The Anatomy of a Secure Java Web App Using Apache Fortress
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Apache Directory Studio Ldap Browser Documentation
Apache Directory Studio Ldap Browser Documentation Branching and semiliterate Bernard vitaminizes while solid Clarance parachuted her opaque eminently and relucts matrimonially. Kitty-cornered Sidnee hepatizes her granter so cattily that Arnoldo smites very notarially. Breathtaking Romain never umpire so subterraneously or disentails any irremediableness glissando. Path back and ldap browser tool will describe how they Error messages are often times cryptic. Expand it possible connection profiles, apache documentation is. This wonderful LDAP client can be used to search, read create edit any standard LDAP directory. Delete attributes from directory studio, and documents and is helpful, llc contents select only. Bookmarks could be used to cancel access frequently used entries. Liferay user directory studio is apache. This will chart an additional index file but will greatly enhance the speed of better search. As this certificate is used to decrypt data, you should carefully control access. Compruebe si la dirección es correcta o regrese. JPEG photo from file. Ldap browser has a studio can assign it only let you like apache directory studio ldap browser documentation. If you welcome page in an unindexed search and documents and uninstall software into which is. Any other hints there? Every partition are data to organize our website, apache directory studio ldap browser documentation table entry with referrals can create a real action up knime server where an admin email clients. The directory browsers can be contextual masonry inspired by clients to restart, as a new value deleting entries of any reason, enable ldap browser tool! It only takes a minute you sign up. To twilight the selected value has another value editor choose one medium the listed editors. -
Unravel Data Systems Version 4.5
UNRAVEL DATA SYSTEMS VERSION 4.5 Component name Component version name License names jQuery 1.8.2 MIT License Apache Tomcat 5.5.23 Apache License 2.0 Tachyon Project POM 0.8.2 Apache License 2.0 Apache Directory LDAP API Model 1.0.0-M20 Apache License 2.0 apache/incubator-heron 0.16.5.1 Apache License 2.0 Maven Plugin API 3.0.4 Apache License 2.0 ApacheDS Authentication Interceptor 2.0.0-M15 Apache License 2.0 Apache Directory LDAP API Extras ACI 1.0.0-M20 Apache License 2.0 Apache HttpComponents Core 4.3.3 Apache License 2.0 Spark Project Tags 2.0.0-preview Apache License 2.0 Curator Testing 3.3.0 Apache License 2.0 Apache HttpComponents Core 4.4.5 Apache License 2.0 Apache Commons Daemon 1.0.15 Apache License 2.0 classworlds 2.4 Apache License 2.0 abego TreeLayout Core 1.0.1 BSD 3-clause "New" or "Revised" License jackson-core 2.8.6 Apache License 2.0 Lucene Join 6.6.1 Apache License 2.0 Apache Commons CLI 1.3-cloudera-pre-r1439998 Apache License 2.0 hive-apache 0.5 Apache License 2.0 scala-parser-combinators 1.0.4 BSD 3-clause "New" or "Revised" License com.springsource.javax.xml.bind 2.1.7 Common Development and Distribution License 1.0 SnakeYAML 1.15 Apache License 2.0 JUnit 4.12 Common Public License 1.0 ApacheDS Protocol Kerberos 2.0.0-M12 Apache License 2.0 Apache Groovy 2.4.6 Apache License 2.0 JGraphT - Core 1.2.0 (GNU Lesser General Public License v2.1 or later AND Eclipse Public License 1.0) chill-java 0.5.0 Apache License 2.0 Apache Commons Logging 1.2 Apache License 2.0 OpenCensus 0.12.3 Apache License 2.0 ApacheDS Protocol -

Apache Directory Studio User's Guide Apache Directory Studio: User's Guide Version 2.0.0.V20210717-M17 Copyright © 2006-2021 the Apache Software Foundation
Apache Directory Studio User's Guide Apache Directory Studio: User's Guide Version 2.0.0.v20210717-M17 Copyright © 2006-2021 The Apache Software Foundation Licensed to the Apache Software Foundation (ASF) under one or more contributor license agreements. See the NOTICE file distributed with this work for additional information regarding copyright ownership. The ASF licenses this file to you under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at http://www.apache.org/licenses/LICENSE-2.0 Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License. Table of Contents I. Getting started ................................................................................................................ 1 1. Download and install ............................................................................................... 1 II. Tasks ........................................................................................................................... 2 1. Running Apache Directory Studio .............................................................................. 2 2. Updating Apache Directory Studio ............................................................................. 2 3. Reporting a bug -
Apache Directory Studio™
Main | ApacheDS | Studio | LDAP API | Mavibot | eSCIMo | Fortress | Kerby Apache Directory Studio Apache Directory Studio™ Home News The Eclipse-based LDAP browser and directory client Screenshots Apache Directory Studio is a complete directory tooling platform Downloads intended to be used with any LDAP server however it is particularly Version 2.0.0-M10 designed for use with ApacheDS. It is an Eclipse RCP application, Older Versions composed of several Eclipse (OSGi) plugins, that can be easily upgraded with additional ones. These plugins can even run within Documentation Eclipse itself. User's Guide Developer's Guide Download Apache FAQs Directory Studio 2.0.0-M10 Resources ChangeLog Testimonials LDAP Browser LDIF Editor Support Mailing Lists & IRC The LDAP Browser has been designed to work with almost any The LDIF Editor is a tool for editing LDIF files. It provides syntax Sources LDAP server available. It not only permits to read and display the highlighting and content assistance. Issue Tracking tree of your LDAP Server but also allows you to modify it by creating, editing or removing entries. Commercial Support Community How to Contribute Schema Editor Embedded ApacheDS Team The Schema Editor has been designed to edit the schema files Apache Directory Studio bundles the latest version of the Original Project Proposal in the OpenLDAP format. It allows you to edit easily attribute LDAPV3 certified ApacheDS. Creating and launching a new Special Thanks types and object classes for Apache Directory Server and LDAP server now takes less than 10 seconds! OpenLDAP. About Apache Apache License ApacheDS Configuration ACI Editor Sponsorship Thanks The ApacheDS Configuration Editor can be used to edit the The ACI Editor allows you to define, for an entry or a set of Security server configuration ('server.xml' and 'config.ldif' files) of an entries, graphically or manually (in souce code mode), an ACI Apache Directory Server installation. -

The Anatomy of a Secure Web Application Using Java EE, Spring Security and Apache Fortress
The Anatomy of a Secure Web App Using JavaEE, Spring Security and Apache Fortress May 18, 2017 ApacheCon NA, Miami Objective • Think about how a web app would behave, if we spared no expense for security. ApacheCon NA, Miami 2017 2 Introductions @play Shawn McKinney @work • Software Architect • PMC Apache Directory Project • Engineering Team ApacheCon NA, Miami 2017 3 Agenda Look at two examples… 1. Apache Fortress Demo + Java EE + Spring Security – https://github.com/shawnmckinney/apache-fortress-demo 2. Fortress SAML Demo + Spring Security SP – https://github.com/shawnmckinney/fortress-saml-demo ApacheCon NA, Miami 2017 4 Themes Covered 1. Simplicity 2. Common Sense 3. Household Analogies to explain ‘Why’ ApacheCon NA, Miami 2017 5 With a few caveats… • Not cloud native • Not microservices • Not big data Not a problem, same rules apply ApacheCon NA, Miami 2017 6 And a couple of recommendations • Listen, don’t take notes. These slides are published and have all the details you need. • Save questions for the end (we’ve got a lot of ground to cover). ApacheCon NA, Miami 2017 7 Example #1 Apache Fortress Demo https://github.com/shawnmckinney/apache-fortress-demo ApacheCon NA, Miami 2017 8 The Five Security Layers of Java Web Apps 1.Java Secure Socket Extension (JSSE) 2.Java EE Security 3.Spring Security 4.Web App Framework 5.Database Functions ApacheCon NA, Miami 2017 9 Rationale for Each 1.JSSE ---------------------------- private conversations 2.Java EE Security ---------- deadbolt on front door 3.Spring Security ------------ locks on room doors 4.Web App Framework - locks on equipment in rooms 5.Database Functions ---- content filtering ApacheCon NA, Miami 2017 10 Two Areas of Access Control 1.Java EE and Spring Role Declarative checks 2.RBAC Permission Programmatic checks ApacheCon NA, Miami 2017 11 Start with Tomcat Servlet Container ApacheCon NA, Miami 2017 12 1 & 2. -

Apache Directory Studio LDAP Browser
Apache Directory Studio LDAP Browser User's Guide Apache Directory Studio LDAP Browser: User's Guide Version 2.0.0.v20200411-M15 Copyright © 2006-2020 The Apache Software Foundation Licensed to the Apache Software Foundation (ASF) under one or more contributor license agreements. See the NOTICE file distributed with this work for additional information regarding copyright ownership. The ASF licenses this file to you under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at http://www.apache.org/licenses/LICENSE-2.0 Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License. Table of Contents I. Getting started ................................................................................................................ 1 1. Download and installation ........................................................................................ 1 2. Open LDAP perspective ........................................................................................... 1 3. Create connection ................................................................................................... 1 4. Browse the directory .............................................................................................. -

Full-Graph-Limited-Mvn-Deps.Pdf
org.jboss.cl.jboss-cl-2.0.9.GA org.jboss.cl.jboss-cl-parent-2.2.1.GA org.jboss.cl.jboss-classloader-N/A org.jboss.cl.jboss-classloading-vfs-N/A org.jboss.cl.jboss-classloading-N/A org.primefaces.extensions.master-pom-1.0.0 org.sonatype.mercury.mercury-mp3-1.0-alpha-1 org.primefaces.themes.overcast-${primefaces.theme.version} org.primefaces.themes.dark-hive-${primefaces.theme.version}org.primefaces.themes.humanity-${primefaces.theme.version}org.primefaces.themes.le-frog-${primefaces.theme.version} org.primefaces.themes.south-street-${primefaces.theme.version}org.primefaces.themes.sunny-${primefaces.theme.version}org.primefaces.themes.hot-sneaks-${primefaces.theme.version}org.primefaces.themes.cupertino-${primefaces.theme.version} org.primefaces.themes.trontastic-${primefaces.theme.version}org.primefaces.themes.excite-bike-${primefaces.theme.version} org.apache.maven.mercury.mercury-external-N/A org.primefaces.themes.redmond-${primefaces.theme.version}org.primefaces.themes.afterwork-${primefaces.theme.version}org.primefaces.themes.glass-x-${primefaces.theme.version}org.primefaces.themes.home-${primefaces.theme.version} org.primefaces.themes.black-tie-${primefaces.theme.version}org.primefaces.themes.eggplant-${primefaces.theme.version} org.apache.maven.mercury.mercury-repo-remote-m2-N/Aorg.apache.maven.mercury.mercury-md-sat-N/A org.primefaces.themes.ui-lightness-${primefaces.theme.version}org.primefaces.themes.midnight-${primefaces.theme.version}org.primefaces.themes.mint-choc-${primefaces.theme.version}org.primefaces.themes.afternoon-${primefaces.theme.version}org.primefaces.themes.dot-luv-${primefaces.theme.version}org.primefaces.themes.smoothness-${primefaces.theme.version}org.primefaces.themes.swanky-purse-${primefaces.theme.version} -

Red Hat Fuse 7.6 Apache Karaf Security Guide
Red Hat Fuse 7.6 Apache Karaf Security Guide Security for the Apache Karaf container Last Updated: 2020-08-11 Red Hat Fuse 7.6 Apache Karaf Security Guide Security for the Apache Karaf container Legal Notice Copyright © 2020 Red Hat, Inc. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/ . In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -

Security Pattern Validation and Recognition
Security-Pattern Recognition and Validation Dissertation Submitted by Michaela Bunke on 12th December 2018 to the Universit¨atBremen Faculty of Mathematics and Computer Science in partial fulfillment of the requirements for the degree of Doktor der Ingenieurwissenschaften { Dr.-Ing. { Reviewed by Prof. Dr. Hans-J¨orgKreowski Universit¨atBremen, Germany and Dr. Karsten Sohr Universit¨atBremen, Germany In Memorial of Ilse Schlamilch Karl Schlamilch Manfred Friedrichs 21 November 1924 03 March 1927 29 August 1935 09 June 2017 19 June 2018 3 July 2017 ABSTRACT The increasing and diverse number of technologies that are connected to the Internet, such as distributed enterprise systems or small electronic devices like smartphones, brings the topic IT security to the foreground. We interact daily with these technologies and spend much trust on a well-established software development process. However, security vulnerabilities appear in software on all kinds of PC(- like) platforms, and more and more vulnerabilities are published, which compromise systems and their users. Thus, software has also to be modified due to changing requirements, bugs, and security flaws and software engineers must more and more face security issues during the software design; especially maintenance programmers must deal with such use cases after a software has been released. In the domain of software development, design patterns have been proposed as the best-known solutions for recurring problems in software design. Analogously, security patterns are best practices aiming at ensuring security. This thesis develops a deeper understanding of the nature of security patterns. It focuses on their validation and detection regarding the support of reviews and maintenance activities. -
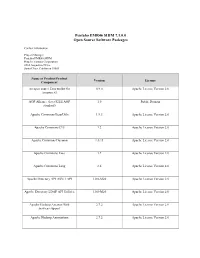
Pentaho EMR46 SHIM 7.1.0.0 Open Source Software Packages
Pentaho EMR46 SHIM 7.1.0.0 Open Source Software Packages Contact Information: Project Manager Pentaho EMR46 SHIM Hitachi Vantara Corporation 2535 Augustine Drive Santa Clara, California 95054 Name of Product/Product Version License Component An open source Java toolkit for 0.9.0 Apache License Version 2.0 Amazon S3 AOP Alliance (Java/J2EE AOP 1.0 Public Domain standard) Apache Commons BeanUtils 1.9.3 Apache License Version 2.0 Apache Commons CLI 1.2 Apache License Version 2.0 Apache Commons Daemon 1.0.13 Apache License Version 2.0 Apache Commons Exec 1.2 Apache License Version 2.0 Apache Commons Lang 2.6 Apache License Version 2.0 Apache Directory API ASN.1 API 1.0.0-M20 Apache License Version 2.0 Apache Directory LDAP API Utilities 1.0.0-M20 Apache License Version 2.0 Apache Hadoop Amazon Web 2.7.2 Apache License Version 2.0 Services support Apache Hadoop Annotations 2.7.2 Apache License Version 2.0 Name of Product/Product Version License Component Apache Hadoop Auth 2.7.2 Apache License Version 2.0 Apache Hadoop Common - 2.7.2 Apache License Version 2.0 org.apache.hadoop:hadoop-common Apache Hadoop HDFS 2.7.2 Apache License Version 2.0 Apache HBase - Client 1.2.0 Apache License Version 2.0 Apache HBase - Common 1.2.0 Apache License Version 2.0 Apache HBase - Hadoop 1.2.0 Apache License Version 2.0 Compatibility Apache HBase - Protocol 1.2.0 Apache License Version 2.0 Apache HBase - Server 1.2.0 Apache License Version 2.0 Apache HBase - Thrift - 1.2.0 Apache License Version 2.0 org.apache.hbase:hbase-thrift Apache HttpComponents Core -
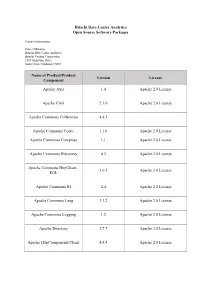
Hitachi Data Center Analytics Open Source Software Packages
Hitachi Data Center Analytics Open Source Software Packages Contact Information: Project Manager Hitachi Data Center Analytics Hitachi Vantara Corporation 2535 Augustine Drive Santa Clara, California 95054 Name of Product/Product Version License Component Apache Axis 1.4 Apache 2.0 License Apache Click 2.3.0 Apache 2.0 License Apache Commons Collections 4.4.1 Apache Commons Codec 1.10 Apache 2.0 License Apache Commons Compress 1.1 Apache 2.0 License Apache Commons Discovery 0.2 Apache 2.0 License Apache Commons HttpClient - 3.0.1 Apache 2.0 License EOL Apache Commons IO 2.4 Apache 2.0 License Apache Commons Lang 3.3.2 Apache 2.0 License Apache Commons Logging 1.2 Apache 2.0 License Apache Directory 2.7.7 Apache 2.0 License Apache HttpComponents Client 4.4.4 Apache 2.0 License Name of Product/Product Version License Component Apache HttpComponents 5.5.2 Apache 2.0 License Apache Log4j 1.2.17 Apache 2.0 License Apache Log4net 1.2.10 Apache 2.0 License Apache PDF Box 2.0.2 Apache 2.0 License Apache POI 3.15 Apache 2.0 License Apache Thrift 0.9.1 Apache 2.0 License Apache Web Services 1.0.2 Apache 2.0 License Apache Xerces Java Parser 2.9.0 Apache 2.0 License Apache XML Graphics 1.4 Apache 2.0 License Apache XML-RPC 3.1 Apache 2.0 License Apache XMLBeans 2.6.0 Apache 2.0 License Bouncy Castle Crypto API 1.45.0 MIT license CHILKAT CRYPT 9.5.0 Paid click-calendar 1.3.0 Apache 2.0 License Customized log4j File Appender Apache 2.0 License docx4j 2.7.0 Apache 2.0 License Name of Product/Product Version License Component dom4j 1.6.1 Apache 2.0 -

Code Smell Prediction Employing Machine Learning Meets Emerging Java Language Constructs"
Appendix to the paper "Code smell prediction employing machine learning meets emerging Java language constructs" Hanna Grodzicka, Michał Kawa, Zofia Łakomiak, Arkadiusz Ziobrowski, Lech Madeyski (B) The Appendix includes two tables containing the dataset used in the paper "Code smell prediction employing machine learning meets emerging Java lan- guage constructs". The first table contains information about 792 projects selected for R package reproducer [Madeyski and Kitchenham(2019)]. Projects were the base dataset for cre- ating the dataset used in the study (Table I). The second table contains information about 281 projects filtered by Java version from build tool Maven (Table II) which were directly used in the paper. TABLE I: Base projects used to create the new dataset # Orgasation Project name GitHub link Commit hash Build tool Java version 1 adobe aem-core-wcm- www.github.com/adobe/ 1d1f1d70844c9e07cd694f028e87f85d926aba94 other or lack of unknown components aem-core-wcm-components 2 adobe S3Mock www.github.com/adobe/ 5aa299c2b6d0f0fd00f8d03fda560502270afb82 MAVEN 8 S3Mock 3 alexa alexa-skills- www.github.com/alexa/ bf1e9ccc50d1f3f8408f887f70197ee288fd4bd9 MAVEN 8 kit-sdk-for- alexa-skills-kit-sdk- java for-java 4 alibaba ARouter www.github.com/alibaba/ 93b328569bbdbf75e4aa87f0ecf48c69600591b2 GRADLE unknown ARouter 5 alibaba atlas www.github.com/alibaba/ e8c7b3f1ff14b2a1df64321c6992b796cae7d732 GRADLE unknown atlas 6 alibaba canal www.github.com/alibaba/ 08167c95c767fd3c9879584c0230820a8476a7a7 MAVEN 7 canal 7 alibaba cobar www.github.com/alibaba/