Algebras for Tree Algorithms
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

15-122: Principles of Imperative Computation, Fall 2010 Assignment 6: Trees and Secret Codes
15-122: Principles of Imperative Computation, Fall 2010 Assignment 6: Trees and Secret Codes Karl Naden (kbn@cs) Out: Tuesday, March 22, 2010 Due (Written): Tuesday, March 29, 2011 (before lecture) Due (Programming): Tuesday, March 29, 2011 (11:59 pm) 1 Written: (25 points) The written portion of this week’s homework will give you some practice reasoning about variants of binary search trees. You can either type up your solutions or write them neatly by hand, and you should submit your work in class on the due date just before lecture begins. Please remember to staple your written homework before submission. 1.1 Heaps and BSTs Exercise 1 (3 pts). Draw a tree that matches each of the following descriptions. a) Draw a heap that is not a BST. b) Draw a BST that is not a heap. c) Draw a non-empty BST that is also a heap. 1.2 Binary Search Trees Refer to the binary search tree code posted on the course website for Lecture 17 if you need to remind yourself how BSTs work. Exercise 2 (4 pts). The height of a binary search tree (or any binary tree for that matter) is the number of levels it has. (An empty binary tree has height 0.) (a) Write a function bst height that returns the height of a binary search tree. You will need a wrapper function with the following specification: 1 int bst_height(bst B); This function should not be recursive, but it will require a helper function that will be recursive. See the BST code for examples of wrapper functions and recursive helper functions. -

Algorithms Documentation Release 1.0.0
algorithms Documentation Release 1.0.0 Nic Young April 14, 2018 Contents 1 Usage 3 2 Features 5 3 Installation: 7 4 Tests: 9 5 Contributing: 11 6 Table of Contents: 13 6.1 Algorithms................................................ 13 Python Module Index 31 i ii algorithms Documentation, Release 1.0.0 Algorithms is a library of algorithms and data structures implemented in Python. The main purpose of this library is to be an educational tool. You probably shouldn’t use these in production, instead, opting for the optimized versions of these algorithms that can be found else where. You should totally check out the docs for implementation details, complexities and further info. Contents 1 algorithms Documentation, Release 1.0.0 2 Contents CHAPTER 1 Usage If you want to use the algorithms in your code it is as simple as: from algorithms.sorting import bubble_sort my_list= bubble_sort.sort(my_list) 3 algorithms Documentation, Release 1.0.0 4 Chapter 1. Usage CHAPTER 2 Features • Pseudo code, algorithm complexities and futher info with each algorithm. • Test coverage for each algorithm and data structure. • Super sweet documentation. 5 algorithms Documentation, Release 1.0.0 6 Chapter 2. Features CHAPTER 3 Installation: Installation is as easy as: $ pip install algorithms 7 algorithms Documentation, Release 1.0.0 8 Chapter 3. Installation: CHAPTER 4 Tests: Pytest is used as the main test runner and all Unit Tests can be run with: $ ./run_tests.py 9 algorithms Documentation, Release 1.0.0 10 Chapter 4. Tests: CHAPTER 5 Contributing: Contributions are always welcome. Check out the contributing guidelines to get started. -

Initial Algebra Semantics in Matching Logic
Technical Report: Initial Algebra Semantics in Matching Logic Xiaohong Chen1, Dorel Lucanu2, and Grigore Ro¸su1 1University of Illinois at Urbana-Champaign, Champaign, USA 2Alexandru Ioan Cuza University, Ia¸si,Romania xc3@illinois, [email protected], [email protected] July 24, 2020 Abstract Matching logic is a unifying foundational logic for defining formal programming language semantics, which adopts a minimalist design with few primitive constructs that are enough to express all properties within a variety of logical systems, including FOL, separation logic, (dependent) type systems, modal µ-logic, and more. In this paper, we consider initial algebra semantics and show how to capture it by matching logic specifications. Formally, given an algebraic specification E that defines a set of sorts (of data) and a set of operations whose behaviors are defined by a set of equational axioms, we define a corresponding matching logic specification, denoted INITIALALGEBRA(E), whose models are exactly the initial algebras of E. Thus, we reduce initial E-algebra semantics to the matching logic specifications INITIALALGEBRA(E), and reduce extrinsic initial E-algebra reasoning, which includes inductive reasoning, to generic, intrinsic matching logic reasoning. 1 Introduction Initial algebra semantics is a main approach to formal programming language semantics based on algebraic specifications and their initial models. It originated in the 1970s, when algebraic techniques started to be applied to specify basic data types such as lists, trees, stacks, etc. The original paper on initial algebra semantics [Goguen et al., 1977] reviewed various existing algebraic specification techniques and showed that they were all initial models, making the concept of initiality explicit for the first time in formal language semantics. -

MONADS and ALGEBRAS I I
\chap10" 2009/6/1 i i page 223 i i 10 MONADSANDALGEBRAS In the foregoing chapter, the adjoint functor theorem was seen to imply that the category of algebras for an equational theory T always has a \free T -algebra" functor, left adjoint to the forgetful functor into Sets. This adjunction describes the notion of a T -algebra in a way that is independent of the specific syntactic description given by the theory T , the operations and equations of which are rather like a particular presentation of that notion. In a certain sense that we are about to make precise, it turns out that every adjunction describes, in a \syntax invariant" way, a notion of an \algebra" for an abstract \equational theory." Toward this end, we begin with yet a third characterization of adjunctions. This one has the virtue of being entirely equational. 10.1 The triangle identities Suppose we are given an adjunction, - F : C D : U: with unit and counit, η : 1C ! UF : FU ! 1D: We can take any f : FC ! D to φ(f) = U(f) ◦ ηC : C ! UD; and for any g : C ! UD we have −1 φ (g) = D ◦ F (g): FC ! D: This we know gives the isomorphism ∼ HomD(F C; D) =φ HomC(C; UD): Now put 1UD : UD ! UD in place of g : C ! UD in the foregoing. We −1 know that φ (1UD) = D, and so 1UD = φ(D) = U(D) ◦ ηUD: i i i i \chap10" 2009/6/1 i i page 224 224 MONADS AND ALGEBRAS i i And similarly, φ(1FC ) = ηC , so −1 1FC = φ (ηC ) = FC ◦ F (ηC ): Thus we have shown that the two diagrams below commute. -

On Coalgebras Over Algebras
On coalgebras over algebras Adriana Balan1 Alexander Kurz2 1University Politehnica of Bucharest, Romania 2University of Leicester, UK 10th International Workshop on Coalgebraic Methods in Computer Science A. Balan (UPB), A. Kurz (UL) On coalgebras over algebras CMCS 2010 1 / 31 Outline 1 Motivation 2 The final coalgebra of a continuous functor 3 Final coalgebra and lifting 4 Commuting pair of endofunctors and their fixed points A. Balan (UPB), A. Kurz (UL) On coalgebras over algebras CMCS 2010 2 / 31 Category with no extra structure Set: final coalgebra L is completion of initial algebra I [Barr 1993] Deficit: if H0 = 0, important cases not covered (as A × (−)n, D, Pκ+) Locally finitely presentable categories: Hom(B; L) completion of Hom(B; I ) for all finitely presentable objects B [Adamek 2003] Motivation Starting data: category C, endofunctor H : C −! C Among fixed points: final coalgebra, initial algebra Categories enriched over complete metric spaces: unique fixed point [Adamek, Reiterman 1994] Categories enriched over cpo: final coalgebra L coincides with initial algebra I [Plotkin, Smyth 1983] A. Balan (UPB), A. Kurz (UL) On coalgebras over algebras CMCS 2010 3 / 31 Locally finitely presentable categories: Hom(B; L) completion of Hom(B; I ) for all finitely presentable objects B [Adamek 2003] Motivation Starting data: category C, endofunctor H : C −! C Among fixed points: final coalgebra, initial algebra Categories enriched over complete metric spaces: unique fixed point [Adamek, Reiterman 1994] Categories enriched over cpo: final coalgebra L coincides with initial algebra I [Plotkin, Smyth 1983] Category with no extra structure Set: final coalgebra L is completion of initial algebra I [Barr 1993] Deficit: if H0 = 0, important cases not covered (as A × (−)n, D, Pκ+) A. -

A Note on the Under-Appreciated For-Loop
A Note on the Under-Appreciated For-Loop Jos´eN. Oliveira Techn. Report TR-HASLab:01:2020 Oct 2020 HASLab - High-Assurance Software Laboratory Universidade do Minho Campus de Gualtar – Braga – Portugal http://haslab.di.uminho.pt TR-HASLab:01:2020 A Note on the Under-Appreciated For-Loop by Jose´ N. Oliveira Abstract This short research report records some thoughts concerning a simple algebraic theory for for-loops arising from my teaching of the Algebra of Programming to 2nd year courses at the University of Minho. Interest in this so neglected recursion- algebraic combinator grew recently after reading Olivier Danvy’s paper on folding over the natural numbers. The report casts Danvy’s results as special cases of the powerful adjoint-catamorphism theorem of the Algebra of Programming. A Note on the Under-Appreciated For-Loop Jos´eN. Oliveira Oct 2020 Abstract This short research report records some thoughts concerning a sim- ple algebraic theory for for-loops arising from my teaching of the Al- gebra of Programming to 2nd year courses at the University of Minho. Interest in this so neglected recursion-algebraic combinator grew re- cently after reading Olivier Danvy’s paper on folding over the natural numbers. The report casts Danvy’s results as special cases of the pow- erful adjoint-catamorphism theorem of the Algebra of Programming. 1 Context I have been teaching Algebra of Programming to 2nd year courses at Minho Uni- versity since academic year 1998/99, starting just a few days after AFP’98 took place in Braga, where my department is located. -

Dualising Initial Algebras
Math. Struct. in Comp. Science (2003), vol. 13, pp. 349–370. c 2003 Cambridge University Press DOI: 10.1017/S0960129502003912 Printed in the United Kingdom Dualising initial algebras NEIL GHANI†,CHRISTOPHLUTH¨ ‡, FEDERICO DE MARCHI†¶ and J O H NPOWER§ †Department of Mathematics and Computer Science, University of Leicester ‡FB 3 – Mathematik und Informatik, Universitat¨ Bremen §Laboratory for Foundations of Computer Science, University of Edinburgh Received 30 August 2001; revised 18 March 2002 Whilst the relationship between initial algebras and monads is well understood, the relationship between final coalgebras and comonads is less well explored. This paper shows that the problem is more subtle than might appear at first glance: final coalgebras can form monads just as easily as comonads, and, dually, initial algebras form both monads and comonads. In developing these theories we strive to provide them with an associated notion of syntax. In the case of initial algebras and monads this corresponds to the standard notion of algebraic theories consisting of signatures and equations: models of such algebraic theories are precisely the algebras of the representing monad. We attempt to emulate this result for the coalgebraic case by first defining a notion of cosignature and coequation and then proving that the models of such coalgebraic presentations are precisely the coalgebras of the representing comonad. 1. Introduction While the theory of coalgebras for an endofunctor is well developed, less attention has been given to comonads.Wefeel this is a pity since the corresponding theory of monads on Set explains the key concepts of universal algebra such as signature, variables, terms, substitution, equations,and so on. -
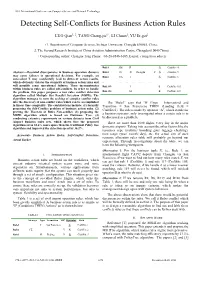
Detecting Self-Conflicts for Business Action Rules
2011 International Conference on Computer Science and Network Technology Detecting Self-Conflicts for Business Action Rules LUO Qian1, 2, TANG Chang-jie1+, LI Chuan1, YU Er-gai2 (1. Department of Computer Science, Sichuan University, Chengdu 610065, China; 2. The Second Research Institute of China Aviation Administration Centre, Chengdu 610041China) + Corresponding author: Changjie Tang Phone: +86-28-8546-6105, E-mail: [email protected] Rule4 FM D A CraftSite 4 Abstract—Essential discrepancies in business operation datasets Rule5 3U D Chengdu Y A CraftSite 5 may cause failures in operational decisions. For example, an Rule6 CA I A CraftSite 6 antecedent X may accidentally lead to different action results, which obviously violates the atomicity of business action rules and … … … … … … … will possibly cause operational failures. These inconsistencies Rule119 I B CraftSite 105 within business rules are called self-conflicts. In order to handle the problem, this paper proposes a fast rules conflict detection Rule120 M B CraftSite 229 algorithm called Multiple Slot Parallel Detection (MSPD). The algorithm manages to turn the seeking of complex conflict rules into the discovery of non-conflict rules which can be accomplished The “Rule1” says that “IF (Type = International and in linear time complexity. The contributions include: (1) formally Transition = San Francisco) THEN (Landing field = proposing the Self-Conflict problem of business action rules, (2) CraftSite1). The rule is made by operator “A", which stands for proving the Theorem of Rules Non-conflict, (3) proposing the MSPD algorithm which is based on Huffman- Tree, (4) a business operator, only investigated when a certain rule is to conducting extensive experiments on various datasets from Civil be discussed as a problem. -

Corecursive Algebras: a Study of General Structured Corecursion (Extended Abstract)
Corecursive Algebras: A Study of General Structured Corecursion (Extended Abstract) Venanzio Capretta1, Tarmo Uustalu2, and Varmo Vene3 1 Institute for Computer and Information Science, Radboud University Nijmegen 2 Institute of Cybernetics, Tallinn University of Technology 3 Department of Computer Science, University of Tartu Abstract. We study general structured corecursion, dualizing the work of Osius, Taylor, and others on general structured recursion. We call an algebra of a functor corecursive if it supports general structured corecur- sion: there is a unique map to it from any coalgebra of the same functor. The concept of antifounded algebra is a statement of the bisimulation principle. We show that it is independent from corecursiveness: Neither condition implies the other. Finally, we call an algebra focusing if its codomain can be reconstructed by iterating structural refinement. This is the strongest condition and implies all the others. 1 Introduction A line of research started by Osius and Taylor studies the categorical foundations of general structured recursion. A recursive coalgebra (RCA) is a coalgebra of a functor F with a unique coalgebra-to-algebra morphism to any F -algebra. In other words, it is an algebra guaranteeing unique solvability of any structured recursive diagram. The notion was introduced by Osius [Osi74] (it was also of interest to Eppendahl [Epp99]; we studied construction of recursive coalgebras from coalgebras known to be recursive with the help of distributive laws of functors over comonads [CUV06]). Taylor introduced the notion of wellfounded coalgebra (WFCA) and proved that, in a Set-like category, it is equivalent to RCA [Tay96a,Tay96b],[Tay99, Ch. -

A Presentation of the Initial Lift-Algebra'
JOURNAL OF PURE AND APPLIED ALGEBRA ELSBVlER Journal of pure and Applied Algebra 116 (1997) 185-198 A presentation of the initial lift-algebra’ Mamuka Jibladze Universiteit Utrecht, Vakgroep Wiskeinde, Postbus 80010, 3508 TA Utrecht, Netherlandr Received 5 February 1996; revised 23 July 1996 Abstract The object of study of the present paper may be considered as a model, in an elementary topos with a natural numbers object, of a non-classical variation of the Peano arithmetic. The new feature consists in admitting, in addition to the constant (zero) SOE N and the unary operation (the successor map) SI : N + N, arbitrary operations s,, : N” --f N of arities u ‘between 0 and 1’. That is, u is allowed to range over subsets of a singleton set. @ 1997 Elsevier Science B.V. 1991 Math. Subj. Class.: Primary 18B25, 03G30; Secondary 68Q55 In view of the Peano axioms, the set of natural numbers can be considered as a solution of the ‘equation’ X + 1 = X. Lawvere with his notion of natural numbers object (NNO) gave precise meaning to this statement: here X varies over objects of some category S, 1 is a terminal object of this category, and X + 1 (let us call it the decidable lift of X) denotes coproduct of X and 1 in S; this obviously defines an endofunctor of S. Now for any E : S + S whatsoever, one solves the ‘equation’ E(X) = X by considering E-algebras: an E-algebra structure on an object X is a morphism E(X) 4 X, and one can form the category of these by defining a morphism from E(X) ---fX to another algebra E(Y) + Y to be an X + Y making E(X) -E(Y) J 1 X-Y ’ Supported by ISF Grant MXH200, INTAS Grant # 93-2618, Fellows’ Research Fund of St John’s College and Leverhulme Fund of the Isaac Newton Institute, Cambridge, UK. -

AFP Assignments (Version: October 16, 2015)
AFP Assignments (version: October 16, 2015) Atze Dijkstra (and Andres Loh,¨ Doaitse Swierstra, and others) Summer - Fall 2015 Contents 1 Beginners exercises 9 1.1 Beginners training, brief (*) ..........................9 1.1.1 Hello, world! . .9 1.1.2 Interaction with the outside world . 10 1.1.3 The exercise . 12 1.2 Beginners training, extensive (*) ....................... 13 1.2.1 Getting started with GHCi . 13 1.2.2 Basic arithmetic . 14 1.2.3 Booleans . 15 1.2.4 Strings . 16 1.2.5 Types . 18 1.2.6 Lists . 19 1.2.7 Tuples . 22 1.2.8 Currying . 22 1.2.9 Overloading . 25 1.2.10 Numeric types and their classes . 26 1.2.11 Printing values . 28 1.2.12 Equality . 29 1.2.13 Enumeration . 30 1.2.14 Defining new functions . 31 1.2.15 Anonymous functions . 32 1.2.16 Higher-order functions . 34 1.2.17 Operator sections . 36 1.2.18 Loading modules . 37 2 Smaller per topic exercises 39 2.1 Tooling (*) .................................... 39 2.2 Programming . 39 2.3 Monads . 47 2.4 Programming jointly with types and values . 50 2.5 Programming with classes . 53 2.6 Type extensions . 56 2.7 Performance . 58 2.8 Observing: performance, testing, benchmarking . 59 2.9 Reasoning (inductive, equational) . 61 3 Contents 2.10 IO, Files, Unsafety, and the rest of the world (∗∗) ............. 62 2.10.1 IO Unsafety (1) . 62 2.10.2 Server . 63 2.10.3 IO Unsafety (2) . 63 2.11 Generic Programming (***) ......................... 64 2.12 Lists (*) ..................................... 64 2.13 Trees (*) .................................... -

A Directory Index for Ext2
A Directory Index for Ext2 Daniel Phillips Abstract has lacked to date. Without some form of directory indexing, there is a practical limit The native filesystem of Linux, Ext2, inherits of a few thousand files per directory before its basic structure from Unix systems that were quadratic performance characteristics become in widespread use at the time Linus Torvalds visible. To date, an applications such as a mail founded the Linux project more than ten years transfer agent that needs to manipulate large ago. Although Ext2 has been improved and numbers of files has had to resort to some strat- extended in many ways over the years, it still egy such as structuring the set of files as a shares an undesireable characteristic with those directory tree, where each directory contains early Unix filesystems: each directory opera- no more files than Ext2 can handle efficiently. tion (create, open or delete) requires a linear Needless to say, this is clumsy and inefficient. search of an entire directory file. This results in The design of a directory indexing scheme to a quadratically increasing cost of operating on be retrofitted onto a filesystem in widespread all the files of a directory, as the number of files production use presents some interesting and in the directory increases. The HTree direc- unique problems. First among these is the need tory indexing extension was designed and im- to maintain backward compatibility with exist- plemented by the author to address this issue, ing filesystems. If users are forced to recon- and has been shown in practice to perform very struct their partitions then much of the con- well.