Parallel Computing?
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
ACM MM 96 Text ACM MULTIMEDIA 96
ACM MM 96 Text ACM MULTIMEDIA 96 General Information Technical Program Demonstrations Art Program Workshops Tutorials Stephan Fischer Last modified: Fri Nov 29 09:28:01 MET 1996 file:///C|/Documents%20and%20Settings/hsu.cheng-hsin/Desktop/acmmm96/index.htm[1/28/2010 9:42:17 AM] ACM MM 96 ACM MULTIMEDIA 96 The Fourth ACM International Multimedia Conference and Exhibition ADVANCE PROGRAM 18-22 November 1996 Hynes Convention Center Boston, Massachusetts, USA Co-located with SPIE's Symposium on Voice, Video and Data Communication, and Broadband Network Engineering program and overlapping with CSCW, to be held in nearby Cambridge. Welcome to ACM Multimedia '96 Special Events Conference-at-a-Glance Ongoing Events Courses Technical Papers Panels Registration Course Selections Hotels Conference Organization Welcome to ACM Multimedia '96 In what seems in retrospect to have been an astonishingly short time, multimedia has progressed from a technically- challenging curiosity to an essential feature of most computer systems -- both professional and consumer. Accordingly, leading-edge research in multimedia no longer is confined to dealing with processing or information- access bottlenecks, but addresses the ever-broadening ways in which the technology is changing and improving interpersonal communication, professional practice, entertainment, the arts, education, and community life. This year's program emphasizes this trend: off-the-shelf building blocks are now available to construct useful and appealing applications which are highlighted in the Demonstration and Art venues. In addition to the full complement of panels, courses, and workshops, the conference program features a distinguished set of technical papers. Keynotes will be provided by Glenn Hall, the Technical Director of Aardman Animations whose work includes Wallace and Gromit; and Professor Bill Buxton of the University of Toronto and Alias | Wavefront Inc. -

Frederick Phillips Brooks, Jr
May 13, 2005 Frederick Phillips Brooks, Jr. Department of Computer Science 413 Granville Road University of North Carolina Chapel Hill, NC 27514-2723 Chapel Hill, NC 27599-3175 (919) 942-2529 (919) 962-1931 (919) 962-1799 Fax Born 19 April 1931; Durham, NC [email protected] Married, three children: http://www.cs.unc.edu/~brooks Kenneth P. Brooks, 8/14/58 Roger G. Brooks, 12/25/61 Barbara B. LaDine, 2/24/65 EDUCATION Ph.D., Harvard University, Applied Mathematics (Computer Science), 1956; Howard H. Aiken, advisor; dissertation: The Analytic Design of Automatic Data Processing Systems S.M., Harvard University, Applied Mathematics (Computer Science), 1955 A.B. summa cum laude, Duke University, Physics, 1953. First in class of 1953. TEACHING EXPERIENCE University of North Carolina at Chapel Hill, Department of Computer Science Kenan Professor of Computer Science, 1975- Professor of Computer Science, 1964-75 Chairman, 1964-1984; founder Twente Technical University, Enschede, The Netherlands: Visiting Professor, 1970 Columbia University: Adjunct Assistant Professor, 1960-61 Vassar College: Visiting Instructor, 1958 IBM Systems Research Institute, Voluntary Education Program, and Summer Student Program Teacher, 1957-59 DEVELOPMENT EXPERIENCE IBM Corporation Poughkeepsie, New York Corporate Processor Manager for Development of System/360 Computer Systems, 1961-1965 Manager of Operating System/360, 1964-65 Manager, System/360 Hardware Development, Data Systems Division, 1961-64 Systems Planning Manager, Data Systems Division (8000 series et al.), -

VMV 2015 Vision, Modeling and Visualization
VMV 2015 Vision, Modeling and Visualization Aachen, Germany October 07 – 10, 2015 General Chairs Leif Kobbelt Program Chairs David Bommes Tobias Ritschel Thomas Schultz Proceedings Production Editor Dieter Fellner (TU Darmstadt & Fraunhofer IGD, Germany) In cooperation with the Eurographics Association DOI: 10.2312/vmv.20152020 This work is subject to copyright. All rights reserved, whether the whole or part of the material is concerned, specifically those of translation, reprinting, re-use of illustrations, broadcasting, reproduction by photocopying machines or similar means, and storage in data banks. Copyright c 2015 by the Eurographics Association Postfach 2926, 38629 Goslar, Germany Published by the Eurographics Association –Postfach 2926, 38629 Goslar, Germany– in cooperation with Institute of Computer Graphics & Knowledge Visualization at Graz University of Technology and Fraunhofer IGD (Fraunhofer Institute for Computer Graphics Research), Darmstadt ISBN 978-3-905674-95-8 The electronic version of the proceedings is available from the Eurographics Digital Library at http://diglib.eg.org Table of Contents TableofContents ...........................................................................iii International Program Committee . ............................................................v Sponsors . .................................................................................vi AuthorIndex...............................................................................vii InvitedTalks ..............................................................................viii -

Opinion Poll on ACM Affiliation for the Symposium on Computational Geometry
Opinion Poll on ACM affiliation for the Symposium on Computational Geometry Dear SoCG community, Since its start 27 years ago, SoCG has always been affiliated to ACM. This means that the proceedings are published by ACM, and that the symposium is organized “sponsored by ACM” (more precisely, sponsored by ACM SIGACT & ACM SIGGRAPH) or “in cooperation with ACM”. The latter happened only a couple of times, namely when SoCG was in Korea in 2007 and when it was in Denmark in 2009. Being affiliated to ACM has certain advantages, but also certain disadvantages, as detailed below. Hence, at the business meeting of this year’s SoCG in Paris, an alternative was discussed: organizing SoCG as an independent symposium, with the proceedings being published by Dagstuhl in their LIPIcs series (see below). A straw poll was taken, and the vast majority of the participants wanted the Steering Committee to investigate this issue further, which we do through this opinion poll. We hope you want to participate in this important poll. The opinion poll consists of three simple questions stated below: one about your preference for the future of SoCG, and two about your relation to SoCG and your current position. You can participate in this poll by sending your answers to [email protected] (do *not* vote by replying to this email). The poll closes November 21, 2011 . All votes will be treated confidentially. Before voting, please first read the background information given below. The SoCG Steering Committee: Mark de Berg (secretary), Joseph Mitchell, Günter Rote, Jack Snoeyink (chair), Monique Teillaud. -

ACM Multimedia 2008 - Home
ACM Multimedia 2008 - Home Home Contact Us About ACM News Flash * The competition for student conference participation grant is open. * The update on tutorials is available. * The instructions for camera ready paper submission have been posted. Menu Home Events Calendar Home Latest updates: « < January 2010 > » S M T W T F S Call For Papers *** October 20, 2008: Full conference program is now available*** 27 28 29 30 31 1 2 Important Dates ACM International Conference on Multimedia 3 4 5 6 7 8 9 Organizing Commitee 10 11 12 13 14 15 16 Submission Instructions Pan Pacific Hotel, Vancouver, BC, Canada 17 18 19 20 21 22 23 October 27 – 31, 2008 Information for Presenters 24 25 26 27 28 29 30 http://www.mcrlab.uottawa.ca/acmmm2008/ Technical Program 31 1 2 3 4 5 6 Arts Program ACM Multimedia 2008 invites your participation in the premier annual « < February 2010 > » Workshops multimedia conference, covering all aspects of multimedia computing: from S M T W T F S MIR 2008 underlying technologies to applications, theory to practice, and servers to 31 1 2 3 4 5 6 networks to devices. Tutorials 7 8 9 10 11 12 13 Registration The technical program will consist of plenary sessions and talks with topics 14 15 16 17 18 19 20 21 22 23 24 25 26 27 Venue of interest in: 28 1 2 3 4 5 6 Sponsors (a) Multimedia content analysis, processing, and retrieval; (b) Multimedia networking and systems support; and News Random Image (c) Multimedia tools, end-systems, and applications; Awards (d) Human-centered multimedia. -

Sample-Sigplan.Pdf
The Name of the Title is Hope Ben Trovato∗ Lars Thørväld Valerie Béranger G.K.M. Tobin∗ The Thørväld Group Inria Paris-Rocquencourt [email protected] Hekla, Iceland Rocquencourt, France [email protected] [email protected] Institute for Clarity in Documentation Dublin, Ohio, USA Aparna Patel Huifen Chan Charles Palmer Rajiv Gandhi University Tsinghua University Palmer Research Laboratories Doimukh, Arunachal Pradesh, India Haidian Qu, Beijing Shi, China San Antonio, Texas, USA [email protected] John Smith Julius P. Kumquat The Thørväld Group The Kumquat Consortium Hekla, Iceland New York, USA [email protected] [email protected] Figure 1. Seattle Mariners at Spring Training, 2010. Abstract CCS Concepts: • Computer systems organization ! Em- bedded systems; Redundancy; Robotics; • Networks ! A clear and well-documented LATEX document is presented as an article formatted for publication by ACM in a conference Network reliability. proceedings or journal publication. Based on the “acmart” Keywords: datasets, neural networks, gaze detection, text document class, this article presents and explains many of tagging the common variations, as well as many of the formatting elements an author may use in the preparation of the docu- ACM Reference Format: mentation of their work. Ben Trovato, G.K.M. Tobin, Lars Thørväld, Valerie Béranger, Aparna Patel, Huifen Chan, Charles Palmer, John Smith, and Julius P. Kumquat. ∗ Both authors contributed equally to this research. 2018. The Name of the Title is Hope. In Woodstock ’18: ACM Sym- posium on Neural Gaze Detection, June 03–05, 2018, Woodstock, NY. Permission to make digital or hard copies of all or part of this work for ACM, New York, NY, USA,7 pages. -

Table of Contents
SELF-STUDY QUESTIONNAIRE FOR THE REVIEW OF Software Engineering Prepared for: Engineering Accreditation Commission Accreditation Board for Engineering and Technology 111 Market Place, Suite 1050 Baltimore, Maryland 21202-4012 Phone: 410-347-7700 Fax: 410-625-2238 e-mail: [email protected] www: http://www.abet.org/ Prepared by: Department of Computer Science and Software Engineering Rose-Hulman Institute of Technology June 9, 2006 ROSE-HULMAN INSTITUTE OF TECHNOLOGY DEPARTMENT OF COMPUTER SCIENCE AND SOFTWARE ENGINEERING 5500 WABASH AVENUE, CM 97 TERRE HAUTE, INDIANA 47803-3999 TELEPHONE: (812) 877-8402 FAX: (812) 872-6060 EMAIL: [email protected] Table of Contents A. Background Information................................................................................................... 1 1. Degree Titles………………………………………………………………………….. 1 2. Program Modes……………………………………………………………………….. 1 3. Actions to Correct Previous Shortcomings………………………………………........ 1 4. Contact Information…………………………………………………………………... 1 B. Accreditation Summary..................................................................................................... 2 1. Students………………………………………………………………………………... 2 a. Evaluation…………………………………………………………………………. 2 b. Advising…………………………………………………………………………… 2 c. Monitoring…………………………………………………………………………. 2 d. Acceptance of Transfer Students…………………………………………………... 4 e. Validation of Transfer Credit……………………………………………………… 4 2. Program Educational Objectives………………………………………………………. 6 a. Mission…………………………………………………………………………….. 6 b. Program Constituencies……………………………………………………………. -

ACM SIGGRAPH Art Papers Programs 2019-2020 Everardo Reyes-García, Andrés Burbano
ACM SIGGRAPH Art Papers Programs 2019-2020 Everardo Reyes-García, Andrés Burbano To cite this version: Everardo Reyes-García, Andrés Burbano. ACM SIGGRAPH Art Papers Programs 2019-2020. Inter- national Symposium on Electronic Art (ISEA 2019), Jun 2019, Gwangju, South Korea. hal-02167636 HAL Id: hal-02167636 https://hal.archives-ouvertes.fr/hal-02167636 Submitted on 28 Jun 2019 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. ACM SIGGRAPH Art Papers Programs 2019-2020 Everardo Reyes, Andrés Burbano Université Paris 8, Universidad de los Andes Paris, France & Bogota, Colombia [email protected], [email protected] Abstract tific papers. To be included in the program, authors first This institutional presentation introduces the ACM submitted their papers as proposals that go through a rigor- SIGGRAPH Art Papers programs 2019 and 2020. The 2019 ous blind peer-review process. Accepted papers are pre- edition marks the 11th version of the program and our main sented in person by at least one of its authors at the goal is to highlight its principal novelties and projections on- SIGGRAPH venue and published in a special issue of Le- to 2020. -
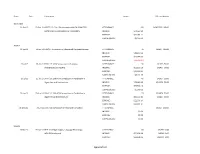
Appendix C SURPLUS/LOSS: $291.34 SIGCSE 0.00 Sigada 100.00 SIGAPP 0.00 SIGPLAN 0.00
Starts Ends Conference Actual SIGs and their % SIGACCESS 21-Oct-13 23-Oct-13 ASSETS '13: The 15th International ACM SIGACCESS ATTENDANCE: 155 SIGACCESS 100.00 Conference on Computers and Accessibility INCOME: $74,697.30 EXPENSE: $64,981.11 SURPLUS/LOSS: $9,716.19 SIGACT 12-Jan-14 14-Jan-14 ITCS'14 : Innovations in Theoretical Computer Science ATTENDANCE: 76 SIGACT 100.00 INCOME: $19,210.00 EXPENSE: $21,744.07 SURPLUS/LOSS: ($2,534.07) 22-Jul-13 24-Jul-13 PODC '13: ACM Symposium on Principles ATTENDANCE: 98 SIGOPS 50.00 of Distributed Computing INCOME: $62,310.50 SIGACT 50.00 EXPENSE: $56,139.24 SURPLUS/LOSS: $6,171.26 23-Jul-13 25-Jul-13 SPAA '13: 25th ACM Symposium on Parallelism in ATTENDANCE: 45 SIGACT 50.00 Algorithms and Architectures INCOME: $45,665.50 SIGARCH 50.00 EXPENSE: $39,586.18 SURPLUS/LOSS: $6,079.32 23-Jun-14 25-Jun-14 SPAA '14: 26th ACM Symposium on Parallelism in ATTENDANCE: 73 SIGARCH 50.00 Algorithms and Architectures INCOME: $36,107.35 SIGACT 50.00 EXPENSE: $22,536.04 SURPLUS/LOSS: $13,571.31 31-May-14 3-Jun-14 STOC '14: Symposium on Theory of Computing ATTENDANCE: SIGACT 100.00 INCOME: $0.00 EXPENSE: $0.00 SURPLUS/LOSS: $0.00 SIGAda 10-Nov-13 14-Nov-13 HILT 2013:High Integrity Language Technology ATTENDANCE: 60 SIGBED 0.00 ACM SIGAda Annual INCOME: $32,696.00 SIGCAS 0.00 EXPENSE: $32,404.66 SIGSOFT 0.00 Appendix C SURPLUS/LOSS: $291.34 SIGCSE 0.00 SIGAda 100.00 SIGAPP 0.00 SIGPLAN 0.00 SIGAI 11-Nov-13 15-Nov-13 ASE '13: ACM/IEEE International Conference on ATTENDANCE: 195 SIGAI 25.00 Automated Software Engineering -

ACM Multimedia 2010 - Worldwide Premier Multimedia Conference - 25-29 October 2010 - Florence (I)
ACM Multimedia 2010 - worldwide premier multimedia conference - 25-29 October 2010 - Florence (I) Conference Program Attendees General History People Program at a glance Technical Program Competitions Interactive Art Exhibit Tutorials Workshops Registration Travel Accommodation Venues Instructions for Presenting Authors You are here: Home Welcome to the ACM Multimedia 2010 website Sponsors Social ACM Multimedia 2010 is the worldwide premier multimedia conference and a key event to display scientific achievements and innovative industrial products. The Conference offers to scientists and practitioners in the area of Multimedia plenary scientific and technical sessions, tutorials, panels and discussion meetings on relevant and challenging questions for the next years horizon of multimedia. The Interactive Art program ACM Multimedia 2010 will provide the opportunity of interaction between artists and computer scientists and investigation on the application of multimedia technologies to art and cultural heritage. Please look inside the ACM MULTIMEDIA Website for more information. Conference videos online! By WEBCHAIRS | Published: FEBRUARY 4, 2011 A. Del Bimbo – Opening Shih-Fu Chang – Opening A. Smeulders – Opening D. Watts – Keynotes M. Shah – Keynotes R. Jain – Tech. achiev. award E. Kokiopoulou – SIGMM award S. Bhattacharya – Best papers ACM Multimedia 2010 Twitter http://www.acmmm10.org/[20/11/2011 7:16:00 PM] ACM Multimedia 2010 - worldwide premier multimedia conference - 25-29 October 2010 - Florence (I) S. Tan – Best papers R. Hong – Best papers S. Milani – Best papers Exhibit VideoLectures.net has finally released the videos of the important events recorded during the conference! ACM Multimedia 2010 Best Paper and Demos Awards at Gala Dinner By WEBCHAIRS | Published: OCTOBER 29, 2010 ACM Multimedia 2010 Gala Dinner was held yesterday in Salone dei 500 at Palazzo Vecchio. -

Ranking of the ACM International Conference on Multimedia Retrieval - ICMR
Int. Jnl. Multimedia Information Retrieval, IJMIR, vol. 2, no. 4, 2013 The final publication is available at Springer via http://dx.doi.org/10.1007/s13735-013-0047-3 International Ranking of the ACM International Conference on Multimedia Retrieval - ICMR In 2010, there were two well respected multimedia retrieval conferences supported by ACM: CIVR and MIR. At that time, a committee consisting of both the CIVR and MIR steering committees was formed to decide on the future. From those discussions, a merged conference was formed: the ACM International Conference on Multimedia Retrieval (acmICMR.org) which would be governed by the ICMR steering committee. Our goal for ICMR was not to create the largest conference, but the highest quality multimedia retrieval meeting worldwide. The Chinese Computing Federation (CCF) Ranking List provides a ranking of all international peer-reviewed conferences and journals in the broad area of computer science. This list is typically consulted by academic institutions in China as a quality metric for PhD promotions and tenure track jobs. Because ICMR was a young conference, it was not on the list in 2012. So, in late 2012, a proposal was assembled by Prabha Balakrishnan, Ramesh Jain, Klara Nahrstedt and myself towards eventual placement of ICMR on the CCF Ranking. The CCF committee examined both the quality of the content and the quality of the meeting and they gave us a ranking: The ranking released in 2013 for "Multimedia and Graphics" is first split into sections A, B, and C, and the conferences are ranked numerically within each section. Section A (only has 3 conferences in this section) 1. -

The Ohio State University Department of Computer Science and Engineering 2006 - 2007 Annual Report
The Ohio State University Department of Computer Science and Engineering 2006 - 2007 Annual Report Striving toward and achieving excellence throughout the world. Investigating the questions Finding the solutions Leading the current generation Preparing the next generation Educating every generation CONTENTS GREETIN G S FROM THE CHAIR ’S OFFI C E II I HI G HLI G HTS & AC HIEVEMENTS 2006 - 2007 1 Faculty 1 Student Achievements 4 Alumni Awards 6 2007 Computer Science and Engineering Department Awards 7 Industrial Advisory Committee 8 RESEAR C H 9 Caching Everywhere in Computer, Storage, and Network Systems 10 Ultra Scale Visualization 11 Automatic Video Surveillance Using Computer Vision 12 Grants, Award & Gifts 13 Editorial Boards of Journals and Chairs of Major Conferences 20 STUDENTS 21 Graduate Program 21 Undergraduate Program 21 Doctorates Bestowed 22 Masters Degrees Awarded 24 CSE Research Exhibition 26 Undergraduate Studies 28 Udergraduate Degrees Conferred 29 FA C ULTY AND STAFF 30 Faculty 30 Lecturers 39 Part-Time Lecturers 40 Administrative & Computer Staffs 40 FINAN C IAL SUPPORT 41 SELE C TED PUBLI C ATIONS BY AREAS 42 Artificial Intelligence 42 Computer Graphics 43 Computer Networking 44 Software Engineering 45 Systems 45 Books 48 COURSE LISTIN G 49 i Mission Statement The Department of Computer Science and Engineering will impact the information age as a national leader in computing research and education. We will prepare computing graduates who are highly sought after, productive, and well-respected for their work, and who contribute to new developments in computing. We will give students in other disciplines an appropriate foundation in computing for their education, research, and experiences after graduation, consistent with computing’s increasingly fundamental role in society.