Windows 10 Upgrade with Drivelock Disk Protection
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Guide to Hardening Windows 10 Technical Guide
NOVEMBER 2020 Guide to Hardening Windows 10 For Administrators, Developers and Office Workers TABLE OF CONTENTS Introduction .......................................................................................................................... 4 Prerequisites ............................................................................................................................ 4 User roles ................................................................................................................................. 4 EFI (BIOS) Configuration ...................................................................................................... 5 To be enabled: ......................................................................................................................... 5 To be disabled: ......................................................................................................................... 5 Windows Defender Firewall .................................................................................................. 6 Enable logging of dropped packets ............................................................................................. 6 Disable enforcement of local rules and disable notifications .......................................................... 7 Block outbound connections by default ....................................................................................... 8 Secure potentially vulnerable protocols ...................................................................................... -

Metasys Server Installation and Upgrade Instructions Code No
Metasys Server Installation and Upgrade Instructions Code No. LIT-12012162 Software Release 10.0 Issued April 15, 2019 Welcome.....................................................................................................................................3 Getting Started...........................................................................................................................3 Summary of Changes.........................................................................................................................4 Prerequisite Software Checklist for Installation and Upgrade.......................................................4 Recommended OS and SQL Server Combinations.........................................................................7 Upgrade Pre-Work Checklist..............................................................................................................8 Metasys Server Installation.....................................................................................................10 Installing Unified Metasys Server on Desktop Computer.............................................................10 Installing Unified Metasys Server on Server Computer................................................................12 Installing Unified Metasys Server and SCT on Desktop Computer.............................................14 Installing Unified Metasys Server and SCT on Server Computer................................................17 Installing a Split Metasys Server and SCT.....................................................................................20 -

Surface Hub 2S Admin Guide
Surface Hub 2S Admin Guide Surface Hub 2S coming soon; Pre-release products shown; products and features subject to regulatory certification/approval, may change, and may vary by country/region. Surface Hub 2S has not yet been authorized under U.S. Federal Communications Commission (FCC) rules; actual sale and delivery is contingent on compliance with applicable FCC requirements. This documentation is an early release of the final documentation, which may be changed prior to final commercial release and is confidential and proprietary information of Microsoft Corporation. This document is provided for informational purposes only and Microsoft makes no warranties, either express or implied, in this document. © 2019. Microsoft Corporation. All rights reserved Introduction .................................................................................................................................................. 1 Welcome to Surface Hub 2S ......................................................................................................................... 1 New User Experience and Features ........................................................................................................................ 1 Microsoft Teams ..................................................................................................................................................... 1 New form factor and hardware changes ................................................................................................................ 2 Surface -

3 Deployment Options
Prior to the parties indicating final agreement by signing a Work Order, the information contained in this document represents the current view of CB5 Solutions, LLC on the issues discussed as of the date of publication and is subject to change. Furthermore, because CB5 must respond to changing market conditions, this document should not be interpreted as an invitation to contract or a commitment on the part of CB5. Changes to this document will be managed through a Change Management Process. CB5 MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), or for any purpose, without the express written permission of CB5 Solutions, LLC. CB5 may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from CB5, our provision of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The descriptions of other companies’ products in this document, if any, are provided only as a convenience to you. Any such references should not be considered an endorsement or support by CB5. CB5 cannot guarantee their accuracy, and the products may change over time. Also, the descriptions are intended as brief highlights to aid understanding, rather than as thorough coverage. -

SECURITY ADVISORY Volume 2017-160
Security Advisory | Volume 2017‐160 PRODUCT DESCRIPTION AFFECTED VERSIONS OTHER INFORMATION Microsoft Edge Remote Chakra Scripting Engine Memory Corruption Vulnerability - CVE-2017- Published - May 12, 2017 0223 CVE-2017-0223 Microsoft Edge Remote Chakra Scripting The Chakra JavaScript engine in Microsoft Edge on Windows 10 version 1703, does not properly CVSS - 7.5 Version(s): <=Windows Ver Engine Memory Corruption Vulnerability - render when handling objects in memory, making it prone to a remote code execution vulnerability. Vendor's Advisory - https://www.microsoft.com/en- 10. CVE-2017-0223 A remote attacker could exploit this issue to cause memory corruption and execute arbitrary code us/windows/microsoft-edge in the context of the current user. To exploit this issue the attacker would have to entice the victim http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2017- to visit a maliciously crafted web site or to open a maliciously crafted file. 0223 Published - May 12, 2017 Linux Kernel 4.11.1 and Earlier Local DoS or Other Impact due to Use-After-Free Error - CVE-2017- CVE-CVE-2017-7487 Linux Kernel 4.11.1 and Earlier Local DoS 7487 CVSS - 7.2 or Other Impact due to Use-After-Free The ipxitf_ioctl function in net/ipx/af_ipx.c in the Linux kernel through 4.11.1 mishandles reference Version(s): <=4.11.1 Vendor's Advisory - Error - CVE-2017-7487 counts, which allows local users to cause a denial of service (use-after-free) or possibly have http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2017- unspecified other impact via a failed SIOCGIFADDR ioctl call for an IPX interface. -
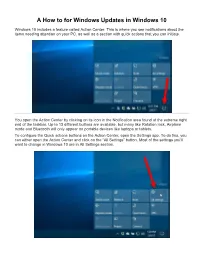
A How to for Windows Updates in Windows 10
A How to for Windows Updates in Windows 10 Windows 10 includes a feature called Action Center. This is where you see notifications about the items needing attention on your PC, as well as a section with quick actions that you can initiate. You open the Action Center by clicking on its icon in the Notification area found at the extreme right end of the taskbar. Up to 13 different buttons are available, but many like Rotation lock, Airplane mode and Bluetooth will only appear on portable devices like laptops or tablets. To configure the Quick actions buttons on the Action Center, open the Settings app. To do this, you can either open the Action Center and click on the “All Settings” button. Most of the settings you'll want to change in Windows 10 are in All Settings section. or you can open the Start menu and click the “Settings” button on the lower-left side of the menu. Windows settings is organized into various categories: System, Devices, Network & Internet, Personalization, Apps, Accounts, Time & language, Ease of Access, Privacy, and Update & security. You click on a category to view and change more settings for that category. Settings in Windows 10 – alternatively use Win () + I key combination. The Settings app from Windows 10 holds almost all the settings governing the way your computer or device works. The traditional way of getting to one setting or to another is to open the appropriate settings category and browse through it until you find what you’re looking for. The Setting app from Windows 10 is very well organized, a lot better than the old Control Panel used to be. -
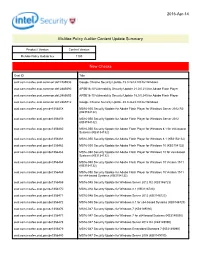
Mcafee Policy Auditor Content Update V1183
2016-Apr-14 McAfee Policy Auditor Content Update Summary Product / Version Content Version McAfee Policy Auditor 6.x 1183 New Checks Oval ID Title oval:com.mcafee.oval.common:def:2485596 Google Chrome Security Update 49.0.2623.108 for Windows oval:com.mcafee.oval.common:def:2485690 APSB16-10 Vulnerability Security Update 21.0.0.213 for Adobe Flash Player oval:com.mcafee.oval.common:def:2485692 APSB16-10 Vulnerability Security Update 18.0.0.343 for Adobe Flash Player oval:com.mcafee.oval.common:def:2485712 Google Chrome Security Update 49.0.2623.108 for Windows oval:com.mcafee.oval.gen:def:356458 MS16-050 Security Update for Adobe Flash Player for Windows Server 2012 R2 (KB3154132) oval:com.mcafee.oval.gen:def:356459 MS16-050 Security Update for Adobe Flash Player for Windows Server 2012 (KB3154132) oval:com.mcafee.oval.gen:def:356460 MS16-050 Security Update for Adobe Flash Player for Windows 8.1 for x64-based Systems (KB3154132) oval:com.mcafee.oval.gen:def:356461 MS16-050 Security Update for Adobe Flash Player for Windows 8.1 (KB3154132) oval:com.mcafee.oval.gen:def:356462 MS16-050 Security Update for Adobe Flash Player for Windows 10 (KB3154132) oval:com.mcafee.oval.gen:def:356463 MS16-050 Security Update for Adobe Flash Player for Windows 10 for x64-based Systems (KB3154132) oval:com.mcafee.oval.gen:def:356464 MS16-050 Security Update for Adobe Flash Player for Windows 10 Version 1511 (KB3154132) oval:com.mcafee.oval.gen:def:356465 MS16-050 Security Update for Adobe Flash Player for Windows 10 Version 1511 for x64-based Systems (KB3154132) -

Windows 10 What to Do Now
WINDOWS 10 WHAT TO DO NOW ARRAYA SOLUTIONS Educating, Engaging, and Elevating IT since 1999 Chuck Kiessling Director, Cloud and Workspace Solutions AGENDA Why are we here? What is your story? What are some key items to help your journey? Changes to Desktop Security WaaS: Servicing your Security Needs INTRODUCTIONS Chuck Kiessling Director, Cloud and Modern Workspace Practice [email protected] Twitter: @CKiessling WHAT IS YOUR INTEREST IN THIS SESSION? Windows and Office Active ConfigMgr Directory Windows Exchange Server SharePoint On-premises Legacy devices Modern devices Windows 7 Windows 10 Office Office 365 Active Directory + Azure Active Directory ConfigMgr + Microsoft Intune Windows Defender + Microsoft Threat Protection Cloud-connect what you have today What is your Digital Transformation Story? WHAT YOU CAN DO TO PROTECT YOUR BUSINESS WITH WINDOWS 10 WINDOWS 10 IS THE MOST SECURE WINDOWS EVER Device safeguards Threat resistance Identity protection Information security Threat detection and response *For the supported lifetime of the device THE MICROSOFT INTELLIGENT SECURITY GRAPH 450B monthly authentications Cyber threat intelligence collected 200+ global from unparalleled security cloud consumer and commercial information sources services Billions of data points Detect threats before they do damage +1B Windows Powered by machine learning and 18+ billion devices Bing web updated human intelligence pages scanned 400B e-mails analyzed THE MOST SECURITY, BUILT IN Where do these data points come from? WINDOWS 10: THE -

KACE® Systems Management Appliance 11.0 Patching Catalog
KACE® Systems Management Appliance 11.0 Patching Catalog: Supported Operating Systems and Applications Table of Contents Patching matrix........................................................................................................................................ 3 Operating systems........................................................................................................................... 3 Applications...................................................................................................................................... 5 About us.................................................................................................................................................20 Technical support resources......................................................................................................... 20 Legal notices..................................................................................................................................20 KACE Systems Management Appliance 11.0 Patching Catalog: Supported Operating Systems and Applications 2 Patching matrix This document contains the most recent list of supported applications and operating systems in the KACE Patch Catalog. The content of this matrix was compiled in March 2021. Operating systems Platform Publisher Operating System (OS) OS Architecture Edition Mac Apple Computer, Inc. macOS Catalina 10.15 ALL x86_64 Mac Apple Computer, Inc. macOS High Sierra 10.13 ALL x86_64 Mac Apple Computer, Inc. macOS Mojave 10.14 ALL x86_64 Mac Apple -

Administrator Guide
Administrator Guide HP ThinUpdate © Copyright 2016, 2017 HP Development Company, L.P. Windows is either a registered trademark or trademark of Microsoft Corporation in the United States and/or other countries. Confidential computer software. Valid license from HP required for possession, use or copying. Consistent with FAR 12.211 and 12.212, Commercial Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under vendor's standard commercial license. The information contained herein is subject to change without notice. The only warranties for HP products and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein. Fifth Edition: November 2017 First Edition: February 2016 Document Part Number: 849856-005 User input syntax key Text that you must enter into a user interface is indicated by fixed-width font. Item Description Text without brackets or braces Items you must type exactly as shown <Text inside angle brackets> A placeholder for a value you must provide; omit the brackets [Text inside square brackets] Optional items; omit the brackets {Text inside braces} A set of items from which you must choose only one; omit the braces | A separator for items from which you must choose only one; omit the vertical bar ... Items that can or must repeat; omit the ellipsis iii iv User input syntax key Table of contents 1 Getting started ............................................................................................................................................. 1 Supported operating systems ............................................................................................................................... 1 Downloading and installing HP ThinUpdate ......................................................................................................... -

Release Notes 7.9.6
Release Notes 7.9.6 © 2019 DriveLock SE Release Notes Table of Contents Part I Introduction 3 1 Document Conventions 3 2 DriveLock Documentation 3 Part II System Requirements 5 1 DriveLock Agent 5 2 DriveLock Management Console and Control Center 5 3 DriveLock Enterprise Service 5 Part III Supported Platforms 7 Part IV Version History 9 1 DriveLock 7.9.6 9 2 DriveLock 7.9.4 10 3 DriveLock 7.9.2 10 Part V Known Issues 12 1 Quickstart Setup Wizard 12 2 Installation of Management Components Using Group Policy 12 3 DriveLock Device Scanner 12 4 Manual Updates 13 5 Self Service unlock 13 6 DriveLock iOS and iTunes 13 7 Windows Portable Devices (WPD) 13 8 DriveLock Disk Protection 13 9 DriveLock File Protection and Microsoft OneDrive 15 10 BitLocker Management 15 11 Antivirus 16 Part VI Test Installation and Upgrade 17 1 DriveLock Evaluation 17 2 Updating DriveLock Components 17 General Issues 17 Updating DriveLock Disk Protection 17 Release Notes 7.9.6 2 © 2019 DriveLock SE Introduction 1 Introduction This document contains important information about the new version of DriveLock and changes from previous DriveLock versions. The DriveLock Release Notes also describes changes and additions to DriveLock that were made after the documentation was completed. This and other documentation can be found on our online help page www.drivelock.help. 1.1 Document Conventions Throughout this document the following conventions and symbols are used to emphasize important points that you should read carefully, or menus, items or buttons that you need to click or select. -

Microsoft Windows FIPS 140 Validation Security Policy Document
Windows Resume Security Policy Document Microsoft Windows FIPS 140 Validation Microsoft Windows 10 (Creators Update, Fall Creators Update) Non-Proprietary Security Policy Document Document Information Version Number 1.03 Updated On May 24, 2018 © 2018 Microsoft. All Rights Reserved Page 1 of 20 This Security Policy is non-proprietary and may be reproduced only in its original entirety (without revision). Windows Resume Security Policy Document The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs- NonCommercial License (which allows redistribution of the work). To view a copy of this license, visit http://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. © 2018 Microsoft Corporation.