White Paper Barracuda Networks Details of a Real Databreach
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Best Practices: Use of Web Application Firewalls
OWASP Papers Program Best Practice: Use of Web Application Firewalls Best Practices: Use of Web Application Firewalls Version 1.0.4, March 2008, English translation 25. May 2008 Author: OWASP German Chapter with collaboration from: Maximilian Dermann Mirko Dziadzka Boris Hemkemeier Achim Hoffmann Alexander Meisel Matthias Rohr Thomas Schreiber OWASP Papers Program Best Practice: Use of Web Application Firewalls Abstract Web applications of all kinds, whether online shops or partner portals, have in recent years increasingly become the target of hacker attacks. The attackers are using methods which are specifically aimed at exploiting potential weak spots in the web application software itself – and this is why they are not detected, or are not detected with sufficient accuracy, by traditional IT security systems such as network firewalls or IDS/IPS systems. OWASP develops tools and best practices to support developers, project managers and security testers in the development and operation of secure web applications. Additional protection against attacks, in particular for already productive web applications, is offered by what is still a emerging category of IT security systems, known as Web Application Firewalls (hereinafter referred to simply as WAF), often also called Web Application Shields or Web Application Security Filters. One of the criteria for meeting the security standard of the credit card industry currently in force (PCI DSS - Payment Card Industry Data Security Standard v.1.1) for example, is either a regular source code review or the use of a WAF. The document is aimed primarily at technical decision-makers, especially those responsible for operations and security as well as application owners (specialist department, technical application managers) evaluating the use of a WAF. -

5 Things You Need to Know About a Web Application Firewall
5 Things You Need to Know about a Web Application Firewall A NEUSTAR SECURITY SOLUTIONS EXCLUSIVE www.security.neustar 5 Things You Need to Know about a Web Application Firewall Table of Contents 1. What is a WAF? 03 2. Why Are Attackers Interested in Your Applications? 04 3. Why Do You Need a WAF? 05 4. Key Features to Expect from a WAF 06 5. Not All WAFs Are Equal 08 About Neustar 09 01 5 Things You Need to Know about a Web Application Firewall Web Application Firewall (WAF) is a priority item for IT professionals who are struggling to protect their customer facing and mission- critical applications. From SQL injection attacks to cleverly executed distributed denial of service (DDoS) attacks, attackers are enjoying success in areas where a WAF would otherwise stop their progression. But before you go out and buy a WAF service, here are five things you need to know. 5 Things You Need to Know about a Web Application Firewall What is a WAF? At its core, a Web Application Firewall (WAF) is responsible for inspecting the Hypertext Transfer Protocol (HTTP) request and responding based on predefined rules;processing preset actions against questionable HTTP/HTTPS requests identified during the inspection phase or the HTTP/HTTPS connection validity check; logging the malicious HTTP/HTTPS requests identified during the inspection; andmanaging visits to websites. Generally speaking, WAFs detect and protect web applications from attacks that try to exploit vulnerabilities. WAFs serve as a way to enhance the security perimeter by providing an additional barrier between attackers and your application layer. -

Best Practices: Use of Web Application Firewalls
OWASP Papers Program Best Practice: Use of Web Application Firewalls Best Practices: Use of Web Application Firewalls Version 1.0.5, March 2008, English translation 25. May 2008 Author: OWASP German Chapter with collaboration from: Maximilian Dermann Mirko Dziadzka Boris Hemkemeier Achim Hoffmann Alexander Meisel Matthias Rohr Thomas Schreiber OWASP Papers Program Best Practice: Use of Web Application Firewalls Abstract Web applications of all kinds, whether online shops or partner portals, have in recent years increasingly become the target of hacker attacks. The attackers are using methods which are specifically aimed at exploiting potential weak spots in the web application software itself – and this is why they are not detected, or are not detected with sufficient accuracy, by traditional IT security systems such as network firewalls or IDS/IPS systems. OWASP develops tools and best practices to support developers, project managers and security testers in the development and operation of secure web applications. Additional protection against attacks, in particular for already productive web applications, is offered by what is still a emerging category of IT security systems, known as Web Application Firewalls (hereinafter referred to simply as WAF), often also called Web Application Shields or Web Application Security Filters. One of the criteria for meeting the security standard of the credit card industry currently in force (PCI DSS - Payment Card Industry Data Security Standard v.1.1) for example, is either a regular source code review or the use of a WAF. The document is aimed primarily at technical decision-makers, especially those responsible for operations and security as well as application owners (specialist department, technical application managers) evaluating the use of a WAF. -

Securing a Modern Web Application in AWS
Securing a Modern Web Application in AWS Explore threat modeling and learn how to create and support your web application security strategy with AWS Marketplace software seller solutions. AWS Marketplace Introduction As more organizations turn to distributed web applications to maintain high availability and reduce costs, many are choosing to store these applications in the AWS cloud for added elasticity, scalability, and ability to handle large workloads. Doing this securely, however, means addressing potential threats to multiple components, such as the front-end cloud application and corresponding databases. In this whitepaper, SANS analyst and instructor, Shaun McCullough, will provide an introduction to exploring the vulnerabilities associated with modern web applications, web application firewalls, and DevSec operations that oversee security to continually update code. This process, known as threat modeling, is vital to the ability to prioritize vulnerabilities and security operations to meet those challenges. Building on Shaun’s perspective, AWS Marketplace shares how this process can be applied to your AWS Cloud environment with an introduction to relevant AWS security services and AWS Marketplace software sellers, such as Fortinet, Barracuda, and Imperva. The featured Fortinet solutions for this use case can be accessed in AWS Marketplace Fortinet Managed Rules for AWS WAF AWS Quick Start for Fortinet FortiGate Fortinet FortiWeb Cloud WAF-as-a-Service A SANS Whitepaper How to Protect a Modern Web Application in AWS Written by Shaun McCullough Sponsored by: April 2019 AWS Marketplace Introduction As businesses move more assets to the cloud, having a security plan is essential, but nobody has the time or resources to do everything that is needed from the start. -

Evolution of Web Application Firewalls
EVOLUTION OF WAF EVOLUTION OF WEB APPLICATION FIRewaLLS: INCIDENT DAMAGES TOP USD 162 MILLION FROM SERVER PROTECTION TO DEFENSE-IN-DEPTH A massive 2013 hack infected Internet-based network attacks have become increasingly sophisticated over the last 20 years. Once-useful payment systems at Target stores Intrusion Detection System/Intrusion Protection System (IDS/IPS) solutions show their age as the diversity running on out-of-date versions and interactivity of today’s web applications open up vectors for invisible, destructive cyberattacks. Most of Windows. The attackers used corporate network breaches are the result of vulnerabilities in web applications, even at companies that use a vulnerable web service, which the traditional security tools. Security-conscious companies are meeting this challenge by supplanting IDS/ allowed uploading arbitrary exe- IPS and classic firewalls with the new technologies found in Web Application Firewall solutions. cutables, to obtain access to POS terminals. Over 19 days, hackers WAF 1.0 made away with 40 million credit The first generation of web application protection featured two main advances over IDS/IPS: utilization of and debit card numbers in addi- HTTP attributes (method, address, parameters) and conversion of data prior to analysis (urlencode, base64). tion to personal information for 70 These solutions used a signature-based approach and were oriented at protection from server attacks (RCE, million customers. The company’s Path Traversal, SQL Injection). direct expenses exceeded $162 million. WAF 2.0 MORE THAN GBP 100 The Web 2.0 technology stack, including AJAX, and explosive growth in the number of critical web appli- MILLION LOST DUE TO A cations drove development of WAF 2.0. -

Importance of Web Application Firewall Technology for Protecting Web-Based Resources
Importance of Web Application Firewall Technology For Protecting Web-based Resources Importance of Web Application Firewall Technology for Protecting Web-based Resources By Andrew J. Hacker, CISSP, ISSAP Senior Security Analyst, ICSA Labs January 10, 2008 ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg, PA 17050 Copyright © 2008 Cybertrust, Inc. All Rights Reserved. Page 1 of 7 Importance of Web Application Firewall Technology For Protecting Web-based Resources Importance of Web Application Firewall Technology for Protecting Web-based Resources By Andrew J. Hacker, CISSP, ISSAP Introduction Web-based applications and services have changed the landscape of information delivery and exchange in today’s corporate, government, and educational arenas. Ease of access, increased availability of information, and the richness of web services have universally increased productivity and operational efficiencies. These increases have led to heavier reliance on web-based services and greater integration of internal information systems and data repositories with web-facing applications. While motivations of attackers against a victim’s corporate and organizational assets remain the same (financial, IP, identity theft, services disruption, or denial of service, for example), web applications enable a whole new class of vulnerabilities and exploit techniques such as SQL injection, cross-site scripting (XSS), and cross-site request forgery, to name a few.1 The complexity of services, potential severity of breaches, and mounting sophistication of attacks requires additional functionality beyond the capability of traditional network-based security products. The emergence of dedicated web application firewall technology provides a comprehensive and focused solution to help increase the security of web-based services and protect valuable information assets. -

Health Information Security in the Age of Ehrs and the 3Rd Platform Learn More White Paper
Health Information Security in the age of EHRs and the 3rd Platform White Paper Barracuda • Health Information Security in the age of EHRs and the 3rd Platform Introduction The last time Health Information Technology (HIT) changed this quickly was when barcoding was introduced to HIT networks in the 1990s. While the federal government pushes adoption of Electronic Health Records (EHRs), patient engagements are migrating to smartphones, tablets, and social media. Healthcare providers are also using cloud computing to analyze “big data” collected about treatments and procedures. Together “big connectivity” and cloud computing along with social media are being hailed as the “3rd Platform;” the successors to mainframe and client-server computing architectures. The challenge is how to add EHRs and 3rd Platform services to HIT mainstay services like email, Web access, and other applications while maintaining privacy for HIPAA compliance in today’s high-risk environment. As evidence of today’s risk, the Department of Health and Human Services’ Office for Civil Rights reported that 2016 was a record-breaking year, with more data breaches reported since they started publishing healthcare data breach summaries in 2009.1 Since 2002, Barracuda Networks’ strategy has been to protect and simplify diversifying IT infrastructures by converging security, performance optimization, and data loss prevention (DLP) features in solutions that are easy to deploy and manage. This white paper deals with the security and DLP issues facing IT professionals in the healthcare industry and how Barracuda technology addresses these issues. EHRs: Security, Storage, and Compliance Three issues to consider when you deploy EHRs are: avoiding data breaches by blocking cyber- attacks on the EHR application, demonstrating “meaningful use” of EHRs for certification, and providing safe, economical backups for a fast-growing volume of EHR data. -

Intelligent Web Application Firewall (Iwaf) Point-And-Click Simplicity for Web Application Security
SOLUTION OVERVIEW Intelligent Web Application Firewall (iWAF) Point-and-Click Simplicity for Web Application Security CHALLENGES WEB APPLICATIONS ARE UNDER-SECURED BY TODAY’S WAFS • Increasing complex process for Web application firewalls (WAFs) are intended to protect businesses from web app writing security policies and rules attacks and proactively prevent threats. Yet, despite the potential security benefits, 90% • Lack of visibility into how of organizations find it complex to implement WAF solutions for three key reasons: policies impact traffic flows • Complex rules. Most WAFs today are very complicated, presenting a wall-of-knobs to • Low performance and massive administrators in order to configure security policies. Tuning rules is even more variability result in scaling and challenging, not to mention customizing for each application. capacity planning challenges • No visibility or intelligence. Most WAFs today provide little visibility and lack attack behavior modeling and application learning. Once rule sets are defined, it is difficult to update, monitor and impossible to react in real time to changes or new security threats. SOLUTION — AVI IWAF • Slow to scale. Traditional WAFs are inelastic and unable to provide the scalability • Real-time visibility and insights into required for increasing volumes of encrypted traffic and variable loads. Hardware application performance, end-user appliance-based WAFs need significant overprovisioning. experience and security patterns • Elastic horizontal autoscaling to handle security attacks and easy rule OPERATIONAL INTELLIGENCE THROUGH MACHINE LEARNING generation to customize response Avi features an Intelligent Web Application Firewall (iWAF) with a distributed application security fabric to enforce security through closed-loop analytics and application learning • GDPR, HIPAA, and PCI compliance mode. -

Web Application Firewall Fully Managed Critical Web Application Protection
SOLUTION BRIEF Web Application Firewall Fully Managed Critical Web Application Protection Hassle-Free Enterprise-Level WAF ALERT LOGIC WEB Web applications are an important part of your business and a vital part of how customers APPLICATION FIREWALL interact with you. Unfortunately, web applications also give attackers another gateway INCLUDES THE FOLLOWING into your critical assets and data. Businesses need to distinguish the good traffic from the bad in real-time, accurately. • 24/7 Support from our SOC • Managed Deployment Alert Logic delivers a highly versatile, enterprise-level, cloud-ready WAF that comes with • Ongoing Management & Tuning a team of experts to eliminate the complexity for you. • WAF Policy Building and Management With Alert Logic’s Fully Managed WAF You Receive • Zero-Day Emerging Threat Detection COMPLETE SETUP AND MANAGEMENT • Rule and Behavior-Based Detection From installation, deployment through to configuration, our experts ensure your Web Application Firewall is ready to block threats against your critical web applications. Our • Usage-based Application analysts fine-tune your WAF by monitoring your web application traffic, whitelisting valid Learning requests and data, and building a policy that blocks malicious web traffic and other • Auto-Scaling and High Availability undesired activity. Setup • Web-Application Aware Policies As new threats emerge and your apps and portfolio change, our analysts will update your policy as needed or required. Our services eliminate the steep learning curve and associated staffing costs that come with managing a WAF. TRADITIONAL AND BEHAVIOR BASED THREAT DETECTION Alert Logic’s WAF provides comprehensive features to protect your web applications. Whitelisting, blacklisting, and signature-based blocking are augmented by a learning engine that builds a model of your application to recognize activity that deviates from a known-good baseline of traffic. -

Fortiguard Datasheet
DATASHEET FortiGuard® Global Security Research and Protection FortiGuard Labs More than 125 security threat researchers, engineers, and forensic specialists comprise FortiGuard Labs operate the FortiGuard Labs team. Operating in Canada, China, France, Japan, Malaysia in Canada, China, France, and the United States, this team provides around the clock and around the globe Japan, Malaysia and coverage to assure some of the fastest response times in the industry to new viruses, the United States vulnerabilities, attacks, and malicious threats. The FortiGuard team collaborates with the world’s leading threat monitoring organizations to advise and learn of new and emerging In a typical week, FortiGuard threats. Additionally, the team contributes to the overall security industry by identifying Labs add or update and responsibly reporting vulnerabilities directly to vendors of hardware, operating approximately: systems, and applications. • 100,000 antivirus signatures FortiGuard Security Subscription Services • 34 intrusion prevention (IPS) signatures The Fortinet FortiGuard Security Subscription Services provide comprehensive antivirus/ • 500,000 URLs ratings for antispyware, intrusion prevention, web filtering, antispam, application control, database Web filtering with more than security, vulnerability management, and web application firewall capabilities to enable 65 languages supported unified protection against multiple threats. These services were designed from the • 30,000,000 antispam ground up to optimize performance and maximize protection afforded by Fortinet signatures security platforms. Since Fortinet developed and delivers these services, there is an inherent synergy and integration that further increases their collective effectiveness. FortiGuard services are continuously updated by FortiGuard Labs. This team enables In addition, FortiGuard Labs Fortinet to deliver a combination of multi-layered security knowledge and provide true deliver comprehensive protection with more than zero-day protection from new and emerging threats. -

Phishing-Proof Your Staff and Software Systems
Phishing-Proof Your Staff and Software Systems Presenter: Joe Basirico SVP of Engineering at Security Innovation Agenda • Housekeeping • Presenters • About Conexxus • Presentation • Q & A Housekeeping This webinar is being recorded and will be made available in approximately 15 days. • YouTube (youtube.com/conexxusonline) • Website Link (conexxus.org) Slide Deck • Survey Link – Presentation provided at end Participants • Ask questions via webinar interface • Please, no vendor specific questions Email: [email protected] Presenters Conexxus Host Moderator Allie Russell Kara Gunderson Conexxus Chair, Data Security Committee [email protected] POS Manager, CITGO Petroleum [email protected] Speakers Joe Basirico Security Innovation [email protected] About Conexxus • We are an independent, non-profit, member driven technology organization • We set standards… – Data exchange – Security – Mobile commerce • We provide vision – Identify emerging tech/trends • We advocate for our industry – Technology is policy 2019 Conexxus Webinar Schedule* Month/Date Webinar Title Speaker Company August 8, 2019 Application Security 101 Denis Sheridan Synopsys August 29, 2019 Phishing-Proof Your Staff and IT Systems Joe Basirico Security Innovation Ashwin Swamy Omega ATC September 2019 Updated Data Science Presentation Thomas Duncan Omega ATC Easy PCI—How to Make PCI & Attestation October 2019 Ajith Edakandi Hughes Easier Brian Russell Verifone November 2019 Outdoor EMV Linda Toth Conexxus December 2019 TBD Sam Pfanstiel ControlScan NACS Show -
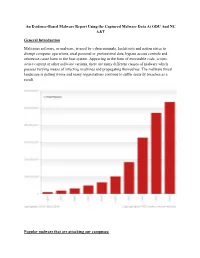
General Malware Report
An Evidence-Based Malware Report Using the Captured Malware Data At ODU And NC A&T General Introduction Malicious software, or malware, is used by cybercriminals, hacktivists and nation states to disrupt computer operations, steal personal or professional data, bypass access controls and otherwise cause harm to the host system. Appearing in the form of executable code, scripts, active content or other software variants, there are many different classes of malware which possess varying means of infecting machines and propagating themselves. The malware threat landscape is getting worse and many organizations continue to suffer security breaches as a result. Popular malware that are attacking our campuses: Our anti-malware software captured a variety of malware that are attacking our campuses in the past year. Below is a list of the popular malware: [1] Backdoor.APT.DarkComet [2] Data.Encoding.xor [3] Eicar-Test-Signature [4] Exploit.Generic [5] Exploit.Java [6] FE_CVE_2013_2460_Malware_Jar_2 [7] FE_Data_Obfuscation [8] FE_Evasion_VMDetect [9] FE_Generic_TaskSchedular [10] FE_Heuristic_Malware_Reflection_Jar [11] FE_Java_Security_Suspicious [12] FE_PUP_Softpulse [13] Infostealer.Banker.Zbot [14] Local.Infection [15] Malicious.URL [16] Malware Name [17] Malware.archive [18] Malware.Binary [19] Malware.Binary.Dll [20] Malware.Binary.Jar [21] Malware.ZerodayCallback [22] Trojan.Adaebook [23] Trojan.Asprox [24] Trojan.Downloader [25] Trojan.Downware [26] Trojan.Gen [27] Trojan.Generic [28] Trojan.GenericKD [29] Trojan.Java [30] Trojan.Medfos