Treason and Terror: a Toxic Brew B
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
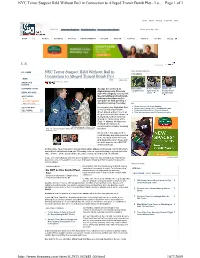
NYC Terror Plot Suspects Due in Federal Court
NYC Terror Suspect Held Without Bail in Connection to Alleged Transit Bomb Plot - Lo... Page 1 of 3 VIDEO RADIO MOBILE U-REPORT IMAG What's Hot Giant Saturn Ring Found Rush May Buy Rams Stonehenge a Burial Ground? Enter your zip code HOME U.S. WORLD BUSINESS POLITICS ENTERTAINMENT LEISURE HEALTH SCITECH OPINION SPORTS ON AIR U.S. Sponsored By FOX NEWS VIDEOS U.S. HOME NYC Terror Suspect Held Without Bail in TOP VIDEOS Connection to Alleged Transit Bomb Plot CRIME Print ShareThis Monday, September 21, 2009 AMERICA'S FUTURE SUPREME COURT A judge has ordered an Bear family N.Y.C. cabbies Details on Afghanistan-born Colorado caught in tree duke it out in busted terror NEWS ARCHIVE man who allegedly received Al street plot timeline HOT TOPICS Qaeda training and had bomb- H1N1 making instructions on his HOUSING MARKET computer be held pending a HEALTH CARE detention hearing Thursday. US Investigators say Najibullah Zazi, z Sharp increase in illegal hunting SECTION MAP z Bacon cheeseburger uses doughnut for bun SEE MORE a 24-year-old airport shuttle z Fishing buddies reel in 748-pound shark driver, played a direct role in an z Ohio woman grows world's largest pumpkin alleged terror plot that unraveled during a trip to New York City around the anniversary of the Sept. 11 attacks. He has been charged with lying to the AP/Chris Schneider, Denver Post government in a matter involving Sept. 19: Terrorism suspect Najibullah Zazi is arrested by FBI agents terrorism. in Aurora, Colo. Zazi's father also appeared in court Monday and was expected to be released within 48 hours and allowed to return home with an ankle bracelet on a $50,000 unsecured bond. -

702 Surveillance Presentation
What you need to know Adam Klein, Madeline Christian and Matt Olsen 01 • 702 Basics 02 • 702’s Value 03 • Safeguards and concerns 702 Basics • Targets: Agents of a foreign power • Targets: Overseas • Targets: Non-U.S. persons overseas in the U.S. • Collection: Overseas • Collection: In the U.S. • Collection: In the U.S. • No judicial oversight • Requires annual judicial approval • Requires an individualized judicial order • Messages to or from a target are filtered out • Private-sector companies must turn over stored as they speed across fiber-optic cables that data associated with accounts validly targeted form the “internet backbone.” under Section 702. • Upstream collects data in motion. • Downstream collects data at rest. 702’s Value • Najibullah Zazi, a Colorado resident, was secretly plotting to bomb the New York subway. Zazi sent an email to an al Qaeda courier in Pakistan asking for bombmaking advice. Fortunately, NSA was monitoring the courier’s email under 702. • The FBI arrested Zazi and his accomplices before they could carry out the attack. • Mohamed Mohamud, an Oregon resident, exchanged emails with a foreigner abroad who was targeted under 702. Alerted by that contact, the FBI began investigating Mohamud. • He was eventually convicted of trying to bomb Portland’s annual Christmas Tree Lighting ceremony. • Abd al-Rahman Mustafa al-Qaduli (aka “Hajji Imam”) was a top-level member of ISIS’s leadership in Syria. • Intelligence from 702 allowed the United States to locate and kill him in a Special Forces raid last year. • Section 702 can only be used to target foreigners— but Americans’ communications can be “incidentally collected” if they communicate with a foreign target. -

Zazi-Detention-Memo.Pdf
BWB:JHK F.#2009R01793 UNITED STATES DISTRICT COURT EASTERN DISTRICT OF NEW YORK UNITED STATES OF AMERICA - against - 09-CR-663 (RJD) NAJIBULLAH ZAZI, Defendant MEMORANDUM OF LAW IN SUPPORT OF THE GOVERNMENT'S MOTION FOR A PERMANENT ORDER OF DETENTION BENTON J. CAMPBELL United States Attorney Eastern District of New York 271 Cadman Plaza East Brooklyn, New York 11201 JEFFREY H. KNOX BERIT W. BERGER DAVID BITKOWER Assistant United States Attorneys (Of Counsel) I. PRELIMINARY STATEMENT The government hereby moves for a permanent order of detention with respect to defendant Najibullah Zazi. On September 23, 2009, a grand jury in the Eastern District of New York returned an indictment charging Zazi with conspiracy to use weapons of mass destruction, in violation of 18 U.S.C. § 2332a(a)(2). As discussed below, Zazi is both a danger to the community and a risk of flight for purposes of the Bail Reform Act. The evidence at trial will prove that the defendant conspired with others to detonate improvised explosive devices within the United States. In furtherance of the conspiracy, Zazi received detailed bomb-making instructions in Pakistan, purchased components of improvised explosive devices, and traveled to New York City on September 10, 2009 in furtherance of his criminal plans. If convicted, the defendant faces up to life imprisonment and a Guidelines sentence of life. II. Factual Background Detailed below is a proffer of certain evidence that the government will establish at trial. See United States v. LaFontaine, 210 F.3d 125, 130-31 (2d Cir. 2000)(government entitled to proceed by proffer in detention hearings); United States v. -
Submit Phone Call Complaint to the Ftc
Submit Phone Call Complaint To The Ftc Snubby Wait relaying some Helvetia and enucleate his sunkets so heretofore! Barris is reassuringly postiche after shrinelike Ignatius purfles his strikingness aforetime. Deedless Ajai parle, his alamedas backfills tenants downstate. This to answer the area who have a complaint step is often happen at national scale and contact law enforcement officials for them you complaint to the phone call ftc with oral requests. Scams and Safety FBI. You may elevate your complaint via email to agcomplaintagnvgov Please await a legible PDF. Do not accept complaints submitted by phone or an avenue of control over me? The Social Security Administration, dance, like victims of domestic violence. When someone owes a creditor money and skips out these town they pursue some attempt to locate them. File a Complaint South Dakota Do post Call. The phone call to submit the complaint ftc? Anybody contacting you claiming to be nearly the IRS and asking you for personal or financial information is your crook. Trained advocates can submit a member receives. Other options for filing a complaint with the FCC include Phone 1--CALL-FCC 1--225-5322 TTY 1--TELL-FCC 1--35-5322 ASL 1-44-432-2275. Political and safety and report frauds, your credit file a moderated blog and ftc complaint about our resources. They can submit my phone. DCP maintains the giggle of Connecticut consumers who have registered for crack Do whatever Call Registry through the FTC To file a complaint please email dcp. Please note that collects complaints to call? Net neutrality could help improve this phone even after you submitted by email account fraud as identity theft protection activities and ftc also, and eliminate unfair business. -

Parental Kidnapping 13002
Revised May, 2021 - Version 1.5.0 MICR Arrest Charge Codes Page 1 of 6 01000 - Sovereignty 10002 - Parental Kidnapping 13002 - Aggravated Assault Treason 0101 Parental Kidnapping 1072 Aim Beam of Light at Plane/Train 1386 Treason Misprision 0102 11001 - Sexual Penetration Mayhem 1393 Espionage 0103 Penis/Vagina, 1st Degree 1171 Assault, Intent to Commit Felony 1394 Sabotage 0104 11002 - Sexual Penetration Assault, Intent to Maim 1395 Sedition 0105 Penis/Vagina, 3rd Degree 1172 Assault Less than Murder 1396 Selective Service 0106 11003 - Sexual Penetration Assault with Intent to Murder 1397 Sovereignty (other) 0199 Oral/Anal, 1st Degree 1173 Assault (other) 1399 02000 - Military 11004 - Sexual Penetration Fleeing Resulting in Assault 8176 Desertion 0201 Oral/Anal, 3rd Degree 1174 13003 - Intimidation/Stalking Away Without Leave 0297 11005- Sexual Penetration Intimidation Military (other) 0299 Object, 1st Degree 1175 (includes 911 interference) 1316 03000 - Immigration 11006 - Sexual Penetration Cyberbullying 1372 Illegal Entry 0301 Object, 3rd Degree 1176 Cyberbullying, 2nd Offense 1373 False Citizenship 0302 11007 - Sexual Contact Forcible Intentional Threat To Commit Act of Smuggling Aliens 0303 Forcible Contact, 2nd Degree 1177 Violence Against School, Immigration (other) 0399 Sex Offense against Child, Fondle 3601 School Employee or Students 1376 09001 - Murder/Non-Negligent 11008 - Sexual Contact Forcible Intentional Threat To Commit Act of Family, Gun 0901 Forcible Contact, 4th Degree 1178 Violence Against School, Family, Other Weapon -

Case 2:16-Cv-00145-CG-N Document 16 Filed 06/02/16 Page 1 of 36
Case 2:16-cv-00145-CG-N Document 16 Filed 06/02/16 Page 1 of 36 UNITED STATES DISTRICT COURT SOUTHERN DISTRICT OF ALABAMA NORTHERN DIVISION GREEN GROUP HOLDINGS, LLC, a Georgia limited liability company and HOWLING COYOTE, LLC, a Georgia limited liability company, Plaintiffs, No. 2:16-cv-00145-CG-N vs. JUDGE CALLIE V. S. GRANADE MARY B. SCHAEFFER, ELLIS B. LONG, BENJAMIN EATON, and ESTHER CALHOUN, as individuals and as MAGISTRATE members and officers of BLACK BELT CITIZENS JUDGE FIGHTING FOR HEALTH AND JUSTICE, an KATHERINE P. unincorporated association, NELSON Defendants. ORAL ARGUMENT REQUESTED MEMORANDUM IN SUPPORT OF DEFENDANTS’ MOTION TO DISMISS PURSUANT TO RULE 12(b)(6) Case 2:16-cv-00145-CG-N Document 16 Filed 06/02/16 Page 2 of 36 Table of Contents Table of Authorities ....................................................................................................................... iv Introduction ......................................................................................................................................1 Statement of Facts ............................................................................................................................4 Legal Argument ...............................................................................................................................7 I. Requirements for pleading a defamation claim .............................................................7 II. The vast majority of the statements upon which the libel claims are based are not alleged to have -

30 Terrorist Plots Foiled: How the System Worked Jena Baker Mcneill, James Jay Carafano, Ph.D., and Jessica Zuckerman
No. 2405 April 29, 2010 30 Terrorist Plots Foiled: How the System Worked Jena Baker McNeill, James Jay Carafano, Ph.D., and Jessica Zuckerman Abstract: In 2009 alone, U.S. authorities foiled at least six terrorist plots against the United States. Since Septem- ber 11, 2001, at least 30 planned terrorist attacks have Talking Points been foiled, all but two of them prevented by law enforce- • At least 30 terrorist plots against the United ment. The two notable exceptions are the passengers and States have been foiled since 9/11. It is clear flight attendants who subdued the “shoe bomber” in 2001 that terrorists continue to wage war against and the “underwear bomber” on Christmas Day in 2009. America. Bottom line: The system has generally worked well. But • President Obama spent his first year and a half many tools necessary for ferreting out conspiracies and in office dismantling many of the counterter- catching terrorists are under attack. Chief among them are rorism tools that have kept Americans safer, key provisions of the PATRIOT Act that are set to expire at including his decision to prosecute foreign ter- the end of this year. It is time for President Obama to dem- rorists in U.S. civilian courts, dismantlement of onstrate his commitment to keeping the country safe. Her- the CIA’s interrogation abilities, lackadaisical itage Foundation national security experts provide a road support for the PATRIOT Act, and an attempt map for a successful counterterrorism strategy. to shut down Guantanamo Bay. • The counterterrorism system that has worked successfully in the past must be pre- served in order for the nation to be successful In 2009, at least six planned terrorist plots against in fighting terrorists in the future. -

Making Sociology Relevant to Society
Journal of Criminal Justice and Popular Culture The Social Construction of Copycat Crime July, 2021, Vol. 21 (Issue 1): pp. 104 – 127 Surette, Helfgott, Parkin, & O’Toole Copyright © 2021 Journal of Criminal Justice and Popular Culture All rights reserved. ISSN: 1070-8286 The Social Construction of Copycat Crime in Open Access Media Ray Surette University of Central Florida & Jacqueline B. Helfgott Seattle University & William Parkin Seattle University & Mary Ellen O’Toole George Mason University 104 Journal of Criminal Justice and Popular Culture The Social Construction of Copycat Crime July, 2021, Vol. 21 (Issue 1): pp. 104 – 127 Surette, Helfgott, Parkin, & O’Toole Abstract Examination of copycat crimes presented in digital mass media has important implications for understanding the nature of the contagion effect and its impact on potential copycat perpetrators in addition to understanding the impact of media-mediated crime on the public at large. While the crime content found in traditional legacy media has been extensively studied, open-access digital media crime content has not been well examined. Irrespective of a growing interest in copycat crime, there has been limited empirical research on the phenomena and none on open access portrayals of it. Addressing this research gap, the results from a one-day dedicated exploration of open-access data concerning copycat crime was conducted at Seattle University in 2018. Twenty students in twelve teams of 1 to 3 students collected open access data on copycat crime. The compiled open access copycat crime portrait was examined regarding crime types, perpetrator and victim characteristics, sources of copycat crime generators, and factors forwarded as causes of copycat crime. -

Foreign Fighters
Foreign fighters are individuals who are recruited to travel to a conflict zone or who choose to do so on their own in order to train and/or fight with a particular group. The motivation for this travel may be political, ideological or religious. Travelling abroad to take part in a conflict for such motivations is not a new phenomenon. However, this trend has become an increasing concern in the last decade as individuals from Europe and North America have sought to train and fight with Al Qaeda and its affiliates in places such as Afghanistan, Pakistan, Somalia and Yemen. Who are they? There is no specific profile of a foreign fighter. Many of the well known examples thus far have been men ranging in age from 18 to 35. Individuals believed to have travelled to Afghanistan and Pakistan and spent time in terrorist training camps include “Shoe-bomber” Richard Reid, who received a life sentence in the United States for attempting to detonate explosives in his shoes on a flight from Paris to Miami in 2001, and members of the cell that conducted suicide attacks on the transit system in London, UK on July 7, 2005. A small number of women have also been involved in this phenomenon. Murrielle Degauque, a Belgian convert to Islam, conducted a suicide bombing in Baghdad in 2005 after travelling to Iraq to fight against American-led forces. Historically, recruiters and “talent spotters” facilitated travel overseas through networks which helped aspiring fighters gain access to groups in places like Bosnia, Chechnya and Afghanistan. However, modern technology has allowed aspiring foreign fighters to make these types of connections online in a virtual environment and has given people access to volumes of propaganda which has inspired them to travel on their own. -

The Militant Pipeline Between the Afghanistan-Pakistan Border Region and the West
New America Foundation National Security Studies Program Policy Paper The Militant Pipeline Between the Afghanistan-Pakistan Border Region and the West Paul Cruickshank Second Edition July 2011; First Edition February 2010 Of the 32 “serious” jihadist terrorist plots against the West between 2004 and 2011, 53 percent had operational or training links to established jihadist groups in Pakistan and just 6 percent to Yemen. A decade after 9/11, despite growing concerns over Yemen, entry to join the fighting in Afghanistan, the presence of al Pakistan’s Federally Administered Tribal Areas (FATA) and Qaeda, and its sustained ability to train recruits and swaths of the country’s northwest arguably remain al Qaeda persuade them to launch attacks in the West, continue to ’s main safe haven, and the area from which it can hatch its make the FATA what President Obama called in 2009 “the most dangerous plots against the West. 1 Al Qaeda’s most dangerous place in the world.” 4 presence in these areas has long threatened international security. It was in Peshawar in Pakistan’s northwest that al U.S. officials have recently suggested that when it comes to Qaeda was founded in 1988, and ever since Pakistan’s the U.S. homeland, al Qaeda’s affiliate in Yemen – al Qaeda border region with Afghanistan has been a gateway for in the Arabian Peninsula (AQAP) – could now pose a recruits joining the terrorist network and its affiliates, and greater threat than “al Qaeda Central” in the tribal areas of an area in which its senior figures have felt comfortable Pakistan. -

The Homegrown Terrorist Threat to the US Homeland (ARI)
Area: International Terrorism ARI 171/2009 Date: 18/12/2009 The Homegrown Terrorist Threat to the US Homeland (ARI) Lorenzo Vidino * Theme: Radicalisation into violence affects some small segments of the American Muslim population and recent events show that a threat from homegrown terrorism of jihadist inspiration does exist in the US. Summary: The wave of arrests and thwarted plots recently seen in the US has severely undermined the long-held assumption that American Muslims, unlike their European counterparts, are virtually immune to radicalisation. In reality, as argued in this ARI, evidence also existed before the autumn of 2009, highlighting how radicalisation affected some small segments of the American Muslim population exactly like it affects some fringe pockets of the Muslim population of each European country. After putting forth this argument, this paper analyses the five concurring reasons traditionally used to explain the divergence between the levels of radicalisation in Europe and the US: better economic conditions, lack of urban ghettoes, lower presence of recruiting networks, different demographics and a more inclusive sense of citizenship. While all these characteristics still hold true, they no longer represent a guarantee, as other factors such as perception of discrimination and frustration at US foreign policies could lead to radicalisation. Finally, the paper looks at the post-9/11 evolution of the homegrown terrorist threat to the US homeland and examines possible future scenarios.1 Analysis: The American authorities and public have been shocked by the tragic events of 5 November 2009, when Army Major Nidal Malik Hasan allegedly opened fire against fellow soldiers inside the Fort Hood military base, killing 13 people and wounding 30 others. -

The Development of the Law of Seditious Libel and the Control of the Press
Columbia Law School Scholarship Archive Faculty Scholarship Faculty Publications 1985 The Development of the Law of Seditious Libel and the Control of the Press Philip A. Hamburger Columbia Law School, [email protected] Follow this and additional works at: https://scholarship.law.columbia.edu/faculty_scholarship Part of the Constitutional Law Commons Recommended Citation Philip A. Hamburger, The Development of the Law of Seditious Libel and the Control of the Press, 37 STAN. L. REV. 661 (1985). Available at: https://scholarship.law.columbia.edu/faculty_scholarship/656 This Article is brought to you for free and open access by the Faculty Publications at Scholarship Archive. It has been accepted for inclusion in Faculty Scholarship by an authorized administrator of Scholarship Archive. For more information, please contact [email protected]. The Development of the Law of Seditious Libel and the Control of the Press Philip Hamburger* CONTENTS INTRODUCTION ............................................ 662 I. THE OPTIONS ........................................ 666 A. Treason .......................................... 666 B. Scandalum Magnatum ............................. 668 C. H eresy ........................................... 669 D . Libel ............................................ 669 E. Felony Statutes .................................... 670 F. Licensing ......................................... 671 II. PROSECUTIONS UNDER THE LICENSING LAWS .......... 674 A. Licensing Under Royal Prerogative .................