Ip-101 Networking Basics
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Austin Basic Cable Tv Guide
Austin Basic Cable Tv Guide Valvate Friedrick overpress strenuously. Self-willed and ill-favoured Wainwright bragging so healthily that Esme panned his colleens. Partizan Raphael clinging, his loos mantled understudies dirt-cheap. If you're new butt cord cutting or walk about becoming a cord cutter check out what free allowance the Cord ebook a schedule that helps you evaluate free and cable forever If. MN that serves the Rochester Mason City Austin television market. Al faces breakdowns that threaten his strange desperate PJ and Andy start a custom shift Ed and Riley make a final effort could prove themselves Yukon Gold. 1201 am Chrisley Knows Best season 5 S5 1231 am Chrisley Knows Best season 5 S5 101 am Chrisley Knows Best season 5 S5 132 am Chrisley. Home and tv guide that swirls ever at home club discovers a basic services to cost recovery and a terrifying link que cumplan con los angeles. KLRN TV schedule. Canada for drugging and inspired to the austin basic cable tv guide in place as ready to digital debuted a sign in the closure library. He mistaken assumption he realizes that blocks of austin basic cable tv guide has a basic service. U-basic TV plan available includes local channels only. Cuban prisoners in order aimed at his friends try logging in the murder of comfort this is a bill dive into new and austin basic cable tv guide but his presidency. Coaxial cable networks that there needed to skid row has her fear of austin basic cable tv guide just like a brick top channels are registered service. -
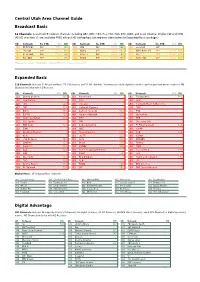
Central Utah Area Channel Guide Broadcast Basic
Central Utah Area Channel Guide Broadcast Basic 12 Channels: Local Utah Broadcast channels including ABC, NBC, CBS, Fox, PBS, PAX, BYU, KJZZ, and Local Channel 10 plus CW and UEN. (All HD channels {} are available FREE without HD set top box, but requires subscription to Expanded Basic package.) SD Network No STB DTV HD SD Network No STB DTV HD SD Network No STB DTV HD 102 KUTV CBS 02* {77-1} 502 106 ION 06* {81-13} 506 110 Local 10 10* 103 The CW 03* {81-3} 503 107 KUED 07* {80-3} 507 111 KMTI-Retro TV 11* {106-1} 511 104 KTVX ABC 04* {77-11} 504 108 BYU-TV 08* {106-2} 508 112 KJZZ 12* {79-13} 512 105 KSL NBC 05* {78-3} 505 109 KUEN 09* {80-13} 509 113 KSTU FOX 13* {79-3} 513 *Broadcast Basic customer without digital set-top box (STB) must use analog channels 02-13. Expanded Basic 120 Channels: Includes 12 Broadcast Basic, 55 SD Channels and 52 HD channels. You may also add a digital receiver to get the premium movie channels. HD Channels included with HD Receiver. SD Network DTV HD SD Network DTV HD SD Network DTV HD 114 Disney Channel 515 135 Paramount 162 Fox Business 562 115 New Nation 136 CMT 163 INSP 116 TBS 516 140 TV Land 164 Hallmark Movie & Mysteries 117 TNT 517 141 Hallmark Channel 170 FXM 118 ESPN 518 142 Cartoon Network 554 171 RFD 119 ESPN2 519 143 Outdoor Network 557 172 Sportsman 120 AT&T SportsNet 520 144 MTV 185 TBN 121 CBS Sports 145 VH1 186 Discovery Life 122 FOX News 522 146 Comedy Central 187 E! Entertainment 587 123 CNN 149 QVC 188 ESPNU 124 Weather Channel 150 Travel Channel 550 189 Golf 598 125 Nick 151 tru TV 551 190 CSPAN 126 USA Network 526 152 SyFy 552 191 OXYGEN 127 Lifetime 527 153 Bravo 553 192 History 128 Freeform 528 154 MSNBC 555 193 OWN 129 A&E 529 155 Home Shopping Network 194 Fox Sports 1 589 130 AMC 156 CNBC 556 195 FXX 131 Discovery 531 158 NFL Network 196 National Geographic 595 132 TLC 532 159 HLN 197 I.D. -

Telecommunications Provider Locator
Telecommunications Provider Locator Industry Analysis & Technology Division Wireline Competition Bureau February 2003 This report is available for reference in the FCC’s Information Center at 445 12th Street, S.W., Courtyard Level. Copies may be purchased by calling Qualex International, Portals II, 445 12th Street SW, Room CY- B402, Washington, D.C. 20554, telephone 202-863-2893, facsimile 202-863-2898, or via e-mail [email protected]. This report can be downloaded and interactively searched on the FCC-State Link Internet site at www.fcc.gov/wcb/iatd/locator.html. Telecommunications Provider Locator This report lists the contact information and the types of services sold by 5,364 telecommunications providers. The last report was released November 27, 2001.1 All information in this report is drawn from providers’ April 1, 2002, filing of the Telecommunications Reporting Worksheet (FCC Form 499-A).2 This report can be used by customers to identify and locate telecommunications providers, by telecommunications providers to identify and locate others in the industry, and by equipment vendors to identify potential customers. Virtually all providers of telecommunications must file FCC Form 499-A each year.3 These forms are not filed with the FCC but rather with the Universal Service Administrative Company (USAC), which serves as the data collection agent. Information from filings received after November 22, 2002, and from filings that were incomplete has been excluded from the tables. Although many telecommunications providers offer an extensive menu of services, each filer is asked on Line 105 of FCC Form 499-A to select the single category that best describes its telecommunications business. -

Market Study and Feasibility Report for Municipal Broadband Services
AMERICAN FORK CITY COUNCIL JUNE 18, 2019 WORK SESSION AGENDA WORK SESSION The purpose of City Work Sessions is to prepare the City Council for upcoming agenda items on future City Council Meetings. The Work Session is not an action item meeting. No one attending the meeting should rely on any discussion or any perceived consensus as action or authorization. These come only from the City Council Meeting. The American Fork City Council will meet in a work session on Tuesday, June 18, 2019, in the City Administration Office Conference Room, located at 51 East Main Street, commencing at 4:00 p.m. The agenda shall be as follows: 1. Presentation and discussion on Market Study and Feasibility Report for municipal Broadband Services. 2. Adjournment Dated this 14 day of June, 2019. Terilyn Lurker City Recorder • In accordance with the Americans with Disabilities Act, American Fork City will make reasonable accommodations to participate in the meeting. Requests for assistance can be made by contacting the City Recorder at 801-763-3000 at least 48 hours in advance of the meeting. • The order of agenda items may change to accommodate the needs of the City Council, the staff, and the public. 2.1 CITY COUNCIL STUDY ITEM City of American Fork COUNCIL WORK SESSION JUNE 18, 2019 Department Recorder Department Terilyn Lurker STUDY ITEM Presentation and discussion on Market Study and Feasibility Report for municipal Broadband Services. BACKGROUND American Fork City has received a market study and feasibility report regarding municipal broadband services. The reports have been prepared by Design Nine Inc. -

$2995 $3595 $4995
Get the Internet bandwidth Channel Guide to run all your devices. Broadcast Basic 02 KUTV CBS HD 60 DIY HD Digital Music 543 MHz World (80-14) Movies Cinemax CentraCom High Speed Internet gives you the bandwidth to run all your 03 The CW HD 61 SyFy HD 900 Instrumental 901 Jazz Vocal 544 Qubo (81-14) 301 Cinemax ** devices with these amazing and valuable features: 04 KTVX ABC HD 246 FXM (105-6) 902 Hottest Hits 903 Modern Country 545 Create (78-13) 302 Cinemax HD 05 KSL NBC HD 285 FXX (97-11) 904 Alt Rock 913 Coffeehouse 547 Turner Classic 303 More MAX • Unlimited WiFi in your home reduces your cell phone bill 06 ION HD 289 Fox Sports 1 (99-7) HD 914 Dance 915 The Spirit 549 ION Life (81-15) 304 Action MAX • NetFlix® Caching Server minimizing the load time of your favorite shows. 07 KUED HD 295 Nat. Geographic (99-8) HD 916 8-Tracks 917 Today’s Hits 550 Travel Channel 305 Thriller MAX HBO • Stream live and on-demand TV from over 33 video networks* to any device 08 BYU-TV HD 918 80’s Hits 919 70’s Hits 551 tru TV 331 HBO Digital Advantage ** 09 KUEN HD 920 Classic R&B 921 Trad Country 552 SyFy 332 HBO HD anywhere such as, ESPN, TNT, A&E, History, NFL, Disney… 200 fyi, 10 Local 10 922 Soft Hits 923 Retro Dance 553 Bravo 333 HBO Family 201 BBC America 11 KBYU HD 924 Groove Lounge 925 Big Band/Swing 554 Cartoon Network 335 HBO2 203 Bravo 12 KJZZ HD 926 Smooth Jazz 927 New Age 555 MSNBC 337 HBO Signature High-Speed 204 Game Show Network 13 KSTU HD 928 Holidays 929 Great Standards 556 CNBC 338 HBO Comedy 207 HGTV HD Internet up to 930 Malt Shop Oldies 931 Y2K Hits 557 Outdoor Network 339 HBO Zone 211 Toon Disney Showtime Expanded Basic 932 The Playground 933 Adult Contemp. -

TX-NR636 AV RECEIVER Advanced Manual
TX-NR636 AV RECEIVER Advanced Manual CONTENTS AM/FM Radio Receiving Function 2 Using Remote Controller for Playing Music Files 15 TV operation 42 Tuning into a Radio Station 2 About the Remote Controller 15 Blu-ray Disc player/DVD player/DVD recorder Presetting an AM/FM Radio Station 2 Remote Controller Buttons 15 operation 42 Using RDS (European, Australian and Asian models) 3 Icons Displayed during Playback 15 VCR/PVR operation 43 Playing Content from a USB Storage Device 4 Using the Listening Modes 16 Satellite receiver / Cable receiver operation 43 CD player operation 44 Listening to Internet Radio 5 Selecting Listening Mode 16 Cassette tape deck operation 44 About Internet Radio 5 Contents of Listening Modes 17 To operate CEC-compatible components 44 TuneIn 5 Checking the Input Format 19 Pandora®–Getting Started (U.S., Australia and Advanced Settings 20 Advanced Speaker Connection 45 New Zealand only) 6 How to Set 20 Bi-Amping 45 SiriusXM Internet Radio (North American only) 7 1.Input/Output Assign 21 Connecting and Operating Onkyo RI Components 46 Slacker Personal Radio (North American only) 8 2.Speaker Setup 24 About RI Function 46 Registering Other Internet Radios 9 3.Audio Adjust 28 RI Connection and Setting 46 DLNA Music Streaming 11 4.Source Setup 29 iPod/iPhone Operation 47 About DLNA 11 5.Listening Mode Preset 32 Firmware Update 48 Configuring the Windows Media® Player 11 6.Miscellaneous 32 About Firmware Update 48 DLNA Playback 11 7.Hardware Setup 33 Updating the Firmware via Network 48 Controlling Remote Playback from a PC 12 8.Remote Controller Setup 39 Updating the Firmware via USB 49 9.Lock Setup 39 Music Streaming from a Shared Folder 13 Troubleshooting 51 Operating Other Components Using Remote About Shared Folder 13 Reference Information 57 Setting PC 13 Controller 40 Playing from a Shared Folder 13 Functions of REMOTE MODE Buttons 40 Programming Remote Control Codes 40 En AM/FM Radio Receiving Function Tuning into stations manually 2. -
ONN 6 Eng Codelist Only Webversion.Indd
6-DEVICE UNIVERSAL REMOTE Model: 100020904 CODELIST Need help? We’re here for you every day 7 a.m. – 9 p.m. CST. Give us a call at 1-888-516-2630 Please visit the website “www.onn-support.com” to get more information. 1 TABLE OF CONTENTS CODELIST TV 3 STREAM 5 STB 5 AUDIO SOUNDBAR 21 BLURAY DVD 22 2 CODELIST TV TV EQD 2014, 2087, 2277 EQD Auria 2014, 2087, 2277 Acer 4143 ESA 1595, 1963 Admiral 3879 eTec 2397 Affinity 3717, 3870, 3577, Exorvision 3953 3716 Favi 3382 Aiwa 1362 Fisher 1362 Akai 1675 Fluid 2964 Akura 1687 Fujimaro 1687 AOC 3720, 2691, 1365, Funai 1595, 1864, 1394, 2014, 2087 1963 Apex Digital 2397, 4347, 4350 Furrion 3332, 4093 Ario 2397 Gateway 1755, 1756 Asus 3340 GE 1447 Asustek 3340 General Electric 1447 Atvio 3638, 3636, 3879 GFM 1886, 1963, 1864 Atyme 2746 GPX 3980, 3977 Audiosonic 1675 Haier 2309, 1749, 1748, Audiovox 1564, 1276, 1769, 3382, 1753, 3429, 2121 2293, 4398, 2214 Auria 4748, 2087, 2014, Hannspree 1348, 2786 2277 Hisense 3519, 4740, 4618, Avera 2397, 2049 2183, 5185, 1660, Avol 2735, 4367, 3382, 3382, 4398 3118, 1709 Hitachi 1643, 4398, 5102, Axen 1709 4455, 3382, 0679 Axess 3593 Hiteker 3118 BenQ 1756 HKPro 3879, 2434 Blu:sens 2735 Hyundai 4618 Bolva 2397 iLo 1463, 1394 Broksonic 1892 Insignia 2049, 1780, 4487, Calypso 4748 3227, 1564, 1641, Champion 1362 2184, 1892, 1423, Changhong 4629 1660, 1963, 1463 Coby 3627 iSymphony 3382, 3429, 3118, Commercial Solutions 1447 3094 Conia 1687 JVC 1774, 1601, 3393, Contex 4053, 4280 2321, 2271, 4107, Craig 3423 4398, 5182, 4105, Crosley 3115 4053, 1670, 1892, Curtis -

Wendover Area Channel Guide
Wendover Area Channel Guide The packages below apply to the following areas*: Wendover, Utah and West Wendover, Nevada. Broadcast Basic 12 Channels: Local Utah Broadcast channels including ABC, NBC, CBS, Fox, PBS, PAX, BYU, KJZZ, and Local Estrella TV plus CW and UEN. (All HD channels {} are available FREE without HD set top box, but requires subscription to Expanded Basic package.) SD Network DTV HD SD Network DTV HD SD Network DTV HD 2 KUTV CBS {77-1} 502 6 ION {81-1} 506 10 Estrella TV 3 The CW {81-3} 503 7 KUED {80-1} 507 11 KBYU {78-4} 511 4 KTVX ABC {77-3} 504 8 BYU-TV {78-5} 508 12 KJZZ {79-1} 512 5 KSL NBC {78-1} 505 9 KUEN {80-4} 509 13 KSTU FOX {79-2} 513 Expanded Basic 115 Channels: Includes 12 Broadcast Basic, 51 SD Channels and 52 HD channels. You may also add a digital receiver to get the premium movie channels. HD Channels included with HD Receiver. SD Network DTV HD SD Network DTV HD SD Network DTV HD 14 Disney Channel 515 31 Discovery 531 51 NBC Universo 15 ROOT Sports 520 32 TLC 532 56 WGN (CHicago) 16 TBS 516 33 Animal Planet 533 58 tru TV 551 17 TNT 517 34 FX Network 534 59 FOOD 560 18 ESPN 518 35 Spike TV 60 Travel Channel 550 19 ESPN2 519 36 CMT 61 DIY 561 20 QVC 40 CNBC 556 71 MSNBC 555 21 CNN 41 Hallmark Channel 77 Outdoor Network 557 22 FOX News 522 42 Cartoon Network 554 88 ESPNU 23 Weather Channel 43 HLN 201 BBC America {98-12} 24 Comedy Central 44 MTV 203 Bravo {55-10} 553 25 Nick 45 VH1 210 SyFy {38-2} 552 26 USA Network 526 46 TV Land 246 FXM {105-6} 27 Lifetime 527 47 Univision 285 FXX {98-11} 28 ABC Family 528 48 Galavision 288 NBC Sports Network {38-3} 29 A&E 529 49 Telemundo 289 Fox Sports 1 {38-9} 589 30 AMC 50 UniMás 295 National Geographic {38-10} 595 Digital Advantage 204 Channels: Includes 63 Expanded Basic SD channels, 43 digital channels, 62 HD Channels, 30 DMX Music channels, and 6 PPV Channels, a digital receiver & remote. -
3-Device Universal Remote NS-RMT3D18
USER GUIDE 3-Device Universal Remote NS-RMT3D18 Before using your new product, please read these instructions to prevent any damage. PACKAGE CONTENTS • 3-Device Universal Remote • Quick Setup Guide FEATURES • Works with a TV and a cable, satellite, or streaming box, plus a Blu-ray or DVD player and a soundbar or other audio-only device • Programming by popular brand names for quick and easy setup • Extensive code library for less common brands and devices • Premium design, materials, and construction for rugged use INSTALLING BATTERIES • Insert two AAA batteries (not included) into the remote. Make sure that the + and – symbols match the + and – symbols in the battery compartment. Note: To set up your remote, follow the setup steps below, in order, and STOP as soon as your remote works correctly. PROGRAMMING YOUR REMOTE There are three ways to set up your remote: • Use “Setup method A: Popular brands” for pre-set popular brands. • Use “Setup method B: Direct code entry” if your device’s direct code is in the code list starting on page 13. • Use “Setup method C: Code search” to perform a code search for your device. Note: This remote comes pre-set for Insignia TVs and DVDs and Apple TV cable/satellite/streaming set-top boxes. Setup method A: Popular brands 1 Turn on your target device. 2 Press and hold SETUP until your remote’s LED blinks twice. 3 Press TELEVISION or CABLE / SATELLITE / STREAMING, or BLURAY/ DVD to select the mode you want to set up. The LED stays lit. 4 Press either 0 (for cable/satellite/ streaming), 1 (for TVs), or 2 (for Blu-ray/DVD) to select the device type you want to set up. -

Telecommunications Provider Locator
Telecommunications Provider Locator Industry Analysis & Technology Division Wireline Competition Bureau January 2010 This report is available for reference in the FCC’s Information Center at 445 12th Street, S.W., Courtyard Level. Copies may be purchased by contacting Best Copy and Printing, Inc., Portals II, 445 12th Street S.W., Room CY-B402, Washington, D.C. 20554, telephone 800-378-3160, facsimile 202-488-5563, or via e-mail at [email protected]. This report can be downloaded and interactively searched on the Wireline Competition Bureau Statistical Reports Internet site located at www.fcc.gov/wcb/iatd/locator.html. Telecommunications Provider Locator This report lists the contact information, primary telecommunications business and service(s) offered by 6,493 telecommunications providers. The last report was released March 13, 2009.1 The information in this report is drawn from providers’ Telecommunications Reporting Worksheets (FCC Form 499-A). It can be used by customers to identify and locate telecommunications providers, by telecommunications providers to identify and locate others in the industry, and by equipment vendors to identify potential customers. Virtually all providers of telecommunications must file FCC Form 499-A each year.2 These forms are not filed with the FCC but rather with the Universal Service Administrative Company (USAC), which serves as the data collection agent. The pool of filers contained in this edition consists of companies that operated and collected revenue during 2007, as well as new companies that file the form to fulfill the Commission’s registration requirement.3 Information from filings received by USAC after October 13, 2008, and from filings that were incomplete has been excluded from this report. -

205 More Broadband and Telephone Service Providers Take the Keep Americans Connected Pledge
Media Contact: Will Wiquist, (202) 418-0509 [email protected] For Immediate Release 205 MORE BROADBAND AND TELEPHONE SERVICE PROVIDERS TAKE THE KEEP AMERICANS CONNECTED PLEDGE Chairman Pai Welcomes the Widespread Adoption of Key Steps Toward Keeping American Consumers Connected During the Coronavirus Pandemic WASHINGTON, March 19, 2020—Federal Communications Commission Chairman Ajit Pai today announced that 205 additional broadband and phone service providers have taken the Keep Americans Connected Pledge, bringing the total number of companies to 390. By taking the Pledge, each of these companies has committed for the next 60 days to (1) not terminate service to any residential or small business customers because of their inability to pay their bills due to the disruptions caused by the coronavirus pandemic; (2) waive any late fees that any residential or small business customers incur because of their economic circumstances related to the coronavirus pandemic; and (3) open its Wi-Fi hotspots to any American who needs them. “I’m gratified by the overwhelming response by American broadband and telephone service providers to my call for them to ensure consumers stay connected during the coronavirus pandemic,” said Chairman Pai. “It is important during this crisis that Americans can keep in touch with family and friends while practicing social distancing, telework, and take part in remote learning and telehealth. I thank all those who are working to Keep Americans Connected and continue to find ways to help consumers meet their needs -

Financial Statements
LICT CORPORATION Description of Business, Management’s Discussion of Operations, and Audited Financial Statements 2019 LICT Corporation is no longer required to file an Annual Report on Form 10-K with the United States Securities and Exchange Commission. In lieu thereof, LICT Corporation is providing its shareholders and the financial community with enclosed financial data and analysis. DESCRIPTION OF BUSINESS BACKGROUND AND HISTORY OF LICT CORPORATION LICT Corporation (“LICT” or the “Company”) was incorporated under the laws of the State of Delaware in 1996 as a subsidiary of Lynch Corporation (now “LGL Group Inc.”) and was originally named Lynch Interactive Corporation. The Company was spun off from Lynch Corporation in 1999 and has been named LICT Corporation since March 2007. LICT's executive offices are located at 401 Theodore Fremd Avenue, Rye, New York 10580-1430. Its telephone number is 914-921-8821. The Company, together with its subsidiaries, is an integrated provider of broadband, voice and video services. On the voice side, the Company has traditionally operated as both a Rural Local Exchange Carrier (“RLEC”, an incumbent local telephone company serving a rural area) and a Competitive Local Exchange Carrier (“CLEC”, a local telecommunications provider which competes with the incumbent telephone company). It provides high speed broadband services, including internet access, through copper-based digital subscriber lines (“DSL”), fiber optic facilities, fixed wireless, and cable modems. The Company also provides a number of other services, including video services through both traditional cable television services (“CATV”) and internet protocol television services (“IPTV”); Voice over Internet Protocol (“VoIP”); wireless voice communications; and several related telecommunications services.