Capivara: a Decentralized Package Version Control Using Blockchain
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Linux on the Road
Linux on the Road Linux with Laptops, Notebooks, PDAs, Mobile Phones and Other Portable Devices Werner Heuser <wehe[AT]tuxmobil.org> Linux Mobile Edition Edition Version 3.22 TuxMobil Berlin Copyright © 2000-2011 Werner Heuser 2011-12-12 Revision History Revision 3.22 2011-12-12 Revised by: wh The address of the opensuse-mobile mailing list has been added, a section power management for graphics cards has been added, a short description of Intel's LinuxPowerTop project has been added, all references to Suspend2 have been changed to TuxOnIce, links to OpenSync and Funambol syncronization packages have been added, some notes about SSDs have been added, many URLs have been checked and some minor improvements have been made. Revision 3.21 2005-11-14 Revised by: wh Some more typos have been fixed. Revision 3.20 2005-11-14 Revised by: wh Some typos have been fixed. Revision 3.19 2005-11-14 Revised by: wh A link to keytouch has been added, minor changes have been made. Revision 3.18 2005-10-10 Revised by: wh Some URLs have been updated, spelling has been corrected, minor changes have been made. Revision 3.17.1 2005-09-28 Revised by: sh A technical and a language review have been performed by Sebastian Henschel. Numerous bugs have been fixed and many URLs have been updated. Revision 3.17 2005-08-28 Revised by: wh Some more tools added to external monitor/projector section, link to Zaurus Development with Damn Small Linux added to cross-compile section, some additions about acoustic management for hard disks added, references to X.org added to X11 sections, link to laptop-mode-tools added, some URLs updated, spelling cleaned, minor changes. -

Experience with a Livecd in an Education Process
EXPERIENCE WITH A LIVECD IN AN EDUCATION PROCESS Experience with a LiveCD in an education process Jan R˚uˇziˇcka, FrantiˇsekKl´ımek Institute of Geoinformatics Faculty of Mining and Geology, VSB-TUO E-mail: [email protected] Key words: LiveCD, GIS´akLiveCD, Distance Learning, E-learning Abstract The paper describes how can be LiveCD (Bootable CD) used for geoinformatics distance learn- ing. We have prepared one LiveCD with basic software for learning geoinformatics and we have some feedback from users and teachers. The paper should evaluate this feedback. LiveCD is a CD-ROM, that can be used as a bootable device. After booting from the CD, the user can access all resources compiled to the CD. There are operating system (usually based on GNU/Linux) and (user, desktop) software installed and configured to be used directly after boot. Our CD named GIS´akLiveCD contains basic GIS software such as UMN MapServer, GRASS, Quantum GIS, Thuban, JUMP, GPS Drive, Blender and we work on other soft- ware packages such as MapLab for UMN MapServer, PostGIS, GeoNetwork Open Source, CatMDEdit, gvSIG, uDIG. GIS´akLiveCD contains set of spatial data from the Czech Re- public. Main part of the CD are tutorials for GIS software. CD is open for other e-learning materials. Now we have about 20 students using our LiveCD and few other users that are not curently our students. The paper should show Pros & Cons of the LiveCD usage for a distance learning. LiveCD Live CD is bootable CD-ROM with operating system and installed and configured programs. It is ready to use as full installed system directly after boot from CD-ROM drive. -

The Hot Seat Dear Linux Magazine Reader
EDITORIAL Welcome THE HOT SEAT Dear Linux Magazine Reader, What’s the top distro on the famous Distrowatch page hit rank- They are staying pretty close to the script that everyone ing list? Not Ubuntu, OpenSUSE, or Fedora. According to Dis- guessed they were in since the beginning. To recap those early trowatch, the hottest Linux is none other than Linux Mint – an assessments: When Ubuntu showed up as a value-added desk- Ubuntu-based, community-driven desktop system that is top operating system back in 2004 – quickly putting a fork in known for easy of use and efficient out-of-the-box multimedia Xandros and Lindows/ Linspire because it was free rather sell- functionality. Mint has been around since 2006, and many ing for the $30-$40 going rate of the fledgling commercial desk- Linux users are familiar with it. We’ve put Mint discs on several top distros – industry experts guessed the real goal was to issues of this magazine (the latest being the issue that you are build a large market share and establish brand loyalty, then holding now). But Mint has found new appreciation recently. move into the server and corporate IT space, where they could Some are calling it the new Ubuntu, which seems a little bit of make some real money with tech support and other surround- an overstatement, since Mint is based on Ubuntu (kind of like ing services. calling CentOS “the new Red Hat”). Nevertheless, Mint has The first part of their plan went really well – it is hard to imag- been on something of a roll recently. -

Lightweight Distros on Test
GROUP TEST LIGHTWEIGHT DISTROS LIGHTWEIGHT DISTROS GROUP TEST Mayank Sharma is on the lookout for distros tailor made to infuse life into his ageing computers. On Test Lightweight distros here has always been a some text editing, and watch some Linux Lite demand for lightweight videos. These users don’t need URL www.linuxliteos.com Talternatives both for the latest multi-core machines VERSION 2.0 individual apps and for complete loaded with several gigabytes of DESKTOP Xfce distributions. But the recent advent RAM or even a dedicated graphics Does the second version of the distro of feature-rich resource-hungry card. However, chances are their does enough to justify its title? software has reinvigorated efforts hardware isn’t supported by the to put those old, otherwise obsolete latest kernel, which keeps dropping WattOS machines to good use. support for older hardware that is URL www.planetwatt.com For a long time the primary no longer in vogue, such as dial-up VERSION R8 migrators to Linux were people modems. Back in 2012, support DESKTOP LXDE, Mate, Openbox who had fallen prey to the easily for the i386 chip was dropped from Has switching the base distro from exploitable nature of proprietary the kernel and some distros, like Ubuntu to Debian made any difference? operating systems. Of late though CentOS, have gone one step ahead we’re getting a whole new set of and dropped support for the 32-bit SparkyLinux users who come along with their architecture entirely. healthy and functional computers URL www.sparkylinux.org that just can’t power the newer VERSION 3.5 New life DESKTOP LXDE, Mate, Xfce and others release of Windows. -

Patagonia Clonesys – a Tool to Install Multi-Boot Environments
Patagonia CloneSys – A Tool to Install Multi-Boot Environments Christian Kurmann, Felix Rauch, Thomas M. Stricker Laboratory for Computersystems ETH Zurich, Switzerland Revised 24 November 1999, Christian Kurmann 1 Introduction The Patagonia CloneSys is designed to provide easy system installations on multi- boot and multi-purpose Clusters of PC’s. Do keep it easy and circumvent the devel- opment of a proprietary system it is based on standard UNIX tools and can easily be ported to other flavours of UNIXes. The scripts and ideas are subject to change and are provided as they are without any support. 2 Cloning: Basic Ideas Everybody knows the drudgery involved in manually setting up and rolling out new PCs, updating existing PCs, and recovering failed PCs. CloneSys makes a big dent in the time required to conduct these jobs. It first creates an exact image of a PC’s hard drive, effectively taking a ”snapshot” of all the files — hidden, visible, and active — that make up the operating system, applications, and configuration settings. The image can then be copied to any number of PCs, thereby creating completely identical installations. Moreover, it can be copied to many PCs simultaneously. This process it completely operating system independent which makes the system very easy and fast. As the raw disk data is copied, no file system initialization is needed, even the partitioning is implicitly done with a total clone. To support multi-boot environments the installation of single partitions is supported as well. To keep the system even easier as other commercially available tools we based it on freely available UNIX tools and Linux. -

Github: a Case Study of Linux/BSD Perceptions from Microsoft's
1 FLOSS != GitHub: A Case Study of Linux/BSD Perceptions from Microsoft’s Acquisition of GitHub Raula Gaikovina Kula∗, Hideki Hata∗, Kenichi Matsumoto∗ ∗Nara Institute of Science and Technology, Japan {raula-k, hata, matumoto}@is.naist.jp Abstract—In 2018, the software industry giants Microsoft made has had its share of disagreements with Microsoft [6], [7], a move into the Open Source world by completing the acquisition [8], [9], the only reported negative opinion of free software of mega Open Source platform, GitHub. This acquisition was not community has different attitudes towards GitHub is the idea without controversy, as it is well-known that the free software communities includes not only the ability to use software freely, of ‘forking’ so far, as it it is considered as a danger to FLOSS but also the libre nature in Open Source Software. In this study, development [10]. our aim is to explore these perceptions in FLOSS developers. We In this paper, we report on how external events such as conducted a survey that covered traditional FLOSS source Linux, acquisition of the open source platform by a closed source and BSD communities and received 246 developer responses. organization triggers a FLOSS developers such the Linux/ The results of the survey confirm that the free community did trigger some communities to move away from GitHub and raised BSD Free Software communities. discussions into free and open software on the GitHub platform. The study reminds us that although GitHub is influential and II. TARGET SUBJECTS AND SURVEY DESIGN trendy, it does not representative all FLOSS communities. -

Linux at 25 PETERHISTORY H
Linux at 25 PETERHISTORY H. SALUS Peter H. Salus is the author of A n June 1991, at the USENIX conference in Nashville, BSD NET-2 was Quarter Century of UNIX (1994), announced. Two months later, on August 25, Linus Torvalds announced Casting the Net (1995), and The his new operating system on comp.os.minix. Today, Android, Google’s Daemon, the Gnu and the Penguin I (2008). [email protected] version of Linux, is used on over two billion smartphones and other appli- ances. In this article, I provide some history about the early years of Linux. Linus was born into the Swedish minority of Finland (about 5% of the five million Finns). He was a “math guy” throughout his schooling. Early on, he “inherited” a Commodore VIC- 20 (released in June 1980) from his grandfather; in 1987 he spent his savings on a Sinclair QL (released in January 1984, the “Quantum Leap,” with a Motorola 68008 running at 7.5 MHz and 128 kB of RAM, was intended for small businesses and the serious hobbyist). It ran Q-DOS, and it was what got Linus involved: One of the things I hated about the QL was that it had a read-only operating system. You couldn’t change things ... I bought a new assembler ... and an editor.... Both ... worked fine, but they were on the microdrives and couldn’t be put on the EEPROM. So I wrote my own editor and assembler and used them for all my programming. Both were written in assembly language, which is incredibly stupid by today’s standards. -

Vectorlinux Documentation Release 7.1
VectorLinux Documentation Release 7.1 VectorLinux development team October 03, 2016 Contents 1 Introduction 1 2 Documentation Manuals 7 3 Packaging 109 4 Search documentation 115 5 Links 117 i ii CHAPTER 1 Introduction Speed, performance, stability – these are attributes that set VectorLinux apart in the crowded field of Linux distribu- tions. There are five editions to choose from. At the links below you will find information about the VL Edition best suited to your needs: 1.1 VectorLinux Deluxe Edition 1.1.1 What is the Deluxe Edition? Vector Linux DELUXE now comes in two Editions: Deluxe SOHO and Deluxe Standard. Both are available from our CD-Store. As at March 1st, 2009 Deluxe Standard is at version 6.0 while Deluxe SOHO is still at Version 5.9, although we expect a version 6.0 of Deluxe SOHO later in 2009. The Deluxe Editions are intended for professionals, extending the SOHO and Standard editions with up to 1000 MB of additional software. The extra applications can be installed individually to build the system exactly as you need it. The two CD package set of Deluxe Standard features a custom XFCE desktop with popular applications like Amarok, Blender, and the Gimp. Additional included applications are KDE 4.2, OpenOffice 3 and E17 amongst many others, particularly multimedia applications. Fourteen days of professional installation and configuration support included. There is automatic support for printers, scanners, USB hardware and CDRW / DVD drives. There are several new multimedia programs and libraries, the latest network applications and development programs along with their needed libraries. -

Linux Laptop-HOWTO
Linux Laptop−HOWTO Linux Laptop−HOWTO Table of Contents Linux Laptop−HOWTO.....................................................................................................................................1 Werner Heuser <[email protected]>...................................................................................................1 1. Preface..................................................................................................................................................1 2. Copyright, Disclaimer and Trademarks...............................................................................................1 3. Which Laptop to Buy?.........................................................................................................................1 4. Laptop Distribution..............................................................................................................................1 5. Installation...........................................................................................................................................2 6. Hardware In Detail...............................................................................................................................2 7. Palmtops, Personal Digital Assistants − PDAs, Handheld PCs − HPCs.............................................2 8. Cellular Phones, Pagers, Calculators, Digital Cameras, Wearable Computing...................................2 9. Accessories..........................................................................................................................................3 -
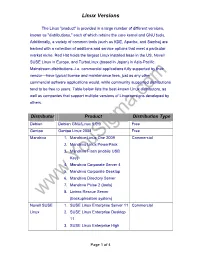
Linux Versions
Linux Versions The Linux "product" is provided in a large number of different versions, known as "distributions," each of which retains the core kernel and GNU tools. Additionally, a variety of common tools (such as KDE, Apache, and Samba) are backed with a collection of additions and service options that meet a particular market niche. Red Hat holds the largest Linux installed base in the US, Novell SUSE Linux in Europe, and TurboLinux (based in Japan) in Asia-Pacific. Mainstream distributions--i.e. commercial applications fully supported by their vendor—have typical license and maintenance fees, just as any other commercial software applications would, while community supported distributions tend to be free to users. Table below lists the best-known Linux distributors, as well as companies that support multiple versions of Linux versions developed by others. Distributor Product Distribution Type Debian Debian GNU/Linux 5.0.0 Free Gentoo Gentoo Linux 2008 Free Mandriva 1. Mandrive Linux One 2009 Commercial 2. Mandriva Linux PowerPack 3. Mandriva Flash (mobile USB Key) 4. Mandriva Corporate Server 4 5. Mandriva Corporate Desktop 6. Mandriva Directory Server 7. Mandriva Pulse 2 (tools) 8. Linbox Rescue Server (backup/restore system) Novell SUSE 1. SUSE Linux Enterprise Server 11 Commercial Linux 2. SUSE Linux Enterprise Desktop 11 3. SUSE Linux Enterprise High Page 1 of 4 Linux Versions Availability Extension 4. SUSE Linux Enterprise Mono Extension 5. SUSE Linux Enterprise Server for System z 6. SUSE Linux Enterprise Real Time Extension 7. SUSE Linux Enterprise Server Priority Support for 8. SAP Applications 9. SUSE Linux Enterprise Point of Service 10. -

Introduction to Fmxlinux Delphi's Firemonkey For
Introduction to FmxLinux Delphi’s FireMonkey for Linux Solution Jim McKeeth Embarcadero Technologies [email protected] Chief Developer Advocate & Engineer For quality purposes, all lines except the presenter are muted IT’S OK TO ASK QUESTIONS! Use the Q&A Panel on the Right This webinar is being recorded for future playback. Recordings will be available on Embarcadero’s YouTube channel Your Presenter: Jim McKeeth Embarcadero Technologies [email protected] | @JimMcKeeth Chief Developer Advocate & Engineer Agenda • Overview • Installation • Supported platforms • PAServer • SDK & Packages • Usage • UI Elements • Samples • Database Access FireDAC • Migrating from Windows VCL • midaconverter.com • 3rd Party Support • Broadway Web Why FMX on Linux? • Education - Save money on Windows licenses • Kiosk or Point of Sale - Single purpose computers with locked down user interfaces • Security - Linux offers more security options • IoT & Industrial Automation - Add user interfaces for integrated systems • Federal Government - Many govt systems require Linux support • Choice - Now you can, so might as well! Delphi for Linux History • 1999 Kylix: aka Delphi for Linux, introduced • It was a port of the IDE to Linux • Linux x86 32-bit compiler • Used the Trolltech QT widget library • 2002 Kylix 3 was the last update to Kylix • 2017 Delphi 10.2 “Tokyo” introduced Delphi for x86 64-bit Linux • IDE runs on Windows, cross compiles to Linux via the PAServer • Designed for server side development - no desktop widget GUI library • 2017 Eugene -

Debian \ Amber \ Arco-Debian \ Arc-Live \ Aslinux \ Beatrix
Debian \ Amber \ Arco-Debian \ Arc-Live \ ASLinux \ BeatriX \ BlackRhino \ BlankON \ Bluewall \ BOSS \ Canaima \ Clonezilla Live \ Conducit \ Corel \ Xandros \ DeadCD \ Olive \ DeMuDi \ \ 64Studio (64 Studio) \ DoudouLinux \ DRBL \ Elive \ Epidemic \ Estrella Roja \ Euronode \ GALPon MiniNo \ Gibraltar \ GNUGuitarINUX \ gnuLiNex \ \ Lihuen \ grml \ Guadalinex \ Impi \ Inquisitor \ Linux Mint Debian \ LliureX \ K-DEMar \ kademar \ Knoppix \ \ B2D \ \ Bioknoppix \ \ Damn Small Linux \ \ \ Hikarunix \ \ \ DSL-N \ \ \ Damn Vulnerable Linux \ \ Danix \ \ Feather \ \ INSERT \ \ Joatha \ \ Kaella \ \ Kanotix \ \ \ Auditor Security Linux \ \ \ Backtrack \ \ \ Parsix \ \ Kurumin \ \ \ Dizinha \ \ \ \ NeoDizinha \ \ \ \ Patinho Faminto \ \ \ Kalango \ \ \ Poseidon \ \ MAX \ \ Medialinux \ \ Mediainlinux \ \ ArtistX \ \ Morphix \ \ \ Aquamorph \ \ \ Dreamlinux \ \ \ Hiwix \ \ \ Hiweed \ \ \ \ Deepin \ \ \ ZoneCD \ \ Musix \ \ ParallelKnoppix \ \ Quantian \ \ Shabdix \ \ Symphony OS \ \ Whoppix \ \ WHAX \ LEAF \ Libranet \ Librassoc \ Lindows \ Linspire \ \ Freespire \ Liquid Lemur \ Matriux \ MEPIS \ SimplyMEPIS \ \ antiX \ \ \ Swift \ Metamorphose \ miniwoody \ Bonzai \ MoLinux \ \ Tirwal \ NepaLinux \ Nova \ Omoikane (Arma) \ OpenMediaVault \ OS2005 \ Maemo \ Meego Harmattan \ PelicanHPC \ Progeny \ Progress \ Proxmox \ PureOS \ Red Ribbon \ Resulinux \ Rxart \ SalineOS \ Semplice \ sidux \ aptosid \ \ siduction \ Skolelinux \ Snowlinux \ srvRX live \ Storm \ Tails \ ThinClientOS \ Trisquel \ Tuquito \ Ubuntu \ \ A/V \ \ AV \ \ Airinux \ \ Arabian