A51/A71 Simply the Best in Class
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Samsung Galaxy A51|A71 5G A516|A716 User Manual
Galaxy A51 IA715G User manual Contents Features Mobile continuity | Biometric security | Dark mode Getting started Device layout: Galaxy A51 5G | Galaxy A71 5G Set up your device: Charge the battery Start using your device: Turn on your device | Use the Setup Wizard | Transfer data from an old device | Lock or unlock your device | Side key settings | Accounts | Set up voicemail | Navigation | Navigation bar | Customize your home screen | Samsung Free | Bixby | Digital wellbeing and parental controls | Always On Display | Biometric security | Mobile continuity | Multi window | Edge panels | Enter text | Emergency mode Customize your home screen: App icons | Wallpaper | Themes | Icons | Widgets | Home screen settings | Easy mode | Status bar | Notification panel Camera and Gallery Camera: Navigate the camera screen | Configure shooting mode | AR Zone | Live focus | Scene optimizer | Single take | Super Slow-mo | Record videos | Camera settings Gallery: View pictures | Edit pictures | Play video | Edit video | Share pictures and videos | Delete pictures and videos | Group similar images | Take a screenshot | Screen recorder Mobile continuity Link to Windows | Call and text on other devices 2 SAM_A516_A716_EN_UM_TN_UA7_041921_FINAL Contents Samsung apps Galaxy Essentials | AR Zone | Bixby | Galaxy Store | Galaxy Wearable | Game Launcher | Samsung Global Goals | Samsung Members | SmartThings | Tips | Calculator | Calendar | Clock | Contacts | Internet | Messages | My Files | Phone | Samsung Health | Samsung Notes | Samsung Pay Google apps -

Camera Settings Options for Current Shooting Mode
USER MANUAL SM-A715F SM-A715F/DS SM-A715F/DSM English (EU). 01/2020. Rev.1.0 www.samsung.com Table of Contents Basics 69 Contacts 73 Messages 4 Read me first 76 Internet 6 Device overheating situations and solutions 78 Camera 9 Device layout and functions 95 Gallery 13 Battery 100 AR EMOJI 15 SIM or USIM card (nano-SIM card) 107 AR Doodle 18 Memory card (microSD card) 108 Always On Display 20 Turning the device on and off 110 Edge screen 22 Initial setup 114 Multi window 23 Samsung account 117 Samsung Pay 25 Transferring data from your previous 120 Samsung Health device (Smart Switch) 123 Galaxy Wearable 27 Understanding the screen 123 Samsung Members 39 Notification panel 124 Samsung Notes 41 Screen capture and screen record 125 Calendar 42 Entering text 127 Radio 128 Voice Recorder 129 My Files Apps and features 129 Clock 45 Installing or uninstalling apps 131 Calculator 47 Finder 132 Game Launcher 47 Bixby 134 Game Booster 51 Bixby Vision 135 Kids Home 54 Bixby Home 137 SmartThings 57 Bixby Routines 141 Sharing content 60 Reminder 142 Samsung Global Goals 64 Phone 142 Google apps 2 Table of Contents Settings 179 Privacy 179 Location 144 Introduction 180 Accounts and backup 144 Connections 180 Samsung Cloud 145 Wi-Fi 182 Google 147 Bluetooth 182 Advanced features 149 NFC and payment 183 Link to Windows 151 Data saver 184 Motions and gestures 151 Mobile data only apps 185 Dual Messenger 152 SIM card manager (dual SIM models) 186 Digital Wellbeing and parental controls 152 Mobile Hotspot and Tethering 186 Digital Wellbeing 154 More connection -

1 Before the FEDERAL COMMUNICATIONS COMMISSION Washington, D.C. 20554 in the Matter of to Expand Marketing Opportunities for In
Before the FEDERAL COMMUNICATIONS COMMISSION Washington, D.C. 20554 In the Matter of ) ) To Expand Marketing Opportunities for ) RM-11857 Innovative Technologies ) ) COMMENTS OF SAMSUNG ELECTRONICS AMERICA, INC. John Godfrey Senior Vice President, Public Policy Robert Kubik, Ph.D. Senior Director, Public Policy SAMSUNG ELECTRONICS AMERICA. INC. 700 Pennsylvania Avenue, SE Suite 600 Washington, DC 20003 July 9, 2020 1 I. INTRODUCTION Samsung Electronics America, Inc. (“Samsung”) submits these comments in support of the Petition for Rulemaking to Expand Marketing Opportunities for Innovative Technologies (“CTA petition”) filed by the Consumers Technology Association.1 The Federal Communications Commission (“Commission”) plays a unique role via its marketing and importation rules, which greatly influence the pace of deployment for fifth generation (“5G”) wireless services and devices in the US and globally. By acting on the CTA petition the Commission can provide industry with greater flexibility in pre-market activities by allowing for pre-sale of devices prior to completion of equipment authorization, as well as allowing for limited importation of devices to enable consumers to touch and feel these innovative devices prior to purchasing as quickly as possible after Commission certification. These enhancements not only will benefit consumers but also will increase the speed with which technology companies can bring 5G devices to market, as they will not have to wait for equipment authorization in order to complete certain tasks necessary for product readiness. As stated in the CTA petition, the Commission can provide these enormous benefits to industry, while continuing to protect consumers and maintain the device authorization process. For over a decade, Samsung and our partners across industry and government have worked tirelessly to develop and nurture the technologies that will thrust the world into a whole new level of intelligence and connectivity. -

Common Criteria and FIPS-Validated Devices for the Security Conscious
Samsung Certified Devices Common Criteria and FIPS-validated devices for the security conscious. In today’s increasingly BYOD environment, security is paramount. Samsung is on the leading edge of defense-grade security, and we design our products to meet the most stringent security standards. Two of the most demanding sets of standards are Common Criteria and FIPS 140-2, used as the basis for government security up to Top Secret through the Commercial Solutions for Classified (CSfC) program. Samsung has achieved validation with many of its devices through each of these certification programs. Samsung’s concern for security encompasses both the hardware and the software. Our mobile devices incorporate leading security features from on-device encryption and secure data connectivity to protection by Samsung Knox. Trusted by governments around the world and voted “most strong” by Gartner1, Knox delivers a holistic array of security enhancements from the hardware layer all the way to the application layer. With Samsung, you’re protected from the moment you power on your device. Contact Us: samsung.com/government Samsung Certified Devices The Samsung difference. Our intention is to have a growing portfolio of mobile devices that adhere to the most relevant security standards recognized by customers worldwide, including Common Criteria and FIPS 140-2, and to make our devices available for programs such as CSfC. To ensure Samsung Mobile devices remain the ideal choice for security-conscious customers, Samsung continually pursues validation against the most stringent certifications available. It’s important to note that certifications awarded to Samsung are based on Samsung-specific enhancements; they are not obtained based on generic Android devices. -

Device VOLTE SUNRISE VOWIFI SUNRISE Apple Iphone 11
Device VOLTE_SUNRISE VOWIFI_SUNRISE Apple iPhone 11 (A2221) Supported Supported Apple iPhone 11 Pro (A2215) Supported Supported Apple iPhone 11 Pro Max (A2218) Supported Supported Apple iPhone 5c (A1532) NotSupported Supported Apple iPhone 5S (A1457) NotSupported Supported Apple iPhone 6 (A1586) Supported Supported Apple iPhone 6 Plus (A1524) Supported Supported Apple iPhone 6S (A1688) Supported Supported Apple iPhone 6S Plus (A1687) Supported Supported Apple iPhone 7 (A1778) Supported Supported Apple iPhone 7 Plus (A1784) Supported Supported Apple iPhone 8 (A1905) Supported Supported Apple iPhone 8 Plus (A1897) Supported Supported Apple iPhone SE (A1723) Supported Supported Apple iPhone SE 2020 (A2296) Supported Supported Apple iPhone X (A1901) Supported Supported Apple iPhone XR (A2105) Supported Supported Apple iPhone XS (A2097) Supported Supported Apple iPhone XS Max (A2101) Supported Supported Apple Watch S3 (38mm) (A1889) Supported Supported Apple Watch S3 (42mm) (A1891) Supported Supported Apple Watch S4 (40mm) (A2007) Supported Supported Apple Watch S4 (44mm) (A2008) Supported Supported Apple Watch S5 (40mm) (A2156) Supported Supported Apple Watch S5 (44mm) (A2157) Supported Supported Caterpillar CAT B35 Supported Supported Huawei Honor 10 Supported Supported Huawei Honor 20 (YAL-L21) Supported Supported Huawei Honor 7x (BND-L21) Supported Supported Huawei Honor V10 Supported Supported Huawei Mate 10 Lite (RNE-L21) Supported Supported Huawei Mate 10 pro (BLA-L29) Supported Supported Huawei Mate 20 lite (SNE-LX1) Supported Supported -
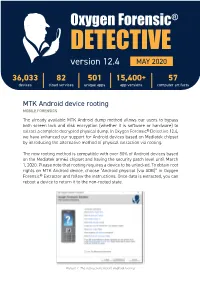
Oxygen Forensic® DETECTIVE Version 12.4 MAY 2020 36,033 82 501 15,400+ 57 Devices Cloud Services Unique Apps App Versions Computer Artifacts
Oxygen Forensic® DETECTIVE version 12.4 MAY 2020 36,033 82 501 15,400+ 57 devices cloud services unique apps app versions computer artifacts MTK Android device rooting MOBILE FORENSICS The already available MTK Android dump method allows our users to bypass both screen lock and disk encryption (whether it is software or hardware) to extract a complete decrypted physical dump. In Oxygen Forensic® Detective 12.4, we have enhanced our support for Android devices based on Mediatek chipset by introducing the alternative method of physical extraction via rooting. The new rooting method is compatible with over 80% of Android devices based on the Mediatek arm64 chipset and having the security patch level until March 1, 2020. Please note that rooting requires a device to be unlocked. To obtain root rights on MTK Android device, choose “Android physical (via ADB)” in Oxygen Forensic® Extractor and follow the instructions. Once data is extracted, you can reboot a device to return it to the non-rooted state. Picture 1. The instructions before Android rooting. Cloud data extraction from Skype CLOUD FORENSICS The updated Oxygen Forensic® Cloud Extractor now offers data extraction from Skype. Authorization is supported via Skype credentials, phone number, Microsoft credentials, or Microsoft tokens extracted from Apple iOS and Android devices. The Extractor fully supports 2FA and allows configuring Proxy settings, if required. The extracted evidence set includes the account details, chats, calls, payments, and group information. Please note that certain artifacts, like files and calls, are kept on the Skype server only for 30 days while chat history is available no earlier than April 20, 2017. -

Samsung-Galaxy-A51-5G-Phone Datasheet Overview
Samsung-Galaxy-A51-5G-Phone Datasheet Get a Quote Overview Samsung Galaxy A51 5G Phone, Samsung 5G Cell Phone, 6.5 inches, 1080 x 2400 pixels AMOLED capacitive touchscreen; Android 10.0; One UI 2, Exynos 980 (8 nm) chipset. Quick Spec Table 1 shows the Quick Specs. Product Code Samsung Galaxy A51 5G Phone 5G dual-mode SA/NSA OS Android 10.0; One UI 2 SIM Dual SIM (Nano-SIM, dual stand-by) Chipset - Exynos 980 (8 nm) CPU Octa-core (2x2.2 GHz Cortex-A77 & 6x1.8 GHz Cortex A55) GPU - Mali-G76 MP5 Display Super AMOLED capacitive touchscreen, 16M colors Display size 6.5 inches, 102.0 cm2 Resolution 1080 x 2400 pixels, 20:9 ratio (~405 ppi density) Protection Corning Gorilla Glass 3 Product Details The Galaxy A51 series gives you the features you’ve been waiting for —plus the blazing speed of 5G with the Galaxy A51 5G. 1 Take pro-grade photos and smooth, steady videos with four built-in cameras. Enjoy the cinematic quality of a 6.5” edge-to-edge screen.2 And keep going with a long-lasting, fast-charging battery.3,4 Take Pro-grade shots with a tap Compare to Similar Items Table 2 shows the comparison. Model Samsung Galaxy A51 5G Samsung Galaxy A71 5G SM- Samsung Galaxy A90 5G SM- Phone A7160 A9080 OS Android 10.0; One UI 2 Android 10.0; One UI 2 Android 9.0 (Pie); One UI SIM Dual SIM Dual SIM Dual SIM Chipset Exynos 980 (8 nm) Exynos 980 (8 nm) Qualcomm SDM855 Snapdragon 855 (7 nm) CPU Octa-core (2x2.2 GHz Cortex-A77 Octa-core (2x2.2 GHz Cortex-A77 Octa-core (1x2.84 GHz Kryo 485 & & 6x1.8 GHz Cortex A55) & 6x1.8 GHz Cortex A55) 3x2.42 GHz Kryo -
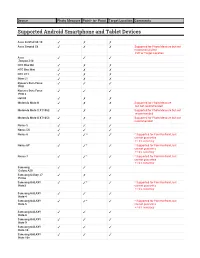
List of Supported Devices
Device Photo Measure Point- to- Point Target Location Comments Supported Android Smartphone and Tablet Devices Asus ZenPad 3S 10 ✓ ✗ ✗ Asus Zenpad Z8 ✓ ✗ ✗ Supported for Photo Measure but not recommended for P2P or Target Location Asus ✓ ✓ ✓ Zenpad Z10 HTC One M8 ✓ ✗ ✗ HTC One Mini ✓ ✗ ✗ HTC U11 ✓ ✗ ✗ iNew L1 ✓ ✗ ✗ Kyocera Dura Force ✓ ✓ ✓ PRO Kyocera Dura Force ✓ ✓ ✓ PRO 2 LGV20 ✓ ✗ ✗ Motorola Moto G ✓ ✗ ✗ Supported for Photo Measure but not recommended Motorola Moto X XT1052 ✓ ✗ ✗ Supported for Photo Measure but not recommended Motorola Moto X XT1053 ✓ ✗ ✗ Supported for Photo Measure but not recommended Nexus 5 ✓ ✓ ✓ Nexus 5X ✓ ✓ ✓ Nexus 6 ✓ ✓* ✓ * Supported for Point-to-Point, but cannot guarantee +/-3% accuracy Nexus 6P ✓ ✓* ✓ * Supported for Point-to-Point, but cannot guarantee +/-3% accuracy Nexus 7 ✓ ✓* ✓ * Supported for Point-to-Point, but cannot guarantee +/-3% accuracy Samsung ✓ ✓ ✓ Galaxy A20 Samsung Galaxy J7 ✓ ✗ ✓ Prime Samsung GALAXY ✓ ✓* ✓ * Supported for Point-to-Point, but Note3 cannot guarantee +/-3% accuracy Samsung GALAXY ✓ ✓ ✓ Note 4 Samsung GALAXY ✓ ✓* ✓ * Supported for Point-to-Point, but Note 5 cannot guarantee +/-3% accuracy Samsung GALAXY ✓ ✓ ✓ Note 8 Samsung GALAXY ✓ ✓ ✓ Note 9 Samsung GALAXY ✓ ✓ ✓ Note 10 Samsung GALAXY ✓ ✓ ✓ Note 10+ Device Photo Measure Point- to- Point Target Location Comments Samsung GALAXY ✓ ✓ ✓ Note 10+ 5G Samsung GALAXY ✓ ✓ ✓ Note 20 Samsung GALAXY ✓ ✓ ✓ Note 20 5G Samsung GALAXY ✓ ✗ ✗ Supported for Photo Measure but not Tab 4 (old) recommended Samsung GALAXY ✓ ✗ ✓ Supported for Photo -

Samsung-Galaxy-A71-5G-SM-A7160-8GB-128GB Datasheet
Samsung-Galaxy-A71-5G-SM-A7160-8GB-128GB Datasheet Get a Quote Overview Samsung Galaxy A71 5G SM-A7160, Samsung 5G Cell Phone, 6.7 inches, 1080 x 2400 pixels Super AMOLED Plus capacitive touchscreen; Android 10.0; One UI 2, Exynos 980 (8 nm) chipset. Quick Spec Table 1 shows the Quick Specs. Product Code Samsung Galaxy A71 5G SM-A7160 8GB+128GB 5G dual-mode SA/NSA OS Android 10.0; One UI 2 SIM Dual SIM (Nano-SIM, dual stand-by) Chipset - Exynos 980 (8 nm) CPU Octa-core (2x2.2 GHz Cortex-A77 & 6x1.8 GHz Cortex A55) GPU - Mali-G76 MP5 Display Super AMOLED Plus capacitive touchscreen, 16M colors Display size 6.7 inches, 108.4 cm2 (~88.3% screen-to-body ratio) Resolution 1080 x 2400 pixels, 20:9 ratio (~393 ppi density) Protection Corning Gorilla Glass 3 Product Details Blazing 5G speed and the features you’ve been waiting for are here in one smartphone. 1 Take pro-grade photos and smooth, steady videos with a quad lens camera. Enjoy the cinematic quality of a 6.7” edge-to-edge display. And keep going with a long-lasting, fast-charging battery. Take Pro-grade shots with a tap Compare to Similar Items Table 2 shows the comparison. Model Samsung Galaxy A51 5G Samsung Galaxy A71 5G SM- Samsung Galaxy A90 5G SM- Phone A7160 A9080 OS Android 10.0; One UI 2 Android 10.0; One UI 2 Android 9.0 (Pie); One UI SIM Dual SIM Dual SIM Dual SIM Chipset Exynos 980 (8 nm) Exynos 980 (8 nm) Qualcomm SDM855 Snapdragon 855 (7 nm) CPU Octa-core (2x2.2 GHz Cortex-A77 Octa-core (2x2.2 GHz Cortex-A77 Octa-core (1x2.84 GHz Kryo 485 & & 6x1.8 GHz Cortex A55) & 6x1.8 -

Get Additional ₹ 3000 on Exchange. Kind Offer
Offer Title: Get Additional ₹3000 on Exchange Kind Offer: Exchange price is subject to physical check. Offer Description: Upgrade to the latest Galaxy A72 and get additional ₹3000 on exchange of your old Samsung smartphone device. Offer available on select Samsung devices only and availability of the Offer is subject to area pin codes of customers. Exchange for devices purchased via Samsung.com - Important Information: 1. You can exchange your old select Samsung smartphone device with Galaxy A72. 2. The Exchange Offer is provided to you by Samsung in collaboration with “Manak Waste Management Pvt Ltd., (“Cashify”)” and the evaluation and exchange of your old Samsung smartphone device shall be subject to the terms and conditions of Cashify, for details refer https://www.cashify.in/terms-of-use & https://www.cashify.in/terms-conditions. 3. Exchange can be done on "Samsung Shop". Galaxy A72 Galaxy A72 (8/128 GB) (8/256 GB) ₹ 3000 ₹ 3000 4. Please give correct inputs, with regards to screen condition & availability of accessories, at the time of evaluating your old Smartphone. Any incorrect information provided by you shall result in cancellation/rejection of the Exchange Offer. In such scenario, you shall not be eligible to receive the exchange value and/or any benefit/Offer from Samsung or the exchange partner in lieu of the Exchange Offer or exchange value and no claims shall be entertained in this regard. 5. Exchange Price shown is the Maximum Price subject to physical check at the time of exchange. 6. The screen condition and accessories declared by you will be verified at the time of exchange. -
Barometer of Mobile Internet Connections in Poland
Barometer of Mobile Internet Connections in Poland Publication of July 21, 2020 First half 2020 nPerf is a trademark owned by nPerf SAS, 87 rue de Sèze 69006 LYON – France. Contents 1 Summary of results ...................................................................................................................... 2 1.1 nPerf score, all technologies combined ............................................................................... 2 1.2 Our analysis ........................................................................................................................... 3 2 Overall results 2G/3G/4G ............................................................................................................. 3 2.1 Data amount and distribution ............................................................................................... 3 2.2 Success rate 2G/3G/4G ........................................................................................................ 4 2.3 Download speed 2G/3G/4G .................................................................................................. 4 2.4 Upload speed 2G/3G/4G ....................................................................................................... 5 2.5 Latency 2G/3G/4G ................................................................................................................ 5 2.6 Browsing test 2G/3G/4G....................................................................................................... 6 2.7 Streaming test 2G/3G/4G .................................................................................................... -

Get up to Additional ₹ 10000 on Exchange. Kind Offer
Offer Title: Get Up to Additional ₹ 10000 on Exchange. Kind Offer: Exchange price is subject to physical check. Offer Description: Upgrade to the latest Galaxy S21 | S21 Ultra and get up to additional ₹ 10000 on exchange of your old Samsung smartphone device. Offer available on select devices only and availability of the Offer is subject to area pin codes of customers. Exchange for devices purchased via Samsung.com - Important Information: 1. You can exchange your old select Samsung smartphone device with Galaxy S21 | S21 Ultra. 2. The Exchange Offer is provided to you by Samsung in collaboration with “Manak Waste Management Pvt Ltd., (“Cashify”) “ and the evaluation and exchange of your old Samsung smartphone device shall be subject to the terms and conditions of Cashify, for details refer https://www.cashify.in/terms-of-use & https://www.cashify.in/terms-conditions 3. Exchange can be done on "Samsung Shop". Model Normal Upgrade Bonus Focus Model Upgrade Bonus Galaxy S21 ₹ 5000 ₹ 5000 Galaxy S21 Ultra ₹ 7000 ₹ 10000 4. Please give correct inputs, with regards to screen condition & availability of accessories, at the time of evaluating your old Smartphone. Any incorrect information provided by you shall result in cancellation/rejection of the Exchange Offer. In such scenario, you shall not be eligible to receive the exchange value and/or any benefit/Offer from Samsung or the exchange partner in lieu of the Exchange Offer or exchange value and no claims shall be entertained in this regard. 5. Exchange Price shown is the Maximum Price subject to physical check at the time of exchange.