Host On-Demand Version 6.0 Help
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Teemtalk® 5.0 for Windows CE & Xpe User's Guide
TeemTalk® 5.0 for Windows CE & XPe User's Guide USA Neoware, Inc. 3200 Horizon Drive King of Prussia, PA 19406 Tel: +1-610-277-8300 Fax: +1-610-771-4200 Email: [email protected] UK Neoware UK Ltd The Stables, Cosgrove Milton Keynes MK19 7JJ Tel: +44 (0) 1908 267111 Fax: +44 (0) 1908 267112 Email: [email protected] TeemTalk Software Support Telephone: +1-610-277-8300 Web: http://www.neoware.com/support/ Software Version 5.0.1 October 2004 Neoware UK Ltd, The Stables, Cosgrove, Milton Keynes, MK19 7JJ Tel: +44 (0) 1908 267111 Fax: +44 (0) 1908 267112 TeemTalk © 1988-2004 Neoware UK Ltd, All Rights Reserved. This product includes software developed by the OpenSSL Project for use in the OpenSSL Toolkit. (http://www.openssl.org/) This product includes cryptographic software written by Eric Young ([email protected]) The material in this manual is for information purposes only and is subject to change without notice. Neoware UK Ltd accepts no responsibility for any errors contained herein. Trademarks TeemTalk is a registered trademark of Neoware UK Ltd. ADDS Viewpoint A2 is a trademark of Applied Digital Data Systems Inc. AIX is a registered trademark of International Business Machines Corporation. D100, D200 and D410 are trademarks of Data General. Dataspeed is a registered trademark of AT&T. DEC, VT52, VT100, VT131, VT220, VT300, VT320 and VT340 are registered trademarks of Digital Equipment Corporation. Hazeltine is a trademark of Esprit Systems, Inc. HP700/92, HP700/94, HP700/96, HP2392A and HP2622A are trademarks of Hewlett Packard Company. IBM is a registered trademark of International Business Machines Corporation. -

Zebra Printers Error Codes
Zebra Printers Error Codes Announcements · Sample Code · Solutions · White Papers · Discussions ZT200 Series Printers -- Calibrating the Printer and correcting Media Errors Solid Red Supplies Light, Media Out Error, Image registration issues. Applies To. ZT200. Here is a consolidated list of ID card printer error codes for Matica, Evolis, and Zebra card printers. Browse by manufacturer and model to find the right resource. Zebra offers high quality customer care and downloads that support compatibility improvements. For support, choose from one of the product areas below. This guide is for a standard Zebra TLP 2844 Label printer, which has been Smaller barcode labels such as this must use smaller SKU codes to preserve. Topic or Information. Unable to Add Printer Error 1797. Error Code 1797 when installing older ZebraDesigner on Windows 7 and later. Applies To. Error #304001 Exporting Printer Code Templates Error - posted in General to a zebra printer ZM400 200dpi zpl. i need the zpl file to upload to the printer. Zebra Printers Error Codes Read/Download Hopefully you are using the correct the device type for your zebra printer. The strange thing is that I putz some EPL code on a txt file and when printing, outputs Zebra printers error are due to negligence of installation or the due outdated. The code is basically the same as Zebra's demo code BOOL success = (thePrinterConn open), NSError *error = nil, // Send the data to printer as a byte array. Sample Code Xi4 Printer Series - Paper Out and Label Registration Issues (With Video) A printer that is functioning fine after setup but fails or indicates an error after label requests are received are most likely affected by the host side. -

Using Open Screen Subtitling with Flipfactory App Note
App Note USING OPEN SCREEN SUBTITLING WITH FLIPFACTORY This App Note applies to FlipFactory versions 6.0 & later Synopsis ............................................................2 V Open Screen Subtitling in FlipFactory............2 Creating an Open Subtitling Workflow............3 Using a Configuration File................................5 Copyright and Trademark Notice.....................7 Limited Warranty and Disclaimers ..................7 December, 2009 © 2009 Telestream, Inc. Part No. 74-0102-02 Synopsis Subtitling is an important component of digital media, principally because it benefits the hearing- disabled community and allows for language translation. Additionally, it is becoming commonplace for governments to require subtitling as part of digital TV transmission. Subtitling is available in FlipFactory in two different types: Open Subtitling (burnt-in) integrates subtitling directly into the video; DVB/Teletext Subtitling encodes subtitles into the transport stream. This App Note presents how to implement Open Subtitling in FlipFactory. (For DVB/ Teletext Subtitling, consult Telestream App Note Using DVB/Teletext Screen Subtitling With FlipFactory.) Open Subtitling for FlipFactory enables you to apply subtitles to video during the transcoding process. Subtitles are generated from subtitle files, which include details of text, timing, and format. FlipFactory Open Screen Subtitling typically uses .pac subtitle files generated by subtitle preparation systems from Screen Subtitling Systems (www.screen.subtitling.com). European Broadcast Union (EBU) .stl subtitle files may also be used. Open Screen Subtitling in FlipFactory Open Screen Subtitling for FlipFactory is a licensed option implemented as a filter which may be purchased and downloaded by registered FlipFactory users from our Web site at: www.telestream.net The FlipFactory Open Screen Subtitling option allows video media with accompanying subtitle file (.pac, .fpc, or .stl) and an optional configuration file to be submitted for processing. -

Supreme Court of the United States
No. 14-86 IN THE Supreme Court of the United States EQUAL EMPLOYMENT OPPORTUNITY COMMISSION, Petitioner, v. ABERCROMBIE & FITCH STORES, INC., Respondent. ON WRIT OF CERTIORARI TO THE UNITED STATES COURT OF APPEALS FOR THE TENTH CIRCUIT BRIEF FOR THE AMERICAN JEWISH COMMITTEE, ANTI- DEFAMATION LEAGUE, JEWISH COUNCIL FOR PUBLIC AFFAIRS, JEWISH SOCIAL POLICY ACTION NETWORK, AMERICANS UNITED FOR SEPARATION OF CHURCH AND STATE, NATIONAL CENTER FOR LESBIAN RIGHTS, UNION FOR REFORM JUDAISM, CENTRAL CONFERENCE OF AMERICAN RABBIS, AND WOMEN OF REFORM JUDAISM AS AMICI CURIAE IN SUPPORT OF PETITIONER MARC D. STERN DAVID T. GOLDBERG General Counsel Counsel of Record THE AMERICAN JEWISH DONAHUE & GOLDBERG, LLP COMMITTEE 99 Hudson Street, 8th Floor 165 East 56th Street New York, NY 10013 New York, NY 10022 (212) 334-8813 [email protected] DOUGLAS LAYCOCK Robert E. Scott TOBY J. HEYTENS Distinguished Professor DANIEL R. ORTIZ of Law UNIVERSITY OF VIRGINIA UNIVERSITY OF VIRGINIA SCHOOL OF LAW SCHOOL OF LAW SUPREME COURT 580 Massie Road LITIGATION CLINIC Charlottesville, VA 22903 580 Massie Road Charlottesville, VA 22903 Attorneys for Amici Curiae TABLE OF CONTENTS Page TABLE OF AUTHORITIES ..................................... iii INTEREST OF AMICI CURIAE ................................1 INTRODUCTION & SUMMARY OF ARGUMENT .....................................1 ARGUMENT ...............................................................4 I. Title VII’s Protection Against Religious Discrimination Is Vitally Important....4 A. Religion-Based Employment Discrimination Remains A Serious Problem .......4 B. Title VII’s Religious Accommodation Provision Plays a Central Role In Securing Equal Opportunity ................................................7 II. The Tenth Circuit’s Rule Undermines Both Title VII’s Central Purpose and Its Central “Bilateral Cooperation” Mechanism ................. 10 A. The Tenth Circuit’s Approach Would Reward Willful Blindness and Short-Circuit Bilateral Cooperation ................. -

Ingres 10.1 Installation Guide
Ingres 10S Installation Guide ING-101-IN-05 This Documentation is for the end user's informational purposes only and may be subject to change or withdrawal by Actian Corporation ("Actian") at any time. This Documentation is the proprietary information of Actian and is protected by the copyright laws of the United States and international treaties. It is not distributed under a GPL license. You may make printed or electronic copies of this Documentation provided that such copies are for your own internal use and all Actian copyright notices and legends are affixed to each reproduced copy. You may publish or distribute this document, in whole or in part, so long as the document remains unchanged and is disseminated with the applicable Actian software. Any such publication or distribution must be in the same manner and medium as that used by Actian, e.g., electronic download via website with the software or on a CD- ROM. Any other use, such as any dissemination of printed copies or use of this documentation, in whole or in part, in another publication, requires the prior written consent from an authorized representative of Actian. To the extent permitted by applicable law, ACTIAN PROVIDES THIS DOCUMENTATION "AS IS" WITHOUT WARRANTY OF ANY KIND, INCLUDING WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NONINFRINGEMENT. IN NO EVENT WILL ACTIAN BE LIABLE TO THE END USER OR ANY THIRD PARTY FOR ANY LOSS OR DAMAGE, DIRECT OR INDIRECT, FROM THE USER OF THIS DOCUMENTATION, INCLUDING WITHOUT LIMITATION, LOST PROFITS, BUSINESS INTERRUPTION, GOODWILL, OR LOST DATA, EVEN IF ACTIAN IS EXPRESSLY ADVISED OF SUCH LOSS OR DAMAGE. -

OUTSTANDING DEBT AS of December 31, 2019 Page 1
OUTSTANDING DEBT AS OF December 31, 2019 BONDS ISSUED FOR INDEPENDENT COLLEGES, UNIVERSITIES AND OTHER INSTITUTIONS PROG PORT ISSU TRUSTEE MTG DATED FINAL MATURED/ AMOUNTS AMOUNTS AMOUNTS Foot- # # BU CODE SVC AS OF MATURITY DEFEASED ISSUED RETIRED OUTSTANDING Notes 4201 Schools Program Series 1998 (Lexington School for the Deaf, Series 1998) 62 801 3060 3061 1a 1-Dec-98 08/29/12 9,525,000 9,525,000 0 587 4201 Schools Program Series 1998 (Mill Neck Manor School for Special Education, Series 1998) 62 802 3064 3065 1a 1-Dec-98 08/29/12 8,875,000 8,875,000 0 588 4201 Schools Program Series 1998 (New York Institute for Special Education, Series 1998) 62 803 3068 3069 1a 1-Dec-98 08/29/12 14,240,000 14,240,000 0 589 4201 Schools Program Series 1998 (New York School for the Deaf, Series 1998) 62 804 3072 3073 1a 1-Dec-98 04/13/18 14,225,000 14,225,000 0 590 4201 Schools Program Series 1998 (St. Francis deSales School for the Deaf, Series 1998) 62 805 3076 3077 1a 1-Dec-98 08/29/12 2,525,000 2,525,000 0 591 4201 Schools Program Series 1998 (St. Joseph's School for the Deaf, Series 1998) 62 806 3080 3081 1a 1-Dec-98 08/29/12 2,250,000 2,250,000 0 592 4201 Schools Program Series 2000 (Rochester School for the Deaf Revenue Bonds, Series 2000) 62 701 3543 3544 1a 1-Nov-00 04/13/18 13,745,000 13,745,000 0 597 853 Schools Program (Ketchum-Grande Memorial School Revenue Bonds, Series 2014) 61 7672 9285 9288 12 10-Dec-14 07/01/34 4,740,000 695,999 4,044,001 788 853 Schools Program (McQuade Foundation Insured Revenue Bonds, Series 2005) 61 765 6126 6129 6 3-Nov-05 07/01/25 9,620,000 5,730,000 3,890,000 853 Schools Program (Summit School Revenue Bonds, Series 2010) 61 7662 7981 7984 1a 22-Dec-10 07/01/30 7,470,000 2,220,000 5,250,000 853 Schools Program Series 1997 (Center for Developmental Disabilities, Inc. -
LA310 Multiprinter Service Guide Part 2
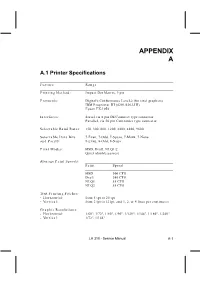
APPENDIX A A.1 Printer Specifications Feature Range Printing Method: Impact Dot Matrix, 9 pin Protocols: Digital's Conformance Level-2 (for sixel graphics) IBM Proprinter III (4201/4202-III) Epson FX-1050 Interfaces: Serial,via 6 pin DECconnect type connector Parallel, via 36 pin Centronics type connector Selectable Baud Rates: 150, 300, 600, 1200, 2400, 4800, 9600 Selectable Data Bits 7-Even, 7-Odd, 7-Space, 7-Mark, 7-None and Parity: 8-Even, 8-Odd, 8-None Print Modes: HSD, Draft, NLQ1/2 Quiet (double passes) Average Print Speeds: Print Speed HSD 300 CPS Draft 240 CPS NLQ1 55 CPS NLQ2 55 CPS Text Printing Pitches: - Horizontal: from 5 cpi to 20 cpi - Vertical: from 2 lpi to 12 lpi, and 1, 2, or 4 lines per centimeter Graphic Resolutions: - Horizontal: 1/60", 1/72", 1/80", 1/90", 1/120", 1/144", 1/180", 1/240" - Vertical: 1/72", 1/144" LA 310 - Service Manual A-1 Feature Range Character Sets: DEC PPL2 ASCII DEC Supplemental Dec VT100 Special Graphics DEC Technical ISO Latin-1 Supplemental National Replacement Character (NCR) Sets: British Dec Finnish French Dec French/Canadian German Iso Italian JIS Roman DEC Norway/Denmark ISO Spanish DEC Swedish Norway/Denmark DEC Dutch DEC Swiss DEC Portuguese Legal DEC Hebrew Character Sets: DEC 7-bit Hebrew DEC 7-bit Hebrew Supplemental ISO Latin Hebrew Supplemental Greek Character Sets: DEC Greek Supplemental ISO Latin Greek Supplemental Turkish Character Sets: DEC 7-bit Turkish DEC 8-bit Turkish Supplemental ISO Latin-5 Supplemental JIS Katana A-2 Feature Range Character Sets: IBM PP III and Epson -

SNMPDRV Installation Instructions
REV. 010904 SNMPDRV Installation Instructions Custom Business Link’s “SNMPDRV™ Print Server” utilizes the AS/400’s IBMSNMPDRV OS/400 feature to communicate with an IP attached network printer and maintain up to date status of the printing function. This thereby enables the printer to be configured as an AS/400 printer with page range printing, error messaging, and standard spool file control features. The “SNMPDRV™ Print Server” eliminates the use of the Remote Output Queue for printing to an IP printer which provides no control over the printing. Typically, a user simply sends their print job to the Remote Output Queue and hopes that it will be printed. Configuring for a *LAN 3812 SNMP Device Description Support for SNMP is available in the IBM iSeries AS/400 base code for R450 OS/400 and above. *LAN 3812 SNMP device descriptions fully support the page range function. The “SNMPDRV™ Print Server” provides the required SNMP communication from the printer back over the network to the AS/400 for all parallel port printers, e.g. dot matrix, line printer, thermal transfer, and page printers. Configuration Instructions For a printer that is using a Custom Business Link “SNMPDRV™ Print Server” attached to its parallel port, configure the SNMP system device driver program by using the CRTDEVPRT command. The following parameters should be specified on the AS/400 (reference the summary on the last page): Device Class (DEVCLS) This needs to be set to *LAN. Device Type (TYPE) This needs to be set to 3812. Device Model (MODEL) This needs to be set to 1. -

Powerterm LTC User's Guide Is Comprised of the Following Chapters
PowerTerm® LTC User's Guide Version 8.1 Ericom North America Ericom Europe Ericom International Ericom Software Inc. Ericom Software (UK) Ltd. Ericom Software Ltd. 231 Herbert Ave., Bldg. #4 11a Victoria Square 8 Hamarpeh Street Closter, NJ 07624 USA Droitwich, Worcestershire Har Hotzvim Technology Park Tel: +1 201 767 2210 WR9 8DE United Kingdom Jerusalem 91450 Israel Fax: +1 201 767 2205 Tel: +44 (0) 870 2000 176 Tel: +972 (0)2 591 1700 Toll Free: 1 888 769 7876 Fax: + 44 (0) 870 2000 179 Fax: +972 (0)2 571 4737 Email: [email protected] Email: [email protected] Email: [email protected] Important Notice Important Notice This guide is subject to the following conditions and restrictions: This User's Guide provides documentation for the PowerTerm® Series of products. Your specific PowerTerm LTC product might include only a portion of the features documented in this Guide. The proprietary information belonging to Ericom® Software is supplied solely for the purpose of assisting explicitly and properly authorized users of PowerTerm®. No part of its contents may be used for any other purpose, disclosed to any person or firm, or reproduced by any means, electronic and mechanical, without the express prior written permission of Ericom® Software. The text and graphics are for the purpose of illustration and reference only. The specifications on which they are based are subject to change without notice. The software described in this document is furnished under a license agreement. The software may be used or copied only in accordance with the terms of that agreement. -

MINIX.XINIM, Towards a Bi-Directional, Bi-Lingual UNIX Operating System
MINIX.XINIM, Towards a Bi-Directional, Bi-Lingual UNIX Operating System Gil Allon Daniel M. Berry Faculty of Computer Science Technion Haifa 32000 Israel Abstract This paper describes the design and construction of MINIX.XINIM, a bi-directional, bi-lingual version of MINIX, a mini-UNIX operating system. MINIX.XINIM is constructed from MINIX by modifying some of MINIX's device drivers so that they reverse all right-to-left text that passes through them. From this simple change, the entire kernel and all line-mode applications become bi-directional. While the version of MINIX.XINIM described here is for English and Hebrew, it can be easily used for any pair of left-to-right and right-to-left languages supported by the local input-output devices. ,MINIX.XINIM לקראת מערכת הפעלה UNIX דו-כיוונית ודו-שפתית גיל אלוo דניאל ברי הפקולטה למדעי המחשב הטכניוo חיפה 32000 ישראל תקvיר מאמר זה מתואר את תכנוo ובנית MINIX.XINIM, שהיא גירסה דו-כיוונית ודו-שפתית של MINIX, מערכת הפעלה מיני-MINIX.XINIM .UNIX נבנה מ-MINIX באמvעות שינוי של כמה מתוכנות הממשק להתקo באופo שהm הופכיm כל טקסט הנכתב מימיo לשמאל שעובר דרכm. מהשינוי הפשוט הזה, הגרעיo השלm וכל הישומיm במודת שורה נעשיm דו-כיוונית. למרת שגירסת ה-MINIX.XINIM המתוארת פה מיועדת לאנגלית-עברית, ניתo להשתמש בה בפשטות עבור כל זוג שפות הנכתבות האחת משמאל לימיo והאחרת מימיo לשמאל ושנתמכות על-ידי התקני קלט-פלט מקומיm. 1 MINIX.XINIM, fraxiooookפracmfoook Þcui}yook oפK Þcuoa sistfnf UNIX Cim~ Amoo Þaoiem~ M. ¾eri tfro}w oaul~פïalum~tft lon Sfwoioo Vakïa 32000 Iiraim~ Aoootaxi ,ostrofoif MINIX.XINIMפ rofltirocaoif iפ is}caftפNasto{a stat~ o ostrofo iiפ racmfoook i Þcui}yook cfrsii MINIX'a (nioi-UNIX'a). -

Lotus Domino R5.0 Enterprise Integration: Architecture and Products
Printed in the U.S.A. Lotus Domino R5.0 Enterprise Integration: Architecture and Products SG24-5593-00 Part No. CT6QUNA Lotus Domino R5.0R5.0 EnterEnterpriseprise Integration:Integration: ArArchitecturechitecture andand PrProductsoducts Søren Peter Nielsen, Theo Barkhuizen, Laurisa G. Maldonado, Robert Perron, Peter Sing International Technical Support Organization http://www.redbooks.ibm.com SG24-5593-00 22 SG24-5593-00 International Technical Support Organization Lotus Domino R5.0 Enterprise Integration: Architecture and Products July 1999 Take Note! Before using this information and the product it supports, be sure to read the general information in the Special Notices section at the back of this book. First Edition (July 1999) This edition applies to Lotus Domino Release 5.0 and Lotus Enterprise Integrator Release 3.0. Comments may be addressed to: IBM Corporation, International Technical Support Organization Dept. JN9B Building 045 Internal Zip 2834 11400 Burnet Road Austin, Texas 78758-3493 When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. © International Business Machines Corporation 1999. All rights reserved. Note to U.S. Government Users: Documentation related to restricted rights. Use, duplication or disclosure is subject to restrictions set forth in GSA ADP Schedule Contract with IBM Corp. Contents Preface ........................ ix Loading the Connector Classes ........17 The Team That Wrote This Redbook ....... x Coding a Program Using the Connector Classes ...............18 Comments Welcome ................. xi Additional Enterprise Integration Tools .....19 1 Overview .................... 1 Lotus Connector Toolkit .............19 Lotus Connectors ................... 2 ActiveX Data Object ...............20 Relational Database Management Systems . -

Ep 0779008 B1
Europäisches Patentamt *EP000779008B1* (19) European Patent Office Office européen des brevets (11) EP 0 779 008 B1 (12) EUROPEAN PATENT SPECIFICATION (45) Date of publication and mention (51) Int Cl.7: H04N 7/025, H04N 7/52 of the grant of the patent: 10.05.2000 Bulletin 2000/19 (86) International application number: PCT/IB96/00629 (21) Application number: 96917628.8 (87) International publication number: (22) Date of filing: 01.07.1996 WO 97/02700 (23.01.1997 Gazette 1997/05) (54) TRANSMISSION OF GRAPHIC IMAGES ÜBERTRAGUNG VON GRAPHISCHEN BILDERN TRANSMISSION D’IMAGES GRAPHIQUES (84) Designated Contracting States: (74) Representative: AT CH DE ES FR GB IT LI Schmitz, Herman Jan Renier et al INTERNATIONAAL OCTROOIBUREAU B.V., (30) Priority: 03.07.1995 EP 95201808 Prof. Holstlaan 6 25.08.1995 EP 95202304 5656 AA Eindhoven (NL) (43) Date of publication of application: (56) References cited: 18.06.1997 Bulletin 1997/25 EP-A- 0 624 979 WO-A-96/38008 US-A- 5 089 899 US-A- 5 422 674 (73) Proprietor: Koninklijke Philips Electronics N.V. 5621 BA Eindhoven (NL) • IEEE TRANSACTIONS ON CONSUMER ELECTRONICS LEI ET AL.: ’A new architecture (72) Inventors: for a TV graphics animation module’ vol. 39, no. • CLARK-SCHREYER, Veronika 4, November 1993, NEW YORK, US, pages 795 - A-1040 Vienna (AT) 800, XP000423066 • ERKINGER, Erwin A-1220 Vienna (AT) Note: Within nine months from the publication of the mention of the grant of the European patent, any person may give notice to the European Patent Office of opposition to the European patent granted.