Packet Inspection for Application Classification
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Undergraduate Report
UNDERGRADUATE REPORT Attack Evolution: Identifying Attack Evolution Characteristics to Predict Future Attacks by MaryTheresa Monahan-Pendergast Advisor: UG 2006-6 IINSTITUTE FOR SYSTEMSR RESEARCH ISR develops, applies and teaches advanced methodologies of design and analysis to solve complex, hierarchical, heterogeneous and dynamic problems of engineering technology and systems for industry and government. ISR is a permanent institute of the University of Maryland, within the Glenn L. Martin Institute of Technol- ogy/A. James Clark School of Engineering. It is a National Science Foundation Engineering Research Center. Web site http://www.isr.umd.edu Attack Evolution 1 Attack Evolution: Identifying Attack Evolution Characteristics To Predict Future Attacks MaryTheresa Monahan-Pendergast Dr. Michel Cukier Dr. Linda C. Schmidt Dr. Paige Smith Institute of Systems Research University of Maryland Attack Evolution 2 ABSTRACT Several approaches can be considered to predict the evolution of computer security attacks, such as statistical approaches and “Red Teams.” This research proposes a third and completely novel approach for predicting the evolution of an attack threat. Our goal is to move from the destructive nature and malicious intent associated with an attack to the root of what an attack creation is: having successfully solved a complex problem. By approaching attacks from the perspective of the creator, we will chart the way in which attacks are developed over time and attempt to extract evolutionary patterns. These patterns will eventually -

Calculation of Signal Detection Theory Measures
Behavior Research Methods, Instruments, & Computers 1999, 31 (1), 137-149 Calculation of signal detection theory measures HAROLD STANISLAW California State University, Stanislaus, Turlock, California and NATASHA TODOROV Macquarie University, Sydney, New South Wales, Australia Signal detection theory (SDT) may be applied to any area of psychology in which two different types of stimuli must be discriminated. We describe several of these areas and the advantages that can be re- alized through the application of SDT. Three of the most popular tasks used to study discriminability are then discussed, together with the measures that SDT prescribes for quantifying performance in these tasks. Mathematical formulae for the measures are presented, as are methods for calculating the measures with lookup tables, computer software specifically developed for SDT applications, and gen- eral purpose computer software (including spreadsheets and statistical analysis software). Signal detection theory (SDT) is widely accepted by OVERVIEW OF SIGNAL psychologists; the Social Sciences Citation Index cites DETECTION THEORY over 2,000 references to an influential book by Green and Swets (1966) that describes SDT and its application to Proper application of SDT requires an understanding of psychology. Even so, fewer than half of the studies to which the theory and the measures it prescribes. We present an SDT is applicable actually make use of the theory (Stanislaw overview of SDT here; for more extensive discussions, see & Todorov, 1992). One possible reason for this apparent Green and Swets (1966) or Macmillan and Creelman underutilization of SDT is that relevant textbooks rarely (1991). Readers who are already familiar with SDT may describe the methods needed to implement the theory. -

Wannacry Ransomware
KNOW THE UNKNOWN® Success Story: WannaCry Ransomware WHITE PAPER Challenge Stopping a Worm & Saving Millions Worms like WannaCry and Petya operate as essentially Even the most recent of these attacks like WannaCry and zero-day attacks: they can lie dormant on our networks Petya still echo the basic principles of past-worms, and as and then rapidly spread between devices upon waking up. such, they are both preventable and stoppable. During The consequences of being hit by one is dramatic: precious the Code Red, Nimda, and ILOVEYOU attacks of the early- data is either ransom-locked or wiped and thus often 2000s, businesses that had invested in a NIKSUN-like irrecoverable. This means millions in lost data, restoration solution were able to run a rapid report to get a list of fees, public relations, and stock-holder confidence. all infected devices and cut them off from their network. Instead of thousands of machines being affected, they When FedEx was hit by Petya, for example, their subsidiary were able to resolve the incident with minor losses of TNT Express experienced “widespread service delays” and hundreds or less. This process takes a mere few minutes were unable to “fully restore all of the affected systems and thus could have saved Reckitt Benckiser from their and recover all of the critical business data that was hour-long attack. encrypted by the virus.”1 Shares in the company dropped 3.4% in the wake of the attack.2 Total, 100% visibility is simply the only way to stop these worms from becoming too damaging. -

A Signal Detection Theory Analysis of Several Psychophysical Procedures Used in Lateralization Tasks
Loyola University Chicago Loyola eCommons Master's Theses Theses and Dissertations 1984 A Signal Detection Theory Analysis of Several Psychophysical Procedures Used in Lateralization Tasks Joseph N. Baumann Loyola University Chicago Follow this and additional works at: https://ecommons.luc.edu/luc_theses Part of the Psychology Commons Recommended Citation Baumann, Joseph N., "A Signal Detection Theory Analysis of Several Psychophysical Procedures Used in Lateralization Tasks" (1984). Master's Theses. 3330. https://ecommons.luc.edu/luc_theses/3330 This Thesis is brought to you for free and open access by the Theses and Dissertations at Loyola eCommons. It has been accepted for inclusion in Master's Theses by an authorized administrator of Loyola eCommons. For more information, please contact [email protected]. This work is licensed under a Creative Commons Attribution-Noncommercial-No Derivative Works 3.0 License. Copyright © 1984 Joseph N. Baumann A SIGNAL DETECTION THEORY ANALYSIS OF SEVERAL PSYCHOPHYSICAL PROCEDURES USED IN LATERALIZATION TASKS by Joseph N. Baumann A Thesis Submitted to the Faculty of the Department of Psychology of Loyola University of Chicago in Fulfillment of the Master's Thesis Requirement in Psychology December 1983 ACKNOWLEDGMENTS The following thesis is the product of much collaboration, and I would like to express my gratitude, and acknowledge those people who greatly contributed to its completion. First, I would like to thank my committee, Richard R. Fay, Ph.D., and Raymond H. Dye, Jr., Ph.D., for their continued help and suggestions, both in data collection and analysis. I have learned greatly from the experience. I would also like to thank William A. -

The Cognitive Revolution: a Historical Perspective
Review TRENDS in Cognitive Sciences Vol.7 No.3 March 2003 141 The cognitive revolution: a historical perspective George A. Miller Department of Psychology, Princeton University, 1-S-5 Green Hall, Princeton, NJ 08544, USA Cognitive science is a child of the 1950s, the product of the time I went to graduate school at Harvard in the early a time when psychology, anthropology and linguistics 1940s the transformation was complete. I was educated to were redefining themselves and computer science and study behavior and I learned to translate my ideas into the neuroscience as disciplines were coming into existence. new jargon of behaviorism. As I was most interested in Psychology could not participate in the cognitive speech and hearing, the translation sometimes became revolution until it had freed itself from behaviorism, tricky. But one’s reputation as a scientist could depend on thus restoring cognition to scientific respectability. By how well the trick was played. then, it was becoming clear in several disciplines that In 1951, I published Language and Communication [1], the solution to some of their problems depended cru- a book that grew out of four years of teaching a course at cially on solving problems traditionally allocated to Harvard entitled ‘The Psychology of Language’. In the other disciplines. Collaboration was called for: this is a preface, I wrote: ‘The bias is behavioristic – not fanatically personal account of how it came about. behavioristic, but certainly tainted by a preference. There does not seem to be a more scientific kind of bias, or, if there is, it turns out to be behaviorism after all.’ As I read that Anybody can make history. -

Nimda Worm Shows You Can't Always Patch Fast Enough
Research Publication Date: 19 September 2001 ID Number: FT-14-5524 Nimda Worm Shows You Can't Always Patch Fast Enough John Pescatore Nimda bundles several known exploits against Internet Information Server and other Microsoft software. Enterprises with Web applications should start to investigate less- vulnerable Web server products. © 2001 Gartner, Inc. and/or its Affiliates. All Rights Reserved. Reproduction of this publication in any form without prior written permission is forbidden. The information contained herein has been obtained from sources believed to be reliable. Gartner disclaims all warranties as to the accuracy, completeness or adequacy of such information. Gartner shall have no liability for errors, omissions or inadequacies in the information contained herein or for interpretations thereof. The reader assumes sole responsibility for the selection of these materials to achieve its intended results. The opinions expressed herein are subject to change without notice. NEWS ANALYSIS Event On 18 September 2001, a new mass-mailing computer worm began infecting computers worldwide, damaging local files as well as remote network files. The w32.Nimda.A @ mm worm can spread through e-mail, file sharing and Web site downloads. For more information, visit: http://www.microsoft.com/technet/security/topics/Nimda.asp or http://www.sarc.com/avcenter/venc/data/[email protected]. Analysis As a "rollup worm," Nimda bundles several known exploits against Microsoft's Internet Information Server (IIS), Internet Explorer (IE) browser, and operating systems such as Windows 2000 and Windows XP, which have IIS and IE embedded in their code. To protect against Nimda, Microsoft recommends installing numerous patches and service packs on virtually every PC and server running IE, IIS Web servers or the Outlook Express e-mail client. -

An Application of Signal Detection Theory (SDT)
An Application of Signal Detection Theory for Understanding Driver Behavior at Highway-Rail Grade Crossings Michelle Yeh and Jordan Multer Thomas Raslear United States Department of Transportation Federal Railroad Administration Volpe National Transportation Systems Center Washington, DC Cambridge, MA We used signal detection theory to examine if grade crossing warning devices were effective because they increased drivers’ sensitivity to a train’s approach or because they encouraged drivers to stop. We estimated d' and β for eight warning devices using 2006 data from the Federal Railroad Administration’s Highway-Rail Grade Crossing Accident/Incident database and Highway-Rail Crossing Inventory. We also calculated a measure of warning device effectiveness by comparing the maximum likelihood of an accident at a grade crossing with its observed probability. The 2006 results were compared to an earlier analysis of 1986 data. The collective findings indicate that grade crossing warning devices are effective because they encourage drivers to stop. Warning device effectiveness improved over the years, as drivers behaved more conservatively. Sensitivity also increased. The current model is descriptive, but it provides a framework for understanding driver decision-making at grade crossings and for examining the impact of proposed countermeasures. INTRODUCTION State of the World The Federal Railroad Administration (FRA) needs a Train is close Train is not close better understanding of driver decision-making at highway-rail grade crossings. Grade crossing safety has improved; from Valid Stop False Stop 1994 through 2003, the number of grade crossing accidents Yes (Stop) (driver stops at (driver stops decreased by 41 percent and the number of fatalities fell by 48 crossing) unnecessarily) percent. -

Code Red Worm Propagation Modeling and Analysis ∗
Code Red Worm Propagation Modeling and Analysis ∗ Cliff Changchun Zou Weibo Gong Don Towsley Dept. Electrical & Dept. Electrical & Dept. Computer Science Computer Engineering Computer Engineering Univ. Massachusetts Univ. Massachusetts Univ. Massachusetts Amherst, MA Amherst, MA Amherst, MA [email protected] [email protected] [email protected] ABSTRACT the Internet has become a powerful mechanism for propa- The Code Red worm incident of July 2001 has stimulated gating malicious software programs. Worms, defined as au- activities to model and analyze Internet worm propagation. tonomous programs that spread through computer networks In this paper we provide a careful analysis of Code Red prop- by searching, attacking, and infecting remote computers au- agation by accounting for two factors: one is the dynamic tomatically, have been developed for more than 10 years countermeasures taken by ISPs and users; the other is the since the first Morris worm [30]. Today, our computing in- slowed down worm infection rate because Code Red rampant frastructure is more vulnerable than ever before [28]. The propagation caused congestion and troubles to some routers. Code Red worm and Nimda worm incidents of 2001 have Based on the classical epidemic Kermack-Mckendrick model, shown us how vulnerable our networks are and how fast we derive a general Internet worm model called the two- a virulent worm can spread; furthermore, Weaver presented factor worm model. Simulations and numerical solutions some design principles for worms such that they could spread of the two-factor worm model match the observed data of even faster [34]. In order to defend against future worms, we Code Red worm better than previous models do. -

Ethical Hacking
Official Certified Ethical Hacker Review Guide Steven DeFino Intense School, Senior Security Instructor and Consultant Contributing Authors Barry Kaufman, Director of Intense School Nick Valenteen, Intense School, Senior Security Instructor Larry Greenblatt, Intense School, Senior Security Instructor Australia • Brazil • Japan • Korea • Mexico • Singapore • Spain • United Kingdom • United States Official Certified Ethical Hacker © 2010 Course Technology, Cengage Learning Review Guide ALL RIGHTS RESERVED. No part of this work covered by the copyright herein Steven DeFino may be reproduced, transmitted, stored or used in any form or by any means Barry Kaufman graphic, electronic, or mechanical, including but not limited to photocopying, Nick Valenteen recording, scanning, digitizing, taping, Web distribution, information networks, Larry Greenblatt or information storage and retrieval systems, except as permitted under Section 107 or 108 of the 1976 United States Copyright Act, without the prior Vice President, Career and written permission of the publisher. Professional Editorial: Dave Garza Executive Editor: Stephen Helba For product information and technology assistance, contact us at Managing Editor: Marah Bellegarde Cengage Learning Customer & Sales Support, 1-800-354-9706 For permission to use material from this text or product, Senior Product Manager: submit all requests online at www.cengage.com/permissions Michelle Ruelos Cannistraci Further permissions questions can be e-mailed to Editorial Assistant: Meghan Orvis [email protected] -

THE CONFICKER MYSTERY Mikko Hypponen Chief Research Officer F-Secure Corporation Network Worms Were Supposed to Be Dead. Turns O
THE CONFICKER MYSTERY Mikko Hypponen Chief Research Officer F-Secure Corporation Network worms were supposed to be dead. Turns out they aren't. In 2009 we saw the largest outbreak in years: The Conficker aka Downadup worm, infecting Windows workstations and servers around the world. This worm infected several million computers worldwide - most of them in corporate networks. Overnight, it became as large an infection as the historical outbreaks of worms such as the Loveletter, Melissa, Blaster or Sasser. Conficker is clever. In fact, it uses several new techniques that have never been seen before. One of these techniques is using Windows ACLs to make disinfection hard or impossible. Another is infecting USB drives with a technique that works *even* if you have USB Autorun disabled. Yet another is using Windows domain rights to create a remote jobs to infect machines over corporate networks. Possibly to most clever part is the communication structure Conficker uses. It has an algorithm to create a unique list of 250 random domain names every day. By precalcuting one of these domain names and registering it, the gang behind Conficker could take over any or all of the millions of computers they had infected. Case Conficker The sustained growth of malicious software (malware) during the last few years has been driven by crime. Theft – whether it is of personal information or of computing resources – is obviously more successful when it is silent and therefore the majority of today's computer threats are designed to be stealthy. Network worms are relatively "noisy" in comparison to other threats, and they consume considerable amounts of bandwidth and other networking resources. -
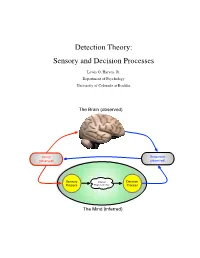
Detection Theory: Sensory and Decision Processes
Detection Theory: Sensory and Decision Processes Lewis O. Harvey, Jr. Department of Psychology University of Colorado at Boulder The Brain (observed) Stimuli Responses (observed) (observed) Sensory Internal Decision Process Representation Process The Mind (inferred) Psychology of Perception Lewis O. Harvey, Jr.–Instructor Psychology 4165-100 Steven M. Parker–Assistant Spring 2014 11:00–11:50 MWF This page blank 2/17 23.Jan.2014 Psychology of Perception Lewis O. Harvey, Jr.–Instructor Psychology 4165-100 Steven M. Parker–Assistant Spring 2014 11:00–11:50 MWF Sensory and Decision Processes A. Introduction All models of detection and discrimination have at least two psychological components or processes: the sensory process (which transforms physical stimulation into internal sensations) and a decision process (which decides on responses based on the output of the sensory process (Krantz, 1969) as illustrated in Figure 1. Stimuli Responses (observed) (observed) Sensory Internal Decision Process Representation Process The Mind (inferred) Figure 1: Detection based on two internal processes: sensory and decision. One goal of classical psychophysical methods was the determination of a stimulus threshold. Types of thresholds include detection, discrimination, recognition, and identification. What is a threshold? The concept of threshold actually has two meanings: One empirical and one theoretical. Empirically speaking, a threshold is the stimulus level needed to allow the observer to perform a task (detection, discrimination, recognition, or identification) at some criterion level of performance (75% or 84% correct, for example). Theoretically speaking, a threshold is property of the detection model’s sensory process. High Threshold Model: The classical concept of a detection threshold, as represented in the high threshold model (HTM) of detection, is a stimulus level below which the stimulus has no effect (as if the stimulus were not there) and above which the stimulus causes the sensory process to generate an output. -

Virus Bulletin, January 2003
ISSN 0956-9979 13666614 JANUARY 2003 THE INTERNATIONAL PUBLICATION ON COMPUTER VIRUS PREVENTION, RECOGNITION AND REMOVAL Editor: Helen Martin CONTENTS Technical Consultant: Matt Ham Technical Editor: Jakub Kaminski COMMENT If Not Now, Then When? 2 Consulting Editors: VIRUS PREVALENCE TABLE 3 Nick FitzGerald, Independent consultant, NZ Ian Whalley, IBM Research, USA NEWS Richard Ford, Independent consultant, USA 1. Lessons to be Learned 3 Edward Wilding, Data Genetics, UK 2. A Happy New Year 3 LETTERS 4 IN THIS ISSUE: VIRUS ANALYSIS IM a Hot Rod(ok) 5 • Conventional wisdom: Nick FitzGerald reports on recent efforts to extend and formalise the CARO Virus Naming FEATURES Convention. See p.7. 1. A Virus by Any Other Name • It’s the quiet ones you have to watch. Although consid- – Virus Naming Updated 7 ered a ‘minor’ curiosity when it made its initial appearance, 2. Are You Being [Opa]Serv[ed]? 10 W32/Opaserv is fast becoming a major headache. Martin 3. Infected or Affected, Overton looks at the spread of what some consider to be the Mobile Users Are Being Plagued 14 ‘quiet twin’ of Klez. See p.10. INSIGHT • Upwardly mobile? Analyst IDC forecasts the number of Hooked on a Feeling 16 wireless SMS messages soaring from 1.4 billion messages in 2002 to a whopping 42 billion in 2006. However, users PRODUCT REVIEW of SMS devices are increasingly being victimized by both Ahnlab V3Net for Windows Server SE 18 spam and email worms. Mary Landesman investigates the dark side of SMS text messaging that could derail the gravy END NOTES AND NEWS 24 train.