Uniform Resource Identifier (URI)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Xincluding Plain-Text Fragments for Symmetry and Profit Piotr Bański, University of Warsaw, [email protected]
XIncluding plain-text fragments for symmetry and profit Piotr Bański, University of Warsaw, [email protected] <xi:include href=”resource.xml” parse=”text|xml” Summary xpointer=”fragment_identifier” /> XML for the annotation of images, audio or video is by necessity of the stand-off kind: the annotations are virtually anchored to the parse=“xml” parse=“text” binary stream (typically by x,y coordinates or time offsets). Work on language resource annotation has extended this approach to plain text, where annotations are anchored by character offsets. This is referred to as extreme stand-off markup. No generic XML tools or standards support it, but... they could, fairly easily. inclusion of inclusion of inclusion of inclusion of Rationale the entire the entire a fragment a fragment ISO Language Annotation Framework (e.g. Ide & Romary, 2007) re- XML text of an XML of a text commends that data be kept as read-only plain text, with one or mo- resource resource resource resource re layers of XML annotation identifying individual spans of charac- ters and adding metadata to them (identifying e.g. segments of va- rious levels of granularity, parts of speech, syntactic or discourse @xpointer present functions, etc.) no @xpointer However, the only way to handle this (as evidenced by the American National Corpus), is to use in-house tools working on correspon- dence semantics for hyperlinks (see Bański, 2010, for terminology What makes it impossible right now? and more remarks). 1. XInclude Ban: XInclude Rec, 3.1: “The xpointer attribute must not be present when parse="text".” But character streams can do better! Because text is what XML is built out of and what it contains, instead of correspondence 2. -

Bibliography of Erik Wilde
dretbiblio dretbiblio Erik Wilde's Bibliography References [1] AFIPS Fall Joint Computer Conference, San Francisco, California, December 1968. [2] Seventeenth IEEE Conference on Computer Communication Networks, Washington, D.C., 1978. [3] ACM SIGACT-SIGMOD Symposium on Principles of Database Systems, Los Angeles, Cal- ifornia, March 1982. ACM Press. [4] First Conference on Computer-Supported Cooperative Work, 1986. [5] 1987 ACM Conference on Hypertext, Chapel Hill, North Carolina, November 1987. ACM Press. [6] 18th IEEE International Symposium on Fault-Tolerant Computing, Tokyo, Japan, 1988. IEEE Computer Society Press. [7] Conference on Computer-Supported Cooperative Work, Portland, Oregon, 1988. ACM Press. [8] Conference on Office Information Systems, Palo Alto, California, March 1988. [9] 1989 ACM Conference on Hypertext, Pittsburgh, Pennsylvania, November 1989. ACM Press. [10] UNIX | The Legend Evolves. Summer 1990 UKUUG Conference, Buntingford, UK, 1990. UKUUG. [11] Fourth ACM Symposium on User Interface Software and Technology, Hilton Head, South Carolina, November 1991. [12] GLOBECOM'91 Conference, Phoenix, Arizona, 1991. IEEE Computer Society Press. [13] IEEE INFOCOM '91 Conference on Computer Communications, Bal Harbour, Florida, 1991. IEEE Computer Society Press. [14] IEEE International Conference on Communications, Denver, Colorado, June 1991. [15] International Workshop on CSCW, Berlin, Germany, April 1991. [16] Third ACM Conference on Hypertext, San Antonio, Texas, December 1991. ACM Press. [17] 11th Symposium on Reliable Distributed Systems, Houston, Texas, 1992. IEEE Computer Society Press. [18] 3rd Joint European Networking Conference, Innsbruck, Austria, May 1992. [19] Fourth ACM Conference on Hypertext, Milano, Italy, November 1992. ACM Press. [20] GLOBECOM'92 Conference, Orlando, Florida, December 1992. IEEE Computer Society Press. http://github.com/dret/biblio (August 29, 2018) 1 dretbiblio [21] IEEE INFOCOM '92 Conference on Computer Communications, Florence, Italy, 1992. -

W3C Working Draft: Scalable Vector
next contents properties index Scalable Vector Graphics (SVG) 1.0 Specification W3C Working Draft 03 March 2000 This version: http://www.w3.org/TR/2000/03/WD-SVG-20000303 (Available as: PDF, zip archive of HTML) Previous public version: http://www.w3.org/TR/1999/WD-SVG-19991203/ Latest public version: http://www.w3.org/TR/SVG/ Editor: Jon Ferraiolo <[email protected]> Authors: See author list Copyright ©1998, 1999, 2000 W3C® (MIT, INRIA, Keio), All Rights Reserved. W3C liability, trademark, document use and software licensing rules apply. Abstract This specification defines the features and syntax for Scalable Vector Graphics (SVG), a language for describing two-dimensional vector and mixed vector/raster graphics in XML. Status of this document This document is a public review draft version of the SVG specification. This working draft attempts to address review comments that were received during the initial Last Call period, which started 12 August 1999, and also incorporates other modifications resulting from continuing collaboration with other working groups and continuing work within the SVG working group. With the publication of this draft, the SVG specification enters a second "Last Call". The second Last Call period will end on 31 March, 2000. The SVG specification is going through a second Last Call review process to provide the public and other working groups an opportunity to review the changes to the specification since the initial Last Call period. A complete list of all changes since the initial Last Call version of the specification is available in Appendix L: Change History. Last call comments should be sent to [email protected]. -

Understanding JSON Schema Release 2020-12
Understanding JSON Schema Release 2020-12 Michael Droettboom, et al Space Telescope Science Institute Sep 14, 2021 Contents 1 Conventions used in this book3 1.1 Language-specific notes.........................................3 1.2 Draft-specific notes............................................4 1.3 Examples.................................................4 2 What is a schema? 7 3 The basics 11 3.1 Hello, World!............................................... 11 3.2 The type keyword............................................ 12 3.3 Declaring a JSON Schema........................................ 13 3.4 Declaring a unique identifier....................................... 13 4 JSON Schema Reference 15 4.1 Type-specific keywords......................................... 15 4.2 string................................................... 17 4.2.1 Length.............................................. 19 4.2.2 Regular Expressions...................................... 19 4.2.3 Format.............................................. 20 4.3 Regular Expressions........................................... 22 4.3.1 Example............................................. 23 4.4 Numeric types.............................................. 23 4.4.1 integer.............................................. 24 4.4.2 number............................................. 25 4.4.3 Multiples............................................ 26 4.4.4 Range.............................................. 26 4.5 object................................................... 29 4.5.1 Properties........................................... -

Bookings of Westin Diplomat Bookings
RESTful Web Applications with Spring 3.0 Arjen Poutsma Senior Software Engineer SpringSource Speaker’s qualifications • Fifteen years of experience in Enterprise Software Development • Six years of Web service experience • Development lead of Spring Web Services • Working on Spring 3.0 • Contributor to various Open Source frameworks: (XFire, Axis2, NEO, ...) SpringSource Confidential. Do not distribute without express permission Overview • RESTful URLs • URI templates • Content negotiation • HTTP method conversion • ETag support SpringSource Confidential. Do not distribute without express permission RESTful URLs Resources • URLs are unique identifiers for Resources • Typically nouns • Customer • Orders • Shopping cart URLs [scheme:][//authority][path][?query][#fragment] http://www.springsource.com https://mybank.com http://www.google.com/search?q=arjen %20poutsma http://java.sun.com/j2se/1.4.2/docs/api/java/lang/ String.html#indexOf(int) SpringSource Confidential. Do not distribute without express permission Paths • Represents hierarchy • Represents value for consumers • Collections on higher levels SpringSource Confidential. Do not distribute without express permission Example Path Description /hotels List of all hotels /hotels/westindiplomat Details of Westin Diplomat /hotels/westindiplomat/ List of bookings of Westin Diplomat bookings /hotels/westindiplomat/ Individual booking bookings/42584 No Hierarchy? Path Description maps/24.9195,17.821 Commas maps/24.9195;17.821 Semicolons Query Variables • Input for algorithms • Get ignored by proxies -
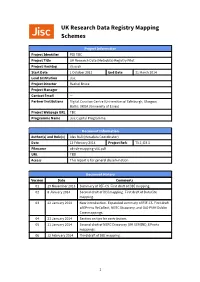
UK Research Data Registry Mapping Schemes
UK Research Data Registry Mapping Schemes Project Information Project Identifier PID TBC Project Title UK Research Data (Metadata) Registry Pilot Project Hashtag #jiscrdr Start Date 1 October 2013 End Date 31 March 2014 Lead Institution Jisc Project Director Rachel Bruce Project Manager — Contact Email — Partner Institutions Digital Curation Centre (Universities of Edinburgh, Glasgow, Bath); UKDA (University of Essex) Project Webpage URL TBC Programme Name Jisc Capital Programme Document Information Author(s) and Role(s) Alex Ball (Metadata Coordinator) Date 12 February 2014 Project Refs T3.1; D3.1 Filename uk-rdr-mapping-v06.pdf URL TBD Access This report is for general dissemination Document History Version Date Comments 01 29 November 2013 Summary of RIF-CS. First draft of DDI mapping. 02 8 January 2014 Second draft of DDI mapping. First draft of DataCite mapping. 03 22 January 2014 New introduction. Expanded summary of RIF-CS. First draft of EPrints ReCollect, NERC Discovery, and OAI-PMH Dublin Core mappings. 04 23 January 2014 Section on tips for contributors. 05 31 January 2014 Second draft of NERC Discovery (UK GEMINI), EPrints mappings. 06 12 February 2014 Third draft of DDI mapping. 1 Contents 1 Introduction 3 1.1 Typographical conventions . 3 2 RIF-CS 4 2.1 Elements . 4 2.2 Controlled vocabularies . 8 3 Internally managed RIF-CS elements 20 4 Mapping from DDI to RIF-CS 21 4.1 Related Objects . 22 5 Mapping from UK GEMINI 2 to RIF-CS 24 5.1 Related Objects . 26 6 Mapping from DataCite to RIF-CS 27 6.1 Related Objects . -

Gemini and NTS Exit Reform API Usage Guidelines
Gemini and NTS Exit Reform API Usage Guidelines ~ 1 ~ Table of Contents 1. Introduction ............................................................................................................................................6 1.1. API Technology Overview ....................................................................................................................6 2. API Client Development Guidelines .....................................................................................................8 2.1. HTTPS and SSL ...................................................................................................................................9 2.2. Authentication and Authorization ...................................................................................................... 10 2.3. Maintaining the Session .................................................................................................................... 10 2.4. Authentication / Loss of Session / Authorization Failures ................................................................. 10 2.5. Request a Compressed Response to your API Client ...................................................................... 11 3. API Configuration Details ................................................................................................................... 14 3.1. API Technology Overview ................................................................................................................. 14 3.2. Network Requirements ..................................................................................................................... -

Iso/Iec 21000-17:2006(E)
This is a preview - click here to buy the full publication INTERNATIONAL ISO/IEC STANDARD 21000-17 First edition 2006-09-15 Information technology — Multimedia framework (MPEG-21) — Part 17: Fragment Identification of MPEG Resources Technologies de l'information — Cadre multimédia (MPEG-21) — Partie 17: Identification de fragments de ressources MPEG Reference number ISO/IEC 21000-17:2006(E) © ISO/IEC 2006 ISO/IEC 21000-17:2006(E) This is a preview - click here to buy the full publication PDF disclaimer This PDF file may contain embedded typefaces. In accordance with Adobe's licensing policy, this file may be printed or viewed but shall not be edited unless the typefaces which are embedded are licensed to and installed on the computer performing the editing. In downloading this file, parties accept therein the responsibility of not infringing Adobe's licensing policy. The ISO Central Secretariat accepts no liability in this area. Adobe is a trademark of Adobe Systems Incorporated. Details of the software products used to create this PDF file can be found in the General Info relative to the file; the PDF-creation parameters were optimized for printing. Every care has been taken to ensure that the file is suitable for use by ISO member bodies. In the unlikely event that a problem relating to it is found, please inform the Central Secretariat at the address given below. © ISO/IEC 2006 All rights reserved. Unless otherwise specified, no part of this publication may be reproduced or utilized in any form or by any means, electronic or mechanical, including photocopying and microfilm, without permission in writing from either ISO at the address below or ISO's member body in the country of the requester. -

Network Working Group H. Birkholz Internet-Draft Fraunhofer SIT Intended Status: Informational C
Network Working Group H. Birkholz Internet-Draft Fraunhofer SIT Intended status: Informational C. Vigano Expires: January 4, 2018 Universitaet Bremen C. Bormann Universitaet Bremen TZI July 03, 2017 Concise data definition language (CDDL): a notational convention to express CBOR data structures draft-greevenbosch-appsawg-cbor-cddl-11 Abstract This document proposes a notational convention to express CBOR data structures (RFC 7049). Its main goal is to provide an easy and unambiguous way to express structures for protocol messages and data formats that use CBOR. Status of This Memo This Internet-Draft is submitted in full conformance with the provisions of BCP 78 and BCP 79. Internet-Drafts are working documents of the Internet Engineering Task Force (IETF). Note that other groups may also distribute working documents as Internet-Drafts. The list of current Internet- Drafts is at http://datatracker.ietf.org/drafts/current/. Internet-Drafts are draft documents valid for a maximum of six months and may be updated, replaced, or obsoleted by other documents at any time. It is inappropriate to use Internet-Drafts as reference material or to cite them other than as "work in progress." This Internet-Draft will expire on January 4, 2018. Copyright Notice Copyright (c) 2017 IETF Trust and the persons identified as the document authors. All rights reserved. This document is subject to BCP 78 and the IETF Trust’s Legal Provisions Relating to IETF Documents (http://trustee.ietf.org/license-info) in effect on the date of publication of this document. Please review these documents carefully, as they describe your rights and restrictions with respect to this document. -

HTTPAPI S. Dalal Internet-Draft Intended Status: Standards Track E
HTTPAPI S. Dalal Internet-Draft Intended status: Standards Track E. Wilde Expires: January 11, 2022 July 10, 2021 The Deprecation HTTP Header Field draft-ietf-httpapi-deprecation-header-02 Abstract The HTTP Deprecation Response Header Field can be used to signal to consumers of a URI-identified resource that the resource has been deprecated. Additionally, the deprecation link relation can be used to link to a resource that provides additional context for the deprecation, and possibly ways in which clients can find a replacement for the deprecated resource. Status of This Memo This Internet-Draft is submitted in full conformance with the provisions of BCP 78 and BCP 79. Internet-Drafts are working documents of the Internet Engineering Task Force (IETF). Note that other groups may also distribute working documents as Internet-Drafts. The list of current Internet- Drafts is at https://datatracker.ietf.org/drafts/current/. Internet-Drafts are draft documents valid for a maximum of six months and may be updated, replaced, or obsoleted by other documents at any time. It is inappropriate to use Internet-Drafts as reference material or to cite them other than as "work in progress." This Internet-Draft will expire on January 11, 2022. Copyright Notice Copyright (c) 2021 IETF Trust and the persons identified as the document authors. All rights reserved. This document is subject to BCP 78 and the IETF Trust’s Legal Provisions Relating to IETF Documents (https://trustee.ietf.org/license-info) in effect on the date of publication of this document. Please review these documents carefully, as they describe your rights and restrictions with respect to this document. -

SARIF) Version 2.1.0 Committee Specification Draft 01 / Public Review Draft 01 27 May23 July 2019
Static Analysis Results Interchange Format (SARIF) Version 2.1.0 Committee Specification Draft 01 / Public Review Draft 01 27 May23 July 2019 This version: https://docs.oasis-open.org/sarif/sarif/v2.1.0/csprd01/sarif-v2.1.0-csprd01.docx (Authoritative) https://docs.oasis-open.org/sarif/sarif/v2.1.0/csprd01/sarif-v2.1.0-csprd01.html https://docs.oasis-open.org/sarif/sarif/v2.1.0/csprd01/sarif-v2.1.0-csprd01.pdf https://docs.oasis-open.org/sarif/sarif/v2.1.0/cs01/sarif-v2.1.0-cs01.docx (Authoritative) https://docs.oasis-open.org/sarif/sarif/v2.1.0/cs01/sarif-v2.1.0-cs01.html https://docs.oasis-open.org/sarif/sarif/v2.1.0/cs01/sarif-v2.1.0-cs01.pdf Previous version: N/A Latest version: https://docs.oasis-open.org/sarif/sarif/v2.1.0/sarif-v2.1.0.docx (Authoritative) https://docs.oasis-open.org/sarif/sarif/v2.1.0/sarif-v2.1.0.html https://docs.oasis-open.org/sarif/sarif/v2.1.0/sarif-v2.1.0.pdf Technical Committee: OASIS Static Analysis Results Interchange Format (SARIF) TC Chairs: David Keaton ([email protected]), Individual Member Luke Cartey ([email protected]), Semmle Editors: Michael C. Fanning ([email protected]), Microsoft Laurence J. Golding ([email protected]), Microsoft Additional artifacts: This prose specification is one component of a Work Product that also includes: • JSON schemas: https://docs.oasis-open.org/sarif/sarif/v2.1.0/csprd01/schemas/ Related work: This specification replaces or supersedes: • Static Analysis Results Interchange Format (SARIF) Version 2.0. -

Secure Public Instant Messaging
Secure Public Instant Messaging By Mohammad Abdul Mannan A thesis submitted to the Faculty of Graduate Studies and Research in partial fulfilment of the requirements for the degree of Master of Computer Science Ottawa-Carleton Institute for Computer Science School of Computer Science Carleton University Ottawa, Ontario, Canada August 2005 ©Copyright Mohammad Abdul Mannan, 2005 Reproduced with permission of the copyright owner. Further reproduction prohibited without permission. Library and Bibliotheque et 1*1 Archives Canada Archives Canada Published Heritage Direction du Branch Patrimoine de I'edition 395 Wellington Street 395, rue Wellington Ottawa ON K1A 0N4 Ottawa ON K1A 0N4 Canada Canada Your file Votre reference ISBN: 0-494-10118-0 Our file Notre reference ISBN: 0-494-10118-0 NOTICE: AVIS: The author has granted a non L'auteur a accorde une licence non exclusive exclusive license allowing Library permettant a la Bibliotheque et Archives and Archives Canada to reproduce,Canada de reproduire, publier, archiver, publish, archive, preserve, conserve,sauvegarder, conserver, transmettre au public communicate to the public by par telecommunication ou par I'lnternet, preter, telecommunication or on the Internet,distribuer et vendre des theses partout dans loan, distribute and sell theses le monde, a des fins commerciales ou autres, worldwide, for commercial or non sur support microforme, papier, electronique commercial purposes, in microform,et/ou autres formats. paper, electronic and/or any other formats. The author retains copyright L'auteur conserve la propriete du droit d'auteur ownership and moral rights in et des droits moraux qui protege cette these. this thesis. Neither the thesis Ni la these ni des extraits substantiels de nor substantial extracts from it celle-ci ne doivent etre imprimes ou autrement may be printed or otherwise reproduits sans son autorisation.