Important: How to Use This List for Software Coding
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Africa Centre of Excellence on Technology Enhanced Learning (ACETEL)
CIT 215: INTRODUCTION TO PROGRAMMING LANGUAGE Africa Centre of Excellence on Technology Enhanced Learning (ACETEL) Course Guide 1 NATIONAL OPEN UNIVERSITY OF NIGERIA FACULTY OF SCIENCE COURSE CODE: CIT 215 COURSE TITLE: INTRODUCTION TO PROGRAMMING LANGUAGE 2 Introduction CIT 215 Introduction to Programming Languages is a three [3] credit unit course of twenty units. It deals with Introduction to Programming languages. Programming languages are not very different from spoken languages. Learning any language requires an understanding of the building blocks and the grammar that govern the construction of statements in that language. This book will serve as an introduction to programming languages, taking you through the history of programming languages. We will also learn about the various universal properties of all programming languages and identify distinct design features of each programming language. By the end of this book, you will have a deeper understanding of what a programming language is and the ability to recognize the properties of programming languages. You will also take overview of some programming languages such as to Basic, Fortran, Pascal, C++ , HTML and Visual Basic. Module 1 provides a foundation for the course. In this module we introduce the art of computer programming; explained computer programming languages, and introductory theory of algorithms. Also covered in the module are Flowcharting Techniques and structured programming Module 2: In this module, we provide introductions to the rudiments of BASIC and FORTRAN programming language. In this module we introduce BASIC Programming; explained more programming statements in BASIC, and introduce you to FORTRAN Language. Also covered in the module are FORTRAN Keywords and Library Functions. -

Graphicconverter 6.6
User’s Manual GraphicConverter 6.6 Programmed by Thorsten Lemke Manual by Hagen Henke Sales: Lemke Software GmbH PF 6034 D-31215 Peine Tel: +49-5171-72200 Fax:+49-5171-72201 E-mail: [email protected] In the PDF version of this manual, you can click the page numbers in the contents and index to jump to that particular page. © 2001-2009 Elbsand Publishers, Hagen Henke. All rights reserved. www.elbsand.de Sales: Lemke Software GmbH, PF 6034, D-31215 Peine www.lemkesoft.com This book including all parts is protected by copyright. It may not be reproduced in any form outside of copyright laws without permission from the author. This applies in parti- cular to photocopying, translation, copying onto microfilm and storage and processing on electronic systems. All due care was taken during the compilation of this book. However, errors cannot be completely ruled out. The author and distributors therefore accept no responsibility for any program or documentation errors or their consequences. This manual was written on a Mac using Adobe FrameMaker 6. Almost all software, hardware and other products or company names mentioned in this manual are registered trademarks and should be respected as such. The following list is not necessarily complete. Apple, the Apple logo, and Macintosh are trademarks of Apple Computer, Inc., registered in the United States and other countries. Mac and the Mac OS logo are trademarks of Apple Computer, Inc. Photo CD mark licensed from Kodak. Mercutio MDEF copyright Ramon M. Felciano 1992- 1998 Copyright for all pictures in manual and on cover: Hagen Henke except for page 95 exa- mple picture Tayfun Bayram and others from www.photocase.de; page 404 PCD example picture © AMUG Arizona Mac Users Group Inc. -

Verizon Wireless Mobile Office User Guides for Windowstm 95/98
Verizon Wireless Mobile Office User Guides For WindowsTM 95/98 To use Mobile Office for basic Internet access, do the following: Setting the Phone Up As a Modem 2 – 5 Setting Up a Mobile Office Quick 2 Netsm Connection 6 – 9 Using The Mobile Office Service 10 - 16 Related Support Documents: Setting Up Your Existing Dial Up Connections 17- 24 Setting Up AOL 4.0 / 5.0 (If you currently use AOL.) 25 - 32 Faxing With Your Digital Data Capable Phone 33 - 53 1 man.doc Setting the Phone Up as a Modem Step 1:(Optional) If you have a driver that was provided with your phone skip this step. If you do not have a driver you can use a standard driver included in Windows or we recommend using our driver. Download the Mobile Office Driver. Step 2: Go into control panel by clicking on Start, Settings, Control Panel Step 3: Select Modems Step 4: Click Add... 2 man.doc Step 5: Select "Other" then click Next. (If your PC does not support PC-Cards you will not get this screen.) Step 6: Check "Don't run the Hardware Installation wizard" if you get this dialog box. Then click on the Next button. Step 7: Check the box labeled "Don't detect my modem; I will select it from a list." Then click Next. 3 man.doc Step 8: If you have a driver provided by your phone manufacturer, click on the "Have Disk..." button. Insert your disk, click "OK" and then choose the model of phone that you have. -

BASIC Programming with Unix Introduction
LinuxFocus article number 277 http://linuxfocus.org BASIC programming with Unix by John Perr <johnperr(at)Linuxfocus.org> Abstract: About the author: Developing with Linux or another Unix system in BASIC ? Why not ? Linux user since 1994, he is Various free solutions allows us to use the BASIC language to develop one of the French editors of interpreted or compiled applications. LinuxFocus. _________________ _________________ _________________ Translated to English by: Georges Tarbouriech <gt(at)Linuxfocus.org> Introduction Even if it appeared later than other languages on the computing scene, BASIC quickly became widespread on many non Unix systems as a replacement for the scripting languages natively found on Unix. This is probably the main reason why this language is rarely used by Unix people. Unix had a more powerful scripting language from the first day on. Like other scripting languages, BASIC is mostly an interpreted one and uses a rather simple syntax, without data types, apart from a distinction between strings and numbers. Historically, the name of the language comes from its simplicity and from the fact it allows to easily teach programming to students. Unfortunately, the lack of standardization lead to many different versions mostly incompatible with each other. We can even say there are as many versions as interpreters what makes BASIC hardly portable. Despite these drawbacks and many others that the "true programmers" will remind us, BASIC stays an option to be taken into account to quickly develop small programs. This has been especially true for many years because of the Integrated Development Environment found in Windows versions allowing graphical interface design in a few mouse clicks. -
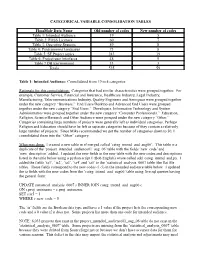
Categorical Variable Consolidation Tables
CATEGORICAL VARIABLE CONSOLIDATION TABLES FlossMole Data Name Old number of codes New number of codes Table 1: Intended Audience 19 5 Table 2: FOSS Licenses 60 7 Table 3: Operating Systems 59 8 Table 4: Programming languages 73 8 Table 5: SF Project topics 243 19 Table 6: Project user interfaces 48 9 Table 7 DB Environment 33 3 Totals 535 59 Table 1: Intended Audience: Consolidated from 19 to 4 categories Rationale for this consolidation: Categories that had similar characteristics were grouped together. For example, Customer Service, Financial and Insurance, Healthcare Industry, Legal Industry, Manufacturing, Telecommunications Industry, Quality Engineers and Aerospace were grouped together under the new category “Business.” End Users/Desktop and Advanced End Users were grouped together under the new category “End Users.” Developers, Information Technology and System Administrators were grouped together under the new category “Computer Professionals.” Education, Religion, Science/Research and Other Audience were grouped under the new category “Other.” Categories containing large numbers of projects were generally left as individual categories. Perhaps Religion and Education should have be left as separate categories because of they contain a relatively large number of projects. Since Mike recommended we get the number of categories down to 50, I consolidated them into the “Other” category. What was done: I created a new table in sf merged called ‘categ_intend_aud_aug06’. This table is a duplicate of the ‘project_intended_audience01_aug_06’ table with the fields ‘new_code’ and ‘new_description’ added. I updated the new fields in the new table with the new codes and descriptions listed in the table below using a python script I (Bob English) wrote called add_categ_intend_aud.py. -

Fax Sharing User's Guide
Fax Sharing User’s Guide February 2000 WinFax PRO Fax Sharing User’s Guide Copyright Notice © Symantec Corporation 2000 All rights reserved. The use and copying of this product is subject to a license agreement. Any other use is prohibited. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system or translated into any language in any form by any means without the prior written consent of Symantec Corporation. Information in this manual is subject to change without notice and does not represent a commitment on the part of the vendor. Federal copyright law permits you to make a backup of this software for archival purposes only. Any other duplication of this software, including copies offered through sale, loan, rental or gift is a violation of law, and subject to both criminal and civil penalties. Notice to WinFax PRO Users It shall be unlawful for any person within the United States to use any computer or other electronic device to send any message via a facsimile machine unless such message clearly contains, in a margin at the top or bottom of each transmitted page or on the first page of the transmission, the date and time it is sent and an identification of the business, other entity or individual sending the message and the telephone number of the sending machine or such business, other entity, or individual. Trademarks Symantec, the Symantec logo, TalkWorks PRO, Cover Your Voice, WinFax PRO, Cover Your Fax, and pcANYWHERE are trademarks of Symantec Corporation and its subsidiaries. AOL is a registered trademark of America Online, Inc. -

DLCC Software Catalog
Daniel's Legacy Computer Collections Software Catalog Category Platform Software Category Title Author Year Media Commercial Apple II Integrated Suite Claris AppleWorks 2.0 Claris Corporation and Apple Computer, Inc. 1987 800K Commercial Apple II Operating System Apple IIGS System 1.0.2 --> 1.1.1 Update Apple Computer, Inc. 1984 400K Commercial Apple II Operating System Apple IIGS System 1.1 Apple Computer, Inc. 1986 800K Commercial Apple II Operating System Apple IIGS System 2.0 Apple Computer, Inc. 1987 800K Commercial Apple II Operating System Apple IIGS System 3.1 Apple Computer, Inc. 1987 800K Commercial Apple II Operating System Apple IIGS System 3.2 Apple Computer, Inc. 1988 800K Commercial Apple II Operating System Apple IIGS System 4.0 Apple Computer, Inc. 1988 800K Commercial Apple II Operating System Apple IIGS System 5.0 Apple Computer, Inc. 1989 800K Commercial Apple II Operating System Apple IIGS System 5.0.2 Apple Computer, Inc. 1989 800K Commercial Apple II Reference: Programming ProDOS Basic Programming Examples Apple Computer, Inc. 1983 800K Commercial Apple II Utility: Printer ImageWriter Toolkit 1.5 Apple Computer, Inc. 1984 400K Commercial Apple II Utility: User ProDOS User's Disk Apple Computer, Inc. 1983 800K Total Apple II Titles: 12 Commercial Apple Lisa Emulator MacWorks 1.00 Apple Computer, Inc. 1984 400K Commercial Apple Lisa Office Suite Lisa 7/7 3.0 Apple Computer, Inc. 1984 400K Total Apple Lisa Titles: 2 Commercial Apple Mac OS 0-9 Audio Audioshop 1.03 Opcode Systems, Inc. 1992 800K Commercial Apple Mac OS 0-9 Audio Audioshop 2.0 Opcode Systems, Inc. -

(CRCS) Release 6.0 Installation
Conference Reservation and Control System (CRCS) Release 6.0 Installation 555-027-109 Comcode 108382085 Issue 1 April 1999 Copyright© 1999 Lucent Technologies Inc. Users outside of the US and Canada should contact their local All Rights Reserved authorized Lucent Technologies distributor if they want to order Printed in U.S.A. additional copies of this document. Also, users in these countries should send any comments on the document to their local authorized Lucent Technologies distributor. Notice Lucent Technologies Inc. Fraud Intervention While reasonable effort was made to ensure that the information If you suspect you are being victimized by toll fraud and you need in this document was complete and accurate at the time of technical support or assistance, call the BCS Technical Service printing, Lucent Technologies Inc. and its authorized agents Center Toll Fraud Intervention hotline at 800 643-2353. cannot assume responsibility for errors. Changes and/or corrections to the information contained in this document may be Comments incorporated in future issues. Names and addresses used for To comment on this document, complete and fax in the comment examples throughout this guide are fictitious. card at the end of the document. Your Responsibility for Your System’s Security Technical Support You are responsible for the security of your system. Lucent Call: Video Technical Center (VTC) Technologies Inc. does not warrant that this product is immune 800 242-2121 then follow the prompts for video from or will prevent unauthorized use of common-carrier conferencing telecommunications services or facilities accessed through or connected to it. Lucent Technologies Inc. -

Technical Specs Intellisoft Group Products Work Best When Installed on Platforms with the Following Specifications
Technical Specs IntelliSoft Group products work best when installed on platforms with the following specifications. It is critical to keep your platforms updated with Microsoft Windows® critical updates. IntelliSoft Group products can be deployed in Client/Server, Intranet/Web, or SaaS implementations. IntelliSoft Group Client/Server and Intranet/Web solution are installed within Customer networks. IntelliSoft Group SaaS solutions are hosted within IntelliSoft group's secure facilities and are continuously monitored and maintained. A full Disaster Recovery and Application Failover protocol is maintained at all times providing continuous Service Uptime. Client Recommended Minimum Requirements Processor Intel® Pentium® 4, 1.8GHz or above RAM 8GB or above Available Hard Disk 40GB or above Windows 7 Professional SP1, Windows 8 Professional, Operating System Windows 8.1 Professional, Windows 10 Professional Microsoft Office Microsoft Office 2003 SP3 32-bit, 2007 SP3 32-bit, 2010 Suite SP2 32-bit, 2013 32-bit IntelliSoft IntelliSoft PDF Writer (Included) Convenience Modules Office Control 4.0.1.0 for Microsoft Office (Included) Microsoft Fax 5.2 or Higher, Microsoft WinFax 10.03 or Faxing Software Higher2 Scanning Software Imaging Professional 2.8.2 (Included) Document Reader Adobe Acrobat Reader 8.0 or Higher Authentication/Single LDAP (Optional) Sign On IE 8, IE 9, IE 10 (In compatibility mode), IE 11 (In Browser compatibility mode) 7-Zip (included) licensed under the GNU LGPL license. File Zip Software For more info see www.7-zip.org. Practitioner -

DEALING with DATA EDITOR’S NOTE Does Your Program Smell Passive Authentication for ASP.NET with WIF Like Bacon? Michele Leroux Bustamante
THE MICROSOFT JOURNAL FOR DEVELOPERS AUGUST 2010 VOL 25 NO 8 COLUMNS DEALING WITH DATA EDITOR’S NOTE Does Your Program Smell Passive Authentication for ASP.NET with WIF Like Bacon? Michele Leroux Bustamante . 20 Keith Ward page 4 CUTTING EDGE Tips for Migrating Your Applications to the Cloud Don’t Worry, Be Lazy George Huey and Wade Wegner . 36 Dino Esposito page 6 Creating Synchronization Providers DATA POINTS Deny Table Access to the with the Sync Framework Entity Framework Without Joydip Kanjilal . 46 Causing a Mutiny Julie Lerman page 14 Building an AtomPub Server Using WCF Data Services TEST RUN Chris Sells . 54 Fault Injection Testing with TestApi James McCaffrey page 84 Tuning Your Database Calls THE WORKING PROGRAMMER with Tier Interaction Profi ling Inside SQLite Mark Friedman . 62 Ted Neward page 88 UI FRONTIERS Building Distributed Apps with NHibernate Multi-Touch Manipulation Events in WPF and Rhino Service Bus, Part 2 Charles Petzold page 92 Oren Eini . 72 DON’T GET ME STARTED Windows Phone and the Cloud: an Introduction Mars and Venus David Platt page 96 Ramon Arjona . 78 Untitled-5 2 3/5/10 10:16 AM Sure, Visual Studio 2010 has a lot of great functionality— we’re excited that it’s only making our User Interface components even better! We’re here to help you go beyond what Visual Studio 2010 gives you so you can create Killer Apps quickly, easily and without breaking a sweat! Go to infragistics.com/beyondthebox today to expand your toolbox with the fastest, best-performing and most powerful UI controls available. -

Historical Product Releases Sep-02 Enterprise Security Manager For
Historical Product Releases Sep-02 Enterprise Security Manager for Databases 3.0 Enterprise Security Manager for Firewall 2.0 Enterprise Security Manager for HIPAA 1.0 Symantec AntiVirus for SMTP Gateways 3.0 Symantec AntiVirus Gateway Solution 3.0 Symantec AntiVirus Enterprise Edition 8.5 Symantec Client Security Norton AntiVirus 2003 Norton AntiVirus Professional 2003 Norton Ghost 2003 Norton Internet Security 2003 Norton Personal Firewall 2003 Norton SystemWorks 2003 Norton SystemWorks Professional 2003 Jun-02 Symantec Web Security 2.5 Syamantec Gateway Security (models 5100, 5200, 5300) VelociRaptor 1.5 (models 1100, 1200, 1300) Net Prowler 3.5.1 Symantec AntiVirus Gateway Solution Symantec AntiVirus Scan Engine 3.0 Symantec AntiVirus for Inktomi Traffic Edge 3.0 Symantec AntiVirus for Network Appliances filer/NetCache 3.0 Norton AntiVirus for Lotus Notes/Domino on Linux Mar-02 Symantec Gateway Security RK4 ESM - Best Practice Policies Firewall 1.0 ESM - Best Practice Policies Oracle Database 2.0 ESM - Best Practice Policies WebServer 2.0 Symantec ESM Unix Console for Solaris Symantec Enterprise Firewall/VPN 7.0 for Win/Solaris Symantec AntiVirus/Filtering for Domino W2N 3.0 Norton AntiVirus Corporate Edition 7.6 + Microsoft Exchange 3.0 pcAnywhere Personal Edition Norton AntiVirus Mac 8.0 Norton Internet Security Mac 2.0 Norton Personal Firewall Mac 2.0 Norton Systems Work Mac 2.0 Norton Utilities Mac 7.0 Dec-01 Enterprise Security Manager 5.5 Symantec AV/Filtering for MSE 3.0 Symantec AntiVirus Command Line Scanner 1.0 Symantec Firewall -

Guía De Presentación De Scripts De CA Desktop Migration Manager
CA Desktop Migration Manager Guía de presentación de scripts Versión 12.8 Esta documentación, que incluye sistemas incrustados de ayuda y materiales distribuidos por medios electrónicos (en adelante, referidos como la "Documentación") se proporciona con el único propósito de informar al usuario final, pudiendo CA proceder a su modificación o retirada en cualquier momento. Queda prohibida la copia, transferencia, reproducción, divulgación, modificación o duplicado de la totalidad o parte de esta Documentación sin el consentimiento previo y por escrito de CA. Esta Documentación es información confidencial, propiedad de CA, y no puede ser divulgada por Vd. ni puede ser utilizada para ningún otro propósito distinto, a menos que haya sido autorizado en virtud de (i) un acuerdo suscrito aparte entre Vd. y CA que rija su uso del software de CA al que se refiere la Documentación; o (ii) un acuerdo de confidencialidad suscrito aparte entre Vd. y CA. No obstante lo anterior, si dispone de licencias de los productos informáticos a los que se hace referencia en la Documentación, Vd. puede imprimir, o procurar de alguna otra forma, un número razonable de copias de la Documentación, que serán exclusivamente para uso interno de Vd. y de sus empleados, y cuyo uso deberá guardar relación con dichos productos. En cualquier caso, en dichas copias deberán figurar los avisos e inscripciones relativas a los derechos de autor de CA. Este derecho a realizar copias de la Documentación sólo tendrá validez durante el período en que la licencia aplicable para el software en cuestión esté en vigor. En caso de terminarse la licencia por cualquier razón, Vd.