Privacy-Preserving Statistical Estimation with Optimal Convergence Rates∗
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lecture 12 Robust Estimation
Lecture 12 Robust Estimation Prof. Dr. Svetlozar Rachev Institute for Statistics and Mathematical Economics University of Karlsruhe Financial Econometrics, Summer Semester 2007 Prof. Dr. Svetlozar Rachev Institute for Statistics and MathematicalLecture Economics 12 Robust University Estimation of Karlsruhe Copyright These lecture-notes cannot be copied and/or distributed without permission. The material is based on the text-book: Financial Econometrics: From Basics to Advanced Modeling Techniques (Wiley-Finance, Frank J. Fabozzi Series) by Svetlozar T. Rachev, Stefan Mittnik, Frank Fabozzi, Sergio M. Focardi,Teo Jaˇsic`. Prof. Dr. Svetlozar Rachev Institute for Statistics and MathematicalLecture Economics 12 Robust University Estimation of Karlsruhe Outline I Robust statistics. I Robust estimators of regressions. I Illustration: robustness of the corporate bond yield spread model. Prof. Dr. Svetlozar Rachev Institute for Statistics and MathematicalLecture Economics 12 Robust University Estimation of Karlsruhe Robust Statistics I Robust statistics addresses the problem of making estimates that are insensitive to small changes in the basic assumptions of the statistical models employed. I The concepts and methods of robust statistics originated in the 1950s. However, the concepts of robust statistics had been used much earlier. I Robust statistics: 1. assesses the changes in estimates due to small changes in the basic assumptions; 2. creates new estimates that are insensitive to small changes in some of the assumptions. I Robust statistics is also useful to separate the contribution of the tails from the contribution of the body of the data. Prof. Dr. Svetlozar Rachev Institute for Statistics and MathematicalLecture Economics 12 Robust University Estimation of Karlsruhe Robust Statistics I Peter Huber observed, that robust, distribution-free, and nonparametrical actually are not closely related properties. -

Investigating Statistical Privacy Frameworks from the Perspective of Hypothesis Testing 234 Able Quantity
Investigating Statistical Privacy Frameworks from the Perspective of Hypothesis Testing 234 able quantity. Only a limited number of previous works which can provide a natural and interpretable guide- [29, 34, 35] have investigated the question of how to line for selecting proper privacy parameters by system select a proper value of ǫ, but these approaches ei- designers and researchers. Furthermore, we extend our ther require complicated economic models or lack the analysis on unbounded DP to bounded DP and the ap- analysis of adversaries with arbitrary auxiliary informa- proximate (ǫ, δ)-DP. tion (see Section 2.3 for more details). Our work is in- Impact of Auxiliary Information. The conjecture spired by the interpretation of differential privacy via that auxiliary information can influence the design of hypothesis testing, initially introduced by Wasserman DP mechanisms has been made in prior work [8, 28, 32, and Zhou [27, 30, 60]. However, this interpretation has 33, 39, 65]. We therefore investigate the adversary’s ca- not been systematically investigated before in the con- pability based on hypothesis testing under three types text of our research objective, i.e., reasoning about the of auxiliary information: the prior distribution of the in- choice of the privacy parameter ǫ (see Section 2.4 for put record, the correlation across records, and the corre- more details). lation across time. Our analysis demonstrates that the We consider hypothesis testing [2, 45, 61] as the tool auxiliary information indeed influences the appropriate used by the adversary to infer sensitive information of selection of ǫ. The results suggest that, when possible an individual record (e.g., the presence or absence of and available, the practitioners of DP should explicitly a record in the database for unbounded DP) from the incorporate adversary’s auxiliary information into the outputs of privacy mechanisms. -
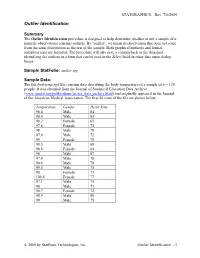
Outlier Identification.Pdf
STATGRAPHICS – Rev. 7/6/2009 Outlier Identification Summary The Outlier Identification procedure is designed to help determine whether or not a sample of n numeric observations contains outliers. By “outlier”, we mean an observation that does not come from the same distribution as the rest of the sample. Both graphical methods and formal statistical tests are included. The procedure will also save a column back to the datasheet identifying the outliers in a form that can be used in the Select field on other data input dialog boxes. Sample StatFolio: outlier.sgp Sample Data: The file bodytemp.sgd file contains data describing the body temperature of a sample of n = 130 people. It was obtained from the Journal of Statistical Education Data Archive (www.amstat.org/publications/jse/jse_data_archive.html) and originally appeared in the Journal of the American Medical Association. The first 20 rows of the file are shown below. Temperature Gender Heart Rate 98.4 Male 84 98.4 Male 82 98.2 Female 65 97.8 Female 71 98 Male 78 97.9 Male 72 99 Female 79 98.5 Male 68 98.8 Female 64 98 Male 67 97.4 Male 78 98.8 Male 78 99.5 Male 75 98 Female 73 100.8 Female 77 97.1 Male 75 98 Male 71 98.7 Female 72 98.9 Male 80 99 Male 75 2009 by StatPoint Technologies, Inc. Outlier Identification - 1 STATGRAPHICS – Rev. 7/6/2009 Data Input The data to be analyzed consist of a single numeric column containing n = 2 or more observations. -

2008 Annual Report
2008 Annual Report NATIONAL ACADEMY OF ENGINEERING ENGINEERING THE FUTURE 1 Letter from the President 3 In Service to the Nation 3 Mission Statement 4 Program Reports 4 Engineering Education 4 Center for the Advancement of Scholarship on Engineering Education 6 Technological Literacy 6 Public Understanding of Engineering Developing Effective Messages Media Relations Public Relations Grand Challenges for Engineering 8 Center for Engineering, Ethics, and Society 9 Diversity in the Engineering Workforce Engineer Girl! Website Engineer Your Life Project Engineering Equity Extension Service 10 Frontiers of Engineering Armstrong Endowment for Young Engineers-Gilbreth Lectures 12 Engineering and Health Care 14 Technology and Peace Building 14 Technology for a Quieter America 15 America’s Energy Future 16 Terrorism and the Electric Power-Delivery System 16 U.S.-China Cooperation on Electricity from Renewables 17 U.S.-China Symposium on Science and Technology Strategic Policy 17 Offshoring of Engineering 18 Gathering Storm Still Frames the Policy Debate 20 2008 NAE Awards Recipients 22 2008 New Members and Foreign Associates 24 2008 NAE Anniversary Members 28 2008 Private Contributions 28 Einstein Society 28 Heritage Society 29 Golden Bridge Society 29 Catalyst Society 30 Rosette Society 30 Challenge Society 30 Charter Society 31 Other Individual Donors 34 The Presidents’ Circle 34 Corporations, Foundations, and Other Organizations 35 National Academy of Engineering Fund Financial Report 37 Report of Independent Certified Public Accountants 41 Notes to Financial Statements 53 Officers 53 Councillors 54 Staff 54 NAE Publications Letter from the President Engineering is critical to meeting the fundamental challenges facing the U.S. economy in the 21st century. -

Digital Communication Systems 2.2 Optimal Source Coding
Digital Communication Systems EES 452 Asst. Prof. Dr. Prapun Suksompong [email protected] 2. Source Coding 2.2 Optimal Source Coding: Huffman Coding: Origin, Recipe, MATLAB Implementation 1 Examples of Prefix Codes Nonsingular Fixed-Length Code Shannon–Fano code Huffman Code 2 Prof. Robert Fano (1917-2016) Shannon Award (1976 ) Shannon–Fano Code Proposed in Shannon’s “A Mathematical Theory of Communication” in 1948 The method was attributed to Fano, who later published it as a technical report. Fano, R.M. (1949). “The transmission of information”. Technical Report No. 65. Cambridge (Mass.), USA: Research Laboratory of Electronics at MIT. Should not be confused with Shannon coding, the coding method used to prove Shannon's noiseless coding theorem, or with Shannon–Fano–Elias coding (also known as Elias coding), the precursor to arithmetic coding. 3 Claude E. Shannon Award Claude E. Shannon (1972) Elwyn R. Berlekamp (1993) Sergio Verdu (2007) David S. Slepian (1974) Aaron D. Wyner (1994) Robert M. Gray (2008) Robert M. Fano (1976) G. David Forney, Jr. (1995) Jorma Rissanen (2009) Peter Elias (1977) Imre Csiszár (1996) Te Sun Han (2010) Mark S. Pinsker (1978) Jacob Ziv (1997) Shlomo Shamai (Shitz) (2011) Jacob Wolfowitz (1979) Neil J. A. Sloane (1998) Abbas El Gamal (2012) W. Wesley Peterson (1981) Tadao Kasami (1999) Katalin Marton (2013) Irving S. Reed (1982) Thomas Kailath (2000) János Körner (2014) Robert G. Gallager (1983) Jack KeilWolf (2001) Arthur Robert Calderbank (2015) Solomon W. Golomb (1985) Toby Berger (2002) Alexander S. Holevo (2016) William L. Root (1986) Lloyd R. Welch (2003) David Tse (2017) James L. -

An Economic Analysis of Privacy Protection and Statistical Accuracy As Social Choices
An Economic Analysis of Privacy Protection and Statistical Accuracy as Social Choices John M. Abowd and Ian M. Schmutte August 15, 2018 Forthcoming in American Economic Review Abowd: U.S. Census Bureau HQ 8H120, 4600 Silver Hill Rd., Washington, DC 20233, and Cornell University, (email: [email protected]); Schmutte: Department of Eco- nomics, University of Georgia, B408 Amos Hall, Athens, GA 30602 (email: [email protected]). Abowd and Schmutte acknowledge the support of Alfred P. Sloan Foundation Grant G-2015-13903 and NSF Grant SES-1131848. Abowd acknowledges direct support from NSF Grants BCS-0941226, TC-1012593. Any opinions and conclusions are those of the authors and do not represent the views of the Census Bureau, NSF, or the Sloan Foundation. We thank the Center for Labor Economics at UC–Berkeley and Isaac Newton Institute for Mathematical Sciences, Cambridge (EPSRC grant no. EP/K032208/1) for support and hospitality. We are extremely grateful for very valuable com- ments and guidance from the editor, Pinelopi Goldberg, and six anonymous referees. We acknowl- edge helpful comments from Robin Bachman, Nick Bloom, Larry Blume, David Card, Michael Castro, Jennifer Childs, Melissa Creech, Cynthia Dwork, Casey Eggleston, John Eltinge, Stephen Fienberg, Mark Kutzbach, Ron Jarmin, Christa Jones, Dan Kifer, Ashwin Machanavajjhala, Frank McSherry, Gerome Miklau, Kobbi Nissim, Paul Oyer, Mallesh Pai, Jerry Reiter, Eric Slud, Adam Smith, Bruce Spencer, Sara Sullivan, Salil Vadhan, Lars Vilhuber, Glen Weyl, and Nellie Zhao along with seminar and conference participants at the U.S. Census Bureau, Cornell, CREST, George Ma- son, Georgetown, Microsoft Research–NYC, University of Washington Evans School, and SOLE. -

Calibrating Noise to Sensitivity in Private Data Analysis
Calibrating Noise to Sensitivity in Private Data Analysis Cynthia Dwork1, Frank McSherry1, Kobbi Nissim2, and Adam Smith3? 1 Microsoft Research, Silicon Valley. {dwork,mcsherry}@microsoft.com 2 Ben-Gurion University. [email protected] 3 Weizmann Institute of Science. [email protected] Abstract. We continue a line of research initiated in [10, 11] on privacy- preserving statistical databases. Consider a trusted server that holds a database of sensitive information. Given a query function f mapping databases to reals, the so-called true answer is the result of applying f to the database. To protect privacy, the true answer is perturbed by the addition of random noise generated according to a carefully chosen distribution, and this response, the true answer plus noise, is returned to the user. Previous work focused on the case of noisy sums, in which f = P i g(xi), where xi denotes the ith row of the database and g maps database rows to [0, 1]. We extend the study to general functions f, proving that privacy can be preserved by calibrating the standard devi- ation of the noise according to the sensitivity of the function f. Roughly speaking, this is the amount that any single argument to f can change its output. The new analysis shows that for several particular applications substantially less noise is needed than was previously understood to be the case. The first step is a very clean characterization of privacy in terms of indistinguishability of transcripts. Additionally, we obtain separation re- sults showing the increased value of interactive sanitization mechanisms over non-interactive. -

Magic Adversaries Versus Individual Reduction: Science Wins Either Way ?
Magic Adversaries Versus Individual Reduction: Science Wins Either Way ? Yi Deng1;2 1 SKLOIS, Institute of Information Engineering, CAS, Beijing, P.R.China 2 State Key Laboratory of Cryptology, P. O. Box 5159, Beijing ,100878,China [email protected] Abstract. We prove that, assuming there exists an injective one-way function f, at least one of the following statements is true: – (Infinitely-often) Non-uniform public-key encryption and key agreement exist; – The Feige-Shamir protocol instantiated with f is distributional concurrent zero knowledge for a large class of distributions over any OR NP-relations with small distinguishability gap. The questions of whether we can achieve these goals are known to be subject to black-box lim- itations. Our win-win result also establishes an unexpected connection between the complexity of public-key encryption and the round-complexity of concurrent zero knowledge. As the main technical contribution, we introduce a dissection procedure for concurrent ad- versaries, which enables us to transform a magic concurrent adversary that breaks the distribu- tional concurrent zero knowledge of the Feige-Shamir protocol into non-black-box construc- tions of (infinitely-often) public-key encryption and key agreement. This dissection of complex algorithms gives insight into the fundamental gap between the known universal security reductions/simulations, in which a single reduction algorithm or simu- lator works for all adversaries, and the natural security definitions (that are sufficient for almost all cryptographic primitives/protocols), which switch the order of qualifiers and only require that for every adversary there exists an individual reduction or simulator. 1 Introduction The seminal work of Impagliazzo and Rudich [IR89] provides a methodology for studying the lim- itations of black-box reductions. -

Calibrating Noise to Sensitivity in Private Data Analysis
Calibrating Noise to Sensitivity in Private Data Analysis Cynthia Dwork1, Frank McSherry1, Kobbi Nissim2, and Adam Smith3? 1 Microsoft Research, Silicon Valley. {dwork,mcsherry}@microsoft.com 2 Ben-Gurion University. [email protected] 3 Weizmann Institute of Science. [email protected] Abstract. We continue a line of research initiated in [10, 11] on privacy- preserving statistical databases. Consider a trusted server that holds a database of sensitive information. Given a query function f mapping databases to reals, the so-called true answer is the result of applying f to the database. To protect privacy, the true answer is perturbed by the addition of random noise generated according to a carefully chosen distribution, and this response, the true answer plus noise, is returned to the user. P Previous work focused on the case of noisy sums, in which f = i g(xi), where xi denotes the ith row of the database and g maps data- base rows to [0, 1]. We extend the study to general functions f, proving that privacy can be preserved by calibrating the standard deviation of the noise according to the sensitivity of the function f. Roughly speak- ing, this is the amount that any single argument to f can change its output. The new analysis shows that for several particular applications substantially less noise is needed than was previously understood to be the case. The first step is a very clean characterization of privacy in terms of indistinguishability of transcripts. Additionally, we obtain separation re- sults showing the increased value of interactive sanitization mechanisms over non-interactive. -

Cpsc 210/310 & Plsc
CPSC 310 and CPSC 210 // PLSC 369: Syllabus v1 Joan Feigenbaum Steven Wilkinson www.cs.yale.edu/homes/jf/ campuspress.yale.edu/steveniwilkinson/ Twenty-first century societies are faced with both threats and opportunities that combine sophisticated computation with politics and international relations in critical ways. Examples include cyber warfare; cyber espionage; cyber crime; the role of social media in democratic self-governance, authoritarian control, and election "hacking"; cryptocurrencies; and mass surveillance. CPSC 310 and CPSC 210 // PLSC 3691 examine some of the political challenges wrought by massive increases in the power of information and communication technologies and the potential for citizens and governments to harness those technologies to solve problems. They are co-taught by Professors Joan Feigenbaum (Computer Science) and Steven Wilkinson (Political Science). The two courses will have common lectures but separate sections. The CPSC 310 section is aimed at STEM students and has CPSC 223 or the equivalent as a prerequisite. The CPSC 210 // PLSC 369 section is aimed at social-science students and has no formal course prerequisites (but assumes Internet literacy). Students may earn credit for CPSC 310 or for CPSC 210 // PLSC 369 but not both. The TF for CPSC 310 is Samuel Judson (CPSC) [email protected], and the TF for CPSC 210 // PLSC 369 is John Ternovski (PLSC) [email protected]. The two courses will have common reading assignments. There will also be four written homework assignments, each worth 15% of the course grade, two due before mid-term break and two due after. In CPSC 310, the homework assignments will be problem sets, and, in CPSC 210 // PLSC 369, they will be short response papers based on the reading. -

David Donoho COMMENTARY 52 Cliff Ord J
ISSN 0002-9920 (print) ISSN 1088-9477 (online) of the American Mathematical Society January 2018 Volume 65, Number 1 JMM 2018 Lecture Sampler page 6 Taking Mathematics to Heart y e n r a page 19 h C th T Ru a Columbus Meeting l i t h i page 90 a W il lia m s r e lk a W ca G Eri u n n a r C a rl ss on l l a d n a R na Da J i ll C . P ip her s e v e N ré F And e d e r i c o A rd ila s n e k c i M . E d al Ron Notices of the American Mathematical Society January 2018 FEATURED 6684 19 26 29 JMM 2018 Lecture Taking Mathematics to Graduate Student Section Sampler Heart Interview with Sharon Arroyo Conducted by Melinda Lanius Talithia Williams, Gunnar Carlsson, Alfi o Quarteroni Jill C. Pipher, Federico Ardila, Ruth WHAT IS...an Acylindrical Group Action? Charney, Erica Walker, Dana Randall, by omas Koberda André Neves, and Ronald E. Mickens AMS Graduate Student Blog All of us, wherever we are, can celebrate together here in this issue of Notices the San Diego Joint Mathematics Meetings. Our lecture sampler includes for the first time the AMS-MAA-SIAM Hrabowski-Gates-Tapia-McBay Lecture, this year by Talithia Williams on the new PBS series NOVA Wonders. After the sampler, other articles describe modeling the heart, Dürer's unfolding problem (which remains open), gerrymandering after the fall Supreme Court decision, a story for Congress about how geometry has advanced MRI, “My Father André Weil” (2018 is the 20th anniversary of his death), and a profile on Donald Knuth and native script by former Notices Senior Writer and Deputy Editor Allyn Jackson. -

Chicago Journal of Theoretical Computer Science the MIT Press
Chicago Journal of Theoretical Computer Science The MIT Press Volume 1997, Article 2 3 June 1997 ISSN 1073–0486. MIT Press Journals, Five Cambridge Center, Cambridge, MA 02142-1493 USA; (617)253-2889; [email protected], [email protected]. Published one article at a time in LATEX source form on the Internet. Pag- ination varies from copy to copy. For more information and other articles see: http://www-mitpress.mit.edu/jrnls-catalog/chicago.html • http://www.cs.uchicago.edu/publications/cjtcs/ • ftp://mitpress.mit.edu/pub/CJTCS • ftp://cs.uchicago.edu/pub/publications/cjtcs • Kann et al. Hardness of Approximating Max k-Cut (Info) The Chicago Journal of Theoretical Computer Science is abstracted or in- R R R dexed in Research Alert, SciSearch, Current Contents /Engineering Com- R puting & Technology, and CompuMath Citation Index. c 1997 The Massachusetts Institute of Technology. Subscribers are licensed to use journal articles in a variety of ways, limited only as required to insure fair attribution to authors and the journal, and to prohibit use in a competing commercial product. See the journal’s World Wide Web site for further details. Address inquiries to the Subsidiary Rights Manager, MIT Press Journals; (617)253-2864; [email protected]. The Chicago Journal of Theoretical Computer Science is a peer-reviewed scholarly journal in theoretical computer science. The journal is committed to providing a forum for significant results on theoretical aspects of all topics in computer science. Editor in chief: Janos Simon Consulting