On the Impact and Defeat of Regular Expression Denial of Service
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

UNIX and Computer Science Spreading UNIX Around the World: by Ronda Hauben an Interview with John Lions
Winter/Spring 1994 Celebrating 25 Years of UNIX Volume 6 No 1 "I believe all significant software movements start at the grassroots level. UNIX, after all, was not developed by the President of AT&T." Kouichi Kishida, UNIX Review, Feb., 1987 UNIX and Computer Science Spreading UNIX Around the World: by Ronda Hauben An Interview with John Lions [Editor's Note: This year, 1994, is the 25th anniversary of the [Editor's Note: Looking through some magazines in a local invention of UNIX in 1969 at Bell Labs. The following is university library, I came upon back issues of UNIX Review from a "Work In Progress" introduced at the USENIX from the mid 1980's. In these issues were articles by or inter- Summer 1993 Conference in Cincinnati, Ohio. This article is views with several of the pioneers who developed UNIX. As intended as a contribution to a discussion about the sig- part of my research for a paper about the history and devel- nificance of the UNIX breakthrough and the lessons to be opment of the early days of UNIX, I felt it would be helpful learned from it for making the next step forward.] to be able to ask some of these pioneers additional questions The Multics collaboration (1964-1968) had been created to based on the events and developments described in the UNIX "show that general-purpose, multiuser, timesharing systems Review Interviews. were viable." Based on the results of research gained at MIT Following is an interview conducted via E-mail with John using the MIT Compatible Time-Sharing System (CTSS), Lions, who wrote A Commentary on the UNIX Operating AT&T and GE agreed to work with MIT to build a "new System describing Version 6 UNIX to accompany the "UNIX hardware, a new operating system, a new file system, and a Operating System Source Code Level 6" for the students in new user interface." Though the project proceeded slowly his operating systems class at the University of New South and it took years to develop Multics, Doug Comer, a Profes- Wales in Australia. -

Ifdef Considered Harmful, Or Portability Experience with C News Henry Spencer – Zoology Computer Systems, University of Toronto Geoff Collyer – Software Tool & Die
#ifdef Considered Harmful, or Portability Experience With C News Henry Spencer – Zoology Computer Systems, University of Toronto Geoff Collyer – Software Tool & Die ABSTRACT We believe that a C programmer’s impulse to use #ifdef in an attempt at portability is usually a mistake. Portability is generally the result of advance planning rather than trench warfare involving #ifdef. In the course of developing C News on different systems, we evolved various tactics for dealing with differences among systems without producing a welter of #ifdefs at points of difference. We discuss the alternatives to, and occasional proper use of, #ifdef. Introduction portability problems are repeatedly worked around rather than solved. The result is a tangled and often With UNIX running on many different comput- impenetrable web. Here’s a noteworthy example ers, vaguely UNIX-like systems running on still more, from a popular newsreader.1 See Figure 1. Observe and C running on practically everything, many peo- that, not content with merely nesting #ifdefs, the ple are suddenly finding it necessary to port C author has #ifdef and ordinary if statements (plus the software from one machine to another. When differ- mysterious IF macros) interweaving. This makes ences among systems cause trouble, the usual first the structure almost impossible to follow without impulse is to write two different versions of the going over it repeatedly, one case at a time. code—one per system—and use #ifdef to choose the appropriate one. This is usually a mistake. Furthermore, given worst case elaboration and nesting (each #ifdef always has a matching #else), Simple use of #ifdef works acceptably well the number of alternative code paths doubles with when differences are localized and only two versions each extra level of #ifdef. -

Algorithms for Approximate String Matching Petro Protsyk (28 October 2016) Agenda
Algorithms for approximate string matching Petro Protsyk (28 October 2016) Agenda • About ZyLAB • Overview • Algorithms • Brute-force recursive Algorithm • Wagner and Fischer Algorithm • Algorithms based on Automaton • Bitap • Q&A About ZyLAB ZyLAB is a software company headquartered in Amsterdam. In 1983 ZyLAB was the first company providing a full-text search program for MS-DOS called ZyINDEX In 1991 ZyLAB released ZyIMAGE software bundle that included a fuzzy string search algorithm to overcome scanning and OCR errors. Currently ZyLAB develops eDiscovery and Information Governance solutions for On Premises, SaaS and Cloud installations. ZyLAB continues to develop new versions of its proprietary full-text search engine. 3 About ZyLAB • We develop for Windows environments only, including Azure • Software developed in C++, .Net, SQL • Typical clients are from law enforcement, intelligence, fraud investigators, law firms, regulators etc. • FTC (Federal Trade Commission), est. >50 TB (peak 2TB per day) • US White House (all email of presidential administration), est. >20 TB • Dutch National Police, est. >20 TB 4 ZyLAB Search Engine Full-text search engine • Boolean and Proximity search operators • Support for Wildcards, Regular Expressions and Fuzzy search • Support for numeric and date searches • Search in document fields • Near duplicate search 5 ZyLAB Search Engine • Highly parallel indexing and searching • Can index Terabytes of data and millions of documents • Can be distributed • Supports 100+ languages, Unicode characters 6 Overview Approximate string matching or fuzzy search is the technique of finding strings in text or dictionary that match given pattern approximately with respect to chosen edit distance. The edit distance is the number of primitive operations necessary to convert the string into an exact match. -
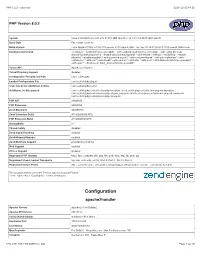
PHP 8.0.2 - Phpinfo() 2021-02-23 14:53
PHP 8.0.2 - phpinfo() 2021-02-23 14:53 PHP Version 8.0.2 System Linux effa5f35b7e3 5.4.83-v7l+ #1379 SMP Mon Dec 14 13:11:54 GMT 2020 armv7l Build Date Feb 9 2021 12:01:16 Build System Linux 96bc8a22765c 4.15.0-129-generic #132-Ubuntu SMP Thu Dec 10 14:07:05 UTC 2020 armv8l GNU/Linux Configure Command './configure' '--build=arm-linux-gnueabihf' '--with-config-file-path=/usr/local/etc/php' '--with-config-file-scan- dir=/usr/local/etc/php/conf.d' '--enable-option-checking=fatal' '--with-mhash' '--with-pic' '--enable-ftp' '--enable- mbstring' '--enable-mysqlnd' '--with-password-argon2' '--with-sodium=shared' '--with-pdo-sqlite=/usr' '--with- sqlite3=/usr' '--with-curl' '--with-libedit' '--with-openssl' '--with-zlib' '--with-pear' '--with-libdir=lib/arm-linux-gnueabihf' '- -with-apxs2' '--disable-cgi' 'build_alias=arm-linux-gnueabihf' Server API Apache 2.0 Handler Virtual Directory Support disabled Configuration File (php.ini) Path /usr/local/etc/php Loaded Configuration File /usr/local/etc/php/php.ini Scan this dir for additional .ini files /usr/local/etc/php/conf.d Additional .ini files parsed /usr/local/etc/php/conf.d/docker-php-ext-gd.ini, /usr/local/etc/php/conf.d/docker-php-ext-mysqli.ini, /usr/local/etc/php/conf.d/docker-php-ext-pdo_mysql.ini, /usr/local/etc/php/conf.d/docker-php-ext-sodium.ini, /usr/local/etc/php/conf.d/docker-php-ext-zip.ini PHP API 20200930 PHP Extension 20200930 Zend Extension 420200930 Zend Extension Build API420200930,NTS PHP Extension Build API20200930,NTS Debug Build no Thread Safety disabled Zend Signal Handling enabled -

MC-1200 Series Linux Software User's Manual
MC-1200 Series Linux Software User’s Manual Version 1.0, November 2020 www.moxa.com/product © 2020 Moxa Inc. All rights reserved. MC-1200 Series Linux Software User’s Manual The software described in this manual is furnished under a license agreement and may be used only in accordance with the terms of that agreement. Copyright Notice © 2020 Moxa Inc. All rights reserved. Trademarks The MOXA logo is a registered trademark of Moxa Inc. All other trademarks or registered marks in this manual belong to their respective manufacturers. Disclaimer Information in this document is subject to change without notice and does not represent a commitment on the part of Moxa. Moxa provides this document as is, without warranty of any kind, either expressed or implied, including, but not limited to, its particular purpose. Moxa reserves the right to make improvements and/or changes to this manual, or to the products and/or the programs described in this manual, at any time. Information provided in this manual is intended to be accurate and reliable. However, Moxa assumes no responsibility for its use, or for any infringements on the rights of third parties that may result from its use. This product might include unintentional technical or typographical errors. Changes are periodically made to the information herein to correct such errors, and these changes are incorporated into new editions of the publication. Technical Support Contact Information www.moxa.com/support Moxa Americas Moxa China (Shanghai office) Toll-free: 1-888-669-2872 Toll-free: 800-820-5036 Tel: +1-714-528-6777 Tel: +86-21-5258-9955 Fax: +1-714-528-6778 Fax: +86-21-5258-5505 Moxa Europe Moxa Asia-Pacific Tel: +49-89-3 70 03 99-0 Tel: +886-2-8919-1230 Fax: +49-89-3 70 03 99-99 Fax: +886-2-8919-1231 Moxa India Tel: +91-80-4172-9088 Fax: +91-80-4132-1045 Table of Contents 1. -

Security Analysis of Firefox Webextensions
6.857: Computer and Network Security Due: May 16, 2018 Security Analysis of Firefox WebExtensions Srilaya Bhavaraju, Tara Smith, Benny Zhang srilayab, tsmith12, felicity Abstract With the deprecation of Legacy addons, Mozilla recently introduced the WebExtensions API for the development of Firefox browser extensions. WebExtensions was designed for cross-browser compatibility and in response to several issues in the legacy addon model. We performed a security analysis of the new WebExtensions model. The goal of this paper is to analyze how well WebExtensions responds to threats in the previous legacy model as well as identify any potential vulnerabilities in the new model. 1 Introduction Firefox release 57, otherwise known as Firefox Quantum, brings a large overhaul to the open-source web browser. Major changes with this release include the deprecation of its initial XUL/XPCOM/XBL extensions API to shift to its own WebExtensions API. This WebExtensions API is currently in use by both Google Chrome and Opera, but Firefox distinguishes itself with further restrictions and additional functionalities. Mozilla’s goals with the new extension API is to support cross-browser extension development, as well as offer greater security than the XPCOM API. Our goal in this paper is to analyze how well the WebExtensions model responds to the vulnerabilities present in legacy addons and discuss any potential vulnerabilities in the new model. We present the old security model of Firefox extensions and examine the new model by looking at the structure, permissions model, and extension review process. We then identify various threats and attacks that may occur or have occurred before moving onto recommendations. -

Implementation of the Programming Language Dino – a Case Study in Dynamic Language Performance
Implementation of the Programming Language Dino – A Case Study in Dynamic Language Performance Vladimir N. Makarov Red Hat [email protected] Abstract design of the language, its type system and particular features such The article gives a brief overview of the current state of program- as multithreading, heterogeneous extensible arrays, array slices, ming language Dino in order to see where its stands between other associative tables, first-class functions, pattern-matching, as well dynamic programming languages. Then it describes the current im- as Dino’s unique approach to class inheritance via the ‘use’ class plementation, used tools and major implementation decisions in- composition operator. cluding how to implement a stable, portable and simple JIT com- The second part of the article describes Dino’s implementation. piler. We outline the overall structure of the Dino interpreter and just- We study the effect of major implementation decisions on the in-time compiler (JIT) and the design of the byte code and major performance of Dino on x86-64, AARCH64, and Powerpc64. In optimizations. We also describe implementation details such as brief, the performance of some model benchmark on x86-64 was the garbage collection system, the algorithms underlying Dino’s improved by 3.1 times after moving from a stack based virtual data structures, Dino’s built-in profiling system, and the various machine to a register-transfer architecture, a further 1.5 times by tools and libraries used in the implementation. Our goal is to give adding byte code combining, a further 2.3 times through the use an overview of the major implementation decisions involved in of JIT, and a further 4.4 times by performing type inference with a dynamic language, including how to implement a stable and byte code specialization, with a resulting overall performance im- portable JIT. -

Red Hat Virtualization 4.4 Package Manifest
Red Hat Virtualization 4.4 Package Manifest Package listing for Red Hat Virtualization 4.4 Last Updated: 2021-09-09 Red Hat Virtualization 4.4 Package Manifest Package listing for Red Hat Virtualization 4.4 Red Hat Virtualization Documentation Team Red Hat Customer Content Services [email protected] Legal Notice Copyright © 2021 Red Hat, Inc. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/ . In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. -

Usenet News HOWTO
Usenet News HOWTO Shuvam Misra (usenet at starcomsoftware dot com) Revision History Revision 2.1 2002−08−20 Revised by: sm New sections on Security and Software History, lots of other small additions and cleanup Revision 2.0 2002−07−30 Revised by: sm Rewritten by new authors at Starcom Software Revision 1.4 1995−11−29 Revised by: vs Original document; authored by Vince Skahan. Usenet News HOWTO Table of Contents 1. What is the Usenet?........................................................................................................................................1 1.1. Discussion groups.............................................................................................................................1 1.2. How it works, loosely speaking........................................................................................................1 1.3. About sizes, volumes, and so on.......................................................................................................2 2. Principles of Operation...................................................................................................................................4 2.1. Newsgroups and articles...................................................................................................................4 2.2. Of readers and servers.......................................................................................................................6 2.3. Newsfeeds.........................................................................................................................................6 -

Mozilla/Firefox: MDN Web Docs, Recommended Extensions and Tenfourfox FPR23 for Intel
Published on Tux Machines (http://www.tuxmachines.org) Home > content > Mozilla/Firefox: MDN Web Docs, Recommended Extensions and TenFourFox FPR23 for Intel Mozilla/Firefox: MDN Web Docs, Recommended Extensions and TenFourFox FPR23 for Intel By Rianne Schestowitz Created 12/06/2020 - 5:32am Submitted by Rianne Schestowitz on Friday 12th of June 2020 05:32:58 AM Introducing the MDN Web Docs Front-end developer learning pathway[1] The MDN Web Docs Learning Area (LA) was first launched in 2015, with the aim of providing a useful counterpart to the regular MDN reference and guide material. MDN had traditionally been aimed at web professionals, but we were getting regular feedback that a lot of our audience found MDN too difficult to understand, and that it lacked coverage of basic topics. Fast forward 5 years, and the Learning Area material is well-received. It boasts around 3.5?4 million page views per month; a little under 10% of MDN Web Docs? monthly web traffic. At this point, the Learning Area does its job pretty well. A lot of people use it to study client- side web technologies, and its loosely-structured, unopinionated, modular nature makes it easy to pick and choose subjects at your own pace. Teachers like it because it is easy to include in their own courses. Recommended extensions ? recent additions [2] When the Recommended Extensions program debuted last year, it listed about 60 extensions. Today the program has grown to just over a hundred as we continue to evaluate new nominations and carefully grow the list. The curated collection grows slowly because one of the program?s goals is to cultivate a fairly fixed list of content so users can feel confident the Recommended extensions they install will be monitored for safety and security for the foreseeable future. -

Introduction to HTML/CSS/SVG/D3
D3 Tutorial Introduction of Basic Components: HTML, CSS, SVG, and JavaScript D3.js Setup Edit by Jiayi Xu and Han-Wei SHen, THe OHio State University HTML - Hyper Text Markup Language • HTML is the standard markup language for creating Web pages • HTML describes the structure of Web pages using markup • HTML elements • HTML elements are the building blocks of HTML pages • represented by tags • Tags • HTML tags label pieces of content such as • <head> tag for “heading” • <p> for “paragraph” • <table> for “table” and so on • Browsers do not display the HTML tags, but use them to render the content of the page HTML - Plain Text • If we display the information only by plain text HTML Basics HTML is designed for marking up text by adding tags such as <p> to create HTML elements. Example image: HTML - Codes and the Result HTML - DOM • When a web page is loaded, the browser creates a Document Object Model of the page • The HTML DOM model is constructed as a tree of Objects HTML - DOM Document Root element: <html> Element: Element: <head> <body> Element: Element: Element: Element: <p> Element: <p> <title> <h1> <img> "to create Text: "HTML Text: "HTML Element "is designed Element: "by adding Element Element: Attribute: Attribute: HTML Tutorial" Basics" <strong> for" <em> tags such as" <code> <strong> "src" "style" elements. " "marking up “Example "HTML" "<p>" text" image” HTML - DOM • With the object model, JavaScript can create dynamic HTML by manipulating the objects: • JavaScript can change all the HTML elements in the page • Change all the -

Quentin Tarantino Retro
ISSUE 59 AFI SILVER THEATRE AND CULTURAL CENTER FEBRUARY 1– APRIL 18, 2013 ISSUE 60 Reel Estate: The American Home on Film Loretta Young Centennial Environmental Film Festival in the Nation's Capital New African Films Festival Korean Film Festival DC Mr. & Mrs. Hitchcock Screen Valentines: Great Movie Romances Howard Hawks, Part 1 QUENTIN TARANTINO RETRO The Roots of Django AFI.com/Silver Contents Howard Hawks, Part 1 Howard Hawks, Part 1 ..............................2 February 1—April 18 Screen Valentines: Great Movie Romances ...5 Howard Hawks was one of Hollywood’s most consistently entertaining directors, and one of Quentin Tarantino Retro .............................6 the most versatile, directing exemplary comedies, melodramas, war pictures, gangster films, The Roots of Django ...................................7 films noir, Westerns, sci-fi thrillers and musicals, with several being landmark films in their genre. Reel Estate: The American Home on Film .....8 Korean Film Festival DC ............................9 Hawks never won an Oscar—in fact, he was nominated only once, as Best Director for 1941’s SERGEANT YORK (both he and Orson Welles lost to John Ford that year)—but his Mr. and Mrs. Hitchcock ..........................10 critical stature grew over the 1960s and '70s, even as his career was winding down, and in 1975 the Academy awarded him an honorary Oscar, declaring Hawks “a giant of the Environmental Film Festival ....................11 American cinema whose pictures, taken as a whole, represent one of the most consistent, Loretta Young Centennial .......................12 vivid and varied bodies of work in world cinema.” Howard Hawks, Part 2 continues in April. Special Engagements ....................13, 14 Courtesy of Everett Collection Calendar ...............................................15 “I consider Howard Hawks to be the greatest American director.