Post's Functional Completeness Theorem
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Physical and Mathematical Sciences 2014, № 1, P. 3–6 Mathematics ON
PROCEEDINGS OF THE YEREVAN STATE UNIVERSITY Physical and Mathematical Sciences 2014, № 1, p. 3–6 Mathematics ON ZIGZAG DE MORGAN FUNCTIONS V. A. ASLANYAN ∗ Oxford University UK, Chair of Algebra and Geometry YSU, Armenia There are five precomplete classes of De Morgan functions, four of them are defined as sets of functions preserving some finitary relations. However, the fifth class – the class of zigzag De Morgan functions, is not defined by relations. In this paper we announce the following result: zigzag De Morgan functions can be defined as functions preserving some finitary relation. MSC2010: 06D30; 06E30. Keywords: disjunctive (conjunctive) normal form of De Morgan function; closed and complete classes; quasimonotone and zigzag De Morgan functions. 1. Introduction. It is well known that the free Boolean algebra on n free generators is isomorphic to the Boolean algebra of Boolean functions of n variables. The free bounded distributive lattice on n free generators is isomorphic to the lattice of monotone Boolean functions of n variables. Analogous to these facts we have introduced the concept of De Morgan functions and proved that the free De Morgan algebra on n free generators is isomorphic to the De Morgan algebra of De Morgan functions of n variables [1]. The Post’s functional completeness theorem for Boolean functions plays an important role in discrete mathematics [2]. In the paper [3] we have established a functional completeness criterion for De Morgan functions. In this paper we show that zigzag De Morgan functions, which are used in the formulation of the functional completeness theorem, can be defined by a finitary relation. -
Expressive Completeness
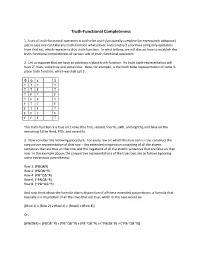
Truth-Functional Completeness 1. A set of truth-functional operators is said to be truth-functionally complete (or expressively adequate) just in case one can take any truth-function whatsoever, and construct a formula using only operators from that set, which represents that truth-function. In what follows, we will discuss how to establish the truth-functional completeness of various sets of truth-functional operators. 2. Let us suppose that we have an arbitrary n-place truth-function. Its truth table representation will have 2n rows, some true and some false. Here, for example, is the truth table representation of some 3- place truth function, which we shall call $: Φ ψ χ $ T T T T T T F T T F T F T F F T F T T F F T F T F F T F F F F T This truth-function $ is true on 5 rows (the first, second, fourth, sixth, and eighth), and false on the remaining 3 (the third, fifth, and seventh). 3. Now consider the following procedure: For every row on which this function is true, construct the conjunctive representation of that row – the extended conjunction consisting of all the atomic sentences that are true on that row and the negations of all the atomic sentences that are false on that row. In the example above, the conjunctive representations of the true rows are as follows (ignoring some extraneous parentheses): Row 1: (P&Q&R) Row 2: (P&Q&~R) Row 4: (P&~Q&~R) Row 6: (~P&Q&~R) Row 8: (~P&~Q&~R) And now think about the formula that is disjunction of all these extended conjunctions, a formula that basically is a disjunction of all the rows that are true, which in this case would be [(Row 1) v (Row 2) v (Row 4) v (Row6) v (Row 8)] Or, [(P&Q&R) v (P&Q&~R) v (P&~Q&~R) v (P&~Q&~R) v (~P&Q&~R) v (~P&~Q&~R)] 4. -

Completeness
Completeness The strange case of Dr. Skolem and Mr. G¨odel∗ Gabriele Lolli The completeness theorem has a history; such is the destiny of the impor- tant theorems, those for which for a long time one does not know (whether there is anything to prove and) what to prove. In its history, one can di- stinguish at least two main paths; the first one covers the slow and difficult comprehension of the problem in (what historians consider) the traditional development of mathematical logic canon, up to G¨odel'sproof in 1930; the second path follows the L¨owenheim-Skolem theorem. Although at certain points the two paths crossed each other, they started and continued with their own aims and problems. A classical topos of the history of mathema- tical logic concerns the how and the why L¨owenheim, Skolem and Herbrand did not discover the completeness theorem, though they proved it, or whe- ther they really proved, or perhaps they actually discovered, completeness. In following these two paths, we will not always respect strict chronology, keeping the two stories quite separate, until the crossing becomes decisive. In modern pre-mathematical logic, the notion of completeness does not appear. There are some interesting speculations in Kant which, by some stretching, could be realized as bearing some relation with the problem; Kant's remarks, however, are probably more related with incompleteness, in connection with his thoughts on the derivability of transcendental ideas (or concepts of reason) from categories (the intellect's concepts) through a pas- sage to the limit; thus, for instance, the causa prima, or the idea of causality, is the limit of implication, or God is the limit of disjunction, viz., the catego- ry of \comunance". -

Propositional Logic (PDF)
Mathematics for Computer Science Proving Validity 6.042J/18.062J Instead of truth tables, The Logic of can try to prove valid formulas symbolically using Propositions axioms and deduction rules Albert R Meyer February 14, 2014 propositional logic.1 Albert R Meyer February 14, 2014 propositional logic.2 Proving Validity Algebra for Equivalence The text describes a for example, bunch of algebraic rules to the distributive law prove that propositional P AND (Q OR R) ≡ formulas are equivalent (P AND Q) OR (P AND R) Albert R Meyer February 14, 2014 propositional logic.3 Albert R Meyer February 14, 2014 propositional logic.4 1 Algebra for Equivalence Algebra for Equivalence for example, The set of rules for ≡ in DeMorgan’s law the text are complete: ≡ NOT(P AND Q) ≡ if two formulas are , these rules can prove it. NOT(P) OR NOT(Q) Albert R Meyer February 14, 2014 propositional logic.5 Albert R Meyer February 14, 2014 propositional logic.6 A Proof System A Proof System Another approach is to Lukasiewicz’ proof system is a start with some valid particularly elegant example of this idea. formulas (axioms) and deduce more valid formulas using proof rules Albert R Meyer February 14, 2014 propositional logic.7 Albert R Meyer February 14, 2014 propositional logic.8 2 A Proof System Lukasiewicz’ Proof System Lukasiewicz’ proof system is a Axioms: particularly elegant example of 1) (¬P → P) → P this idea. It covers formulas 2) P → (¬P → Q) whose only logical operators are 3) (P → Q) → ((Q → R) → (P → R)) IMPLIES (→) and NOT. The only rule: modus ponens Albert R Meyer February 14, 2014 propositional logic.9 Albert R Meyer February 14, 2014 propositional logic.10 Lukasiewicz’ Proof System Lukasiewicz’ Proof System Prove formulas by starting with Prove formulas by starting with axioms and repeatedly applying axioms and repeatedly applying the inference rule. -

Sets, Propositional Logic, Predicates, and Quantifiers
COMP 182 Algorithmic Thinking Sets, Propositional Logic, Luay Nakhleh Computer Science Predicates, and Quantifiers Rice University !1 Reading Material ❖ Chapter 1, Sections 1, 4, 5 ❖ Chapter 2, Sections 1, 2 !2 ❖ Mathematics is about statements that are either true or false. ❖ Such statements are called propositions. ❖ We use logic to describe them, and proof techniques to prove whether they are true or false. !3 Propositions ❖ 5>7 ❖ The square root of 2 is irrational. ❖ A graph is bipartite if and only if it doesn’t have a cycle of odd length. ❖ For n>1, the sum of the numbers 1,2,3,…,n is n2. !4 Propositions? ❖ E=mc2 ❖ The sun rises from the East every day. ❖ All species on Earth evolved from a common ancestor. ❖ God does not exist. ❖ Everyone eventually dies. !5 ❖ And some of you might already be wondering: “If I wanted to study mathematics, I would have majored in Math. I came here to study computer science.” !6 ❖ Computer Science is mathematics, but we almost exclusively focus on aspects of mathematics that relate to computation (that can be implemented in software and/or hardware). !7 ❖Logic is the language of computer science and, mathematics is the computer scientist’s most essential toolbox. !8 Examples of “CS-relevant” Math ❖ Algorithm A correctly solves problem P. ❖ Algorithm A has a worst-case running time of O(n3). ❖ Problem P has no solution. ❖ Using comparison between two elements as the basic operation, we cannot sort a list of n elements in less than O(n log n) time. ❖ Problem A is NP-Complete. -

Some Analogues of the Sheffer Stroke Function in N-Valued Logic
MA THEMA TICS SOME ANALOGUES OF THE SHEFFER STROKE FUNCTION IN n-VALUED LOGIe BY NORMAN M. MARTIN (Communicated by Prof. A. HEYTING at the meeting of June 24, 1950) The interpretation of the ordinary (two-valued) propositional logic in terms of a truth-table system with values "true" and "false" or, more abstractly, the numbers "I" and "2" has become customary. This has been useful in giving an algorithm for the concept "analytic" , in giving an adequacy criterion for the definability of one function by another and it has made possible the proof of adequacy of a list of primitive terms for the definition of all truth-functions (functional completeness). If we generalize the concept of truth-function so as to allow for systems of functions of 3, 4, etc. values (preserving the "extensionality" requirement on functions examined) we obtain systems of functions of more than 2 values analogous to the truth-table interpretation of the usual pro positional calculus. The problem of functional completeness (the term is due to TURQUETTE) arises in each ofthe resulting systems. Strictly speaking, this problem is notclosely connected with problems of deducibility but is rather a combinatorial question. It will be the purpose of this paper to examine the problem of functional completeness of functions in n-valued logic where by n-valued logic we mean that system of functions such that each function of the system determines, by substitution of an arbitrary numeral a for the symbol n in the definition of the n-valued function, a function in the truth table system of a values. -

Boolean Logic
Boolean logic Lecture 12 Contents . Propositions . Logical connectives and truth tables . Compound propositions . Disjunctive normal form (DNF) . Logical equivalence . Laws of logic . Predicate logic . Post's Functional Completeness Theorem Propositions . A proposition is a statement that is either true or false. Whichever of these (true or false) is the case is called the truth value of the proposition. ‘Canberra is the capital of Australia’ ‘There are 8 day in a week.’ . The first and third of these propositions are true, and the second and fourth are false. The following sentences are not propositions: ‘Where are you going?’ ‘Come here.’ ‘This sentence is false.’ Propositions . Propositions are conventionally symbolized using the letters Any of these may be used to symbolize specific propositions, e.g. :, Manchester, , … . is in Scotland, : Mammoths are extinct. The previous propositions are simple propositions since they make only a single statement. Logical connectives and truth tables . Simple propositions can be combined to form more complicated propositions called compound propositions. .The devices which are used to link pairs of propositions are called logical connectives and the truth value of any compound proposition is completely determined by the truth values of its component simple propositions, and the particular connective, or connectives, used to link them. ‘If Brian and Angela are not both happy, then either Brian is not happy or Angela is not happy.’ .The sentence about Brian and Angela is an example of a compound proposition. It is built up from the atomic propositions ‘Brian is happy’ and ‘Angela is happy’ using the words and, or, not and if-then. -

From Fuzzy Sets to Crisp Truth Tables1 Charles C. Ragin
From Fuzzy Sets to Crisp Truth Tables1 Charles C. Ragin Department of Sociology University of Arizona Tucson, AZ 85721 USA [email protected] Version: April 2005 1. Overview One limitation of the truth table approach is that it is designed for causal conditions are simple presence/absence dichotomies (i.e., Boolean or "crisp" sets). Many of the causal conditions that interest social scientists, however, vary by level or degree. For example, while it is clear that some countries are democracies and some are not, there are many in-between cases. These countries are not fully in the set of democracies, nor are they fully excluded from this set. Fortunately, there is a well-developed mathematical system for addressing partial membership in sets, fuzzy-set theory. Section 2 of this paper provides a brief introduction to the fuzzy-set approach, building on Ragin (2000). Fuzzy sets are especially powerful because they allow researchers to calibrate partial membership in sets using values in the interval between 0 (nonmembership) and 1 (full membership) without abandoning core set theoretic principles, for example, the subset relation. Ragin (2000) demonstrates that the subset relation is central to the analysis of multiple conjunctural causation, where several different combinations of conditions are sufficient for the same outcome. While fuzzy sets solve the problem of trying to force-fit cases into one of two categories (membership versus nonmembership in a set), they are not well suited for conventional truth table analysis. With fuzzy sets, there is no simple way to sort cases according to the combinations of causal conditions they display because each case's array of membership scores may be unique. -

12 Propositional Logic
CHAPTER 12 ✦ ✦ ✦ ✦ Propositional Logic In this chapter, we introduce propositional logic, an algebra whose original purpose, dating back to Aristotle, was to model reasoning. In more recent times, this algebra, like many algebras, has proved useful as a design tool. For example, Chapter 13 shows how propositional logic can be used in computer circuit design. A third use of logic is as a data model for programming languages and systems, such as the language Prolog. Many systems for reasoning by computer, including theorem provers, program verifiers, and applications in the field of artificial intelligence, have been implemented in logic-based programming languages. These languages generally use “predicate logic,” a more powerful form of logic that extends the capabilities of propositional logic. We shall meet predicate logic in Chapter 14. ✦ ✦ ✦ ✦ 12.1 What This Chapter Is About Section 12.2 gives an intuitive explanation of what propositional logic is, and why it is useful. The next section, 12,3, introduces an algebra for logical expressions with Boolean-valued operands and with logical operators such as AND, OR, and NOT that Boolean algebra operate on Boolean (true/false) values. This algebra is often called Boolean algebra after George Boole, the logician who first framed logic as an algebra. We then learn the following ideas. ✦ Truth tables are a useful way to represent the meaning of an expression in logic (Section 12.4). ✦ We can convert a truth table to a logical expression for the same logical function (Section 12.5). ✦ The Karnaugh map is a useful tabular technique for simplifying logical expres- sions (Section 12.6). -

The Logic of Internal Rational Agent 1 Introduction
Australasian Journal of Logic Yaroslav Petrukhin The Logic of Internal Rational Agent Abstract: In this paper, we introduce a new four-valued logic which may be viewed as a variation on the theme of Kubyshkina and Zaitsev’s Logic of Rational Agent LRA [16]. We call our logic LIRA (Logic of Internal Rational Agency). In contrast to LRA, it has three designated values instead of one and a different interpretation of truth values, the same as in Zaitsev and Shramko’s bi-facial truth logic [42]. This logic may be useful in a situation when according to an agent’s point of view (i.e. internal point of view) her/his reasoning is rational, while from the external one it might be not the case. One may use LIRA, if one wants to reconstruct an agent’s way of thinking, compare it with respect to the real state of affairs, and understand why an agent thought in this or that way. Moreover, we discuss Kubyshkina and Zaitsev’s necessity and possibility operators for LRA definable by means of four-valued Kripke-style semantics and show that, due to two negations (as well as their combination) of LRA, two more possibility operators for LRA can be defined. Then we slightly modify all these modalities to be appropriate for LIRA. Finally, we formalize all the truth-functional n-ary extensions of the negation fragment of LIRA (including LIRA itself) as well as their basic modal extension via linear-type natural deduction systems. Keywords: Logic of rational agent, logic of internal rational agency, four-valued logic, logic of generalized truth values, modal logic, natural deduction, correspondence analysis. -

Lecture 1: Propositional Logic
Lecture 1: Propositional Logic Syntax Semantics Truth tables Implications and Equivalences Valid and Invalid arguments Normal forms Davis-Putnam Algorithm 1 Atomic propositions and logical connectives An atomic proposition is a statement or assertion that must be true or false. Examples of atomic propositions are: “5 is a prime” and “program terminates”. Propositional formulas are constructed from atomic propositions by using logical connectives. Connectives false true not and or conditional (implies) biconditional (equivalent) A typical propositional formula is The truth value of a propositional formula can be calculated from the truth values of the atomic propositions it contains. 2 Well-formed propositional formulas The well-formed formulas of propositional logic are obtained by using the construction rules below: An atomic proposition is a well-formed formula. If is a well-formed formula, then so is . If and are well-formed formulas, then so are , , , and . If is a well-formed formula, then so is . Alternatively, can use Backus-Naur Form (BNF) : formula ::= Atomic Proposition formula formula formula formula formula formula formula formula formula formula 3 Truth functions The truth of a propositional formula is a function of the truth values of the atomic propositions it contains. A truth assignment is a mapping that associates a truth value with each of the atomic propositions . Let be a truth assignment for . If we identify with false and with true, we can easily determine the truth value of under . The other logical connectives can be handled in a similar manner. Truth functions are sometimes called Boolean functions. 4 Truth tables for basic logical connectives A truth table shows whether a propositional formula is true or false for each possible truth assignment. -

Propositional Logic, Truth Tables, and Predicate Logic (Rosen, Sections 1.1, 1.2, 1.3) TOPICS
Propositional Logic, Truth Tables, and Predicate Logic (Rosen, Sections 1.1, 1.2, 1.3) TOPICS • Propositional Logic • Logical Operations • Equivalences • Predicate Logic Logic? What is logic? Logic is a truth-preserving system of inference Truth-preserving: System: a set of If the initial mechanistic statements are transformations, based true, the inferred on syntax alone statements will be true Inference: the process of deriving (inferring) new statements from old statements Proposi0onal Logic n A proposion is a statement that is either true or false n Examples: n This class is CS122 (true) n Today is Sunday (false) n It is currently raining in Singapore (???) n Every proposi0on is true or false, but its truth value (true or false) may be unknown Proposi0onal Logic (II) n A proposi0onal statement is one of: n A simple proposi0on n denoted by a capital leJer, e.g. ‘A’. n A negaon of a proposi0onal statement n e.g. ¬A : “not A” n Two proposi0onal statements joined by a connecve n e.g. A ∧ B : “A and B” n e.g. A ∨ B : “A or B” n If a connec0ve joins complex statements, parenthesis are added n e.g. A ∧ (B∨C) Truth Tables n The truth value of a compound proposi0onal statement is determined by its truth table n Truth tables define the truth value of a connec0ve for every possible truth value of its terms Logical negaon n Negaon of proposi0on A is ¬A n A: It is snowing. n ¬A: It is not snowing n A: Newton knew Einstein. n ¬A: Newton did not know Einstein.