Steganogaphy and Hidden Watermarks with Openpuff
Total Page:16
File Type:pdf, Size:1020Kb
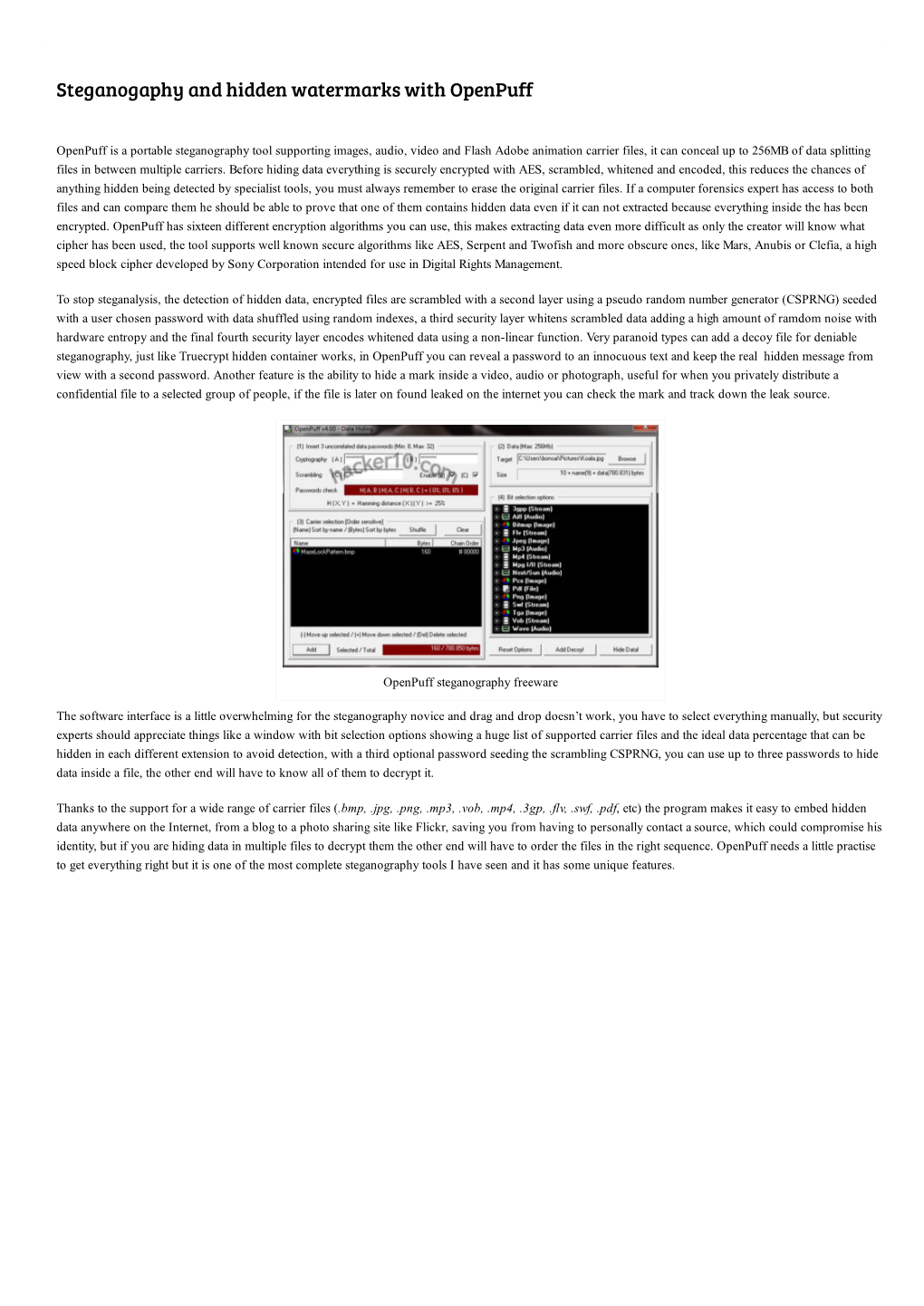
Load more
Recommended publications
-

A Method for Automatic Identification of Signatures of Steganography Software 3
SUBMITTED TO IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY 1 A Method for Automatic Identification of Signatures of Steganography Software Graeme Bell* and Yeuan-Kuen Lee Abstract—A fully automated, blind, media-type agnostic approach to research attention in steganalysis has been directed towards until now. steganalysis is presented here. Steganography may sometimes be exposed Implementation-induced artefacts are however a valid and interesting by detecting automatically-characterised regularities in output media target for steganalytic research, as the primary goal of steganography caused by weak implementations of steganography algorithms. Fast and accurate detection of steganography is demonstrated experimentally here (covert communication) is defeated whenever steganographic and across a range of media types and a variety of steganography approaches. non-steganographic media can be easily distinguished by any means. As Westfeld states in [2], Index Terms—blind, media-type agnostic, steganalysis, steganography, “The goal is to modify the carrier in an imperceptible way WAT-STEG only, so that it reveals nothing - neither the embedding of a message nor the embedded message itself.” I. INTRODUCTION In the past, discovery of implementation artefacts during research TEGANOGRAPHY is the field of research that studies how has occurred infrequently and on an ad-hoc basis. This paper dis- secret data can be hidden in carrier media, without being cusses a new steganalytic method by which the attempted discovery detectableS either to normal human observation or programmatic of these implementation-induced peculiarities can be automated. The scrutiny. Steganalysis [1]–[5] is the field of research that (primarily) method is applied in two stages. First, some known-stego training seeks methods to detect steganographic media. -

Openpuff Steganography & Watermarking
OPENPUFF V4.01 STEGANOGRAPHY & WATERMARKING Data hiding and watermarking made easy, safe and free EmbeddedSW © 2018 Send your suggestions, comments, bug reports, requests to [email protected] – Skype "embeddedsw.company" OPENPUFF HOMEPAGE LEGAL REMARKS P. 2 OPENPUFF INSTALLATION: WINDOWS P. 3 OPENPUFF INSTALLATION: LINUX P. 4 FEATURES: WHY IS THIS STEGANOGRAPHY TOOL DIFFERENT FROM THE OTHERS? P. 7 FEATURES: PROGRAM ARCHITECTURE P. 9 FEATURES: ADAPTIVE ENCODING AND STEGANALYSIS RESISTANCE P. 13 FEATURES: MULTI-CRYPTOGRAPHY & DATA OBFUSCATION P. 14 WHAT IS STEGANOGRAPHY? P. 15 WHAT IS DENIABLE STEGANOGRAPHY? P. 16 WHAT IS MARKING? P. 18 SUPPORTED FORMATS IN DETAIL P. 19 SUGGESTIONS FOR BETTER RESULTS P. 24 OPTIONS: BITS SELECTION LEVEL P. 26 STEP BY STEP DATA HIDING P. 27 STEP BY STEP DATA UNHIDING P. 31 STEP BY STEP MARK SETTING P. 34 STEP BY STEP MARK CHECKING P. 35 STEP BY STEP DATA & MARK ERASING P. 36 OPENPUFF V4.01 - ENGLISH - 11/JUL/2018 1 LEGAL REMARKS Remember: this program was not written for illegal use. Usage of this program that may violate your country's laws is severely forbidden. The author declines all responsibilities for improper use of this program. No patented code or format has been added to this program. THIS IS A FREE SOFTWARE: This software is released under LGPL 3.0 You’re free to copy, distribute, remix and make commercial use of this software under the following conditions: You have to cite the author (and copyright owner): WWW.EMBEDDEDSW.NET You have to provide a link to the author’s Homepage: WWW.EMBEDDEDSW.NET/OPENPUFF.HTML -

JPEG Versus GIF Images in Forms of LSB Steganography JPEG Versus
IJCSN International Journal of Computer Science and Network, Volume 2, Issue 6, December 2013 ISSN (Online) : 2277-5420 www.IJCSN.org 86 JPEG versus GIF Images in forms of LSB Steganography 1 ELTYEB E. ABED ELGABAR, 2 FAKHRELDEEN A. MOHAMMED 1, 2 Information Technology, College of Computer Science and Information Technology - Khulais, King Abdul Aziz University, Jeddah, Khulais, Saudi Arabia Abstract - Steganography (from Greek steganos, or "covered," message within another message called cover message and graphie, or "writing") is the hiding of undisclosed message such as text, image video and audio, so steganography can (such as text, image, audio and video) within an ordinary be seen as the complement of cryptography whose goal is message (such as text, image, audio and video) and the to hide the content of a message. extraction of it at its target (receiver). Steganography takes cryptography a step farther by hiding an encrypted Steganography message so that no one suspects it exists. This paper compares and analyses Least Significant Bit (LSB) algorithm using the cover object as an image with a focus on two types: JPEG and GIF. The comparison and analysis are done with deference Text Image Audio/video Protocol number of criteria (Robustness against statistical attacks, Invisibility, Steganalysis detection, Robustness against image manipulation, Efficient when amount of data reasonable, Fig1. Categories of Steganography Payload capacity, Unsuspicious files and Amount of embedded data) to understand their strengths and weaknesses. 1.1 Types of Steganography Keywords - Steganography, Steganographic, Least significant Steganography can be classified into various types bit (LSB), Lossless, lossy (General types) [30]: 1. -

An Approach for Stego-Insider Detection Based on a Hybrid Nosql Database †
Journal of Sensor and Actuator Networks Article An Approach for Stego-Insider Detection Based on a Hybrid NoSQL Database † Igor Kotenko 1,* , Andrey Krasov 2 , Igor Ushakov 2 and Konstantin Izrailov 1,2 1 St. Petersburg Federal Research Center of the Russian Academy of Sciences, 199178 St. Petersburg, Russia; [email protected] 2 Department of Secured Communication Systems, The Bonch-Bruevich State University of Telecommunications, 199178 St. Petersburg, Russia; [email protected] (A.K.); [email protected] (I.U.) * Correspondence: [email protected] † This paper is an extended version of the conference paper: Igor Kotenko, Andrey Krasov, Igor Ushakov and Konstantin Izrailov. Detection of Stego-Insiders in Corporate Networks Based on a Hybrid NoSQL Database Model. The 4th International Conference on Future Networks and Distributed Systems (ICFNDS 2020). Saint-Petersburg, Russia, 26–27 November 2020. Abstract: One of the reasons for the implementation of information security threats in organizations is the insider activity of its employees. There is a big challenge to detect stego-insiders-employees who create stego-channels to secretly receive malicious information and transfer confidential information across the organization’s perimeter. Especially presently, with great popularity of wireless sensor networks (WSNs) and Internet of Things (IoT) devices, there is a big variety of information that could be gathered and processed by stego-insiders. Consequently, the problem arises of identifying such intruders and their transmission channels. The paper proposes an approach to solving this Citation: Kotenko, I.; Krasov, A.; problem. The paper provides a review of the related works in terms of insider models and methods Ushakov I.; Izrailov K. -

Steganography FAQ
Steganography FAQ Aelphaeis Mangarae [Zone-H.Org] March 18th 2006 http://zone-h.org © Copyright Zone-H.Org 2006 Zone-H.Org Table Of Contents Introduction What Is Steganography? Steganography Terms History Of Steganography How Does It Work? Steganography In Images Steganography In Audio Steganography In Video Steganography In Documents Detecting Steganography Could Steganography Be Used By Terrorists? Steganography Tools Steganalysis Tools Conclusion About The Author Greetz To Zone-H.Org Introduction Steganography is a subject which is rarely touched upon by most IT Security Enthusiasts. Most people don't see Steganography has a potential threat, some people don't even know what Steganography is. With this FAQ I hope to answer any questions anyone may want to ask about Steganography, and to educate people so they can understand what exactly Steganography is. Is Steganography a potential threat? Well your about to find out. What Is Steganography? Steganography is the practice of hiding private or sensitive information within something that appears to be nothing out of the usual. Steganography is often confused with cryptology because the two are similar in the way that they both are used to protect important information. The difference between the two is that Steganography involves hiding information so it appears that no information is hidden at all. If a person or persons views the object that the information is hidden inside of he or she will have no idea that there is any hidden information, therefore the person will not attempt to decrypt the information. Steganography comes from the Greek words Steganós (Covered) and Graptos (Writing). -

Openpuff Steganography & Watermarking
OPENPUFF V4.01 STEGANOGRAFIA & WATERMARKING Nascondere dati e marking, semplice, sicuro e gratuito EmbeddedSW © 2018 Inviate i vostri suggerimenti, commenti, segnalazioni, richieste a [email protected] – Skype "embeddedsw.company" OPENPUFF HOMEPAGE NOTE LEGALI P. 2 INSTALLARE OPENPUFF: WINDOWS P. 3 INSTALLARE OPENPUFF: LINUX P. 4 CARATTERISTICHE: PERCHÈ QUESTO PROGRAMMA STEGANOGRAFICO È DIFFERENTE DAGLI ALTRI? P. 7 CARATTERISTICHE: ARCHITETTURA DEL PROGRAMMA P. 9 CARATTERISTICHE: CODIFICA ADATTIVA E RESISTENZA ALLA STEGANALISI P. 13 CARATTERISTICHE: MULTI CRITTOGRAFIA E OFFUSCAMENTO DATI P. 14 COSA È LA STEGANOGRAFIA? P. 15 COSA È LA STEGANOGRAFIA NEGABILE? P. 16 COSA È IL MARKING? P. 18 FORMATI SUPPORTATI IN DETTAGLIO P. 19 SUGGERIMENTI PER RISULTATI MIGLIORI P. 24 OPZIONI: LIVELLO DI SELEZIONE BIT P. 26 DATA HIDING IN DETTAGLIO P. 27 DATA UNHIDING IN DETTAGLIO P. 31 MARK SETTING IN DETTAGLIO P. 34 MARK CHECKING IN DETTAGLIO P. 35 DATA & MARK ERASING IN DETTAGLIO P. 36 OPENPUFF V4.01 - ITALIANO - 11/JUL/2018 1 NOTE LEGALI Ricordate: questo programma non è stato scritto per uso illegale. L’uso di questo programma in violazione delle leggi del vostro paese è assolutamente proibito. L’autore declina qualsiasi responsabilità conseguente dall’uso improprio di questo programma. Né codice né formati coperti da brevetto sono stati inseriti in questo programma. QUESTO È UN FREE SOFTWARE: Questo software è rilasciato con licenza LGPL 3.0 Siete liberi di copiare, distribuire, modificare e fare uso commerciale di questo software alle seguenti -

Authentication of MP4 File by Perceptual Hash and Data Hiding, Pp. 304-314
Authentication of MP4 File by Perceptual Hash and Data Hiding, pp. 304-314 AUTHENTICATION OF MP4 FILE BY PERCEPTUAL HASH AND DATA HIDING April Pyone Maung Maung1, Yiqi Tew2, and KokSheik Wong3 1Faculty of Computer Science & Information Technology, University of Malaya, Malaysia 2Faculty of Computing and Information Technology, Tunku Abdul Rahman University College, Malaysia 3School of Information Technology, Monash University Malaysia, Malaysia Email: [email protected]* (corresponding author), [email protected]* (corresponding author), [email protected] DOI: https://doi.org/10.22452/mjcs.vol32no4.4 ABSTRACT With advances in multimedia signal processing and abundance of data, multimedia authentication becomes more and more challenging and demanding. Although many prior techniques were put forward to authenticate individual video or audio stream, the cross-layer authentication of audio-visual content as a whole remains unexplored. In this work, an authentication system of the dominant audio-visual content file format (MP4) is presented. Specifically, the perceptual hashes of I-frames from video stream are encrypted and embedded into the audio stream, and the audio hash vector is encrypted and embedded in the synchronization information, i.e., stts box, in the MP4 file. The proposed system is implemented and tested on various videos downloaded from YouTube. Results show that the proposed system can authenticate MP4 files correctly without degrading the video quality while being able to provide indication of tampering. Keywords: MP4, Perceptual Hash, Data Hiding, Authentication 1.0 INTRODUCTION Multimedia authentication is the process of confirming the genuineness of a content and its alleged source. It is vital and critical for many applications, especially those involving legal issues. -

An Examination on Information Hiding Tools for Steganography
INTERNATIONAL JOURNAL OF INFORMATION SECURITY SCIENCE İ. Karadoğan, R. Daş, Vol. 3, No.3 An Examination on Information Hiding Tools for Steganography İsmail Karadoğan*, Resul Daş** *Kahramanmaraş Sütçü İmam Univ., Elbistan Vocational School, Department of Computer Technologies, Kahramanmaraş, Turkey. e-mail: [email protected] **Fırat University, Technology Faculty, Department of Software Engineering, Elazığ, Turkey. e-mail: [email protected] Abstract— In this paper, information about the steganographic methods and tools that are used to hide important data in digital media are presented. At the same time, different aspects of these tools such as used methods, types of hidden data and cover media are examined. Keywords- Information security; information hiding; steganography; steganography tools. 1. Introduction Since the dawn of written communication people have been concerned with both obscuring the contents of communication (Cryptography) and obscuring the fact that communication is taking place (Steganography). As a result of the digitization of communication, new stegonagraphic approaches, protocols and Figure 1. The data hiding diagram as a simple form applications have been developed. Conforming to the principle of ‘Defense in Steganography is the art and science of hiding Depth’ it is standard practice to employ secret messages or information within innocent cryptography, compression, and steganography looking media. Because the sender and intended when hiding data. Even if the existence of covert recipient want to communicate securely, the communication can be determined by unwanted carrier medium in which the hidden message is third parties, the encoding or the obfuscation of embedded should not arouse the suspicion of third data complicates the retrieval of data, typically parties’ concerning the existence of the hidden requiring access to keys. -

Analysis of Steganographic on Digital Evidence Using General Computer Forensic Investigation Model Framework
(IJACSA) International Journal of Advanced Computer Science and Applications, Vol. 11, No. 11, 2020 Analysis of Steganographic on Digital Evidence using General Computer Forensic Investigation Model Framework 1 Muh. Hajar Akbar Sunardi2* Imam Riadi3 Master Program of Informatics Electrical Engineering Department Information System Department Universitas Ahmad Dahlan Universitas Ahmad Dahlan Universitas Ahmad Dahlan Yogyakarta, Indonesia Yogyakarta, Indonesia Yogyakarta, Indonesia Abstract—Steganography is one of the anti-forensic Tick type malware was spread by the creator through a techniques used by criminals to hide information in other steganography technique by inserting it into an image with the messages which can cause problems in the investigation process extension jpg to spy on Japanese, South Korean, Russian, and difficulties in obtaining original information evidence on the Singaporean and Chinese companies. Reported by digital crime. Digital forensic analysts are required ability to find Kompas.com December 9th, 2017 entitled "16 Years of 9/11 and extract the messages that have been inserted by using proper Attack: WTC Collapsed not because of a Plane Collision?". At tools. The purpose of this research is to analyze the hidden digital that time, terrorists hide their terror activities in various digital evidence using steganography techniques. This research uses the media such as images, audios, and videos. The maps and static forensics method by applying five stages in the Generic photos of targets as well as orders for terrorist activity in sport Forensics Investigation Model framework, namely pre-process, chat rooms, porn bulletin boards, and other websites. The acquisition & preservation, analysis, presentation, and post- process as well as extracting files that have been infiltrated based existence of cases reported by the mass media regarding on case scenarios involving digital crime. -

Text Security Using Lossless Portable Network Graphics
Vol-4 Issue-1 2018 IJARIIE-ISSN(O)-2395-4396 Text security using lossless portable network graphics Swapnali Patil1, Prof.P.B.Koli 2, ProfN.R.Wankhade3 1 Student, Computer Department,late G.N.Sapkal coe, Maharashtra,India 2Assoc Professor, Department,late G.N.Sapkal coe, Maharashtra,India 3HOD and Asst Professor, Department,late G.N.Sapkal coe, Maharashtra,India ABSTRACT Data is an important asset for any individual or organization and must be protected from intruders or hackers. The need to hide data from hackers has existed since ancient times, and nowadays, there are developments in digital media, such as audio, video, images, and so on. To secure secret information, different media methods are used and steganography is one. Steganography hides the data under other data without any differen tiable changes. Many individual steganography tools can be used to transfer data securely and, in this report, a new tool is proposed that decreases time and effort. Using this tool, we hide the text in images in one place, so there was no need to have access to multiple tools. This proposed tool developed using the least significant bit (LSB) approach. Steganography is a method of hiding secret messages in a cover object while communication takes place between sender and receiver. Security of confidential information has always been a major issue from the past times to the present time. It has always been the interested topic for researchers to develop secure techniques to send data without revealing it to anyone other than the receiver. There for from time to time researchers have developed many techniques to fulfil secure transfer of data and steganography is one of them. -

CANVASS - a Steganalysis Forensic Tool for JPEG Images
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Embry-Riddle Aeronautical University 2010 Annual ADFSL Conference on Digital Forensics, Security and Law Proceedings May 20th, 1:00 PM CANVASS - A Steganalysis Forensic Tool for JPEG Images Jennifer L. Davidson Department of Mathematics, Iowa State University, Ames, IA, [email protected] Jaikishan Jalan Department of Computer Science, Iowa State University, Ames, IA, [email protected] Follow this and additional works at: https://commons.erau.edu/adfsl Part of the Computer Engineering Commons, Computer Law Commons, Electrical and Computer Engineering Commons, Forensic Science and Technology Commons, and the Information Security Commons Scholarly Commons Citation Davidson, Jennifer L. and Jalan, Jaikishan, "CANVASS - A Steganalysis Forensic Tool for JPEG Images" (2010). Annual ADFSL Conference on Digital Forensics, Security and Law. 6. https://commons.erau.edu/adfsl/2010/thursday/6 This Peer Reviewed Paper is brought to you for free and open access by the Conferences at Scholarly Commons. It has been accepted for inclusion in Annual ADFSL Conference on Digital Forensics, Security and Law by an (c)ADFSL authorized administrator of Scholarly Commons. For more information, please contact [email protected]. ADFSL Conference on Digital Forensics, Security and Law, 2010 CANVASS - A Steganalysis Forensic Tool for JPEG Images Jennifer L. Davidson Department of Mathematics Iowa State University, Ames, IA 50011 Phone: (515) 294-0302 Fax: (515) 294-5454 [email protected] Jaikishan Jalan Department of Computer Science Iowa State University, Ames, IA 50011 [email protected] ABSTRACT Steganography is a way to communicate a message such that no one except the sender and recipient suspects the existence of the message. -

Identification of LSB Image Steganography Using Cover Image Comparisons
Journal of Digital Forensics, Security and Law Volume 15 Article 6 February 2021 Identification of LSB image Steganography using Cover Image Comparisons Michael Pelosi Texas A&M University — Texarkana, [email protected] Chuck Easttom Independent Forensic Expert, [email protected] Follow this and additional works at: https://commons.erau.edu/jdfsl Part of the Computer Law Commons, and the Information Security Commons Recommended Citation Pelosi, Michael and Easttom, Chuck (2021) "Identification of LSB image Steganography using Cover Image Comparisons," Journal of Digital Forensics, Security and Law: Vol. 15 , Article 6. DOI: https://doi.org/10.15394/jdfsl.2021.1551 Available at: https://commons.erau.edu/jdfsl/vol15/iss2/6 This Article is brought to you for free and open access by the Journals at Scholarly Commons. It has been accepted for inclusion in Journal of Digital Forensics, Security and Law by an authorized administrator of (c)ADFSL Scholarly Commons. For more information, please contact [email protected]. Journal of Digital Forensics, Security and Law POSITIVE IDENTIFICATION OF LEAST SIGNIFICANT BIT (LSB)1 IMAGE STEGANOGRAPHY USING COVER IMAGE COMPARISONS ABSTRACT Steganography has long been used to counter forensic investigation. This use of steganography as an anti- forensics technique is becoming more widespread. This requires forensic examiners to have additional tools to more effectively detect steganography. In this paper we introduce a new software concept specifically designed to allow the digital forensics professional to clearly identify and attribute instances of least significant bit (LSB) image steganography by using the original cover image in side-by-side comparison with a suspected steganographic payload image.