Foundations of Information System in Business
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Framework for National Information Infrastructure Services
NISTIR 5478 Framework for National Information Infrastructure Services U.S. DEPARTMENT OF COMMERCE Technology Administration National Institute of Standards and Technology Computer Systems Laboratory Gaithersburg, MD 20899 July 1994 QC 100 NIST .U56 // 5478 1994 NISTIR 5478 Framework for National Information Infrastructure Services U.S. DEPARTMENT OF COMMERCE Technology Administration National Institute of Standards and Technology Computer Systems Laboratory Gaithersburg, MD 20899 July 1994 U.S. DEPARTMENT OF COMMERCE Ronald H. Brown, Secretary TECHNOLOGY ADMINISTRATION Mary L. Good, Under Secretary for Technology NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY Aratl Prabhakar, Director ACKNOWLEDGMENTS This report is the result of the efforts of many individuals who contributed to its development, revision, and preparation for publication. The principal authors of the report were: William Majurski and Wayne McCoy of the National Institute of Standards and Technology (NIST), James Pottmeyer of the Defense Information Systems Agency (DISA), Wayne Jansen, Richard Schneeman, David Cypher and Oscar Farah of NIST. In addition, material for the report was contributed by: Martin Gross of DISA, Anthony Villasenor of the National Aeronautics and Space Administration (NASA), Roger Martin and Fritz Schulz of NIST, David Jejferson, Shirley Hurwitz, Yelena Yesha, and Brad Fordham of NIST, and Bruce Lund also of NIST. Valuable constructive criticism was offered by: Duane Adams of ARPA, George Cotter of the National Security Agency (NSA), Howard Frank of ARPA, Randy Katz of ARPA, Paul Hunter of NASA, Barry Leiner of ARPA, and Shukri Wakid of NIST. Other comments were also provided by other reviewers, including Michael Papillo of Houston Associates and David Brown of Sterling Software. -

Energylens: Combining Smartphones with Electricity Meter for Accurate Activity Detection and User Annotation
EnergyLens: Combining Smartphones with Electricity Meter for Accurate Activity Detection and User Annotation Manaswi Sahay, Shailja Thakury, Amarjeet Singhy, Yuvraj Agarwalz yIndraprastha Institute of Information Technology, Delhi zCarnegie Mellon University y{manaswis, shailja1275, amarjeet}@iiitd.ac.in, [email protected] ABSTRACT Categories and Subject Descriptors Inferring human activity is of interest for various ubiquitous C.3 [Special-Purpose and Application-Based Systems]: computing applications, particularly if it can be done using Real-time and embedded systems ambient information that can be collected non intrusively. In this paper, we explore human activity inference, in the context of energy consumption within a home, where we de- Keywords fine an \activity" as the usage of an electrical appliance, its Smart Meters; Smartphones; Energy Disaggregation; Activ- usage duration and its location. We also explore the dimen- ity Detection; User Association sion of identifying the occupant who performed the activity. Our goal is to answer questions such as \Who is watching TV in the Dining Room and during what times?". This 1. INTRODUCTION Smartphones, over the past few years, have seen unprece- information is particularly important for scenarios such as dented growth across the world. In many markets, such as the apportionment of energy use to individuals in shared the US, they have long since surpassed sales of traditional settings for better understanding of occupant's energy con- feature phones. While many factors have contributed to sumption behavioral patterns. Unfortunately, accurate ac- their popularity, the most important perhaps is the increase tivity inference in realistic settings is challenging, especially in device capabilities as supported by higher end components when considering ease of deployment. -

Administrative Memorandum County of San Mateo
ADMINISTRATIVE MEMORANDUM COUNTY OF SAN MATEO NUMBER: B-19 SUBJECT: Mobile Technology Use Policy RESPONSIBLE DEPARTMENT: County Manager / Clerk of the Board APPROVED: _____________________________ DATE: _May 5, 2014____ John L. Maltbie, County Manager This memorandum replaces an earlier version of Memorandum B-19 dated October 22, 2007, which was limited to the acquisition and use of cellular telephones and personal digital assistants. This memorandum revises and expands the policy to cover the County’s acquisition of “mobile devices” and provision of such devices to employees. This memorandum also covers the use of such mobile devices to transact County business (including but not limited to accessing County information systems and technology) whether such devices are County-provided or personally-owned. It is San Mateo County’s policy that both the operation of County-provided mobile devices, as well as access to County information systems and technology from personally-owned devices, be appropriate and beneficial to the County and, by extension, its residents. The term “mobile devices” includes not only cellular telephones and personal digital assistants, but also smartphones, tablets and other mobile technologies. Under this policy, County Departments may choose to either provide County-supplied mobile devices to specific workforce members or authorize specific workforce members to access the County’s information systems and technology with their personally-owned mobile devices. In either case, such authorized workforce members will be required to meet the specific requirements of this Mobile Technology Use Policy. It is the responsibility of each Department Head to provide a list of authorized department users to ISD on an annual basis. -
2 End User Roadmaps
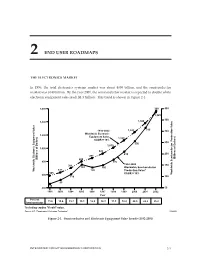
2 END USER ROADMAPS THE ELECTRONICS MARKET In 1996, the total electronics systems market was about $850 billion, and the semiconductor market was $140 billion. By the year 2001, the semiconductor market is expected to double while electronic equipment sales reach $1.3 trillion. This trend is shown in Figure 2-1. 1,600 390 400 1,545 350 1,400 1,380 315 1992-2002 1,243 300 Worldwide Electronic 1,200 Equipment Sales 1,120 CAGR = 10% 256 250 1,010 1,000 920 210 200 851 (Billions of Dollars) (Billions of Dollars) 800 800 175 1992-2002 701 150 153 150 Worldwide Semiconductor 633 Worldwide Electronic Equipment Sales 140 Production Value* 585 CAGR = 19% Worldwide Semiconductor Production Value 600 110 100 85 68 400 50 1992 1993 1994 1995 1996 1997 1998 1999 2000 2001 2002 Year Percent 11.6 13.4 15.7 19.1 16.516.3 17.3 18.820.5 22.2 25.2 Semiconductor *Including captive "if sold" value. Source: ICE, "Roadmaps of Packaging Technology" 11082AD Figure 2-1. Semiconductor and Electronic Equipment Sales Trends (1992-2001) INTEGRATED CIRCUIT ENGINEERING CORPORATION 2-1 End User Roadmaps 1996 TOTAL MERCHANT Of the total semiconductor market, SEMICONDUCTOR USAGE the top three categories, making up Auto Military <1% a total of 83% of the market are com- Industrial 6% 11% puters (50%), communications (15%) and consumer electronics (18%). Computer The actual breakdown is shown in Communications $135B 15% 50% Figure 2-2. These three areas are Consumer also expected to at least maintain 18% their market share, if not grow, through the end of the century. -

Survey on Information Appliances
Information Appliances Survey on Information Roy Want Xerox Palo Alto Research Center Gaetano Borriello Appliances University of Washington n appliance is a tool or machine adapted enabled the development of information appliances. A Afor a special purpose. Our retail stores are single technology trend by itself would not have been full of traditional appliances that attempt to improve our sufficient. For information appliances to make their lives by making an activity less unpleasant. Appliances debut as a recognized class of device, low-power dis- may provide an increase in efficiency that liberates per- plays, rechargeable batteries, and miniature radios all sonal time, such as a washing machine or dishwasher. needed to be developed in parallel. In addition, the Or they may perform a task that users couldn’t carry out information infrastructure plays a significant role in to a high standard by hand alone, such as a vacuum enabling the usefulness of an information appliance. cleaner or a label maker. If a task must be performed fre- Key infrastructural communication technologies rele- quently, it often becomes worth the investment to spend vant to this discussion include the digital cellular tele- money on a specialized appliance for the job. phone network, Digital Subscriber Lines (DSL), cable Since their invention, computers have changed dra- modems, and advanced services such as the Global Posi- matically in their capability, size, tioning System (GPS). and form factor. The original com- We classify the use of information appliances into the Information appliances take puters filled an entire room and led following four categories: to the mainframe concept. -

The Generative Internet
The Generative Internet The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citation Jonathan Zittrain, The Generative Internet, 119 Harvard Law Review 1974 (2006). Published Version doi:10.1145/1435417.1435426;doi:10.1145/1435417.1435426 Citable link http://nrs.harvard.edu/urn-3:HUL.InstRepos:9385626 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Other Posted Material, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#LAA ARTICLE THE GENERATIVE INTERNET Jonathan L. Zittrain TABLE OF CONTENTS I. INTRODUCTION..............................................................................................................................1975 II. A MAPPING OF GENERATIVE TECHNOLOGIES....................................................................1980 A. Generative Technologies Defined.............................................................................................1981 1. Capacity for Leverage .........................................................................................................1981 2. Adaptability ..........................................................................................................................1981 3. Ease of Mastery....................................................................................................................1981 4. Accessibility...........................................................................................................................1982 -

Kimono: Kiosk-Mobile Phone Knowledge Sharing System
Kimono: Kiosk-Mobile Phone Knowledge Sharing System Albert Huang1 Kari Pulli1,2 Larry Rudolph1 1Massachusetts Institute of Technology 2Nokia Research Center Abstract The functionality of an information kiosk can be extended by allowing it to interact with a smartphone, as demonstrated by the Kimono system, and the user interface can be greatly simplified by “associations” between pieces of information. A kiosk provides information that is relevant to a particu- lar location and can use valuable context information, such as the fact that a user is physically standing in front of the kiosk, to tailor the display. Its graphically rich screen is suit- able for presenting information to the user and has a natural input modality requiring the user to simply touch the screen. However, a kiosk lacks mobility and cannot stay with the user as he or she moves about the environment. Also, infor- mation provided by the kiosk must be remembered by the user. Finally, it is difficult to add information to the kiosk, and so the kiosk remains an information display device. All this changes when a handset, such as a PDA or smart- phone, can interact with the kiosk. The handset acts like a personalized proxy of the kiosk. It accompanies the user serving as a memory device. It is also an excellent media cre- Figure 1: The OK-net terminal with a touch panel display ation device, capable of taking pictures and recording voice and an optional keyboard. memos as well as short text messages. Associating newly created content with other currently selected content makes for a simpler user interface. -

Introduction to Computer.Pdf
Chapter One Introduction to Computer Computer A computer is an electronic device, operating under the control of instructions stored in its own memory that can accept data (input), process the data according to specified rules, produce information (output), and store the information for future use1. Functionalities of a computer2 Any digital computer carries out five functions in gross terms: Computer Components Any kind of computers consists of HARDWARE AND SOFTWARE. Hardware: Computer hardware is the collection of physical elements that constitutes a computer system. Computer hardware refers to the physical parts or components of a computer such as the monitor, mouse, keyboard, computer data storage, hard drive disk (HDD), system unit (graphic cards, sound cards, memory, motherboard and chips), etc. all of which are physical objects that can be touched.3 1 Vermaat, Misty E. Microsoft Office 2013 Introductory. Cengage Learning, p.IT3. 2014 2 http://www.tutorialspoint.com/computer_fundamentals/computer_quick_guide.htm 3 http://en.wikipedia.org/wiki/Computer_hardware 1 Input Devices Input device is any peripheral (piece of computer hardware equipment to provide data and control signals to an information processing system such as a computer or other information appliance. Input device Translate data from form that humans understand to one that the computer can work with. Most common are keyboard and mouse Example of Input Devices:- 1. Keyboard 2. Mouse (pointing device) 3. Microphone 4. Touch screen 5. Scanner 6. Webcam 7. Touchpads 8. MIDI keyboard 9. 10. Graphics Tablets 11. Cameras 12. Pen Input 13. Video Capture Hardware 14. Microphone 15. Trackballs 16. Barcode reader 17. Digital camera 18. -

Computer Skills Chapter 1
Computer Skills Chapter 1: 1 Introduction to Computer 2 What is Computer A computer is a programmable electronic device that accepts raw data as input and processes it with a set of instructions (a program) to produce the result as output. It renders output just after performing mathematical and logical operations and can save the output for future use. It can process numerical as well as non-numerical calculations. The term "computer" is derived from the Latin word "computare" which means to calculate. 3 Difference between Calculator & Computer Calculator Computer An electronic calculator is typically a A computer is a device that can be portable electronic device used to instructed to carry out sequences of perform calculations, ranging from arithmetic or logical operations basic arithmetic to complex automatically via computer mathematics. programming. Calculator is slow than Computer Computer works faster than Calculator It has very less memory Computer has more Memory In calculator we cannot use alphabet It provide facility to use alphabets as well as number Calculator only provides output on It provide facility to take output in the screen. Printed form 4 Functionalities of a computer Any digital computer carries out five functions in gross terms: Takes data as input. Stores the data/instructions in its memory and use them when required. Processes the data and converts it into useful information. Generates the output Controls all the above four steps Functionalities of a computer(Contd.) 5 Processing Data Information Advantage of Computer 6 Multitasking Multitasking is one of the major advantage of computer. Person can perform multiple task, multiple operation, calculate numerical problems within few seconds. -

Introduction to Computer
Chapter One: Introduction to Computer Computer A computer is an electronic device, operating under the control of instructions stored in its own memory that can accept data (input), process the data according to specified rules, produce information (output), and store the information for future use1. 2 Functionalities of a computer Any digital computer carries out five functions in gross terms: Computer Components Any kind of computers consists of HARDWARE AND SOFTWARE. Hardware: Computer hardware is the collection of physical elements that constitutes a computer system. Computer hardware refers to the physical parts or components of a computer such as the monitor, mouse, keyboard, computer data storage, hard drive disk (HDD), system unit (graphic cards, sound cards, memory, motherboard and chips), etc. all of 3 which are physical objects that can be touched. 1 2 Input Devices Input device is any peripheral (piece of computer hardware equipment to provide data and control signals to an information processing system such as a computer or other information appliance. Input device Translate data from form that humans understand to one that the computer can work with. Most common are keyboard and mouse Example of Input Devices:- 1. Keyboard 2. Mouse (pointing device) 3. Microphone 4. Touch screen 5. Scanner 6. Webcam 7. Touchpads 8. MIDI keyboard 9. 10.Graphics Tablets 11.Cameras 12.Pen Input 13.Video Capture Hardware 14.Microphone 15.Trackballs 16.Barcode reader 17.Digital camera 18.Joystick 19.Gamepad 20.Electronic Whiteboard 21. Note: The most common use keyboard is the QWERTY keyboard. Generally standard Keyboard has 104 keys. 3 Central Processing Unit (CPU) A CPU is brain of a computer. -

Information Appliances Ances and Consumer Electronics Contained Computing Proved More Difficult Than We Imagined for Two Prima- Devices
Guest Editors’ Introduction Information Roy Want Xerox PARC Gaetano Borriello Appliances University of Washington roducing a special issue on the rapidly didn’t even exist. Certainly many, if not all, of our appli- Pevolving area of information appliances ances and consumer electronics contained computing proved more difficult than we imagined for two prima- devices. However, we didn’t view them as information ry reasons: the field is moving quickly, and there is appliances because they didn’t have much information much commercial activity. The first makes it difficult to in them. What they had was the ability to play a CD, fol- determine the approaches and applications likely to be low instructions we tapped out on some buttons, or allow successful. The second makes it difficult to recruit us to place a phone call. All this changed when the World authors who are actually willing and able to discuss Wide Web came on the scene. Now, information can flow their work. around the world using standard protocols and be ren- Until a few years ago, the term “information appliance” dered on a variety of devices from desktop machines to Mr Java Joseph Kaye and Niko Matsakis MIT Media Lab Mr Java is a smart coffee machine, part of a new breed of connected and information-enabled appliances. When you put your mug under the spout (Figure A), the machine recognizes an RFID tag glued to the base. It greets you, makes you the coffee you prefer, and plays your prespecified choice of news or information. For example, when Kaye puts his mug under the spout, the machine’s LCD screen displays “Hi Jofish.” It makes a double tall latte and plays the latest RealAudio news feed from London. -

Qualitative Study of Smartphone Use: Subjective Experience of Time Through Personal Ubiquitous Technology
Design Research Society DRS Digital Library DRS Biennial Conference Series DRS2014 - Design's Big Debates Jun 16th, 12:00 AM Qualitative Study of Smartphone use: Subjective Experience of Time through Personal Ubiquitous Technology Yong-Ki Lee KAIST (Korea Advanced Institute of Science and Technology), Daejeon, Republic of Korea Kun-Pyo Lee KAIST (Korea Advanced Institute of Science and Technology), Daejeon, Republic of Korea Follow this and additional works at: https://dl.designresearchsociety.org/drs-conference-papers Citation Lee, Y., and Lee, K. (2014) Qualitative Study of Smartphone use: Subjective Experience of Time through Personal Ubiquitous Technology, in Lim, Y., Niedderer, K., Redstrom,̈ J., Stolterman, E. and Valtonen, A. (eds.), Design's Big Debates - DRS International Conference 2014, 16-19 June, Umea,̊ Sweden. https://dl.designresearchsociety.org/drs-conference-papers/drs2014/researchpapers/61 This Research Paper is brought to you for free and open access by the Conference Proceedings at DRS Digital Library. It has been accepted for inclusion in DRS Biennial Conference Series by an authorized administrator of DRS Digital Library. For more information, please contact [email protected]. Qualitative Study of Smartphone use: Subjective Experience of Time through Personal Ubiquitous Technology Yong-Ki Lee, KAIST (Korea Advanced Institute of Science and Technology), Daejeon, Republic of Korea Kun-Pyo Lee, KAIST (Korea Advanced Institute of Science and Technology), Daejeon, Republic of Korea Abstract We explore Smartphone use in Korea to develop a grounded theory on the experience with personal ubiquitous technologies. The preliminary theory that emerged during our data analysis centres on the role of changing time experiences in the use of Smartphones.