An Evaluation of Windows-Based Computer Forensics Application Software Running on a Macintosh
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Niresh Mac Os X Mavericks
Niresh mac os x mavericks click here to download Hackintosh Mavericks with AMD & Intel Support - USB & ISO. Install Mac OS X Mavericks on PC with Niresh Mavericks aka Mavericks Zone, to Install this you don't need access to a Mac. Thanks for the distro Niresh!. May 23, Download Niresh Mac OSX Mavericks DVD ISO free standalone offline setup for AMD and Intel Computers. Niresh Mac OSX Mavericks Zone is a powerful operating system with all the latest enhancements and fixes with better compatibility features. Download Niresh Mac OSX Mavericks. Installing Mac OS X on PC is not easy as installing windows or linux, because mac First you must download the Niresh's Mavericks USB Version from the link. Jan 3, If you're interested in running Mac OS X, but you don't want to pay ridiculous prices for a normal Mac, then a Hackintosh just might be for you. Hello. I want to instal Mac OS X Maverick and I find the nice image from Niresh on the internet. Can my PC run this mac without problems?. Hackintosh = A PC that has Mac installed on it. - Macintosh = A Mac PC. - Mac OS X Mavericks = The Mac operating system. - Niresh = A guy who hacks Mac. Nov 7, If you have installed Niresh Version of Mac OS X Mavericks system in your virtual machine software like VirtualBox, it may be really confused. Jul 11, With more than new features, OS X Mavericks brings Maps and iBooks to the Mac, introduces Finder Tabs and Tags, enhances. How to install Niresh Mavericks () on any PC!! IF your PC supports these, then you can install MAC OS X on your PC. -

Ios App Reverse Engineering
snakeninny, hangcom Translated by Ziqi Wu, 0xBBC, tianqing and Fei Cheng iOS App Reverse Engineering Table of Contents Recommendation ..................................................................................................................................................... 1 Preface ....................................................................................................................................................................... 2 Foreword ................................................................................................................................................................... 7 Part 1 Concepts ....................................................................................................................................................... 12 Chapter 1 Introduction to iOS reverse engineering ............................................................................................. 13 1.1 Prerequisites of iOS reverse engineering .......................................................................................................... 13 1.2 What does iOS reverse engineering do ............................................................................................................ 13 1.2.1 Security related iOS reverse engineering ...................................................................................................... 16 1.2.2 Development related iOS reverse engineering ............................................................................................ -
Download Mac Os Sierra Iso After Macos Sierra Disappears from the Mac App Store
download mac os sierra iso after macOS Sierra disappears from the Mac App Store. Previously, whenever a major new version of macOS (or OS X) would launch on the Mac App Store, the previous version would still be available for download in the Purchased tab on the store. But things have changed this year. Now that macOS High Sierra has launched, its predecessor, Sierra, is nowhere to be found. It appears that updates for macOS are no longer tied to your Apple ID, which explains why Sierra and High Sierra don't show up in your Purchased tab. However, Sierra is also missing when you search for it in the Mac App Store. As Stephen Hackett of 512 Pixels notes: This means there's no easy way for someone to install macOS Sierra at this point. If your Mac came with 10.12.4 or greater, you can reinstall that version from Apple's servers, but going back from High Sierra isn't doable unless you've got a copy of Sierra laying around. As Hackett goes on to note, it's likely that at least part of this move is motivated by Apple's desire for Macs running Sierra to upgrade to High Sierra, which offers many refinements of the Sierra experience. It's also worth noting that, at least for Macs with internal SSDs, downgrading from High Sierra would be more difficult thanks to the APFS transition. Question: Q: Where can I download OSX Sierra DMG/ISO? Mac wont start! I upgraded my Macbook Pro OS to Sierra on Thursday Friday morning and its been a disaster. -

Debugger for Hackintosh
Debug for bug: Crack and Hack Apple Core by itself Lilang Wu, Moony Li About US ❖ Lilang Wu ❖ 4 years security experience ❖ macOS/iOS malware/vulnerability ❖ Fuzzing project ❖ BH USA 2018, BH EU 2018, HITB, CodeBlue About US ❖ Moony Li ❖ 9 years security experience ❖ macOS/iOS/Android malware/ vulnerability ❖ 0Day/NDay hunting/exploit ❖ BH EU 2015, BH USA2018, BH EU 2018, BH ASIA 2018, HITB, CodeBlue Agenda ❖ Kernel Debugger Overview ❖ The Introduction of LLDBFuzzer ❖ Attack Surfaces on Graphic Extensions ❖ Practice and Demo ❖ Vulnerabilities Found ❖ Implement a Debugger for Hackintosh ❖ Conclusion Agenda ❖ Kernel Debugger Overview ❖ The Introduction of LLDBFuzzer ❖ Attack Surfaces on Graphic Extensions ❖ Practice and Demo ❖ Vulnerabilities Found ❖ Implement a Debugger for Hackintosh ❖ Conclusion Kernel Debugger Overview ❖ KDP: a remote debugger protocol ❖ Active by change boot-args ❖ Only a single IOKernelDebugger can be activated at a given time ❖ Ethernet Debugging, Firewire Debugging, Serial Debugging Kernel Debugging Overview NetworkingFamily.kext Ethernet Driver BSD Kernel receivePacket kdp_poll Ethernet Debugger Driver Loop sendPacket kdp_reply Debugger world Kernel smp_init() kdp_i386_trap() handle_debugger_trap() BSD Kernel Bootstrap kernel_thread_creat() kdp_raise_exception() kdp_init() kdp_handler() kdp_register_send_receive() kdp_poll() kdp_reply() receive = kdp_en_recv_pkt kdp_receive_data() kdp_send_data() send = kdp_en_send_pkt Kdp Packet Process kdp.c IONetworkingFamily.kext IONetworkController:: IOKernelDebugger IOKernelDebugger -

Computer Requirements (Kenzie Academy)
KENZIE ACADEMY COMPUTER REQUIREMENTS It’s going to be the #1 tool in your career. You may use it more than anything in your life (other than a bed). So get the best one you can, treat it well, and pay for the warranty if you can afford it. Note: If the links in this document do not work for you, then download and open the PDF. Simple PDF previewers, such as those running on websites in your browser, don’t support the advanced features in this PDF. Operating Systems Hardware Models Minimum Specs macOS Catalina (10.15.x) or newer Approved models only Memory: 8 GB+ (no Hackintosh) Processor: ”Intel” or “AMD” only(!) Storage: 10 GB+ of free space Ubuntu 18.04.x or newer Approved models only (avoid dual-boot) (avoid VMs) Other: Headset, webcam, Windows 10 Pro or Home Any model with a physical second monitor, etc. keyboard Note: Chromebooks, Android devices, and iOS devices cannot run the software you will need. Some Good Advice Computers: “You get what you pay for!” Generally, when it comes to computers, you do get what you pay for – although sometimes you are paying, in part, for the aesthetics, build-quality, or the brand. But as a rule-of-thumb, if a computer is inexpensive, it is not likely to last long. So weigh your options: you don’t want your computer breaking down during your time in the program, if you can help it. If you’re choosing Ubuntu, install it well before Orientation Day! Have Ubuntu installed before Orientation Day. -

Interface Ios for Control of an Unmanned Helicopter in ROS
CZECH TECHNICAL UNIVERSITY IN PRAGUE Faculty of Electrical Engineering BACHELOR'S THESIS Filip Bulander Interface iOS for control of an unmanned helicopter in ROS Department of Control Engineering Thesis supervisor: Dr. Martin Saska BACHELOR‘S THESIS ASSIGNMENT I. Personal and study details Student's name: Bulander Filip Personal ID number: 456876 Faculty / Institute: Faculty of Electrical Engineering Department / Institute: Department of Control Engineering Study program: Cybernetics and Robotics Branch of study: Systems and Control II. Bachelor’s thesis details Bachelor’s thesis title in English: Interface iOS for control of an unmanned helicopter in ROS Bachelor’s thesis title in Czech: Rozhraní iOS pro řízení bezpilotní helikoptéry v ROSu Guidelines: The goal of the thesis is to design, implement, and experimentally verify in Gazebo simulator and real experiments an application in iOS for control an Unmanned Aerial Vehicle (UAV) equipped by onboard Linux PC with Robot Operating System (ROS). 1. Implement an interface in iOS to operate by iPhones a UAV equipped by Linux onboard computer with ROS [1,2]. 2. Design and implement an iOS application for basic UAV control by iPhones (joystick, setting GPS points, displaying a UAV telemetry - position estimation, battery status, data from selected onboard sensors). 3. Verify the application in Gazebo and with a real platform in outdoor conditions. 4. Design and implement an iOS application to setup and control an inspection/monitoring task. A user submits a sequence of points of snapshots and camera orientations in these points and the application returns a collision-free path in a known map. The user can edit the obtained path and confirm its execution. -

Mac Os High Sierra App Store Background Download Question: Q: How to Download Full Installer of High Sierra
mac os high sierra app store background download Question: Q: How to Download full installer of High sierra. i have Purchased macbook pro mid 2014 13" today. it currently have Mac Os X Yosemite .I want to download Mac Os High Sierra . When ever i tried to download it from app store, it just download a 19.9MB file instead of 4.80GB. i have 4 MacBooks. i want to download full installer and then make a bootable USB from it to update my all 4 MacBooks. what should i do? how can i download full installer . MacBook Pro with Retina display, OS X Yosemite (10.10.5), Macbook Pro Mid 2014 13" Download the New macOS High Sierra 10.13 Wallpaper for your Mac. Apart from the amazing hardware announcements at WWDC 2017, Apple unveiled a new operating system for Mac called macOS High Sierra. The new operating system comes with many performance improvements under-the-hood and new features, such as the Apple File System, support for HVEC format, better user privacy in Safari, and much more. As is the case with every new iteration of macOS, a new wallpaper was also added to macOS 10.13 that looks beautiful. Below is a preview of the macOS High Sierra wallpaper. To download it, click on the link below it and save to your desktop. The first beta version of macOS can be downloaded by developers via the software update mechanism in the Mac App Store or through the Apple Developer Center. The public beta will be released by the end of June, while the official release will be made later this year as a free software update from the MacApp Store. -

Table of Contents
Table of Contents FireWolf OS X PE 9 Manual Preface 1.1 Chapter 1 Introduction 1.2 Chapter 2 Preparation 1.3 Restore the disk image 1.3.1 Boot FireWolf OS X PE 1.3.2 Chapter 3 Start to use 1.4 First View 1.4.1 Toolbar 1.4.2 Main Panel 1.4.3 Rocket Launcher 1.4.4 Applications Management 1.4.5 Importing Applications (Basic) 1.4.5.1 Importing Applications (Advanced) 1.4.5.2 Exporting Applications and Others 1.4.5.3 Chapter 4 System Maintenance 1.5 Chapter 5 1.6 Mount ESP Partitions 1.6.1 Delete Files in Path Finder 1.6.2 Show Invisible Files 1.6.3 Downloads Thankyou 2.1 1 Preface FireWolf OS X PE 9 All-in-one Manual English Version Version: 1.0 Date: 2018.05.31 The PDF version of this manual is generated by GitBook automatically. License: Attribution-NonCommercial 4.0 International License 2 Chapter 1 Introduction Chapter 1 Introduction >> What is FireWolf OS X PE? FireWolf OS X PE, also known as Mac PE, is an enhanced macOS Recovery, providing native support for accessing files on HFS and APFS formatted partitions. Applications and maintenance kits embedded in PE provide you a chance to transfer personal data, restoring from backups, repairing disk permissions and more when your main system won't boot. FireWolf OS X PE supports both genuine Mac and Hackintosh systems. >> Is it safe to use? Yes, it is safe! It does not include any virus, malicious softwares and backdoors. -

Mac Os 10.8 for Intel Pc
Mac os 10.8 for intel pc Installing or updating to the latest version of OS X on a PC is simpler than ever. This guide Choose Mac App Store Mountain Lion - UniBeast: Install OS X Mavericks on Any Supported. I don't know why people like to install Mac OS X on their PC. A lots of people ask How to Install it on Intel PC. When Apple moved from Power. Hackintosh install os x mountain lion on any computer including amd cpus. install and use the best operating system in the world. Mountain Lion Installation Guide. In this video, my successful installation of Mac OS X Mountain Lion on my Intel Dual Core-based PC. This Video will help you to Install Mac OS X on your Computer. Please visit our Blog to get all software. Install Mountain Lion OSX on INTEL pc windows (HD with Voice) to install Mountain Lion OSX (MAC) on a. It is final bootable OS X Mountain Lion InstallESD. app ne mac lion dmg image file kis software se boot ke hai intel pc pe plz help. macOS High Sierra and OS X Sierra Hackintosh instructions, tutorials, Installation guides for OS X Mavericks (), OS X Mountain Lion (), OS X Lion . can't install Windows on any old PC and expect it to work like OS X does on a Mac. EVGA, Gigabyte, Intel and MSI "aware" of Mac OS X. In turn, this is promised to. Either way, you can install Mountain Lion on your Intel-based PC in a few easy You'll need to format the drive with one partition as Mac OS How To: Create a Bootable Install DVD or USB Drive of OS X Mountain Lion. -

Auf Einer Festplatte: Windows Und Macos Im Dualboot
Auf einer Festplatte: Windows und macOS im Dualboot Diese Anleitung ist für Ozmosis geschrieben sollte aber auch mit Clover und Konsorten funktionieren was ich aber selber nicht testen konnte. Das generelle Prinzip ist auf jeden Bootloader übertragbar. Was man braucht: Eine laufende Installation von OS X auf der Festplatte für das DualbootSystem. Bei einem DualBoot System ist es wichtig, dass erst MacOS und dann erst Windows etc installiert wird. Zudem braucht man eine groß genuge Festplatte, am besten das Festplattendienstprogramm von YOSEMITE (zb von hier für ElCapitan oder von hier für Sierra ) und einen Windows 10 InstallStick (kann auch mit Boot Camp erstellt werden, indem man vorher eine Windows 10 ISO runterlädt, dann den Boot Camp Assistant startet und den Assistenten durchläuft. Dabei formatiert Bootcamp im ersten Schritt den gewählten USB Stick, dann wird Windows darauf kopiert, das ganze Bootbar gemacht und danach noch Zusatz-Treiber für MacBooks etc von Apple heruntergeladen und auf den Stick gepackt. Da du letztere Treiber nicht brauchst, kannst du einfach, wenn das herunterladen der Zusätzlichen Dateien oben in der Fortschrittsleiste von Boot Camp angezeigt wird, unten auf "Abbrechen" klicken, der Stick funktioniert dann trotzdem) Jetzt wird zur Sicherheit bitte erstmal ein Backup aller Daten gemacht denn es geht jetzt ans Formatieren wobei schon kleinste Fehler ALLES löschen können! Als nächstes geht man auf das Festplattendienstprogramm und wählt die zu partitionierende Festplatte aus. Sie hat derzeit normal nur eine Partition. Man geht auf den Tab "Partition" und schiebt jetzt einfach die bereits vorhandene Partition zusammen, sodass komplett unpartitionierter, freier Platz entsteht mit so viel Speicherplatz wie man eben für Windows haben will. -
Everything You Need to Get Started with Installing Macos on Virtualbox
Mac Os Snow Leopard For Oracle Virtualbox Oracle Virtualbox Mac Os Running Snow Leopard On Virtualbox Mac Os Snow Leopard For Oracle Virtualbox Download Mac Os Snow Leopard Download Mac Os Snow Leopard Virtualbox Mac Os Snow Leopard For Oracle Virtualbox 7 Mac Os Snow Leopard For Oracle Virtualbox 10 I almost pulled my hair out trying to install Snow Leopard into Virtual Box, but with a few minor tweaks I finally made it happen. I hope this helps. Note: This is a Retail installation guide, hence little more tricky.If you don’t mind an osx86 distro inside virtualbox and want ease of installation, tryout Install Mac OS X Hackintosh in VirtualBox Snow Leopard instead. Before you begin, make sure you have enough CPU. Guru Meditation while booting Mac OS X 10.6 Snow Leopard. Reported by: nvittoa03: Owned by: Component: other: Version: VirtualBox 5.2.18: Keywords: Cc: Guest type: OSX Server: Host type: Windows: Description I just booted my virtual PC, but then it. Before we install OS X, we’ll need to set up VirtualBox so the OS X install disc can boot correctly. Here’s what you need to do: Step 1: Launch VirtualBox and click the New button. Give your new virtual machine a name (I just called it “Mac OS X”) and set the operating system to “Mac OS X Server (64-bit)”. Windows, macOS – which one do you want to use today? On a traditional setup, you’re stuck with one or the other. But with virtual box, you actually have macOS on a Windows PC. -
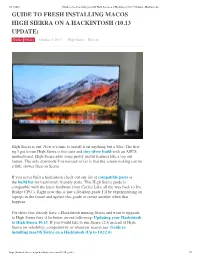
Guide to Fresh Installing Macos High
9/14/2018 Guide to fresh installing macOS High Sierra on a Hackintosh (10.13 Update) - Hackintosher GUIDE TO FRESH INSTALLING MACOS HIGH SIERRA ON A HACKINTOSH (10.13 UPDATE) Guides Sticky October 5, 2017 High Sierra, How-to High Sierra is out. Now it’s time to install it on anything but a Mac. The first rig I got to run High Sierra is this cute and tiny silver build with an ASUS motherboard. High Sierra adds some pretty useful features like a log out button. The only downside I’ve noticed so far is that the screen waking can be a little slower then on Sierra. If you never built a hackintosh check out our list of compatible parts or the build list for hackintosh friendly parts. This High Sierra guide is compatible with the latest hardware from Coffee Lake all the way back to Ivy Bridge CPU’s. Right now this is just a Desktop guide I’ll be experimenting on laptops in the future and update this guide or create another when that happens. For those that already have a Hackintosh running Sierra and want to upgrade to High Sierra they’d be better served following: Updating your Hackintosh to High Sierra 10.13. If you would like to run Sierra 12.6 instead of High Sierra for reliability, compatibility or whatever reason see: Guide to installing macOS Sierra on a Hackintosh (Up to 10.12.6) https://hackintosher.com/guides/high-sierra-install-full-guide/ 1/7 9/14/2018 Guide to fresh installing macOS High Sierra on a Hackintosh (10.13 Update) - Hackintosher High Sierra Hackintosh Install Full Guide This is a full install guide that will walk you through clean installing High Sierra on a custom PC.