Rcanalyzer: Visual Analytics of Rare Categories in Dynamic Networks∗
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Antiferromagnetic Element Mn Modified Ptco Truncated Octahedral Nanoparticles with Enhanced Activity and Durability for Direct Methanol Fuel Cells
Electronic Supplementary Material Antiferromagnetic element Mn modified PtCo truncated octahedral nanoparticles with enhanced activity and durability for direct methanol fuel cells Qiqi Zhang1,§, Jialong Liu2,§, Tianyu Xia3 (), Jie Qi1, Haochang Lyu1, Baoyuan Luo1, Rongming Wang4, Yizhong Guo5, Lihua Wang5, and Shouguo Wang1,4 () 1 Beijing Advanced Innovation Center for Materials Genome Engineering, School of Materials Science and Engineering, University of Science and Technology Beijing, Beijing 100083, China 2 Institute of Geology and Geophysics, Chinese Academy of Sciences, Beijing 100029, China 3 Key Laboratory of Material Physics of Ministry of Education, School of Physics and Engineering, Zhengzhou University, Zhengzhou 450052, China 4 Institute for multidisciplinary Innovation, University of Science and Technology Beijing, Beijing 100083, China 5 Beijng Key Lab of Microstructure and Property of Advanced Materials, Beijing University of Technology, Beijing 100124, China § Qiqi Zhang and Jialong Liu contributed equally to this work. Supporting information to https://doi.org/10.1007/s12274-019-2479-4 Figure S1 (a-d) TEM images of Mn-PtCo TONPs with different Mn contents, inset: size distribution and high-resolution image with scale bar of 2 nm. Address correspondence to Tianyu Xia, [email protected]; Shouguo Wang, [email protected] Nano Res. Figure S2 (a-c) TEM image of Pt, PtCo, PtMn NPs prepared by the same experimental conditions, respectively. Figure S3 (a-f) TEM image of Mn-PtCo-3 samples acquired with reaction time of 1h, 2h, 3h, 4h, 12h, 16h, respectively. Figure S4 (a) TEM image of as-prepared sample with precursors replaced by K2PtCl6, CoCl2∙6H2O, and MnCl2∙4H2O. (b) TEM image of as-prepared sample with DMF replaced by OAm. -

Settlement Prediction of Foundation Pit Excavation Based on the GWO-ELM Model Considering Different States of Influence
Hindawi Advances in Civil Engineering Volume 2021, Article ID 8896210, 11 pages https://doi.org/10.1155/2021/8896210 Research Article Settlement Prediction of Foundation Pit Excavation Based on the GWO-ELM Model considering Different States of Influence Qiao Shi-fan,1 Tan Jun-kun,1 Zhang Yong-gang ,2 Wan Li-jun,3 Zhang Ming-fei,4 Tang Jun,5 and He Qing6 1School of Civil Engineering, Central South University, Changsha 410083, China 2Key Laboratory of Geotechnical and Underground Engineering of Ministry of Education and Department of Geotechnical Engineering, Tongji University, Shanghai 200092, China 3Railway Engineering Research Institute, China Academy of Railway Science Co., Ltd., Beijing 12 100081, China 4Civil Engineering and Architecture Institute, Zhengzhou University of Aeronautics, Zhengzhou 450046, China 5College of Civil Engineering, Huaqiao University, Xiamen 361000, China 6School of Geotechnical Engineering, China University of Mining and Technology (Beijing), Beijing 100083, China Correspondence should be addressed to Zhang Yong-gang; [email protected] Received 12 June 2020; Revised 13 November 2020; Accepted 13 January 2021; Published 27 January 2021 Academic Editor: Chunshun Zhang Copyright © 2021 Qiao Shi-fan et al. +is is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. +is paper proposes a novel grey wolf optimization-extreme learning machine model, namely, the GWO-ELM model, to train and predict the ground subsidence by combining the extreme learning machine with the grey wolf optimization algorithm. Taking an excavation project of a foundation pit of Kunming in China as an example, after analyzing the settlement monitoring data of cross sections JC55 and JC56, the representative monitoring sites JC55-2 and JC56-1 were selected as the training monitoring samples of the GWO-ELM model. -

Editors-In-Chief: Ma, Hongbao, Ph.D
, '" Life Science Journal Acta Zhengzhou University Overseas Edition Life Science Journal, the Acta Zhengzhou University Overseas Edition, is an international journal with the purpose to enhance our natural and scientific knowledge dissemination in the world under the free publication princi- ple. The journal is calling for papers from all who are associated with Zhengzhou University - home and abroad. Any valuable papers or reports that are related to life science are welcome. Other academic articles that are less rele- vant but are of high quality will also be considered and published. Papers submitted could be reviews, objective de- scriptions, research reports, opinions/debates, news, letters, and other types of writings. All publications of Life Science ]aurnal are under vigorous peer-review. Let's work together to disseminate our research results and our opmlons. Editorial Board: Editor- in-Chief: Shen,Changyu, Ph. D. , Zhengzhou University, China Associate Editors-in-Chief: Ma, Hongbao, Ph.D. , Michigan State University, USA Xin, Shijun, Prof. , Zhengzhou University, China Li, Qingshan, Ph.D., Zhengzhou University, China Cherng, Shen, Ph. D. , M. D. , Chengshiu University, China Editors: (in alphabetical order) An, Xiuli, Ph.D., New York Blood Center, USA Chen, George, Ph. D. , Michigan State University, USA Dong, Ziming, M. D. , Zhengzhou University, China Duan, Guangcai, Ph. D. , M. D. , Zhengzhou University, China Edmondson, Jingiing Z. , Ph. D. , Zhejiang University, China Li, Xinhua, M. D. , Zhengzhou University, China Li, Yuhua, Ph. D. , Emory University, USA Lindley, Mark, Ph. D. , Columbia University, USA Liu, Hongmin, Ph. D. , Zhengzhou University, China Liu, Zhanju, Ph. D. , M. D. , Zhengzhou University, China Lu, Longdou, Ph. -
Type of the Paper (Article
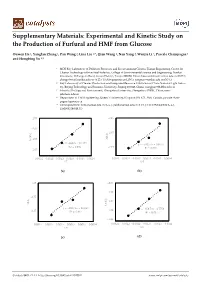
Supplementary Materials: Experimental and Kinetic Study on the Production of Furfural and HMF from Glucose Ouwen He 1, Yangfan Zhang 1, Pan Wang 2, Lina Liu 1,*, Qian Wang 1, Nan Yang 1, Wenjie Li 3, Pascale Champagne 4 and Hongbing Yu 1,* 1 MOE Key Laboratory of Pollution Processes and Environmental Criteria, Tianjin Engineering Centre for Cleaner Technology of Iron-Steel Industry, College of Environmental Science and Engineering, Nankai University, 38 Tongyan Road, Jinnan District, Tianjin 300350, China; [email protected] (O.H.); [email protected] (Y.Z.); [email protected] (Q.W.); [email protected] (N.Y.) 2 Key Laboratory of Cleaner Production and Integrated Resource Utilization of China National Light Indus- try, Beijing Technology and Business University, Beijing 100048, China; [email protected] 3 School of Ecology and Environment, Zhengzhou University, Zhengzhou 450001, China; wen- [email protected] 4 Department of Civil Engineering, Queen’s University, Kingston ON K7L 3N6, Canada; pascale.cham- [email protected] * Correspondence: [email protected] (L.L.); [email protected] (H.Y.); Tel: 18526446994 (L.L.), 13920683244 (H.Y.) -2.55 -3.15 -2.05 -2.65 -1.55 Ln(k1) Ln(kG) y = -8052x + 16.277 y = -5405.7x + 9.6074 R2 = 0.991 -2.15 R² = 0.935 -1.05 0.0021 0.0022 0.0022 0.0023 0.0023 0.0024 0.0021 0.0022 0.0022 0.0023 0.0023 0.0024 1/T 1/T (a) (b) -3.25 -4.03 -3.98 -2.75 -3.93 Ln(k3) Ln(k2) y = -6007.1x + 10.824 y = -958.73x - 1.7758 -2.25 -3.88 R² = 0.932 R² = 0.997 -3.83 0.0021 0.0022 0.0022 0.0023 0.0023 0.0024 0.0021 0.0022 0.0022 0.0023 0.0023 0.0024 1/T 1/T (c) (d) Catalysts 2021, 11, 11. -

International Academic Partnerships
International Academic Partnerships General Collaboration Collaborative Degree Programs Agreements International Accelerated Degree Programs (IADP): Earn two degrees; one bachelor’s degree from Institutional-level agreements to the partner university and one master’s degree from ASU. seek a variety of collaboration • Graduate Dual-Degree Programs: Earn two graduate degrees, one from each institution. opportunities across both universities. (university-wide) • Undergraduate Dual-Degree Programs: Earn two bachelor’s degrees, one from each institution Student Exchange Direct Enrollment Global Visiting Additional Partnerships Agreements Partnership Programs PLuS Alliance Partnerships offer Reciprocal exchange of ASU ASU students study abroad Undergraduate students research, degree and continuing students to the host institution, for one semester or one year, attend ASU for one education programs. and students from the host and pay a program fee that semester or for one year Other agreements, such as MOU institution to ASU. includes host institution tuition. (non-exchange). and Collaborative Agreements. Agreements by country General CollaborativeCollaborationStudent Degree Agrmts.Direct Exchange Progs. EnrollmentGlobal Agrmts. VisitingAdditional P’ship. Progs. General CollaborativeCollaborationStudent Degree Agrmts.Direct Exchange Progs. EnrollmentGlobal Agrmts. VisitingAdditional P’ship. Progs. Australia Guanxi University Macquarie University Hainan University Monash University Heibei University Queensland University of Technology Hong -

Abstract Submission/Modification Form
Tislelizumab (BGB-A317) for Relapsed/Refractory Classical Hodgkin Lymphoma: Preliminary Efficacy and Safety Results from a Phase 2 Study Yuqin Song, MD, PhD,1 Quanli Gao, MD,2 Huilai Zhang, PhD,3 Lei Fan, MD, PhD,4 Jianfeng Zhou, PhD,5 Dehui Zou, MD,6 Wei Li, MD,7 Haiyan Yang, PhD,8 Ting Liu, MD, PhD,9 Quanshun Wang, MD, PhD,10 Fangfang Lv, MD,11 Yu Yang, MD,12 Haiyi Guo, MD,13 Liudi Yang, MD,13 Rebecca Elstrom, 13 13 13 13 1 MD, Jane Huang, MD, William Novotny, MD, Vivian Wei, PhD, and Jun Zhu, MD, PhD 1Department of Lymphoma, Peking University Cancer Hospital & Institute (Beijing Cancer Hospital), Beijing, China 2Department of Immunotherapy, Affiliated Cancer Hospital of Zhengzhou University, Henan Cancer Hospital, Zhengzhou, China 3Tianjin Medical University Cancer Institute and Hospital, National Clinical Research Center for Cancer, Key Laboratory of Cancer Prevention and Therapy, Tianjin, Tianjin’s Clinical Research Center for Cancer, Tianjin, China 4Department of Hematology, the First Affiliated Hospital of Nanjing Medical University, Jiangsu Province Hospital, Collaborative Innovation Center for Cancer Personalized Medicine, Nanjing, China 5Department of Hematology, Tongji Hospital, Tongji Medical College, Wuhan, China 6State Key Laboratory of Experimental Hematology, Institute of Hematology & Blood Diseases Hospital, Chinese Academy of Medical Sciences and Peking Union Medical College, Tianjin, China 7Department of Hematology, Cancer Center, The First Hospital of Jilin University, Changchun, China 8Department of Oncology, Zhejiang -

Universities and the Chinese Defense Technology Workforce
December 2020 Universities and the Chinese Defense Technology Workforce CSET Issue Brief AUTHORS Ryan Fedasiuk Emily Weinstein Table of Contents Executive Summary ............................................................................................... 3 Introduction ............................................................................................................ 5 Methodology and Scope ..................................................................................... 6 Part I: China’s Defense Companies Recruit from Civilian Universities ............... 9 Part II: Some U.S. Tech Companies Indirectly Support China’s Defense Industry ................................................................................................................ 13 Conclusion .......................................................................................................... 17 Acknowledgments .............................................................................................. 18 Appendix I: Chinese Universities Included in This Report ............................... 19 Appendix II: Breakdown by Employer ............................................................. 20 Endnotes .............................................................................................................. 28 Center for Security and Emerging Technology | 2 Executive Summary Since the mid-2010s, U.S. lawmakers have voiced a broad range of concerns about academic collaboration with the People’s Republic of China (PRC), but the most prominent -

Honor Rolls of Best Hospitals in China Released
News Page 1 of 23 Honor rolls of best hospitals in China released Luna Young, Molly J. Wang Editorial Office,Journal of Hospital Management and Health Policy, Nanjing 210000, China Correspondence to: Molly J. Wang, Senior Editor. Editorial Office, Journal of Hospital Management and Health Policy, Nanjing 210000, China. Email: [email protected]. Received: 24 November 2017; Accepted: 03 December 2017; Published: 08 December 2017. doi: 10.21037/jhmhp.2017.12.01 View this article at: http://dx.doi.org/10.21037/jhmhp.2017.12.01 On November 11, 2017, the Honor Roll of the Best Best Comprehensive Hospitals in 2016. Comprehensive Hospitals in 2016 has been released by the In the meantime, the Honor Roll of Best Hospitals of Hospital Management Institute, Fudan University, China. Specialties in 2016 has been unveiled as well. Notably, The Honor Roll recognizes 100 hospitals for their altogether top 10 hospitals are selected in each of these exceptional comprehensive abilities where reputation of 37 specialties. The specialties range from Pathology, specialties and scientific research ability are among the Radiology, Pulmonology, Stomatology, Urology and factors predominantly weighed. Psychiatry and others with a rather comprehensive As usual, Peking Union Medical College Hospital, coverage on our daily needs. With no doubt, Peking Union West China Hospital of Sichuan University and General Medical College Hospital, West China Hospital of Sichuan Hospital of the People’s Liberation Army easily made University and General Hospital of the People’s Liberation the list, respectively ranking the top 3. Moreover, there Army, the top 3 comprehensive hospitals, are leading the are several hospitals rising greatly in the list, such as most entries of the specialties among the list. -

MATHI: Call for Papers Special Issue “Biomedical Applications of Micro- and Nanoparticles”
MATHI: Call for Papers Special Issue “Biomedical Applications of Micro- and Nanoparticles” Guest Editors: Xiang Zhang Zhengzhou University, China E-mail: [email protected] Jianhua Zhou Sun Yat-sen University, China E-mail: [email protected] Liguo Zhang Zhengzhou University, China E-mail: [email protected] Aims and Scope This Special Issue on biomedical applications of micro- and nanoparticles is motivated by the current challenges that are fueling a growing interest on the use of micro- and nanoparticles in biomedical fields. Recently, a lot of progress has been made not only related to metal nanoparticles, magnetic nanoparticles, carbon nanomaterials, and mesoporous silica nanoparticles, but also in emerging fields such as virus-like particles, quantum dots, polymeric particles, cerium oxide nanoparticles, self-assembled nanoparticles, etc. The aim of this Special Issue is to present the latest developments in micro- and nanoparticles related to biomedical applications for solving the increase in and complexity of real-world health issues. Papers contributing in developments in fundamentals, approaches, methodologies, and applications such as drug delivery, biomedical imaging, biosensors, disease therapy, bioprinting, and tissue engineering are encouraged to submit. Finally, as micro- and nanoparticles biomedical applications are multidisciplinary, discussions in this area in different perspectives, cross- disciplinary and interdisciplinary, are welcome as well. Materials Highlights (MATHI) 1/3 MATHI: Call for Papers Special Issue “Biomedical Applications of Micro- and Nanoparticles” Main topics and quality control The major topics of interest include, but are not limited to: New methods of micro-nanoparticle fabrication New applications of micro- and nanoparticles Functional nanoparticles used in drug delivery Micro- and nanoparticles used in Biomedical imaging Bioprinting Biosensors Photothermal therapy of diseases Tissue engineering This special issue is dedicated to a set of best papers in the field of micro- and nanoparticles. -

Yang Liu's Resume
Yang Liu’s CV 1 Personal Information Yang Liu, PhD Postdoctoral Associate, Li-Lab The Jackson Laboratory for Genomic Medicine 10 Discovery Drive, Farmington, CT 06032 Email: [email protected], [email protected] Phone: 860.278.9955, +86-13213136875 2 Work Experience 2019/08- Present Postdoctoral Associate in Li-Lab, The Jackson Laboratory for Genomic Medicine. Adv: Dr. Sheng Li, see also web page 2010/07- 2019/08 Staff Lecturer at school of information engineering in Zhengzhou University1, P.R. China, , see also web page 3 Education 2007/09- 2009/06 Visiting Ph.D. at school of engineering in Blekinge Institute of Technology(BTH)2, Sweden 2004/06, 2010/06 Bachelor and Ph.D. degrees at Dept. of computer science and technology, Xi’an Jiaotong University(XJTU)3, P.R. China 4 Awards & Fundings 2020 First place in Speak4Science of UCONN Health and JAX Postdoctoral Meet- ing 2018 Key project of improvement of students’ innovative ability and top talent training in ZZU(in Zhengzhou University), Supervisor teacher 2017 Supervisor of project of innovative and entrepreneurial training program for college students in ZZU 2016 National Natural Science Foundation of China, 61572444, Research on DNA Computing Methods for Logical Tree Model Tests 1ZZU is the abbreviation for Zhengzhou University. ZZU is in the list of Chinese construction plan of ”double-first universities”, which means world-first university and first-class discipline. See also http://www.zzu.edu.cn. 2BTH is the abbreviation for Blekinge Tekniska Hogskola.¨ See also http://www.bth.se. 3XJTU is the abbreviation for Xi’an Jiaotong University. -

The Relationship Between the Facial Expression of People in University Campus and Host- City Variables
Supplementary: The relationship between the facial expression of people in university campus and Host- city variables Hongxu Wei 1, Richard J. Hauer 2 and Xuquan Zhai 3,* 1 Northeast Institute of Geography and Agroecology, Chinese Academy of Sciences, Changchun 130102, China; [email protected] 2 College of Natural Resources, University of Wisconsin–Stevens Point, 800 Reserve St., Stevens Point, WI 54481, United States; [email protected] 3 China Center for Public Sector Economy Research, Jilin University, Room 3007, Kuang, Yaming Building, 2699 Qianjin Road, Chaoyang District, Changchun 130012, China, Changchun 130012, China; * Correspondence: [email protected]; Tel.: +86-431-8516-8829 Figure S1. The panel of FireFACETM-V1.0 to recognize photos with typically happy, sad, and neutral facial expressions. The model is Ryōko Hirosue from Japan. Photos are downloaded from following websites: Happy: https://images.app.goo.gl/Kh5FgWEMMSPUa3sD9 Sad: https://images.app.goo.gl/GazwjvTh8a6qiyBa9 Neutral: https://images.app.goo.gl/Hn2gtLonVpoLd5o27 Figure S2. The copyright of the FireFACETM-V1.0 software that is authorized in mainland China. Table S1. The list of key universities in the 211-Project of mainland China with Province and City names. Rank Province City University name 1 Anhui University 2 Anhui Hefei Hefei University of Technology 3 University of Science and Technology of China 4 Beijing Foreign Studies University 5 Beijing Forestry University 6 Beijing Institute of Technology 7 Beijing Jiaotong University 8 Beijing Normal University -

Initiative Disciplines Development List 01 Natural and Physical Sciences (100)
“Double First-Class” initiative disciplines development list (Sorted by discipline) Note: The list was published by the Ministry of Education of the People’s Republic of China on 21 September 2017. This list sorted by discipline has been prepared by the Education and Research Section, Australian Embassy, Beijing based on the Australian Standard Classification of Education (ASCED) 2001, Australian Bureau of Statistics. Initial translation credit to Science, Technology and Education Section, Embassy of Switzerland in China. 01 Natural and Physical Sciences (100) Astronomy (2) Nanjing University University of Science and Technology of China Atmosphere Science (3) Nanjing University Nanjing University of Information Science & Technology Lanzhou University Biology (16) Peking University Tsinghua University China Agricultural University Peking Union Medical College Inner Mongolia University Fudan University Shanghai Jiao Tong University Nanjing University Zhejiang University University of Science and Technology of China Xiamen University Huazhong Agricultural University Henan University Sun Yat-sen University Wuhan University Southwest University Chemistry (25) Peking University Tsinghua University Nankai University Tianjin University Dalian University of Technology Jilin University Northeast Normal University Fudan University Shanghai Jiao Tong University East China University of Science and Technology Nanjing University Zhejiang University Xiamen University University of Science and Technology of China Fuzhou University Shandong University