Portable Operating Systems and Information Security Risks 1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Linux on a Stick Everyone Knows You Can Boot Linux from a Live CD, but Have You Thought About Putting Linux on a Compact and Highly Portable USB
KNOW HOW Memory Stick Linux Booting Linux from a USB Memory Stick Linux on a Stick Everyone knows you can boot Linux from a live CD, but have you thought about putting Linux on a compact and highly portable USB memory stick? BY FABRIZIO CIACCHI bootable “live” CD like Knoppix much more common. Part of our pur- ent from DSL, but it includes more [1] or Kanotix [2] gives the user a pose is to create an inexpensive system, software (about 14 MB plus), and it Afully portable operating environ- so I will base this discussion on the stan- has already been refined and tested for ment. You can carry your system with dard and very common 128 MB size. USB devices. you and boot it from anywhere. However, the procedure I describe in this • Flonix [8]: Flonix is also based on Your tools, your files, and your work- article can also be used to put a larger DSL, but it uses some different pro- space will follow you wherever you go – Knoppix-based distribution on a larger grams (for instance, IceWM instead even to another PC with a different USB memory stick. of Fluxbox). The Flonix project also operating system. Live CDs are also used Assuming you want room to work and introduced a useful web install by system administrators for trouble- store documents, it is a good idea to only process. Ultimately, Flonix was so shooting computers that won’t boot use half of the available space (64 MB) successful that it become a commer- normally. for the Linux system and related tools. -
Backbox Penetration Testing Never Looked So Lovely
DISTROHOPPER DISTROHOPPER Our pick of the latest releases will whet your appetite for new Linux distributions. Picaros Diego Linux for children. here are a few distributions aimed at children: Doudou springs to mind, Tand there’s also Sugar on a Stick. Both of these are based on the idea that you need to protect children from the complexities of the computer (and protect the computer from the children). Picaros Diego is different. There’s nothing stripped- down or shielded from view. Instead, it’s a normal Linux distro with a brighter, more kid-friendly interface. The desktop wallpaper perhaps best We were too busy playing Secret Mario on Picaros Diego to write a witty or interesting caption. exemplifies this. On one hand, it’s a colourful cartoon image designed to interest young file manager. In the programming category, little young for a system like this, but the it children. Some of the images on the we were slightly disappointed to discover it may well work for children on the upper end landscape are icons for games, and this only had Gambas (a Visual Basic-like of that age range. should encourage children to investigate the language), and not more popular teaching Overall, we like the philosophy of wrapping system rather than just relying on menus. languages like Scratch or a Python IDE. Linux is a child-friendly package, but not On the other hand, it still displays technical However, it’s based on Debian, so you do dumbing it down. Picaros Diego won’t work details such as the CPU usage and the RAM have the full range of software available for every child, but if you have a budding and Swap availability. -
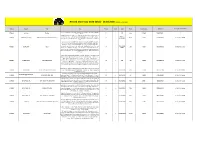
Record Store Day 2020 (GSA) - 18.04.2020 | (Stand: 05.03.2020)
Record Store Day 2020 (GSA) - 18.04.2020 | (Stand: 05.03.2020) Vertrieb Interpret Titel Info Format Inhalt Label Genre Artikelnummer UPC/EAN AT+CH (ja/nein/über wen?) Exclusive Record Store Day version pressed on 7" picture disc! Top song on Billboard's 375Media Ace Of Base The Sign 7" 1 !K7 Pop SI 174427 730003726071 D 1994 Year End Chart. [ENG]Pink heavyweight 180 gram audiophile double vinyl LP. Not previously released on vinyl. 'Nam Myo Ho Ren Ge Kyo' was first released on CD only in 2007 by Ace Fu SPACE AGE 375MEDIA ACID MOTHERS TEMPLE NAM MYO HO REN GE KYO (RSD PINK VINYL) LP 2 PSYDEL 139791 5023693106519 AT: 375 / CH: Irascible Records and now re-mastered by John Rivers at Woodbine Street Studio especially for RECORDINGS vinyl Out of print on vinyl since 1984, FIRST official vinyl reissue since 1984 -Chet Baker (1929 - 1988) was an American jazz trumpeter, actor and vocalist that needs little introduction. This reissue was remastered by Peter Brussee (Herman Brood) and is featuring the original album cover shot by Hans Harzheim (Pharoah Sanders, Coltrane & TIDAL WAVES 375MEDIA BAKER, CHET MR. B LP 1 JAZZ 139267 0752505992549 AT: 375 / CH: Irascible Sun Ra). Also included are the original liner notes from jazz writer Wim Van Eyle and MUSIC two bonus tracks that were not on the original vinyl release. This reissue comes as a deluxe 180g vinyl edition with obi strip_released exclusively for Record Store Day (UK & Europe) 2020. * Record Store Day 2020 Exclusive Release.* Features new artwork* LP pressed on pink vinyl & housed in a gatefold jacket Limited to 500 copies//Last Tango in Paris" is a 1972 film directed by Bernardo Bertolucci, saxplayer Gato Barbieri' did realize the soundtrack. -

Why Os/2 Failed: Business Mistakes Compounded by Memory Prices
Mountain Plains Journal of Business and Economics Volume 10 Issue 1 Article 4 Date Published: 10-1-2009 Why Os/2 Failed: Business Mistakes Compounded By Memory Prices Eric G. Swedin Weber State University Davis Follow this and additional works at: https://openspaces.unk.edu/mpjbt Part of the Business Commons Recommended Citation Swedin, E. G. (2009). Why Os/2 Failed: Business Mistakes Compounded By Memory Prices. Mountain Plains Journal of Business and Economics, 10(1). Retrieved from https://openspaces.unk.edu/mpjbt/ vol10/iss1/4 This Case Study is brought to you for free and open access by OpenSPACES@UNK: Scholarship, Preservation, and Creative Endeavors. It has been accepted for inclusion in Mountain Plains Journal of Business and Economics by an authorized editor of OpenSPACES@UNK: Scholarship, Preservation, and Creative Endeavors. For more information, please contact [email protected]. 36 WHY OS/2 FAILED: BUSINESS MISTAKES COMPOUNDED BY MEMORY PRICES ERIC G. SWEDIN WEBER STATE UNIVERSITY DAVIS ABSTRACT In 2006, IBM ended their support of OS/2, closing the book on an ambitious effort to create a modern operating system for the personal computer. IBM and Microsoft released the OS/2 operating system in December 1987 to replace the primitive DOS with a more sophisticated, preemptive multitasking operating system for personal computers. This article argues that OS/2 failed because of the U.S.-Japan Semiconductor Trade Agreement of 1986, subsequent accusations of DRAM chip dumping by the United States, and the resulting tariffs on Japanese memory chips, led to a memory chip shortage that drove up memory prices. -

Getestete Versionen Wine Debian Und Dessen Derivate (Ubuntu/Kubuntu/Xubuntu, Knoppix, Etc) Redhat, Fedora, Centos Opensuse Mandr
Wie kann die MSR-Software unter Linux verwendet FAQ werden ? MSR Electronics GmbH Getestete Versionen Gentoo Linux 2.6.34 64-Bit Wine 1.3.3 MSR PC-Software V5.10.18 → VERSION Wine Für den Betrieb der MSR PC-Software unter Linux ist die Software Wine1 erforderlich. Diese muss zuerst installiert werden. Für die verschiedenen Linux Distributionen wird dies mittels ver schiedener Kommandos getan. Debian und dessen Derivate (Ubuntu/Kubuntu/Xubuntu, Knoppix, etc) Entweder die offiziellen Pakete der Distribution verwenden (oft veraltet): $ sudo apt-get install wine Oder die neusten Pakete der Wine Maintainer verwenden (empfohlen): $ sudo add-apt-repository ppa:ubuntu-wine/ppa $ sudo apt-get updates $ sudo apt-get install wine1.3 RedHat, Fedora, CentOS Wine sollte sich in den offiziellen Quellen befinden. $ sudo yum install wine die Option --enablerepo=updates-testing erzwingt die neuste Version aus dem testing Repository: openSUSE Mittels YaST2 oder yum (siehe RedHat). Eventuell lohnt es sich auch, die neuste Version vom openSUSE Build Server herunterzuladen respektive diesen einzubinden, siehe dazu auch die entsprechende Webseite2. Mandriva Offizielle Version: $ su $ urpmi wine oder neuste Version von der Sourceforge Seite3. Gentoo $ emerge wine 1 Wine Is Not an Emulator: ist eine Windows-kompatible Laufzeitumgebung für POSIX-kompatible Betriebssyste me. Mit Wine ist es möglich, viele Programme, die für die Microsoft-Windows-Betriebssysteme kompiliert wur den, auch unter Unix mit dem X Window System laufen zu lassen. 2 http://download.opensuse.org/repositories/Emulators:/Wine/ 3 http://sourceforge.net/projects/wine/files/Mandriva Packages/ Version 0.9 Draft 1/5 Wie kann die MSR-Software unter Linux verwendet FAQ werden ? MSR Electronics GmbH Eventuell funktionieren oben genannte Kommandos nicht unter allen Versionen der entspre chenden Distributionen. -

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -

How to Create a Custom Live CD for Secure Remote Incident Handling in the Enterprise
How to Create a Custom Live CD for Secure Remote Incident Handling in the Enterprise Abstract This paper will document a process to create a custom Live CD for secure remote incident handling on Windows and Linux systems. The process will include how to configure SSH for remote access to the Live CD even when running behind a NAT device. The combination of customization and secure remote access will make this process valuable to incident handlers working in enterprise environments with limited remote IT support. Bert Hayes, [email protected] How to Create a Custom Live CD for Remote Incident Handling 2 Table of Contents Abstract ...........................................................................................................................................1 1. Introduction ............................................................................................................................5 2. Making Your Own Customized Debian GNU/Linux Based System........................................7 2.1. The Development Environment ......................................................................................7 2.2. Making Your Dream Incident Handling System...............................................................9 2.3. Hardening the Base Install.............................................................................................11 2.3.1. Managing Root Access with Sudo..........................................................................11 2.4. Randomizing the Handler Password at Boot Time ........................................................12 -

Devicelock® DLP 8.3 User Manual
DeviceLock® DLP 8.3 User Manual © 1996-2020 DeviceLock, Inc. All Rights Reserved. Information in this document is subject to change without notice. No part of this document may be reproduced or transmitted in any form or by any means for any purpose other than the purchaser’s personal use without the prior written permission of DeviceLock, Inc. Trademarks DeviceLock and the DeviceLock logo are registered trademarks of DeviceLock, Inc. All other product names, service marks, and trademarks mentioned herein are trademarks of their respective owners. DeviceLock DLP - User Manual Software version: 8.3 Updated: March 2020 Contents About This Manual . .8 Conventions . 8 DeviceLock Overview . .9 General Information . 9 Managed Access Control . 13 DeviceLock Service for Mac . 17 DeviceLock Content Security Server . 18 How Search Server Works . 18 ContentLock and NetworkLock . 20 ContentLock and NetworkLock Licensing . 24 Basic Security Rules . 25 Installing DeviceLock . .26 System Requirements . 26 Deploying DeviceLock Service for Windows . 30 Interactive Installation . 30 Unattended Installation . 35 Installation via Microsoft Systems Management Server . 36 Installation via DeviceLock Management Console . 36 Installation via DeviceLock Enterprise Manager . 37 Installation via Group Policy . 38 Installation via DeviceLock Enterprise Server . 44 Deploying DeviceLock Service for Mac . 45 Interactive Installation . 45 Command Line Utility . 47 Unattended Installation . 48 Installing Management Consoles . 49 Installing DeviceLock Enterprise Server . 52 Installation Steps . 52 Installing and Accessing DeviceLock WebConsole . 65 Prepare for Installation . 65 Install the DeviceLock WebConsole . 66 Access the DeviceLock WebConsole . 67 Installing DeviceLock Content Security Server . 68 Prepare to Install . 68 Start Installation . 70 Perform Configuration and Complete Installation . 71 DeviceLock Consoles and Tools . -

Page 1 of 3 How to Enable NTLM 2 Authentication 2/8/2012 Http
How to enable NTLM 2 authentication Page 1 of 3 Article ID: 239869 - Last Review: January 25, 2007 - Revision: 4.7 How to enable NTLM 2 authentication System Tip This article applies to a different version of Windows than the one you are using. Content in this article may not be relevant to you. Visit the Windows 7 Solution Center This article was previously published under Q239869 SUMMARY Historically, Windows NT supports two variants of challenge/response authentication for network logons: • LAN Manager (LM) challenge/response • Windows NT challenge/response (also known as NTLM version 1 challenge/response) The LM variant allows interoperability with the installed base of Windows 95, Windows 98, and Windows 98 Second Edition clients and servers. NTLM provides improved security for connections between Windows NT clients and servers. Windows NT also supports the NTLM session security mechanism that provides for message confidentiality (encryption) and integrity (signing). Recent improvements in computer hardware and software algorithms have made these protocols vulnerable to widely published attacks for obtaining user passwords. In its ongoing efforts to deliver more secure products to its customers, Microsoft has developed an enhancement, called NTLM version 2, that significantly improves both the authentication and session security mechanisms. NTLM 2 has been available for Windows NT 4.0 since Service Pack 4 (SP4) was released, and it is supported natively in Windows 2000. You can add NTLM 2 support to Windows 98 by installing the Active Directory Client Extensions. After you upgrade all computers that are based on Windows 95, Windows 98, Windows 98 Second Edition, and Windows NT 4.0, you can greatly improve your organization's security by configuring clients, servers, and domain controllers to use only NTLM 2 (not LM or NTLM). -

Windows 95, Windows 98, Windows 98SE, and Windows ME Courtesy of Nashville Home Linux Solutions
Important information for users of Windows 95, Windows 98, Windows 98SE, and Windows ME courtesy of Nashville Home Linux Solutions FACT: As of July 2006, Microsoft has officially ended support for Windows 95, Windows 98, Windows 98SE, and Windows ME (Millennium Edition). What does this mean for you? Microsoft©s end-of-support announcement means that users of Windows 95, 98, and ME will no longer receive security updates, bug fixes, and other patches for their computer©s operating system. It also means that future releases of Microsoft software (such as Media Player, Internet Explorer, and Outlook Express) will no longer support these operating systems. Users of these versions of Windows will not benefit from enhanced features and security in these new versions. Why should I be concerned? Windows 95, 98, and ME are based around the DOS operating system, an inherently insecure operating system. Users of DOS-based Windows will become increasingly at risk for viruses, spyware, malware, and system intrusions as new holes and exploits are discovered in these operating systems and the older software that runs on them. In addition, software vendors (including makers of anti-virus and other security products) will be phasing out support for these operating systems now that Microsoft has ended its support. If you are connecting your DOS-based Windows operating system to the Internet, you need to take action to secure your computer. What are my options? If you would like to continue to operate on your current hardware, you have a few options available to you: 1. Upgrade Windows Microsoft©s only currently-available Windows workstation operating system is Windows XP (Home or Professional). -

Membuat Linux Distro Dengan SLAX
Membuat Linux Distro dengan SLAX Susi Rianti Abstract Lack of understanding of the operating system as well as the dependence on a specific vendor , underdevelopment of creativity of the nation.So to improve the creativity and eliminate dependence on certain vendors then use Linux. Linux is an operating system open souce, portable, small size and bootable. Linux used is Linux Slax Keyword : Enhancing creativity , Linux , Linux Slax Pendahuluan hasilkan puluhan distro anak, antara lain Selama ini kita begitu tergantung dengan Ubuntu, Knoppix, Xandros, DSI, dan sistem operasi yang siap pakai, tanpa sebagainya. terlalu banyak memerlukan pemikiran serta kita tergantung dengan satu vendor saja. Slax adalah varian dari distro linux yang Dimana kita selalu dimanjakan, bila ada berbasis slaxware, ukurannya kecil, cepat, masalah tinggal kirim (send) secara online portable, dengan pendekatan desain dan kita tidak pernah memikirkan bagai modular. Mempunyai kemampuan bootable mana cara memperbaiki permasalahan (dapat dijalankan langsung dari CD atau yang ada pada sistem operasi tersebut. USB tanpa proses instalasi) Dengan adanya Linux diharapkan kita lebih kreatif dalam berfikir dan tidak bergantung Varian Slax pada bangsa manapun. Slax merupakan salah satu jenis distribusi (distro) Linux yang berbasis Slackware dan Linux adalah suatu sistem operasi yang dapat didownload pada “www.slax.org”. berukuran kecil dan dapat diandalkan, baik Disitusnya ini Slax dibagi menjadi beberapa dari sisi keamanannya dan Linux juga me- jenis distro, antara lain: rupakan sistem operasi yang bersifat open 1. SLAX Standard Edition. soure code artinya pemakai bisa meng- Sistem operasi Slax dengan unduh sistem ini tanpa harus membayar. ketersediaan aplikasi yang luas dan dilengkapi dengan sistem Xwindow dan Distro Linux adalah singkatan dari Distribusi lingkungan desktop KDE. -

Introduction to Fmxlinux Delphi's Firemonkey For
Introduction to FmxLinux Delphi’s FireMonkey for Linux Solution Jim McKeeth Embarcadero Technologies [email protected] Chief Developer Advocate & Engineer For quality purposes, all lines except the presenter are muted IT’S OK TO ASK QUESTIONS! Use the Q&A Panel on the Right This webinar is being recorded for future playback. Recordings will be available on Embarcadero’s YouTube channel Your Presenter: Jim McKeeth Embarcadero Technologies [email protected] | @JimMcKeeth Chief Developer Advocate & Engineer Agenda • Overview • Installation • Supported platforms • PAServer • SDK & Packages • Usage • UI Elements • Samples • Database Access FireDAC • Migrating from Windows VCL • midaconverter.com • 3rd Party Support • Broadway Web Why FMX on Linux? • Education - Save money on Windows licenses • Kiosk or Point of Sale - Single purpose computers with locked down user interfaces • Security - Linux offers more security options • IoT & Industrial Automation - Add user interfaces for integrated systems • Federal Government - Many govt systems require Linux support • Choice - Now you can, so might as well! Delphi for Linux History • 1999 Kylix: aka Delphi for Linux, introduced • It was a port of the IDE to Linux • Linux x86 32-bit compiler • Used the Trolltech QT widget library • 2002 Kylix 3 was the last update to Kylix • 2017 Delphi 10.2 “Tokyo” introduced Delphi for x86 64-bit Linux • IDE runs on Windows, cross compiles to Linux via the PAServer • Designed for server side development - no desktop widget GUI library • 2017 Eugene