Comodo Web Application Firewall Administartor Guide for Directadmin
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Sistem Pendukung Keputusan Dalam Pemilihan Control Panel Virtual Private Server Menggunakan Metode AHP Dan SAW
Citec Journal, Vol. 5, No. 1, November 2017 – Januari 2018 ISSN: 2460-4259 14 Sistem Pendukung Keputusan Dalam Pemilihan Control Panel Virtual Private Server Menggunakan Metode AHP dan SAW Decision Support System in Selection of a Control Panel Virtual Private Server Using AHP and SAW Method Arwendra Adi Putra*1, Kusrini 2, Eko Pramono3 1,2,3Magister Teknik Informatika, Universitas Amikom Yogyakarta E-mail: [email protected], [email protected], [email protected] Abstrak Hosting dapat dibedakan menjadi berbagai macam type, salah satunya adalah Virtual Private Server (VPS). VPS merupakan sebuah cara untuk membagi sumber daya sebuah physical server menjadi server virtual. Sebuah VPS memerlukan control panel karena untuk mempermudah pengaturan seperti mengelola email, disk, database, penambahan domain, memonitor bandwidth dan backup data. Terdapat berbagai macam control panel dengan spesifikasi yang berbeda-beda. Pemilihan control panel tersebut sangat penting karena control panel tersebut harus disesuaikan dengan spesifikasi VPS. Berdasarkan permasalahan tersebut, diperlukan sistem yang dapat membantu dalam pengambilan keputusan dalam pemilihan control panel. Metode yang digunakan dalam penelitian ini adalah dengan menggunakan metode Analitical Hierarcy Process (AHP) dan Simple Additive Weighting (SAW). Metode AHP digunakan untuk mencari bobot variabel kriteria, sedangkan metode SAW digunakan untuk menentukan nilai akhir dan perangkingan. Hasil perangkingan alternatif control panel pada sistem ini menunjukkan hasil yang sama dengan hasil perangkingan dari pakar control panel, sehingga sistem ini dapat digunakan oleh pengguna sebagai dasar pengambilan keputusan dalam menentukan pemilihan alternatif control panel. Kata Kunci — control panel, VPS, AHP, SAW, sistem pendukung keputusan Abstract Hosting can be divided into various types, one of them is Virtual Private Server (VPS). -

Sun Microsystems Solaris 10 What's
Solaris 10 What’s New Sun Microsystems, Inc. 4150 Network Circle Santa Clara, CA 95054 U.S.A. Part No: 817–0547–15 January 2005 Copyright 2005 Sun Microsystems, Inc. 4150 Network Circle, Santa Clara, CA 95054 U.S.A. All rights reserved. This product or document is protected by copyright and distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this product or document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Third-party software, including font technology, is copyrighted and licensed from Sun suppliers. Parts of the product may be derived from Berkeley BSD systems, licensed from the University of California. UNIX is a registered trademark in the U.S. and other countries, exclusively licensed through X/Open Company, Ltd. Sun, Sun Microsystems, the Sun logo, docs.sun.com, AnswerBook, AnswerBook2, SunVTS, Java, J2SE, J2EE, JavaServer, JumpStart, Sun Fire, StarOffice, Sun Blade, Sun Ray, Solstice Enterprise Agents, CacheFS, Sun StorEdge, and Solaris are trademarks or registered trademarks of Sun Microsystems, Inc. in the U.S. and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the U.S. and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. FireWire is a trademark of Apple Computer, Inc., used under license. Netscape and Netscape Navigator are trademarks or registered trademarks of Netscape Communications Corporation. Mozilla is a trademark or registered trademark of Netscape Communications Corporation in the United States and other countries. -

Subject: VPS Services and Templates Posted by Touchvps on Sun, 13 Apr
Subject: VPS Services and templates Posted by touchvps on Sun, 13 Apr 2008 13:07:17 GMT View Forum Message <> Reply to Message We offer custom templates with any request by customer , we also have ready to go some templates : Custom OS Template cPanel: Fedora Core 5 or Centos 5 cPanel + Fantastico with support for ffmpeg: Installed FFmpeg Modules FFmpeg & FFmpeg-php Libogg & Libvorbis Flv2tool LAME MP3 Encoder Mplayer Mencoder GD Library You can run scripts like clip-share vshare youtube , phpfox, phpmotion etc... Fedora Core 8 with Gnome , directly access to your Desktop via RealVNC + a lot of scripts installed like openoffice , browsers , putty , mirc , etc... Debian 4 + VHCS2 ready to go for you with many ssh tools for your help. you can contact us with your request directly to email [email protected] or visit our website www.touchvps.eu Subject: Re: VPS Services and templates Posted by kir on Sun, 13 Apr 2008 19:07:45 GMT View Forum Message <> Reply to Message If you have those templates for download, please add yourself to http://wiki.openvz.org/Partners. If you provide OpenVZ-based hosting, please add yourself to http://wiki.openvz.org/Hosting. Subject: Re: VPS Services and templates Posted by SoftDux on Thu, 17 Apr 2008 08:10:43 GMT View Forum Message <> Reply to Message I presume those templates incur some costs, and are not for free? Subject: Re: VPS Services and templates Posted by touchvps on Thu, 17 Apr 2008 08:33:27 GMT View Forum Message <> Reply to Message Page 1 of 3 ---- Generated from OpenVZ Forum SoftDux wrote on Thu, 17 April 2008 04:10I presume those templates incur some costs, and are not for free? right true, and price start from $8 for template one-time and +support , updates 1 year , so is more than cheaper. -

Godaddy's Hosting Services System Description Updated
GoDaddy’s Hosting Services System Description Background GoDaddy, based in Scottsdale, Arizona, provides a broad range of internet business software and services. GoDaddy’s hosting services refer to the housing, maintenance, and provision of internet service (bandwidth) to servers. GoDaddy offers the following hosting services which are covered by this system overview: • Web Hosting including cPanel for Linux, Parallels Plesk for Windows, and legacy Shared/Grid Hosting products (4GH) • WordPress Hosting • Servers – Dedicated and Virtual Private GoDaddy’s hosting services are housed in the following domestic and international data center locations, with the breakdown of hosting services as referenced in the table below: Data cPanel Plesk Legacy WordPress Dedicated Virtual Center Shared Private Virginia √ √ √ √ √ Arizona √ √ √ √ √ √ Netherlands √ √ √ √ √ Germany √ Singapore √ √ √ √ Infrastructure Shared web hosting services and WordPress hosting house multiple customers in a single server cluster, following a multi-tenant architecture. Customers interact with their hosting environment using the applicable control panel – cPanel for Linux, Parallels Plesk for Windows, and Hosting Control Center (HCC) for the legacy shared environment. Customers manage their own content including information stored on MySQL and MSSQL customer databases. Customers are also responsible for website setup and backups. GoDaddy manages system and hardware level security and patching. Updated: December 30, 2019 Page 1 GoDaddy’s Hosting Services System Description Dedicated servers in VA and AZ provide customers with an entire single-tenant virtual server housed on a single hypervisor1. Initial configuration is performed by provisioning code on the hypervisor based on customer elections made during the setup process. The customer manages system level access and is responsible for server setup, security, patching, and backups while GoDaddy manages hardware level security for all dedicated servers. -
For Your Linux Server
cPanel // Linux Server Getting Started Guide cPanel for your Linux Server AKJZNAzsqknsxxkjnsjx Getting Started Guide Page 1 cPanel // Linux Server Getting Started Guide: cPanel, Linux Server Version 2.2 (1.6.2012) © Copyright 2012. All rights reserved. Distribution of this work or derivative of this work is prohibited unless prior written permission is obtained from the copyright holder. Trademarks used in this book Linux® is a registered trademark of Linus Torvalds. cPanel® is a registered trademark of cPanel, Inc. SSH® and Secure Shell® are trademarks of SSH Communications Security, Inc. RedHat® and Fedora® are registered trademarks of Red Hat Software, Inc. Mac® is a registered trademark of Apple Computer, Inc. UNIX® is a registered trademark of The Open Group. Windows XP®, Entourage®, and Outlook® are registered trademarks of Microsoft Corporation in the United States and/or other countries. Thunderbird™ is an unregistered trademark of the Mozilla Foundation. All other trademarks and copyrights are the property of their respective owners. AKJZNAzsqknsxxkjnsjx Getting Started Guide Page 2 cPanel // Linux Server Table of Contents Introduction 5 SECURITY INFORMATION! 5 REPROVISIONING YOUR SERVER! 6 GETTING HELP! 7 OTHER RESOURCES! 9 Setting Up Your Dedicated Server 10 CHOOSING A HOST NAME, USER ID, AND PASSWORD! 10 LOGGING IN TO YOUR MANAGER FOR THE FIRST TIME! 13 Connecting to Your Dedicated Server 14 CONNECTING TO YOUR SERVER USING WHM! 15 CONNECTING TO YOUR SERVER USING SSH! 20 GAINING ROOT ACCESS ON YOUR SERVER! 22 AKJZNAzsqknsxxkjnsjx -

The Ultimate Guide to Web Hosting for Beginners. Don't Be
Welcome to the Ultimate Guide to Web Hosting for Beginners. Don’t be fooled by the name – this is a top-notch exhaustive resource, for new website owners and veterans alike, created by hosting experts with years of experience. Our mission: to help you save money and avoid hosting scams. Your part: please be kind and share this guide with someone. We made it to help you choose the right hosting, make the most of it and save big bucks on the long run. Here’s what this guide covers: VPS, Cloud and Dedicated hosting: types, pricing and technologies How to choose the right OS SEO and web hosting Installing WordPress in 5 easy steps The common dirty tricks of web hosting companies (and how to avoid them) The Most important features in shared web hosting To make the most of the information we’ve gathered here for you, we recommend taking these articles one at a time. Be sure to keep a notepad and a pen with you, because there will be some stuff you may want to write down. And now, 1. We hope you enjoy reading this guide as much as we had enjoyed writing it 2. Keep safe out there, and open your eyes to avoid scams and dirty tricks 3. Feel free to ask us anything. We’re at http://facebook.com/HostTracer 4. Please consider sharing your hosting experience with us on our community, at http://hosttracer.com Good luck! Idan Cohen, Eliran Ouzan, Max Ostryzhko and Amos Weiskopf Table of Contents Chapter 1: Introduction, and a Hosting Glossary ................................................. -

How to Install Webmin/Virtualmin in Linux (Centos 7)
Advanced Network/System Administration and Security Workshop ECE Building, Building, BUET, Dhaka Date: 10-12 December 2019 How to Install Webmin/Virtualmin in Linux (CentOS 7) What Is Virtualmin? Virtualmin is a Webmin module that is typically used to manage multiple virtual hosts through a single interface, similar to cPanel. It supports multiple functions such as creating/managing Apache virtual hosts, MySQL database creation/management, generating DNS zones, managing mailboxes, and much more. How Do I Install Virtualmin On CentOS 7? This guide implies that you’re using the root account on Cloud, VPS or Dedicated Server to perform the installation and that you have a basic working knowledge of a Linux shell. We highly suggest taking a backup of your server prior to proceeding with this script. Although this document is written for CentOS 7, Virtualmin offers an automated installation script for the following distros: • CentOS/RHEL/Scientific Linux 7 on x86_64 • CentOS/RHEL/Scientific Linux 5 and 6 on i386 or x86_64 • Debian 6, 7, and 8 on i386 or amd64 • Ubuntu 12.04 LTS, 14.04 LTS, and 16.04 LTS on i386 or amd64 (non-LTS releases are not supported) The following steps can be utilized to install Virtualmin in a CentOS 7 (RHEL 7) environment on a fresh OS installation. 1. Ensure your server is up to date sudo yum update -y 2. Download the Virtualmin installer script using wget sudo wget http://software.virtualmin.com/gpl/scripts/install.sh 3. Execute the install script Md. Ariful Islam Manager (Data & Transmission Network), BdREN E-mail: [email protected] Advanced Network/System Administration and Security Workshop ECE Building, Building, BUET, Dhaka Date: 10-12 December 2019 sudo sh install.sh As per the warning when the script is executed ensure that your OS is listed and type “y” then press “Enter” to continue with the installation If prompted you may need to enter in a fully qualified hostname. -

Teaching Guide- Cyberpiprojects System Admin Interface Pi
Teaching Guide- CyberPiProjects System Admin Interface Pi Teacher Overview Raspbian is a Debian-based computer operating system for the Raspberry Pi computer. There are several versions of Raspbian including: Raspbian Stretch and Raspbian Jessie. Raspbian was created by Mike Thompson and Peter Green as an independent project, with an initial build completed in June 2012. Since 2015, Raspbian has been officially provided by the Raspberry Pi Foundation as its primary operating system for the family of Raspberry Pi single-board computers and is highly optimized for the Raspberry Pi line's low-performance ARM CPUs. The internet of things, or IoT, is a system of interrelated computing devices, mechanical and digital machines, objects, animals or people that are provided with unique identifiers (UIDs) and the ability to transfer data over a network without requiring human-to-human or human-to-computer interaction. IoT devices could be a person with a heart monitor implant, a farm animal with a biochip transponder, an automobile that has built-in sensors to alert the driver when tire pressure is low or any other natural or man-made object that can be assigned an IP address and is able to transfer data over a network. Increasingly, organisations in a variety of industries are using IoT to operate more efficiently, better understand customers to deliver enhanced customer service, improve decision-making and increase the value of the business. In this project you will go through all the steps to set up the Webmin software package for the Raspbian operating system. Webmin is an excellent capability if you wish to have a web-based interface for system administration. -

Raspberry Pi Home Page Introduction to the Raspberry Pi 3 Video (20 Min)
Raspberry Pi home page https://www.raspberrypi.org/ Introduction to the Raspberry Pi 3 video (20 min): https://www.youtube.com/watch?v=-6OGuhLtKbU This document is about using 15 – 20 Raspberry Pis to implement an Internet Café or Learning Center. An internet café allows people to rent computers to access the internet. A learning center will be slightly different to set up, it will allow classroom learning to be augmented by the computer. The Raspberry Pi is a very small computer, about the size of a deck of cards. It uses an ARM processor like many smart phones, and so is incompatible with most PC software. You can run various versions of Linux on it, the most popular is Raspbian, a Linux based on Debian. The standard implementation includes office and productivity software, math software, and some other educational programs. The Raspberry Pi is a bare computer, you also need a monitor, a keyboard and mouse, and a power supply to turn it into a desktop computer system. Raspberry Pi 3 Model B Raspberry Pi with case, mouse, keyboard, and monitor Monitors Raspberry Pis have an HDMI video output. You could use HDMI compatible monitors: HDMI Monitor: SCEPTRE E205W-1600 20" $79.99 from Newegg, $69.99 from Walmart If you have old VGA monitors you need a HDMI to VGA adaptor with a power input, raspberry pi's HDMI port do not provide enough power to run the adaptor, but you can hook up to the USB port for power. (HDMI 50 mA, USB 500 mA, raspberry pi USB 1.2 A total (all usb ports) if you put max_usb_current=1 in /boot/config.txt) We had some strange side effects from pulling too much current from the R-pi usb ports, we could get to some web sites in the browser, but not others. -
Spamexperts Incoming Email Filter a Powerful Solution to Safeguard Networks from Inbound Spam and Malware, Helping Web Hosts Save Time and Money
DATASHEET SpamExperts Incoming Email Filter A powerful solution to safeguard networks from inbound spam and malware, helping web hosts save time and money. Inbound spam, ransomware, and phishing attempts can put any internet service provider at risk. N-able™ SpamExperts helps web hosts and ISPs/telcos strengthen email protection. Services include affordable inbound filtering driven by a continuously updated Intelligent Protection & Filtering Engine to meet emerging threats. The solution can be deployed in a redundant cloud environment or on premises. How it works: N-able SpamExperts incoming spam filter is an email gateway solution. Activation is done with a simple DNS adjustment. Once the MX records are changed, all inbound email goes to our system first, where it is filtered and then relayed to the unchanged destination mail servers of your clients. It provides first-level defense running in front of your mail infrastructure and separates legitimate from unsolicited email with the help of advanced filtering algorithms and spam pattern detection methods. It offers full inbox protection with a nearly 100% accuracy rate. Potentially harmful messages are queued in quarantine and can be managed by end users. Helps save resources and money • Protects networks against the latest email-based threats. • Saves network resources with an efficient first-level incoming filter defense. • Helps save money with competitive and affordable licenses. Offers dual deployment options and integrates with a broad range of tools • Cloud or on-premises deployment. • Free add-ons to integrate with the most popular control panels and other email collaboration tools. • Multiple branding options available. Global statistics Gives customers and users visibility and control over their email flows • Empowers users to manage their email flows and gain real-time visibility into threats. -

Control Panels
Control Panels cPanel Plesk Direct Admin Other Control Panels Docker cPanel Intro CrossBox for cPanel is one of our most popular control panel integrations. It's Plug-and-Play in its core, covering 95% of all cPanel setups out of the box. Our deep integration with cPanel hooks and APIs enables an automated and fine- tuned experience for both the end-user and service provider. All data and computing are 100% hosted/done on the cPanel server. Benefits End-users: Easy access either via cPanel's webmail system or direct URL No complicated IMAP/SMTP/POP3 configuration, only email address, and password are required Instant access to Email Chat Audio/video calls Conferences Files Contacts And many other features, directly integrated with a cPanel hosting account Real-time push notifications Change password within CrossBox Recover access to an email account Service Providers: Provide users with a modern communication suite that is deeply integrated with and running on a cPanel server Easier customer onboarding Better brand exposure No changes to the cPanel server, services, or configuration files needed Everything is 100% hosted on the cPanel server itself cPanel account quota support WHM Feature List support Automatic cPanel Integration MTA/Mail Server CrossBox supports Exim and Dovecot out of the box, and won't make any changes to your existing MTA/mail server configuration. From standard Exim configurations to smart external relays, CrossBox supports any configuration. Webmail cPanel users can choose CrossBox as their Webmail Application of choice when accessing cPanel's Webmail. Note that if you have a Branding Addon purchased, the cPanel Webmail interface will show your custom App Logo. -
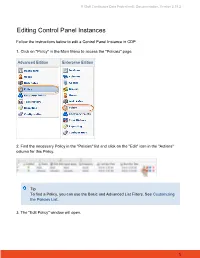
Editing Control Panel Instances
R1Soft Continuous Data Protection®, Documentation, Version 3.18.2 Editing Control Panel Instances Follow the instructions below to edit a Control Panel Instance in CDP. 1. Click on "Policy" in the Main Menu to access the "Policies" page. Advanced Edition Enterprise Edition 2. Find the necessary Policy in the "Policies" list and click on the "Edit" icon in the "Actions" column for this Policy. Tip To find a Policy, you can use the Basic and Advanced List Filters. See Customizing the Policies List. 3. The "Edit Policy" window will open. 1 R1Soft Continuous Data Protection®, Documentation, Version 3.18.2 4. Choose the "Control Panels" tab. 5. Then you will access the "Control Panel Instance" list on the "Control Panels" tab. 6. Find the necessary Instance in the "Control Panel Instance" list and click on the "Edit" icon in the "Actions" column for this Instance. 2 R1Soft Continuous Data Protection®, Documentation, Version 3.18.2 7. The "Edit Control Panel Instance" window will appear. Familiarize yourself with the introductory information and click "Next" to proceed with adding the Instance. 8. On the following "Instance Details" screen you can change options for your Control Panel Instance: Enabled - Use this checkbox to enable or disable the Control Panel Instance. If an instance is disabled, it will not be discovered during replication, and control panel users will not be able to access their data from any recovery points created while the instance is disabled. Name - Define a new name for the Control Panel Instance to identify it. A control panel instance's name must be unique to its policy, meaning no more than one instance associated with a policy can have a certain name.