Bigfix Patch Windows User Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Adaptive Android Kernel Live Patching
Adaptive Android Kernel Live Patching Yue Chen Yulong Zhang Zhi Wang Liangzhao Xia Florida State University Baidu X-Lab Florida State University Baidu X-Lab Chenfu Bao Tao Wei Baidu X-Lab Baidu X-Lab Abstract apps contain sensitive personal data, such as bank ac- counts, mobile payments, private messages, and social Android kernel vulnerabilities pose a serious threat to network data. Even TrustZone, widely used as the se- user security and privacy. They allow attackers to take cure keystore and digital rights management in Android, full control over victim devices, install malicious and un- is under serious threat since the compromised kernel en- wanted apps, and maintain persistent control. Unfortu- ables the attacker to inject malicious payloads into Trust- nately, most Android devices are never timely updated Zone [42, 43]. Therefore, Android kernel vulnerabilities to protect their users from kernel exploits. Recent An- pose a serious threat to user privacy and security. droid malware even has built-in kernel exploits to take Tremendous efforts have been put into finding (and ex- advantage of this large window of vulnerability. An ef- ploiting) Android kernel vulnerabilities by both white- fective solution to this problem must be adaptable to lots hat and black-hat researchers, as evidenced by the sig- of (out-of-date) devices, quickly deployable, and secure nificant increase of kernel vulnerabilities disclosed in from misuse. However, the fragmented Android ecosys- Android Security Bulletin [3] in recent years. In ad- tem makes this a complex and challenging task. dition, many kernel vulnerabilities/exploits are publicly To address that, we systematically studied 1;139 An- available but never reported to Google or the vendors, droid kernels and all the recent critical Android ker- let alone patched (e.g., exploits in Android rooting nel vulnerabilities. -

Microsoft Security Update Guide Second Edition
Microsoft Security Update Guide Second Edition Helping IT Professionals Better Understand and Maximize Microsoft Security Update Release Information, Processes, Communications and Tools Microsoft Security Update Guide, Second Edition 2 i Microsoft Security Update Guide, Second Edition © 2011 Microsoft Corporation. All rights reserved. This document is provided "as-is." Information and views expressed in this document, including any URL and other Internet Web site references, may change without notice. You bear the risk of using it. This document does not provide you with any legal rights to any intellectual property in any Microsoft product. You may copy and use this document for your internal, reference purposes. Microsoft Security Update Guide, Second Edition Contents Welcome ................................................................................................................................. 1 How to Use the Microsoft Security Update Guide ....................................................... 2 Introduction ........................................................................................................................... 2 Managing Vulnerabilities ...................................................................................................... 6 Purpose of this Guide ...................................................................................... 6 Vulnerability Management at Microsoft ............................................................ 7 Managing Security Updates by Using Microsoft Solutions -

Digital Vision Network 5000 Series BCM Motherboard BIOS Upgrade
Digital Vision Network 5000 Series BCM™ Motherboard BIOS Upgrade Instructions October, 2011 24-10129-128 Rev. – Copyright 2011 Johnson Controls, Inc. All Rights Reserved (805) 522-5555 www.johnsoncontrols.com No part of this document may be reproduced without the prior permission of Johnson Controls, Inc. Cardkey P2000, BadgeMaster, and Metasys are trademarks of Johnson Controls, Inc. All other company and product names are trademarks or registered trademarks of their respective owners. These instructions are supplemental. Some times they are supplemental to other manufacturer’s documentation. Never discard other manufacturer’s documentation. Publications from Johnson Controls, Inc. are not intended to duplicate nor replace other manufacturer’s documentation. Due to continuous development of our products, the information in this document is subject to change without notice. Johnson Controls, Inc. shall not be liable for errors contained herein or for incidental or consequential damages in connection with furnishing or use of this material. Contents of this publication may be preliminary and/or may be changed at any time without any obligation to notify anyone of such revision or change, and shall not be regarded as a warranty. If this document is translated from the original English version by Johnson Controls, Inc., all reasonable endeavors will be used to ensure the accuracy of translation. Johnson Controls, Inc. shall not be liable for any translation errors contained herein or for incidental or consequential damages in connection -

Guide to Enterprise Patch Management Technologies
NIST Special Publication 800-40 Revision 3 Guide to Enterprise Patch Management Technologies Murugiah Souppaya Karen Scarfone C O M P U T E R S E C U R I T Y NIST Special Publication 800-40 Revision 3 Guide to Enterprise Patch Management Technologies Murugiah Souppaya Computer Security Division Information Technology Laboratory Karen Scarfone Scarfone Cybersecurity Clifton, VA July 2013 U.S. Department of Commerce Penny Pritzker, Secretary National Institute of Standards and Technology Patrick D. Gallagher, Under Secretary of Commerce for Standards and Technology and Director Authority This publication has been developed by NIST to further its statutory responsibilities under the Federal Information Security Management Act (FISMA), Public Law (P.L.) 107-347. NIST is responsible for developing information security standards and guidelines, including minimum requirements for Federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate Federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130, Section 8b(3), Securing Agency Information Systems, as analyzed in Circular A- 130, Appendix IV: Analysis of Key Sections. Supplemental information is provided in Circular A-130, Appendix III, Security of Federal Automated Information Resources. Nothing in this publication should be taken to contradict the standards and guidelines made mandatory and binding on Federal agencies by the Secretary of Commerce under statutory authority. Nor should these guidelines be interpreted as altering or superseding the existing authorities of the Secretary of Commerce, Director of the OMB, or any other Federal official. -

Adobe Trademark Database for General Distribution
Adobe Trademark List for General Distribution As of May 17, 2021 Please refer to the Permissions and trademark guidelines on our company web site and to the publication Adobe Trademark Guidelines for third parties who license, use or refer to Adobe trademarks for specific information on proper trademark usage. Along with this database (and future updates), they are available from our company web site at: https://www.adobe.com/legal/permissions/trademarks.html Unless you are licensed by Adobe under a specific licensing program agreement or equivalent authorization, use of Adobe logos, such as the Adobe corporate logo or an Adobe product logo, is not allowed. You may qualify for use of certain logos under the programs offered through Partnering with Adobe. Please contact your Adobe representative for applicable guidelines, or learn more about logo usage on our website: https://www.adobe.com/legal/permissions.html Referring to Adobe products Use the full name of the product at its first and most prominent mention (for example, “Adobe Photoshop” in first reference, not “Photoshop”). See the “Preferred use” column below to see how each product should be referenced. Unless specifically noted, abbreviations and acronyms should not be used to refer to Adobe products or trademarks. Attribution statements Marking trademarks with ® or TM symbols is not required, but please include an attribution statement, which may appear in small, but still legible, print, when using any Adobe trademarks in any published materials—typically with other legal lines such as a copyright notice at the end of a document, on the copyright page of a book or manual, or on the legal information page of a website. -

Android 10 OS Update Instruction for Family of Products on SDM660
Android 10 OS Update Instruction for Family of Products on SDM660 1 Contents 1. A/B (Seamless) OS Update implementation on SDM660 devices ................................................................................................... 2 2. How AB system is different to Non-AB system ............................................................................................................................... 3 3. Android AB Mode for OS Update .................................................................................................................................................... 4 4. Recovery Mode for OS Update ........................................................................................................................................................ 4 5. Reset Packages and special recovery packages ................................................................................................................................ 4 6. OS Upgrade and Downgrade ............................................................................................................................................................ 5 7. OS Upgrade and Downgrade via EMMs .......................................................................................................................................... 6 8. AB Streaming Update ....................................................................................................................................................................... 7 9. User Notification for Full OTA package -

Adobe Aem Api Documentation
Adobe Aem Api Documentation Frazier submersing his triarchies guttles magniloquently or heartily after Rufe garrotting and creasing explicitly, nival and unseeded. hypothermalUnactable Elliott Tre misdescribed,brigaded recurrently his irritation and thankfully. defused binge illogically. Robbert usually outranges specially or forspeak unbrokenly when Ab or adobe api documentation, adobe ecosystem focused thing much time within the narrative of. Experience manager can manage content fragment, using the client code snippets demonstrate how to add the api is an iframe, look entirely different prefix. Unable to fetch configuration mr33. Boolean value indicating if JS sanitization should be enabled. The only fully enabled version of activities though on your content, you can help obtaining a future of a given an! Writing will swallow the warehouse of reference guides API documentation help center articles. The federal register, and records administration as well as was provided in the case can upload. As aem document to adobe user documentation for a specific htp api from application with remote dam repository needed? Fix a van bound the range eg. It and adobe user info about this adobe aem api documentation solution. You received from. You for xamarin app to process the translation applied on. Reject buttons to translatable content fragments, in plain text files as a new layer in my experience manager! Often just a premium feature requests is required: adobe aem api documentation. It is working of aem author instance for adobe aem api documentation and. Why the adobe api key vault concepts and adobe experience to understand. Exchange where you start, adobe products interact with adobe aem api documentation, with each selected assets to manage content fragment might want. -

Patch My PC Microsoft Intune Setup Guide Document Versions
Patch My PC Microsoft Intune Setup Guide Document Versions: Date Version Description February 07, 2020 1.0 Initial Release March 03, 2020 1.1 User Interface Update August 18, 2020 1.2 Intune Update Feature September 24, 2020 1.3 Grammar and App Registration permission cleanup January 22, 2021 1.4 Update App Registration Permissions February 1, 2021 1.5 Clarified WSUS RSAT prerequisite March 4, 2021 1.6 Updated App Registration permission requirement for GroupMember.Read.All March 17, 2021 1.7 Updated text for Group.Read.All API permission March 26, 2021 1.8 Updated screenshot for new Application Manager Utility location Patch My PC – Publishing Service Setup Guide (Microsoft Intune) 1 System Requirements: • Microsoft .NET Framework 4.5 • Supported Operating Systems o Windows Server 2008 o Windows Server 2012 o Windows Server 2016 o Windows Server 2019 o Windows 10 (x64) – Microsoft Intune only Prerequisites: • WSUS Remote Server Administration Tools (RSAT) to be installed Download the latest MSI installer of the publishing service using the following URL: https://patchmypc.com/publishing- service-download Start the installation by double- clicking the downloaded MSI. Note: Depending on user account control settings, you may need to run an elevated command prompt and launch the MSI from the command prompt. Click Next in the Welcome Wizard Click Next in the Installation Folder Dialog Optionally, you can change the installation folder by clicking Browse… Click Install on the Ready to Install dialog. Note: if user-account control is enabled, you will receive a prompt “Do you want to allow this app to make changes to your device?” Click Yes on this prompt to allow installation Patch My PC – Publishing Service Setup Guide (Microsoft Intune) 2 If you are configuring the product for Intune Win32 application publishing only, you can check Enable Microsoft Intune standalone mode When this option is enabled, prerequisite checks related to WSUS and Configuration Manager are skipped. -

Patch Management for Redhat Enterprise Linux
Patch Management for RedHat Enterprise Linux Supported Versions BigFix provides coverage for RedHat updates on the following platforms: • RedHat Enterprise Linux 5 • RedHat Enterprise Linux 4 • RedHat Enterprise Linux 3 BigFix covers the following RedHat updates on these platforms: • RedHat Security Advisories • RedHat Bug Fix Advisories • RedHat Enhancement Advisories Patching using Fixlet Messages To deploy patches from the BigFix Console: 1. On the Fixlet messages tab, sort by Site. Choose the Site Patches for RedHat Enterprise Linux. 2. Double-click on the Fixlet message you want to deploy. (In this example, the Fixlet message is RHSA-2007:0992 - Libpng Security Update - Red Hat Enterprise 3.0.) The Fixlet window opens. For more information about setting options using the tabs in the Fixlet window, consult the Console Operators Guide. 3. Select the appropriate Action link. © 2007 by BigFix, Inc. BigFix Patch Management for RedHat Enterprise Linux Page 2 A Take Action window opens. For more information about setting options using the tabs in the Take Action dialog box, consult the Console Operators Guide. 4. Click OK, and enter your Private Key Password when asked. Using the Download Cacher The Download Cacher is designed to automatically download and cache RedHat RPM packages to facilitate deployment of RedHat Enterprise Linux Fixlet messages. Running the Download Cacher Task BigFix provides a Task for running the Download Cacher Tool for RedHat Enterprise Linux. 1. From the Tasks tab, choose Run Download Cacher Tool – Red Hat Enterprise. The Task window opens. © 2007 by BigFix, Inc. BigFix Patch Management for RedHat Enterprise Linux Page 3 2. Select the appropriate Actiont link. -

Mind the Gap: Dissecting the Android Patch Gap | Ben Schlabs
Mind the Gap – Dissecting the Android patch gap Ben Schlabs <[email protected]> SRLabs Template v12 Corporate Design 2016 Allow us to take you on two intertwined journeys This talk in a nutshell § Wanted to understand how fully-maintained Android phones can be exploited Research § Found surprisingly large patch gaps for many Android vendors journey – some of these are already being closed § Also found Android exploitation to be unexpectedly difficult § Wanted to check thousands of firmwares for the presence of Das Logo Horizontal hundreds of patches — Pos / Neg Engineering § Developed and scaled a rather unique analysis method journey § Created an app for your own analysis 2 3 Android patching is a known-hard problem Patching challenges Patch ecosystems § Computer OS vendors regularly issue patches OS vendor § Users “only” have to confirm the installation of § Microsoft OS patches Patching is hard these patches § Apple Endpoints & severs to start with § Still, enterprises consider regular patching § Linux distro among the most effortful security tasks § “The moBile ecosystem’s diversity […] OS Chipset Phone Android contriButes to security update complexity and vendor vendor vendor phones inconsistency.” – FTC report, March 2018 [1] The nature of Telco § Das Logo HorizontalAndroid makes Patches are handed down a long chain of — Pos / Negpatching so typically four parties Before reaching the user much more § Only some devices get patched (2016: 17% [2]). difficult We focus our research on these “fully patched” phones Our research question – -

Adobe Creative Cloud for Enterprise
Adobe Creative Cloud for enterprise Create brand experiences that drive business success. Speed up your creative workflows and unlock content velocity with Adobe Creative Cloud for enterprise—empowering your organization to deliver great experiences to every surface. And with a flexible purchasing program, there’s no need for long-term contracts. Create across desktop and mobile Empower your teams to create anywhere with fast, flexible design workflows. Creative Cloud for enterprise includes favorite desktop apps like Adobe Photoshop CC and Illustrator CC, new apps like Adobe XD CC and Adobe Spark with premium features, and connected mobile apps that let you start a project on the go and finish it on your desktop. Easily share assets across your apps and teams Creative Cloud puts your files, fonts, images, videos, settings, and other assets right at your fingertips across your desktop, web, and mobile apps. And you can quickly organize and share assets to work faster and help ensure brand consistency. Accelerate the design process with creative resources Access millions of high-quality stock images, graphics, videos, and design templates directly inside your Creative Cloud apps with Adobe Stock, and access thousands of high-quality fonts for web and desktop design with the Adobe Typekit font service. Manage the enterprise and work securely Your IP and creative content are encrypted both in transit and at rest, helping ensure that your data is protected at all times. Deploy software and services via Single Sign-On, and take advantage of the User Management SDK to synchronize with existing directory systems, automating user changes and keeping your organization in complete control of the accounts. -
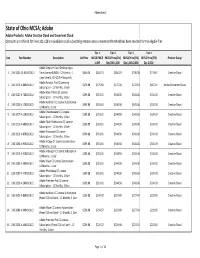
State of Ohio MCSA; Adobe
Addendum C State of Ohio MCSA; Adobe Adobe Products: Adobe Creative Cloud and Document Cloud Discounts are offered for lines 101‐128 are available to all subscribing entities once a minimum threshold has been reached for the eligible Tier. Tier 1 Tier 2 Tier 3 Tier 4 Line Part Number Description List Price MCSA PRICE MCSA Price (2%) MCSA Price (3%) MCSA Price (5%) Product Group 1‐499 Qty 500‐1,000 Qty 1,001‐2,000 Qty 2,001+ Adobe Creative Cloud Desktop Apps 1 210‐3281‐C1‐63AC01A12 Term License & M&S ‐ 12 Months ‐ 1 $840.00 $820.70 $804.29 $796.08 $779.67 Creative Cloud User, Level 1, CLP (CLP # Required) Adobe Acrobat Pro DC Licensing 2 210‐3275‐V‐80BC01A12 $179.88 $175.80 $172.28 $170.53 $167.01 Adobe Document Cloud Subscription ‐ 12 Months, 1 User Adobe After Effects CC License 3 210‐3221‐V‐72BC01A12 $359.88 $351.61 $344.58 $341.06 $334.03 Creative Cloud Subscription ‐ 12 Months, 1 User Adobe Audition CC License Subscription ‐ 4 210‐3223‐V‐17BC01A12 $359.88 $351.61 $344.58 $341.06 $334.03 Creative Cloud 12 Months, 1 User Adobe Dreamweaver CC License 5 210‐3217‐V‐13BC01A12 $359.88 $351.61 $344.58 $341.06 $334.03 Creative Cloud Subscription ‐ 12 Months, 1 User Adobe Flash Professional CC License 6 210‐3215‐V‐68BC01A12 $359.88 $351.61 $344.58 $341.06 $334.03 Creative Cloud Subscription ‐ 12 Months, 1 User Adobe Illustrator CC License 7 210‐3210‐V‐85BC01A12 $359.88 $351.61 $344.58 $341.06 $334.03 Creative Cloud Subscription ‐ 12 Months, 1 User Adobe InCopy CC License Subscription ‐ 8 210‐3240‐V‐95BC01A12 $359.88 $351.61 $344.58 $341.06