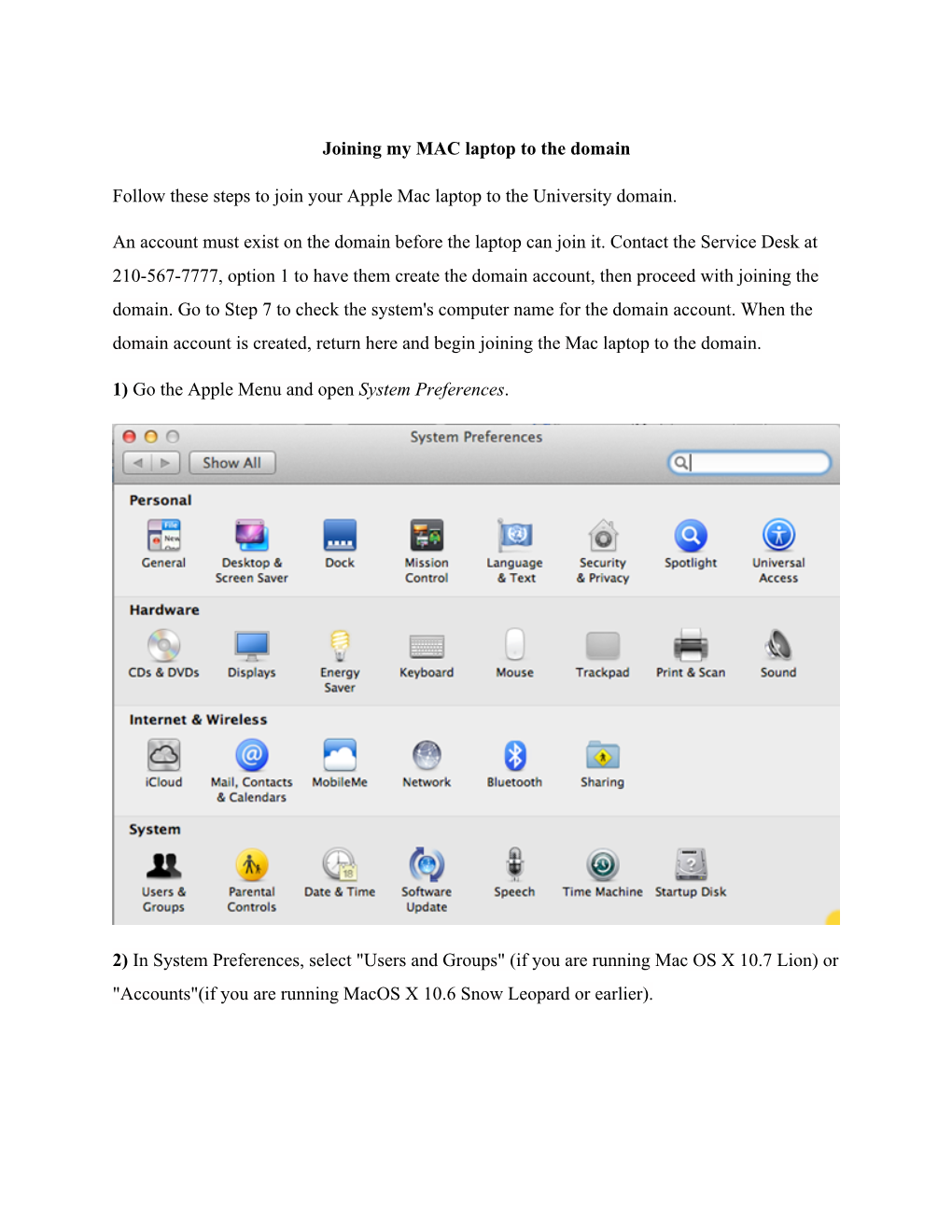
Joining My MAC Laptop to the Domain Follow These Steps to Join Your
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mac OS X Server Administrator's Guide
034-9285.S4AdminPDF 6/27/02 2:07 PM Page 1 Mac OS X Server Administrator’s Guide K Apple Computer, Inc. © 2002 Apple Computer, Inc. All rights reserved. Under the copyright laws, this publication may not be copied, in whole or in part, without the written consent of Apple. The Apple logo is a trademark of Apple Computer, Inc., registered in the U.S. and other countries. Use of the “keyboard” Apple logo (Option-Shift-K) for commercial purposes without the prior written consent of Apple may constitute trademark infringement and unfair competition in violation of federal and state laws. Apple, the Apple logo, AppleScript, AppleShare, AppleTalk, ColorSync, FireWire, Keychain, Mac, Macintosh, Power Macintosh, QuickTime, Sherlock, and WebObjects are trademarks of Apple Computer, Inc., registered in the U.S. and other countries. AirPort, Extensions Manager, Finder, iMac, and Power Mac are trademarks of Apple Computer, Inc. Adobe and PostScript are trademarks of Adobe Systems Incorporated. Java and all Java-based trademarks and logos are trademarks or registered trademarks of Sun Microsystems, Inc. in the U.S. and other countries. Netscape Navigator is a trademark of Netscape Communications Corporation. RealAudio is a trademark of Progressive Networks, Inc. © 1995–2001 The Apache Group. All rights reserved. UNIX is a registered trademark in the United States and other countries, licensed exclusively through X/Open Company, Ltd. 062-9285/7-26-02 LL9285.Book Page 3 Tuesday, June 25, 2002 3:59 PM Contents Preface How to Use This Guide 39 What’s Included -

Tinkertool System 7 Reference Manual Ii
Documentation 0642-1075/2 TinkerTool System 7 Reference Manual ii Version 7.5, August 24, 2021. US-English edition. MBS Documentation 0642-1075/2 © Copyright 2003 – 2021 by Marcel Bresink Software-Systeme Marcel Bresink Software-Systeme Ringstr. 21 56630 Kretz Germany All rights reserved. No part of this publication may be redistributed, translated in other languages, or transmitted, in any form or by any means, electronic, mechanical, recording, or otherwise, without the prior written permission of the publisher. This publication may contain examples of data used in daily business operations. To illustrate them as completely as possible, the examples include the names of individuals, companies, brands, and products. All of these names are fictitious and any similarity to the names and addresses used by an actual business enterprise is entirely coincidental. This publication could include technical inaccuracies or typographical errors. Changes are periodically made to the information herein; these changes will be incorporated in new editions of the publication. The publisher may make improvements and/or changes in the product(s) and/or the program(s) described in this publication at any time without notice. Make sure that you are using the correct edition of the publication for the level of the product. The version number can be found at the top of this page. Apple, macOS, iCloud, and FireWire are registered trademarks of Apple Inc. Intel is a registered trademark of Intel Corporation. UNIX is a registered trademark of The Open Group. Broadcom is a registered trademark of Broadcom, Inc. Amazon Web Services is a registered trademark of Amazon.com, Inc. -

Mac OS X: an Introduction for Support Providers
Mac OS X: An Introduction for Support Providers Course Information Purpose of Course Mac OS X is the next-generation Macintosh operating system, utilizing a highly robust UNIX core with a brand new simplified user experience. It is the first successful attempt to provide a fully-functional graphical user experience in such an implementation without requiring the user to know or understand UNIX. This course is designed to provide a theoretical foundation for support providers seeking to provide user support for Mac OS X. It assumes the student has performed this role for Mac OS 9, and seeks to ground the student in Mac OS X using Mac OS 9 terms and concepts. Author: Robert Dorsett, manager, AppleCare Product Training & Readiness. Module Length: 2 hours Audience: Phone support, Apple Solutions Experts, Service Providers. Prerequisites: Experience supporting Mac OS 9 Course map: Operating Systems 101 Mac OS 9 and Cooperative Multitasking Mac OS X: Pre-emptive Multitasking and Protected Memory. Mac OS X: Symmetric Multiprocessing Components of Mac OS X The Layered Approach Darwin Core Services Graphics Services Application Environments Aqua Useful Mac OS X Jargon Bundles Frameworks Umbrella Frameworks Mac OS X Installation Initialization Options Installation Options Version 1.0 Copyright © 2001 by Apple Computer, Inc. All Rights Reserved. 1 Startup Keys Mac OS X Setup Assistant Mac OS 9 and Classic Standard Directory Names Quick Answers: Where do my __________ go? More Directory Names A Word on Paths Security UNIX and security Multiple user implementation Root Old Stuff in New Terms INITs in Mac OS X Fonts FKEYs Printing from Mac OS X Disk First Aid and Drive Setup Startup Items Mac OS 9 Control Panels and Functionality mapped to Mac OS X New Stuff to Check Out Review Questions Review Answers Further Reading Change history: 3/19/01: Removed comment about UFS volumes not being selectable by Startup Disk. -

Zoom – Facilitating a Meeting
Zoom – Facilitating a Meeting Prepared for U3A Victoria By Russell Incoll Updated September 13th, 2020 1 Table of Contents How to use this Guide There is a lot of information in this document, and people come to this document with a range of skills and knowledge. With this in mind we have included a clickable table of contents. So, our recommendation is that you use the table of contents to click on the topic of interest to move you directly to the item on which you need information, rather than read the whole document. At the bottom of each page is an icon, on which you can click, and you will be returned to the top of the document. You can also use “Command + F” on a Mac or “Control + F” to find the subject in which you are interested. Introduction ................................................................................................................. 6 What is Zoom ............................................................................................................... 6 Getting Zoom on Your Device .......................................................................................... 6 Initial Settings .................................................................................................. 6 Zoom Settings for Hosts ................................................................................................. 8 Computer Equipment............................................................................................... 8 Internet Speed ...................................................................................................... -

Best Practices for Integrating OS X with Active Directory
Apple Technical White Paper Best Practices for Integrating OS X with Active Directory OS X Mountain Lion v10.8 Contents Introduction ........................................................................................................................3 How to Integrate OS X with Active Directory .......................................................4 Enterprise Integration Challenges .............................................................................7 Deployment Strategies ..................................................................................................9 Home Directories ..............................................................................................................10 Conclusion ...........................................................................................................................11 Appendix A: More Information ....................................................................................12 Appendix B: Third-Party Add-on Solutions ............................................................13 2 Apple Technical White Paper Best Practices for Integrating OS X with Active Directory Introduction Apple’s support for Active Directory within OS X enables Mac clients and servers to integrate smoothly into existing Active Directory environments, and provides the option of deploying a single, directory services infrastructure that can support both Mac and Windows clients. Apple’s Built-in Solution Large organizations have a need to manage user identities and access across a variety -

How to Disable Gatekeeper and Allow Apps from Anywhere in Macos Sierra
How to Disable Gatekeeper and Allow Apps From Anywhere in macOS Sierra Gatekeeper, first introduced in OS X Mountain Lion, is a Mac security feature which prevents the user from launching potentially harmful applications. In macOS Sierra, however, Apple made some important changes to Gatekeeper that seemingly limit the choices of power users. But don’t worry, Gatekeeper can still be disabled in Sierra. Here’s how. Stand out at the party or promote your business with colorful powder coated and custom engraved Yeti tumblers from Perfect Etch. Traditionally, Gatekeeper offered three settings of increasing security: anywhere, App Store and identified developers, and App Store only. The first choice, as its name describes, allowed users to launch applications from any source, effectively disabling the Gatekeeper feature. The second choice allowed users to run apps from the Mac App Store as well as from software developers who have registered with Apple and securely sign their applications. Finally, the most secure setting limited users to running apps obtained from the Mac App Store only. While the secure options were good ideas for less experienced Mac users, power users found Gatekeeper to be too limiting and typically sought to disable it by setting it to “Anywhere.” In macOS Sierra, however, the “Anywhere” option is gone, leaving “App Store” and “App Store and identified developers” as the only two options. Disable Gatekeeper in macOS Sierra The Gatekeeper settings can be found in System Preferences > Security & Privacy > General. The Gatekeeper options are located beneath “All apps downloaded from:” with the choice of “Anywhere” missing. Thankfully, the “Anywhere” setting can be restored to Gatekeeper in Sierra with a Terminal command. -

BLACKLIGHT 2020 R1 Release Notes
BlackLight 2020 R1 Release Notes April 20, 2020 Thank you for using BlackBag Technologies products. The Release Notes for this version include important information about new features and improvements made to BlackLight. In addition, this document contains known limitations, supported versions, and updated system requirements. While this information is complete at time of release, it is subject to change without notice and is provided for informational purposes only. Summary To enhance our forensic analysis tool, BlackLight 2020 R1 includes: • Apple Keychain Processing • Processing iCloud Productions obtained via search warrants from Apple • Additional processing of Spotlight Artifacts • Updated Recent Items parsing for macOS In Actionable Intel • Parsing AirDrop Artifacts • Updates to information parsed for macOS systems in Extended Information • Added support for log file parsing from logical evidence files or folders • Support added for Volexity Surge Memory images • Email loading process improved for faster load times • Support added for extended attributes in logical evidence files • Newly parsed items added to Smart Index (Keychain, Spotlight, and AirDrop) NEW FEATURES Apple Keychain Processing Keychains are encrypted containers built into macOS and iOS. Keychains store passwords and account information so users do not have to type in usernames and passwords. Form autofill information and secure notes can also be stored in keychains. In macOS a System keychain, accessible by all users, stores AirPort (WiFi) and Time Machine passwords. The System keychain does not require a password to open. Each user account has its own login keychain. By default, each user’s login keychain is opened with the user’s login password. While users can change this, most users do not. -

Open Directory Administration for Version 10.5 Leopard Second Edition
Mac OS X Server Open Directory Administration For Version 10.5 Leopard Second Edition Apple Inc. © 2008 Apple Inc. All rights reserved. The owner or authorized user of a valid copy of Mac OS X Server software may reproduce this publication for the purpose of learning to use such software. No part of this publication may be reproduced or transmitted for commercial purposes, such as selling copies of this publication or for providing paid-for support services. Every effort has been made to make sure that the information in this manual is correct. Apple Inc., is not responsible for printing or clerical errors. Apple 1 Infinite Loop Cupertino CA 95014-2084 www.apple.com The Apple logo is a trademark of Apple Inc., registered in the U.S. and other countries. Use of the “keyboard” Apple logo (Option-Shift-K) for commercial purposes without the prior written consent of Apple may constitute trademark infringement and unfair competition in violation of federal and state laws. Apple, the Apple logo, iCal, iChat, Leopard, Mac, Macintosh, QuickTime, Xgrid, and Xserve are trademarks of Apple Inc., registered in the U.S. and other countries. Finder is a trademark of Apple Inc. Adobe and PostScript are trademarks of Adobe Systems Incorporated. UNIX is a registered trademark of The Open Group. Other company and product names mentioned herein are trademarks of their respective companies. Mention of third-party products is for informational purposes only and constitutes neither an endorsement nor a recommendation. Apple assumes no responsibility with regard to the performance or use of these products. -
MATC Mac System Preferences Defined
MATC Mac System Preferences Defined: Below are all of the standard settings that your MATC Macintosh system preferences should be set for. If they differ by name or appearance, it may be due to versions of the operating system. The following illustrations are based on Macintosh OS X 10.4.7. In addition, these screens are taken from my personal Macintosh therefore, the names will reflect my personal settings, but your names could reflect your personal settings in much the same manner. Please look carefully to notice the best setting for your Mac. I will be highlighting the area of concern in some system preferences. Personal Settings: Appearance system preference MATC Macintosh Standard System Preferences Dashboard and Expose Desktop and Screen Saver Page 2 MATC Macintosh Standard System Preferences Dock International See edit list on the next page. Page 3 MATC Macintosh Standard System Preferences Edit list for the language list. Please keep English checked and active. Formats Page 4 MATC Macintosh Standard System Preferences Input Menu. This is where the keyboard viewer is located. Security-No Master Password! Page 5 MATC Macintosh Standard System Preferences Spotlight Page 6 MATC Macintosh Standard System Preferences Hardware Settings Bluetooth Settings Bluetooth Devices Page 7 MATC Macintosh Standard System Preferences Bluetooth Sharing CD’s and DVD’s Displays Show displays in menu bar for easy access to changing the display resolutions. Page 8 MATC Macintosh Standard System Preferences Energy Saver. Set the computer to never sleep everywhere! Energy Saver-Laptop Battery Settings Page 9 MATC Macintosh Standard System Preferences Keyboard and Mouse Trackpad-for Laptop users Notice the new feature for new Macintosh Laptop Users! Page 10 MATC Macintosh Standard System Preferences Mouse-Mighty Mouse users Bluetooth Settings Page 11 MATC Macintosh Standard System Preferences Keyboard Shortcuts Print and Fax Main The printers will be personalized for each person and each Mac. -

The Apple Ecosystem
APPENDIX A The Apple Ecosystem There are a lot of applications used to manage Apple devices in one way or another. Additionally, here’s a list of tools, sorted alphabetically per category in order to remain vendor agnostic. Antivirus Solutions for scanning Macs for viruses and other malware. • AVG: Basic antivirus and spyware detection and remediation. • Avast: Centralized antivirus with a cloud console for tracking incidents and device status. • Avira: Antivirus and a browser extension. Avira Connect allows you to view device status online. • BitDefender: Antivirus and malware managed from a central console. • CarbonBlack: Antivirus and Application Control. • Cylance: Ransomware, advanced threats, fileless malware, and malicious documents in addition to standard antivirus. • Kaspersky: Antivirus with a centralized cloud dashboard to track device status. © Charles Edge and Rich Trouton 2020 707 C. Edge and R. Trouton, Apple Device Management, https://doi.org/10.1007/978-1-4842-5388-5 APPENDIX A THe AppLe ECOSYSteM • Malware Bytes: Antivirus and malware managed from a central console. • McAfee Endpoint Security: Antivirus and advanced threat management with a centralized server to track devices. • Sophos: Antivirus and malware managed from a central console. • Symantec Mobile Device Management: Antivirus and malware managed from a central console. • Trend Micro Endpoint Security: Application whitelisting, antivirus, and ransomware protection in a centralized console. • Wandera: Malicious hot-spot monitoring, jailbreak detection, web gateway for mobile threat detection that integrates with common MDM solutions. Automation Tools Scripty tools used to automate management on the Mac • AutoCasperNBI: Automates the creation of NetBoot Images (read: NBI’s) for use with Casper Imaging. • AutoDMG: Takes a macOS installer (10.10 or newer) and builds a system image suitable for deployment with Imagr, DeployStudio, LANrev, Jamf Pro, and other asr or Apple Systems Restore-based imaging tools. -

Aver IFP Screen Share App Frequently Asked Questions
AVer IFP Screen Share App Frequently Asked Questions 3/1/2018 This document is intended to help the user or the network administrator to ensure that the network environment is compatible with AVer IFP Screen Share App for AirPlay, Chromecast, and Miracast protocols. 0 Screen Sharing FAQ I cannot see the AirPlay icon on my iOS device If the AirPlay mirror icon isn't displaying on your iOS device, it isn't able to see the IFP running Screen Sharing App for one reason or another. The firewall on your computer may be preventing the devices from communicating. It's also possible that the firewall on your router is preventing internal network communication. Microsoft has included instructions for allowing applications through the Windows firewall: http://windows.microsoft.com/en-US/windows7/Allow-a-program-to-communicate-through-Windows- Firewall If you're using a Mac, Apple has provided similar instructions: http://support.apple.com/kb/ht1810 Corporate and school networks often block a number of ports from communicating across networks. You may need to have the school's IT department allow TCP ports 7000, 47000, 7100, 49228, 50259 and UDP 62572, 54780 to be open to communicate. The network must also be allowed to run Bonjour, MultiCast, and mDNS. Or you must also be on the same VLAN or subnet within the network to connect, Apple's Airplay cannot cross subnets/VLANs, this is a limitation of Apple's AirPlay. Apple has provided more instructions on this issue here: http://support.apple.com/kb/TS4215 Some Samsung device will not connect to Screen Share Samsung devices use a slight variation of the Google Cast protocol and may need the assistance of the free Google Home app to connect to IFP Screen Share. -

Apple Security Checklist Companion 2Nd Edition
Apple Security Checklist Companion 2nd Edition A practical guide for automating security standards in the Apple Enterprise with the Casper Suite September 2009 JAMF Software, LLC © 2009 JAMF Software, LLC. All Rights Reserved. JAMF Software has made all efforts to ensure that this guide is accurate. JAMF Software 1011 Washington Ave South Suite 350 Minneapolis, MN 55415 (612) 605-6625 JAMF Software, the JAMF Software logo, the Casper Suite, Casper Admin, Casper Imaging, Casper Remote, Casper VNC, Composer, the JAMF Software Server (JSS), JSS Mobile, JSS Set Up Utility, JAMFVNC, Recon and Recon for PC are all trademarks of JAMF Software, LLC registered in the US. Apple, the Apple logo, AirPort, AppleScript, AppleShare, AppleTalk, Bonjour, Boot Camp, ColorSync, Exposé, FileVault, FireWire, iCal, iChat, iMac, iSight, iTunes, Keychain, Leopard, Mac, Mac Book, Macintosh, Mac OS,QuickTime, Safari, Xgrid, Xsan, and Xserve are trademarks of Apple Inc., registered in the U.S. and other countries. Contents Introduction 4 Target Audience 4 How to use this guide 4 Acknowledgements 5 Regulatory Compliance Frameworks 6 Useful Links on Security Concern ASC Guide 7 Installing Mac OS X 8 Protecting System Hardware 9 Securing Global System Settings 10 Securing Accounts 11 Securing System Preferences 13 Securing Data Using Encryption 14 Information Assurance with Applications 15 Information Assurance with Services 16 Advanced Security Management Appendix A 17 Meeting Sarbanes-Oxley Objectives 19 Role Based Administrator Access 22 Software Restriction 23 CasperVNC Security 24 Change Local Administrator Account Password 28 Enforce Screen Saver Settings 30 Protocol Security 3 Introduction Target Audience The Apple Security Checklist Companion (ASCC) is intended for IT practitioners engaged in governance, compliance and security related to Macintosh OS X computers.