windows 7 Ultimate 13 Windows Anytime Upgrade 14 Microsoft Desktop Optimization Pack 14 Windows 7 Editions Comparison 15 GETTING STARTED WITH WINDOWS 7 16 Upgrading a PC to Windows 7 16 WHAT’S NEW IN WINDOWS 7 20 Top Features for You 20 Top Features for IT Professionals 22 Application and Device Compatibility 23 WINDOWS 7 FOR YOU 24 WINDOWS 7 FOR YOU: SIMPLIFIES EVERYDAY TASKS 28 Simple to Navigate 28 Easier to Find Things 35 Easy to Browse the Web 38 Easy to Connect PCs and Manage Devices 41 Easy to Communicate and Share 47 WINDOWS 7 FOR YOU: WORKS THE WAY YOU WANT 50 Speed, Reliability, and Responsiveness 50 More Secure 55 Compatible with You 62 Better Troubleshooting and Problem Solving 66 WINDOWS 7 FOR YOU: MAKES NEW THINGS POSSIBLE 70 Media the Way You Want It 70 Work Anywhere 81 New Ways to Engage 84 INTRODUCTION TO WINDOWS 7 6 WINDOWS 7 FOR IT PROFESSIONALS 88 DESIGNING WINDOWS 7 8 WINDOWS 7 FOR IT PROFESSIONALS: Market Trends that Inspired Windows 7 9 MAKE PEOPLE PRODUCTIVE ANYWHERE 92 WINDOWS 7 EDITIONS 10 Remove Barriers to Information 92 Windows 7 Starter 11 Access -
How Do I Download Microsoft Games on My Pc How to Reinstall a Purchased Game from Microsoft Store That Is Not Showing up in Library
how do i download microsoft games on my pc how to reinstall a purchased game from microsoft store that is not showing up in Library. Thanks for your feedback, it helps us improve the site. How satisfied are you with this reply? Thanks for your feedback. First, try signing out of the Microsoft Store. Click your Profile picture at the top right, click your account then sign out. Restart your computer, launch the Microsoft Store app, sign in again, then attempt downloading again. Click the ellipsis in the top right corner of the screen (. ) Click My Library Scroll through the list then click the Cuphead app if its listed there, then click the download button. If doesn't help, let us know and we can explore more options. Other things you can try. Start by running the Windows Store Apps troubleshooter. Open Start > Settings > Update & security > Troubleshoot Scroll down to the bottom Click Windows Store Apps. Click Run the troubleshooter. When complete try opening the Store again. Also check if the Store works in another user account. Press Windows key + R Type: wsreset.exe Hit Enter. Do this a couple times then try launching the Store again. Your Antivirus might be interfering with the Store, try disabling it 'temporarily' to see if it launches. Check Windows Update and install the latest updates. Sometimes Microsoft releases infrastructure fixes for the Store through Windows Update. You can also try resetting the store app using the following instructions: Reinstall the Store: Press Windows key + X Click Windows PowerShell (Admin) At the command prompt, type the following then hit Enter: Get-AppXPackage *WindowsStore* -AllUsers | Foreach. -

No More Excuses: Windows 7 Makes It Easy to Manage Computer Power
• Products that earn the ENERGY STAR® prevent greenhouse gas emissions by meeting strict energy efficiency guidelines set by the U.S. Environmental Protection Agency and the U.S. Department of Energy. www.energy star.gov NO MORE EXCUSES: WINDOWS 7 MAKES IT EASY TO MANAGE COMPUTER POWER CONSUMPTION ORGANIZATION-WIDE Here’s how you can take advantage of Windows 7’s new power management features The University of Wisconsin at Oshkosh is no stranger to the idea of sustainability. In 2003 it became the first university in the state to join the Environmental Protection Agency’s Green Power Partnership. Its green initiatives also earned the university high marks from the Sierra Club, which ranked the university nationally in its Cool Schools survey. Given this commitment to green, it’s no surprise that the university first deployed computer power management back in 2005, and that it was one of the first Energy Star power management success stories. At that time, the University’s computers ran the Windows XP and Windows 2000 operating systems, neither of which included native tools for the central administration of power management features. To implement power management settings on these machines, the University used third-party software from ENERGY STAR called EZ GPO. For detailed information and resources concerning Now that Windows 7 has CPM client management features built in, it’s much the power management of easier to administer power management. This case study will show you how the University of Wisconsin at Oshkosh took full advantage of computer power PCs running Windows XP, management features on Windows Vista and Windows 7 clients managed by please see the ENERGY STAR Windows Server 2008. -
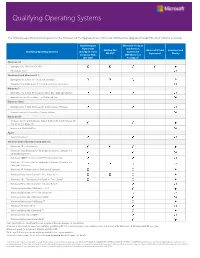
Qualifying Operating Systems
Qualifying Operating Systems The following operating systems qualify for the Windows 10 Pro Upgrade and/or Windows 10 Enterprise Upgrade through Microsoft Volume Licensing. New Enterprise Microsoft Products Agreement and Services Existing EA/ Microsoft Cloud Academic and Qualifying Operating Systems (EA)/Open Value Agreement OV-CW2 Agreement Charity Company-Wide (MPSA)/Select (OV-CW)1 Plus/Open3 Windows 10 4 Enterprise (N, KN) , Pro (N, KN) Education, Home Windows 8 and Windows 8.1 Enterprise (N, K, KN), Pro (N, K, KN, diskless) Windows 8 and Windows 8.1 (including Single Language) Windows 7 Enterprise (N, K, KN), Professional (N, K, KN, diskless), Ultimate Home Premium, Home Basic, or Starter Edition Windows Vista Enterprise (N, K, KN), Business (N, K, KN, Blade), Ultimate Home Premium, Home Basic, Starter Edition Windows XP Professional (N, K, KN, Blade), Tablet Edition (N, K, KN, Blade), XP Pro N, XP Pro Blade PC Home and Starter Edition Apple Apple Macintosh Windows Embedded Operating Systems Windows 10 IoT Enterprise Windows Vista Business for Embedded Systems, Ultimate for Embedded Systems Windows 2000 Professional for Embedded Systems Windows 7 Professional for Embedded Systems, Ultimate for Embedded Systems Windows XP Professional for Embedded Systems Windows Embedded 8 and 8.1 Pro, Industry Pro Windows 10 IoT Enterprise for Retail or Thin Clients5 5 Windows Embedded 8 and 8.1 Industry Retail Windows Embedded POSReady 7 Pro5 5 Windows Embedded for Point of Service Windows Embedded POSReady 20095 5 Windows Embedded POSReady 7 5 Windows XP Embedded Windows Embedded Standard 75 5 Windows Embedded 2009 5 Windows Embedded 8 Standard 1Also applicable to Qualified Devices acquired through merger or acquisition. -

Download Torrent 32 Bit Windows 7 Download Torrent 32 Bit Windows 7
download torrent 32 bit windows 7 Download torrent 32 bit windows 7. Download Tixati v2.84 for 32-Bit Windows. Windows XP Windows Vista Windows 7 Windows 8 Windows 10 Windows Server 2003 Windows Server 2008 Windows Server 2012. First Time Users Remember, you can press F1 any time for context-sensitive help. We also have a Finding Content Guide for those who are new to torrents in general, and an Optimizing Tixati Guide for those who want to squeeze every last drop of speed out of their internet connection. Your Suggestions And Bug-Reports Are Welcome Feel free to visit forum.tixati.com and let us know what you think. Registration is not required and posting a comment is fast and simple. We consider all suggestions and your opinion counts! Our NO Spyware, NO Adware, NO Nonsense Guarantee Unlike many other torrent clients, we take pride in saying NO to spyware and adware. Tixati installs and uninstalls cleanly and doesn't add anything extra to your system. Our software is fully self-contained and doesn't have annoying dependencies on Java or .Net frameworks. Download torrent 32 bit windows 7. Source: Windows 10 Pro v1803 RS4 3in1 Fr x64 (13 Juin 2018).iso (Fais par ace N kelly ) Build: v1803 build 17134.112 Compression: ESD Langue: Français MD5: 823C3F936E7AC20A722C9CE67F4E0D34 SHA-1: 1539A155124D691743C74CFB983B272CB3264092. Fonctions de Bases Supprimés et "Tweaks" : Supprimés : Windows Defender Cortana Microsoft Edge Internet Explorer (Réinstallable via "Programmes et Fonctionnalités") Tweaks : Desktop - Icône du poste de travail visible -

Windows 10 Download for Windows Vista Windows 10 Download for Windows Vista
windows 10 download for windows vista Windows 10 download for windows vista. Dummies has always stood for taking on complex concepts and making them easy to understand. Dummies helps everyone be more knowledgeable and confident in applying what they know. Whether it’s to pass that big test, qualify for that big promotion or even master that cooking technique; people who rely on dummies, rely on it to learn the critical skills and relevant information necessary for success. Learning Made Easy. Copyright © 2021 & Trademark by John Wiley & Sons, Inc. All rights reserved. Upgrade from Windows Vista to Windows 10 or 8.1? If you pay for 7 and then try for a free upgrade to 10 you may not get it as that offer expired in 2016. And 10 is cheaper than 7 to buy. But check everything first:: It depends on the hardware requirements of later operating systems and also whether the computer/laptop manufacturer supports and supplies drivers for the later operating systems as to whether it is possible or feasible to upgrade or not. There is no free upgrade from Vista to 7, 8.1 or 10. Follow these steps before you buy Windows 7; extended support Windows 7 SP1 until January 14, 2020 . Microsoft no longer sells 7; try amazon.com. Go to your Computer / Laptop Manufacturer's website and see if Windows 7 Drivers are available for your Make and Model Computer / Laptop. If not available, Windows 7 will not work correctly for you. Run the "Windows 7 Upgrade Advisor" Check to see if your System Specifications are compatible for Windows 7: "Windows 7 system requirements" Windows 7 Upgrade paths: Follow these steps before you buy and Upgrade (clean install) to Windows 8.1; extended support ends January 10, 2023 . -

Windows Tool Reference
AppendixChapter A1 Windows Tool Reference Windows Management Tools This appendix lists sets of Windows management, maintenance, configuration, and monitor- ing tools that you may not be familiar with. Some are not automatically installed by Windows Setup but instead are hidden away in obscure folders on your Windows Setup DVD or CD- ROM. Others must be downloaded or purchased from Microsoft. They can be a great help in using, updating, and managing Windows. We’ll discuss the following tool kits: ■ Standard Tools—Our pick of handy programs installed by Windows Setup that we think are unappreciated and not well-enough known. ■ Support Tools—A set of useful command-line and GUI programs that can be installed from your Windows Setup DVD or CD-ROM. ■ Value-Added Tools—Several more sets of utilities hidden away on the Windows Setup CD-ROM. ■ Windows Ultimate Extras and PowerToys for XP—Accessories that can be downloaded for free from microsoft.com. The PowerToys include TweakUI, a program that lets you make adjustments to more Windows settings than you knew existed. ■ Resource Kits—A set of books published by Microsoft for some versions of Windows that includes a CD-ROM containing hundreds of utility programs. What you may not have known is that in some cases you can download the Resource Kit program toolkits with- out purchasing the books. ■ Subsystem for UNIX-Based Applications (SUA)—A package of network services and command-line tools that provide a nearly complete UNIX environment. It can be installed only on Windows Vista Ultimate and Enterprise, and Windows Server 2003. -

Access Point (AP), 364, 366 Security For, 365 Accessories
Z00WINV.qxd 1/8/2007 10:06 AM Page 529 Index A security settings, monitoring, 494-495 System Configuration tool, 500 access point (AP), 364, 366 system information, viewing, 499 security for, 365 viewing, 486 accessories, 25 Adobe's Type 1 PostScript font, 115 working with, 29 Advanced Research Projects Agency accounts Network (ARPANET), 133 for Live Messenger, 208 advanced searches. See searching Mail account, setting up, 168-169 advertising banners, 333 Active Search Directory, 350 adware, 331, 344 ActiveX controls, 333 Information Bar and, 343 Information Bar and, 343 Aero, 2 Mail security zones and, 345 introduction to, 6-7 activation, Windows Vista, 5 live thumbnails, 6 Add Hardware Wizard, 450, 452 preparing for, 7 Add-on Manager, 344 running, 7 add-ons AIF files, 289 Internet Explorer without, 138 Airbrush tool, 236 security, managing, 344 alerts. See also Defender; Security Center Add Printer Wizard, 400-401 Internet Explorer as default, turning Add Search Providers option, 155 on/off alert for, 164 adding/removing. See also deleting with Live Messenger, 232 components, 437 printer alerts, 407 indexed locations, 78 Align to Grid option, 82 programs from Startup menu, 28 alignment of document text, 34 recently used documents, 31 All Programs submenu, 26 Address bar, 116 command, 13 browsing folders and programs from, Internet Explorer, finding, 138 141 allocation units, 426 in Explorer windows, 54 antivirus software, 310, 322, 330-331 folders, navigating between, 62 Apple/Microsoft's TrueType font, 115 in Internet Explorer, 139 applications. See programs Web searches with, 154 Applications and Services Logs, 487 Address Book security, 345 appointments. -

COPYRIGHTED Materialtasks B Changing Color, 319, 321 Backing Up
35_045770 bindex.qxp 1/29/07 8:21 PM Page 554 A BOOT.INI files, editing, 39 brightness settings, 246, 248, 351 accessibility features, 78–79 broadband connections. See networks Active Directory, 5, 359, 438 Browse dialog box, 153 ActiveX controls, 183 browsers, Web, 382, 426. See also Internet Explorer 7 Administrative Tools, 172–173 Administrator accounts, 106, 107 adware, 128, 166–7. See also spyware Aero interface, 66, 67 C Always Available Offline option, 506–507 cable modems, 360, 361, 362 Appearance Settings dialog box, 86, 88–89, 494–495 Calendar Application Compatibility Toolkit, 49 appointments applications. See also Windows Vista configuration deleting, 317 applets, 519 e-mailing invitations, 324–325 ending non-responsive, 459 editing details, 320–321 hibernation mode and, 501 moving, 317 launching, 65, 80–81 receiving invitations, 326–327 minimizing open, 71, 99 recurring, 320, 322–323 removing unused, 509, 519 reminders, 319, 321 restricting access to, 136–137 setting up, 316–317 slowing down, 49 creating calendars, 327 switching between open, 64–67 as default program, 325, 327 transferring, 16, 19 defined, 316 Vista upgrades and, 33 setting options, 318–319 appointments. See Calendar shared calendars aspect ratio settings, 246, 248 publishing, 330–331 audio. See Media Player; Media Center; CDs Automated Installation Kit, Windows (WAIK), 23 subscribing to, 332–333 Avast AntiVirus software, 170–171 troubleshooting, 331 AVI (Audio Video Interleaved) format, 225 unpublishing, 333 updating, 333 COPYRIGHTED MATERIALtasks B changing color, 319, 321 backing up. See system management creating, 328–329 bandwidth, 363 hiding completed, 319 BitLocker Drive Encryption, 4 reminders, 329 blocking errors, 10 turning off panes, 329 blogs, 315, 383 cameras, digital, 214–217 boot managers, 479 cards. -

Standard Vorlage
SIE MACHEN IHREN JOB. WIR MACHEN IHRE IT. Vom CLPA-Agent unterstützte „Non Microsoft“ Applikationen: Vendor Product ActiveState Software Inc. ActivePython AOE media FileZilla Client Apache OpenOffice OpenOffice.org Apache Group Apache Web Server ** Apple Incorporated Apple QuickTime Apple iTunes Apple Safari Adobe Systems Incorporated Adobe Acrobat Adobe Acrobat DC Adobe Acrobat DC-Classic Adobe Air Adobe Flash Player Adobe Illustrator Adobe InDesign Adobe PhotoShop Adobe Reader Adobe Reader DC Adobe Reader DC-Classic Adobe Shockwave Player AudacityTeam.org Audacity Bandisoft.com Bandizip Box BoxSync Bullzip.com COMPUTERS & LESSONS GmbH Geschäftsführer: Stefan Körbel Tel.: 06021 8483-0 Magnolienweg 12 Handelsregister Aschaffenburg HRB 5334 Fax: 06021 8483-19 63741 Aschaffenburg USt-IDNr.: DE 1604 189 65 www.comless.de [email protected] Seite 1 von 12 SIE MACHEN IHREN JOB. WIR MACHEN IHRE IT. Bullzip PDF Printer Canneverbe Limited CDBurnerXP Citrix Systems Inc. GoToMeeting Core FTP Core FTP Don Ho Notepad++ dotPDN LLC Paint.NET Evernote Corporation Evernote Foxit Corporation Foxit PhantomPDF Foxit Reader Fyodor Nmap Google Google Chrome * Google Drive Google Earth Google Picasa ideaMK STP Viewer gor Pavlov 7-Zip Irfan Skiljan IrfanView JAM Software TreeSize Free Lightning UK COMPUTERS & LESSONS GmbH Geschäftsführer: Stefan Körbel Tel.: 06021 8483-0 Magnolienweg 12 Handelsregister Aschaffenburg HRB 5334 Fax: 06021 8483-19 63741 Aschaffenburg USt-IDNr.: DE 1604 189 65 www.comless.de [email protected] Seite 2 von 12 SIE MACHEN IHREN JOB. WIR -

Microsoft Windows: the Launch of Windows 7
S w 909A23 MICROSOFT WINDOWS: THE LAUNCH OF WINDOWS 7 Matthew Ball wrote this case under the supervision of Professor Miranda Goode solely to provide material for class discussion. The authors do not intend to illustrate either effective or ineffective handling of a managerial situation. The authors may have disguised certain names and other identifying information to protect confidentiality. Ivey Management Services prohibits any form of reproduction, storage or transmittal without its written permission. Reproduction of this material is not covered under authorization by any reproduction rights organization. To order copies or request permission to reproduce materials, contact Ivey Publishing, Ivey Management Services, c/o Richard Ivey School of Business, The University of Western Ontario, London, Ontario, Canada, N6A 3K7; phone (519) 661-3208; fax (519) 661-3882; e-mail [email protected]. Copyright © 2009, Ivey Management Services Version: (A) 2009-08-13 INTRODUCTION It was the spring of 2009, and Steve Ballmer, chief executive officer of Microsoft Corporation, was planning the launch of Windows 7, the company’s newest operating system. Successfully marketing Windows 7 had become essential for the company, which had faced numerous challenges in recent years. The company’s image had been tarnished by the commercial and public relations failure of its last operating system, Windows Vista. Moreover, the company became the target of a brutal series of advertisements by its largest competitor, Apple Inc., and was continuing to bleed market share. Beta releases had been well received by the Internet community, and Microsoft hoped that Windows 7 would not only improve its bottom line, but also restore its tarnished image.