Quadrature Amplitude Modulation: from Basics to Adaptive Trellis-Coded, Turbo-Equalised and Space-Time Coded OFDM, CDMA and MC-CDMA Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Optical Single Sideband for Broadband and Subcarrier Systems
University of Alberta Optical Single Sideband for Broadband And Subcarrier Systems Robert James Davies 0 A thesis submitted to the faculty of Graduate Studies and Research in partial fulfillrnent of the requirernents for the degree of Doctor of Philosophy Department of Electrical And Computer Engineering Edmonton, AIberta Spring 1999 National Library Bibliothèque nationale du Canada Acquisitions and Acquisitions et Bibliographie Services services bibliographiques 395 Wellington Street 395, rue Wellington Ottawa ON KlA ON4 Ottawa ON KIA ON4 Canada Canada Yom iUe Votre relérence Our iSie Norre reference The author has granted a non- L'auteur a accordé une licence non exclusive licence allowing the exclusive permettant à la National Library of Canada to Bibliothèque nationale du Canada de reproduce, loan, distribute or sell reproduire, prêter, distribuer ou copies of this thesis in microform, vendre des copies de cette thèse sous paper or electronic formats. la forme de microfiche/nlm, de reproduction sur papier ou sur format électronique. The author retains ownership of the L'auteur conserve la propriété du copyright in this thesis. Neither the droit d'auteur qui protège cette thèse. thesis nor substantial extracts fkom it Ni la thèse ni des extraits substantiels may be printed or otheMrise de celle-ci ne doivent être Unprimés reproduced without the author's ou autrement reproduits sans son permission. autorisation. Abstract Radio systems are being deployed for broadband residential telecommunication services such as broadcast, wideband lntemet and video on demand. Justification for radio delivery centers on mitigation of problems inherent in subscriber loop upgrades such as Fiber to the Home (WH)and Hybrid Fiber Coax (HFC). -

Development of an SNMP Managing Application for Adaptation of Coding & Modulation on DVB-S Satellite Modems Is Structured As Follows
Development of an SNMP Managing Application for Adaptation of Coding & Modulation on DVB-S Satellite Modems by Dipl.-Ing. Dr.techn. Gerhard VRISK Submitted in a partial fulfilment of the requirements for the degree of Master of Sciences of the Post-graduate University Course Space Sciences (Main Track: Space Communication and Navigation ) Karl-Franzens University of Graz Graz, Austria 2009 Acknowledgments / Danksagung This master thesis has been written at the IKS ( Institute of Communication Networks and Satellite Communications / Institut für Kommunikationsnetze und Satellitenkommunikation ) at Graz University of Technology in the years 2009. First, I would like to thank my thesis advisor, Univ.-Prof. Dipl.-Ing. Dr. Otto Koudelka, Chair of the IKS, who offered me to work on this subject. Furthermore, I would like to thank (em.)Univ.-Prof. DDr. Willibald Riedler, retired Director of the former Institute of Communications and Wave Propagation at the Technical University of Graz and retired Director of the Space Research Institute of the Austrian Academy of Sciences, for his complaisant attendance to act as 2nd reviewer of this master thesis. Last but not least I would like to thank Univ.-Prof. Dr. Helmut Rucker, Research Director at the Space Research Institute of the Austrian Academy of Sciences, especially for his support during the course and generally for organization and managing the 4th MSc University Course Space Sciences . A big kiss goes to my wife Gerlinde for her support und patience during my studies and for the photographs, too. Am Schluss möchte ich mich noch bei meinen Eltern bedanken, für all die Förderung von früh an und für ihre Unterstützung während meinen Studienzeiten. -

Application of Noise Mapping in an Indian Opencast Mine for Effective Noise Management
12th ICBEN Congress on Noise as a Public Health Problem Application of noise mapping in an Indian opencast mine for effective noise management Veena Manwar1, Bibhuti Bhusan Mandal2, Asim Kumar Pal3 1 National Institute of Miners’ Health, Department of Occupational Hygiene, Nagpur, India (corresponding author) 2 National Institute of Miners’ Health, Department of Occupational Hygiene, Nagpur, India 3 Indian Institute of Technology-Indian School of Mines (IIT-ISM), Department of Environmental Science and Engineering, Dhanbad, India Corresponding author's e-mail address: [email protected] ABSTRACT So far as mining industry is concerned, noise pollution is not new. It is generated from operation of equipment and plants for excavation and transport of minerals which affects mine employees as well as population residing in nearby areas. Although in the Recommendations of Tenth Conference on Safety in Mines, noise mapping has been made mandatory in Indian mines still mining industry are not giving proper importance on producing noise maps of mines. Noise mapping is preferred for visualization and its propagation in the form of noise contours so that preventive measures are planned and implemented. The study was conducted in an opencast mine in Central India. Sound sources were identified and noise measurements were carried out according to national and international standards. Considering source locations along with noise levels and other meteorological, geographical factors as inputs, noise maps were generated by Predictor LimA software. Results were evaluated in the light of Central Pollution Control Board norms as to whether noise exposure in the residential and industrial area were within prescribed limits or not. -

Chapter 1 Experiment-8
Chapter 1 Experiment-8 1.1 Single Sideband Suppressed Carrier Mod- ulation 1.1.1 Objective This experiment deals with the basic of Single Side Band Suppressed Carrier (SSB SC) modulation, and demodulation techniques for analog commu- nication.− The student will learn the basic concepts of SSB modulation and using the theoretical knowledge of courses. Upon completion of the experi- ment, the student will: *UnderstandSSB modulation and the difference between SSB and DSB modulation * Learn how to construct SSB modulators * Learn how to construct SSB demodulators * Examine the I Q modulator as SSB modulator. * Possess the necessary tools to evaluate and compare the SSB SC modulation to DSB SC and DSB_TC performance of systems. − − 1.1.2 Prelab Exercise 1.Using Matlab or equivalent mathematics software, show graphically the frequency domain of SSB SC modulated signal (see equation-2) . Which of the sign is given for USB− and which for LSB. 1 2 CHAPTER 1. EXPERIMENT-8 2. Draw a block diagram and explain two method to generate SSB SC signal. − 3. Draw a block diagram and explain two method to demodulate SSB SC signal. − 4. According to the shape of the low pass filter (see appendix-1), choose a carrier frequency and modulation frequency in order to implement LSB SSB modulator, with minimun of 30 dB attenuation of the USB component. 1.1.3 Background Theory SSB Modulation DEFINITION: An upper single sideband (USSB) signal has a zero-valued spectrum for f <fcwhere fc, is the carrier frequency. A lower single| | sideband (LSSB) signal has a zero-valued spectrum for f >fc where fc, is the carrier frequency. -

Designline PROFILE 42
High Performance Displays FLAT TV SOLUTIONS DesignLine PROFILE 42 Plasma FlatTV 106cm / 42" WWW.CONRAC.DE HIGH PERFORMANCE DISPLAYS FLAT TV SOLUTIONS DesignLine PROFILE 42 (106cm / 42 Zoll Diagonale) Neu: Verarbeitet HD-Signale ! New: HD-Compliant ! Einerseits eine bestechend klare Linienführung. Andererseits Akzente durch die farblich gestalteten Profilleisten in edler Metallic-Lackierung. Das Heimkino-Erlebnis par Excellence. Impressively clear lines teamed with decorative aluminium strips in metallic finish provide coloured highlights. The ultimate home cinema experience. Für höchste Ansprüche: Die FlatTVs der DesignLine kombinieren Hightech mit einzigartiger Optik. Die komplette Elektronik sowie die hochwertigen Breitband-Stereolautsprecher wurden komplett ins Gehäuse integriert. Der im Lieferumfang enthaltene Design-Standfuß aus Glas lässt sich für die Wandmontage einfach und problemlos entfernen, so dass das Display noch platzsparender wie ein Bild an der Wand angebracht werden kann. Die extrem flachen Bildschirme bieten eine unübertroffene Bildbrillanz und -schärfe. Das lüfterlose Konzept basiert auf dem neuesten Stand der Technik: Ohne störende Nebengeräusche hören Sie nur das, was Sie hören möchten. Einfaches Handling per Fernbedienung und mit übersichtlichem On-Screen-Menü. Die Kombination aus Flachdisplay-Technologie, einer High Performance Scaling Engine und einem zukunftsweisenden De-Interlacer* mit speziellen digitalen Algorithmen zur optimalen Darstellung bewegter Bilder bietet Ihnen ein unvergleichliches Fernseherlebnis. Zusätzlich vermittelt die Noise Reduction eine angenehme Bildruhe. For the most decerning tastes: DesignLine flat panel TVs combine advanced technology with outstanding appearance. All the electronics and the high-quality broadband stereo speakers have been fully integrated in the casing. The design glass stand included in the scope of supply can easily be removed for wall assembly, allowing the display to be mounted to the wall like a picture to save even more space. -

Loudspeaker FM and AM Distortion an 10
Loudspeaker FM and AM Distortion AN 10 Application Note to the KLIPPEL R&D SYSTEM The amplitude modulation of a high frequency tone f1 (voice tone) and a low frequency tone f2 (bass tone) is measured by using the 3D Distortion Measurement module (DIS) of the KLIPPEL R&D SYSTEM. The maximal variation of the envelope of the voice tone f1 is represented by the top and bottom value referred to the averaged envelope. The amplitude modulation distortion (AMD) is the ratio between the rms value of the variation referred to the averaged value and is comparable to the modulation distortion Ld2 and Ld3 of the IEC standard 60268 provided that the loudspeaker generates pure amplitude modulation of second- or third-order. The measurement of amplitude modulation distortion (AMD) allows assessment of the effects of Bl(x) and Le(x) nonlinearity and radiation distortion due to pure amplitude modulation without Doppler effect. CONTENTS: 1 Method of Measurement ............................................................................................................................... 2 2 Checklist for dominant modulation distortion ............................................................................................... 3 3 Using the 3D distortion measurement (DIS) .................................................................................................. 4 4 Setup parameters for DIS Module .................................................................................................................. 4 5 Example ......................................................................................................................................................... -
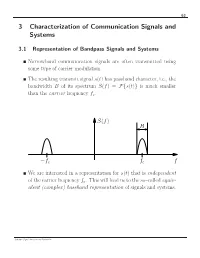
3 Characterization of Communication Signals and Systems
63 3 Characterization of Communication Signals and Systems 3.1 Representation of Bandpass Signals and Systems Narrowband communication signals are often transmitted using some type of carrier modulation. The resulting transmit signal s(t) has passband character, i.e., the bandwidth B of its spectrum S(f) = s(t) is much smaller F{ } than the carrier frequency fc. S(f) B f f f − c c We are interested in a representation for s(t) that is independent of the carrier frequency fc. This will lead us to the so–called equiv- alent (complex) baseband representation of signals and systems. Schober: Signal Detection and Estimation 64 3.1.1 Equivalent Complex Baseband Representation of Band- pass Signals Given: Real–valued bandpass signal s(t) with spectrum S(f) = s(t) F{ } Analytic Signal s+(t) In our quest to find the equivalent baseband representation of s(t), we first suppress all negative frequencies in S(f), since S(f) = S( f) is valid. − The spectrum S+(f) of the resulting so–called analytic signal s+(t) is defined as S (f) = s (t) =2 u(f)S(f), + F{ + } where u(f) is the unit step function 0, f < 0 u(f) = 1/2, f =0 . 1, f > 0 u(f) 1 1/2 f Schober: Signal Detection and Estimation 65 The analytic signal can be expressed as 1 s+(t) = − S+(f) F 1{ } = − 2 u(f)S(f) F 1{ } 1 = − 2 u(f) − S(f) F { } ∗ F { } 1 The inverse Fourier transform of − 2 u(f) is given by F { } 1 j − 2 u(f) = δ(t) + . -

Radio Communications in the Digital Age
Radio Communications In the Digital Age Volume 1 HF TECHNOLOGY Edition 2 First Edition: September 1996 Second Edition: October 2005 © Harris Corporation 2005 All rights reserved Library of Congress Catalog Card Number: 96-94476 Harris Corporation, RF Communications Division Radio Communications in the Digital Age Volume One: HF Technology, Edition 2 Printed in USA © 10/05 R.O. 10K B1006A All Harris RF Communications products and systems included herein are registered trademarks of the Harris Corporation. TABLE OF CONTENTS INTRODUCTION...............................................................................1 CHAPTER 1 PRINCIPLES OF RADIO COMMUNICATIONS .....................................6 CHAPTER 2 THE IONOSPHERE AND HF RADIO PROPAGATION..........................16 CHAPTER 3 ELEMENTS IN AN HF RADIO ..........................................................24 CHAPTER 4 NOISE AND INTERFERENCE............................................................36 CHAPTER 5 HF MODEMS .................................................................................40 CHAPTER 6 AUTOMATIC LINK ESTABLISHMENT (ALE) TECHNOLOGY...............48 CHAPTER 7 DIGITAL VOICE ..............................................................................55 CHAPTER 8 DATA SYSTEMS .............................................................................59 CHAPTER 9 SECURING COMMUNICATIONS.....................................................71 CHAPTER 10 FUTURE DIRECTIONS .....................................................................77 APPENDIX A STANDARDS -

Microwave Frequency Demodulation Using Two Coupled Optical Resonators with Modulated Refractive Index
PHYSICAL REVIEW APPLIED 15, 034056 (2021) Microwave Frequency Demodulation Using two Coupled Optical Resonators with Modulated Refractive Index Adam Mock * School of Engineering and Technology, Central Michigan University, Mount Pleasant, Michigan 48859, USA (Received 16 October 2020; revised 1 February 2021; accepted 10 February 2021; published 18 March 2021) Traditional electronic frequency demodulation of a microwave frequency voltage is challenging because it requires complicated phase-locked loops, narrowband filters with fixed passbands, or large footprint local oscillators and mixers. Herein, a different frequency demodulation concept is proposed based on refractive index modulation of two coupled microcavities excited by an optical wave. A frequency- modulated microwave frequency voltage is applied to two photonic crystal microcavities in a spatially odd configuration. The spatially odd perturbation causes coupling between the even and odd supermodes of the coupled-cavity system. It is shown theoretically and verified by finite-difference time-domain sim- ulations how careful choice of the modulation amplitude and frequency can switch the optical output from on to off. As the modulating frequency is detuned from its off value, the optical output switches from off to on. Ultimately, the optical output amplitude is proportional to the frequency deviation of the applied voltage making this device a frequency-modulated-voltage to amplitude-modulated-optical- wave converter. The optical output can be immediately detected and converted to a voltage that would result in a frequency-demodulated voltage signal. Or the optical output can be fed into a larger radio- over-fiber optical network. In this case the device presents a compact, low power, and tunable route for multiplexing frequency-modulated voltages with amplitude-modulated optical communication systems. -

AN9725LG Datasheet
AN9725LG Analog Logo Inserter System The AN9725LG Logo Inserter system is a complete analog logo insertion The onboard preview allows you to cue your logos for position and content package that will key one, or many, static/animated "bugs" over a composite verifi cation prior to going "On Air". analog video signal. Logos created in BMP, TIF or TGA fi le formats can be imported into the Evertz® Overture™ software and transferred to the The EAS crawl support allows for connection to an existing EAS decoder. This AN9725LG via Ethernet. RS–232 connection allows weekly tests (white text on green), watch alerts (white on yellow) and warnings (white on red) to be scrolled across the analog Logos are stored in fl ash memory and can be quickly accessed via front panel, video with no need for format conversion. The variable height text font can be quick select keys, GPI inputs, automation and Overture™. With the removable positioned anywhere on the screen and rendered with any TrueType font. Compact Flash option you can access up to 4GB of online logo storage space and virtually unlimited archived media storage. The TXT option allows for the creation of custom text messages that can be displayed as crawls or fi xed position fi elds on top of keyed graphic logos. The AN9725LG has been designed to manage and store multiple logos. Each These user–defi ned elements can be dynamically updated by Ethernet using logo size is variable and ranges from 1/25th to full screen. The position of the Overture™ software. Text crawls and fi elds retain display information such the logo, fade rates and animation rates are user–controllable. -

Lecture 25 Demodulation and the Superheterodyne Receiver EE445-10
EE447 Lecture 6 Lecture 25 Demodulation and the Superheterodyne Receiver EE445-10 HW7;5-4,5-7,5-13a-d,5-23,5-31 Due next Monday, 29th 1 Figure 4–29 Superheterodyne receiver. m(t) 2 Couch, Digital and Analog Communication Systems, Seventh Edition ©2007 Pearson Education, Inc. All rights reserved. 0-13-142492-0 1 EE447 Lecture 6 Synchronous Demodulation s(t) LPF m(t) 2Cos(2πfct) •Only method for DSB-SC, USB-SC, LSB-SC •AM with carrier •Envelope Detection – Input SNR >~10 dB required •Synchronous Detection – (no threshold effect) •Note the 2 on the LO normalizes the output amplitude 3 Figure 4–24 PLL used for coherent detection of AM. 4 Couch, Digital and Analog Communication Systems, Seventh Edition ©2007 Pearson Education, Inc. All rights reserved. 0-13-142492-0 2 EE447 Lecture 6 Envelope Detector C • Ac • (1+ a • m(t)) Where C is a constant C • Ac • a • m(t)) 5 Envelope Detector Distortion Hi Frequency m(t) Slope overload IF Frequency Present in Output signal 6 3 EE447 Lecture 6 Superheterodyne Receiver EE445-09 7 8 4 EE447 Lecture 6 9 Super-Heterodyne AM Receiver 10 5 EE447 Lecture 6 Super-Heterodyne AM Receiver 11 RF Filter • Provides Image Rejection fimage=fLO+fif • Reduces amplitude of interfering signals far from the carrier frequency • Reduces the amount of LO signal that radiates from the Antenna stop 2/22 12 6 EE447 Lecture 6 Figure 4–30 Spectra of signals and transfer function of an RF amplifier in a superheterodyne receiver. 13 Couch, Digital and Analog Communication Systems, Seventh Edition ©2007 Pearson Education, Inc. -

4430+ Composite Analogue to SDI ADC
DTL MiniBlox™ 4430+ Composite analogue to SDI ADC Features • Analogue composite to SDI ADC • Dual high speed oversampling 11-bit ADC’s • Digital TBC and jitter filter for greater output stability • Temporal frame recursive noise reduction • Motion adaptive 3D YC separation using a 5 line comb filter • Automatic gain control Description • Differential input to eliminate common mode ‘hum’ up to 6Vp-p The 4430+ is a broadcast quality composite analogue to SDI converter. • Extremely compact and rugged It uses dual 11 bit over sampling ADCs with 5 line • Locking connector for PSU adaptive comb filtering. Temporal noise reduction and Control switches 3D motion adaptive YC separation offer the highest • Pedestal control quality conversion on the market. The unit accepts PAL, • VBI blanking NTSC and SECAM analogue inputs. The input format is • Disable AGC automatically detected. • Disable jitter filter It is housed in an extremely compact and rugged aluminium case ideally suited to both studio and portable • Enable noise reduction applications. • Enable motion adaptive YC separation www.miniblox.com Specifications Analogue input Performance Standards Composite NTSC (J, M, 4.43), PAL (B, D, G, H, I, Differential gain <1.5% M, N, Nc, 60) and SECAM (B, D, G, K, K1, L) Composite PAL, NTSC & SECAM Differential phase <0.4° Connector 75Ω BNCs Power Signal level 1V p-p nominal Voltage 6-12V DC Return loss >40dB to 5.5MHz Current 600mA at 6V CMR >6Vp-p Power connector Locking 2.5mm jack connector (centre +ve) SDI output Other Standards SMPTE 259M 270Mb/s 525/625 SDI LED Shows power and signal Connector 75Ω BNC Temperature range 0˚C to 40˚C Number 2 Dimensions 63.5mm x84mm x30mm (excluding connectors) Signal level 800mV p-p ±10% (terminated) Weight 180g Jitter <0.15UI with colour bars input Return loss >18dB to 270MHz Ordering information 4430+ Composite analogue to SDI ADC 4006 Desktop power supply with IEC320 C14 inlet 4010 1U rack mounting frame for up to 5 units including PSU We reserve the right to change technical specifications without prior notice.