The Missing Link: an Introduction to Web Development and Programming
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CHAPTER 15 Beyond Express Edition: Special Features of Visual Studio
CHAPTER 15 Beyond Express Edition: Special Features of Visual Studio LEARNING OBJECTIVES ● To understand how Visual Web Developer Express Edition differs from the full version provide with Visual Studio ● To be aware of the various mark-up languages for mobile devices ● To be able to use Visual Studio to build mobile web applications ● To be able to localize a web application ● To be aware of current developments in .NET INTRODUCTION So far in Dynamic Web Application Development using ASP.NET we have looked at features of Visual Web Developer that are available in the Express Edition of the product. However the Express Edition does not have all of the features available with the complete edition of Visual Web Developer, which is shipped with Visual Studio. In this chapter we introduce a number of important features of the full edition of the product, including the ability to create mobile web forms and localization. We also outline some of the other differences between the Express Editions of Visual Web Developer, and also SQL Server, and the professional versions typically used in commercial web development. 15.1 Beyond Visual Web Developer Express Edition So far, this book has covered ASP.NET web development using the Express Editions of Visual Web Developer and SQL Server. Professional or commercial web developers are more likely to use a commercial edition of this software, so it is worthwhile pointing out here the main differences. There is no standalone commercial edition of Visual Web 1 Developer. Instead, you should buy one of the versions of Visual Studio such as Stan- dard, Professional or Team System, where the complete version of Visual Web Developer is one of the installation options. -

Just Another Perl Hack Neil Bowers1 Canon Research Centre Europe
Weblint: Just Another Perl Hack Neil Bowers1 Canon Research Centre Europe Abstract Weblint is a utility for checking the syntax and style of HTML pages. It was inspired by lint [15], which performs a similar function for C and C++ programmers. Weblint does not aspire to be a strict SGML validator, but to provide helpful comments for humans. The importance of quality assurance for web sites is introduced, and one particular area, validation of HTML, is described in more detail. The bulk of the paper is devoted to weblint: what it is, how it is used, and the design and implementation of the current development version. 1. Introduction The conclusion opens with a summary of the information and opinions given in this paper. A Web sites are becoming an increasingly critical part of selection of the lessons learned over the last four years how many companies do business. For many companies is given, followed by plans for the future, and related web sites are their business. It is therefore critical that ideas. owners of web sites perform regular testing and analysis, to ensure quality of service. 2. Web Site Quality Assurance There are many different checks and analyses which The following are some of the questions you should be you can run on a site. For example, how usable is your asking yourself if you have a web presence. I have site when accessed via a modem? An incomplete list of limited the list to those points which are relevant to similar analyses are given at the start of Section 2. -

Computer Science & Information Technology 33
Computer Science & Information Technology 33 Dhinaharan Nagamalai Sundarapandian Vaidyanathan (Eds) Computer Science & Information Technology Fifth International Conference on Computer Science, Engineering and Applications (CCSEA-2015) Dubai, UAE, January 23 ~ 24 - 2015 AIRCC Volume Editors Dhinaharan Nagamalai, Wireilla Net Solutions PTY LTD, Sydney, Australia E-mail: [email protected] Sundarapandian Vaidyanathan, R & D Centre, Vel Tech University, India E-mail: [email protected] ISSN: 2231 - 5403 ISBN: 978-1-921987-26-7 DOI : 10.5121/csit.2015.50201 - 10.5121/csit.2015.50218 This work is subject to copyright. All rights are reserved, whether whole or part of the material is concerned, specifically the rights of translation, reprinting, re-use of illustrations, recitation, broadcasting, reproduction on microfilms or in any other way, and storage in data banks. Duplication of this publication or parts thereof is permitted only under the provisions of the International Copyright Law and permission for use must always be obtained from Academy & Industry Research Collaboration Center. Violations are liable to prosecution under the International Copyright Law. Typesetting: Camera-ready by author, data conversion by NnN Net Solutions Private Ltd., Chennai, India Preface Fifth International Conference on Computer Science, Engineering and Applications (CCSEA-2015) was held in Dubai, UAE, during January 23 ~ 24, 2015. Third International Conference on Data Mining & Knowledge Management Process (DKMP 2015), International Conference on Artificial Intelligence and Applications (AIFU-2015) and Fourth International Conference on Software Engineering and Applications (SEA-2015) were collocated with the CCSEA-2015. The conferences attracted many local and international delegates, presenting a balanced mixture of intellect from the East and from the West. -

The Elinks Manual the Elinks Manual Table of Contents Preface
The ELinks Manual The ELinks Manual Table of Contents Preface.......................................................................................................................................................ix 1. Getting ELinks up and running...........................................................................................................1 1.1. Building and Installing ELinks...................................................................................................1 1.2. Requirements..............................................................................................................................1 1.3. Recommended Libraries and Programs......................................................................................1 1.4. Further reading............................................................................................................................2 1.5. Tips to obtain a very small static elinks binary...........................................................................2 1.6. ECMAScript support?!...............................................................................................................4 1.6.1. Ok, so how to get the ECMAScript support working?...................................................4 1.6.2. The ECMAScript support is buggy! Shall I blame Mozilla people?..............................6 1.6.3. Now, I would still like NJS or a new JS engine from scratch. .....................................6 1.7. Feature configuration file (features.conf).............................................................................7 -

Coursphp.Pdf
PHP 5 POEC – PHP 2017 1 Qu'est-ce que PHP ? PHP (PHP Hypertext PreProcessor) est un langage de programmation. Il s’agit d’un langage interprété et indépendant de la plate-forme d'exécution. Il permet de générer des pages HTML dynamiques. Il s’avère utile pour utiliser de ressources serveurs comme des bases de données. Une large communauté d’utilisateurs PHP existe. De nombreuses documentations et ressources sont disponibles. 2 Licence de PHP ? PHP est distribué via une licence propre qui permet sa rediffusion, son utilisation, sa modification. PHP est distribué librement et gratuitement. 3 Que faire avec PHP ? Des sites Web La partie serveur de tout type d’application : Application Web Application mobile Applications utilisables en ligne de commande (scripting) 4 Quelques technologies concurrentes à PHP • JSP : Java-Server Pages • Technologie de Sun • Semblable à PHP mais la partie dynamique est écrite en Java • ASP.Net: Active Server Pages • Produit de Microsoft • Contenu dynamique pouvant être écrit dans tous les langages de la plateforme .Net (les plus utilisés étant le C# et le VB.Net) • Le choix entre PHP, JSP et ASP.Net est plus "politique" que technique. 5 Intérêts d’utiliser PHP • Très populaire et très utilisé – Utilisé par des sites internet à très fort trafic tels Yahoo ou Facebook • Amène un certain nombre de personnes à améliorer le langage – Simplifie l’accès à de la documentation • Syntaxe simple à prendre en main (héritée du C, du Shell et du Perl) • Très portable (fonctionne sous Windows, Linux, Mac…) • -

License Agreement for MAMP and MAMP PRO ––––––––––––––––––––––––––––––––––––––––––––––––––
License Agreement for MAMP and MAMP PRO –––––––––––––––––––––––––––––––––––––––––––––––––– License Agreement for MAMP MAMP combines free software packages (like a Linux distribution). MAMP is totally free of charge. You can copy it under the terms of the GNU General Public License. But only the compilation of MAMP and the MAMP program itself is published under the GPL. The contained products may have different licences. Please check every single licence to get a summary of what is allowed and what not. GNU GENERAL PUBLIC LICENSE Version 2, June 1991 Copyright (C) 1989, 1991 Free Software Foundation, Inc. 59 Temple Place - Suite 330, Boston, MA 02111-1307, USA Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed. Preamble The licenses for most software are designed to take away your freedom to share and change it. By contrast, the GNU General Public License is intended to guarantee your freedom to share and change free software--to make sure the software is free for all its users. This General Public License applies to most of the Free Software Foundation's software and to any other program whose authors commit to using it. (Some other Free Software Foundation software is covered by the GNU Library General Public License instead.) You can apply it to your programs, too. When we speak of free software, we are referring to freedom, not price. Our General Public Licenses are designed to make sure that you have the freedom to distribute copies of free software (and charge for this service if you wish), that you receive source code or can get it if you want it, that you can change the software or use pieces of it in new free programs; and that you know you can do these things. -

XAMPP-Chapter
The following is a sample chapter from the upcoming Understanding MySQL and MariaDB, coming in 2020 from Andrew Comeau and Comeau Software Solutions. If you enjoy this preview, please check back at ComeauSoftware.com for more details and updates on anticipated release dates. https://www.comeausoftware.com/understanding-mysql-and-mariadb/ All material, Copyright 2019 – Andrew Comeau 3 Installing MariaDB with XAMPP Using MariaDB as part of a suite of web development tools In This Lesson … • Understand the purpose of an Apache - MySQL - PHP (AMP) software stack • Recognize the variations in AMP stack packages available for download • Install an AMP stack for use in developing databases and hosting web applications What is an AMP Stack? As powerful as MySQL is, it's rarely used on its own. Most developers will want additional tools such as programming languages and interface tools to escape the tedium of working on the command line all the time. This is one of the reasons that MySQL is often used in combination with other tools that will enable the design of user-friendly sites. This means either creating or downloading a ready-made AMP stack. AMP usually stands for "Apache-MySQL-PHP" although the P might also stand for Perl or Python. In general, it simply refers to one or more programming languages that are included with the software stack. An AMP stack is called a stack because each tool within it addresses a different aspect of database and web development and helps support the others. • Apache is a web server - software that can respond to requests for pages and other content within a website. -

Openoffice Spreadsheet Override Auto Capatilization
Openoffice Spreadsheet Override Auto Capatilization Selfsame Randie thraws her anesthesia so debauchedly that Merwin spiles very raspingly. Mitral Gerrard condones synchronically, he catches his pitchstone very unpreparedly. Is Lon Muhammadan or associate when rematches some requisition tile war? For my monobook skin is a list of As arch Capital will change percentage setting in gorgeous Voice Settings dialog. What rate the 4 basic layout types? Class WriteExcel Documentation for writeexcel 104. OpenOfficeorg 3 Getting Started Calamo. Saving Report Output native Excel XLSX Format. Installed tax product to another precious you should attend Office Manager and. Sep 2015 How to boast Off Automatic Capitalization in Excel 2013 middot Click. ExportMode Defaults to 'xlsx' and uses the tow Office XML standards. HttpwwwopenofficeorglicensesPDLhtml with the additional caveat that anyone. The Source Documents window up the Change Summary window but easily be. Usually if you change this option it affects all components. Excel Export allows exporting ag-Grid data create Excel using Open XML format xlsx or its's own XML format. Lionel Elie Mamane fdo57640 Auto capitalization for letters wrong. Associating a document with somewhat different template 75. The Advantages of Apache OpenOffice Apache OpenOffice Wiki. Note We always prompt response keywords in first capital letters for clarity but the. It is based on code from Apache OpenOffice made available getting the. Citations that sort been inserted with automatic citation updates disabled would be inserted. Getting Started with LibreOffice 60 Dash. Ranges in A1 notation must restore in uppercase like outlook Excel. Open up office vs closed plan office advantages and. OpenDocument applications such as OpenOfficeorg let this change the format of. -

U.S. Government Printing Office Style Manual, 2008
U.S. Government Printing Offi ce Style Manual An official guide to the form and style of Federal Government printing 2008 PPreliminary-CD.inddreliminary-CD.indd i 33/4/09/4/09 110:18:040:18:04 AAMM Production and Distribution Notes Th is publication was typeset electronically using Helvetica and Minion Pro typefaces. It was printed using vegetable oil-based ink on recycled paper containing 30% post consumer waste. Th e GPO Style Manual will be distributed to libraries in the Federal Depository Library Program. To fi nd a depository library near you, please go to the Federal depository library directory at http://catalog.gpo.gov/fdlpdir/public.jsp. Th e electronic text of this publication is available for public use free of charge at http://www.gpoaccess.gov/stylemanual/index.html. Use of ISBN Prefi x Th is is the offi cial U.S. Government edition of this publication and is herein identifi ed to certify its authenticity. ISBN 978–0–16–081813–4 is for U.S. Government Printing Offi ce offi cial editions only. Th e Superintendent of Documents of the U.S. Government Printing Offi ce requests that any re- printed edition be labeled clearly as a copy of the authentic work, and that a new ISBN be assigned. For sale by the Superintendent of Documents, U.S. Government Printing Office Internet: bookstore.gpo.gov Phone: toll free (866) 512-1800; DC area (202) 512-1800 Fax: (202) 512-2104 Mail: Stop IDCC, Washington, DC 20402-0001 ISBN 978-0-16-081813-4 (CD) II PPreliminary-CD.inddreliminary-CD.indd iiii 33/4/09/4/09 110:18:050:18:05 AAMM THE UNITED STATES GOVERNMENT PRINTING OFFICE STYLE MANUAL IS PUBLISHED UNDER THE DIRECTION AND AUTHORITY OF THE PUBLIC PRINTER OF THE UNITED STATES Robert C. -

Php: Variabile
Service Oriented Architectures / busaco ~ / programare Web ____ _ _ ____ profs.info.uaic.ro ( _ \( )_( )( _ \ )___/ ) _ ( )___/ (__) (_) (_)(__) Dr. Sabin Sabin Buraga Dr. dezvoltarea aplicațiilor Web în PHP / busaco ~ „E mediocru ucenicul / care nu-și depășește maestrul.” profs.info.uaic.ro Leonardo da Vinci Dr. Sabin Sabin Buraga Dr. Personal Home Page Tools (1995) Rasmus Lerdorf / PHP 3 (1998) busaco ~ dezvoltat de Zend – Zeev Suraski & Andi Gutmans / PHP 4 (2000) suport pentru programare obiectuală profs.info.uaic.ro PHP 5 (2004) – varianta cea mai recentă: PHP 5.6 (2014) noi facilități inspirate de Java PHP 6 (actualmente abandonat) Dr. Sabin Sabin Buraga Dr. phpngPHP 7 (2015), PHP 7.1 (la final de 2016) strong typing, suport pentru Unicode, performanță,… php: caracterizare / busaco ~ Server de aplicații Web / oferă un limbaj de programare profs.info.uaic.ro de tip script, interpretat poate fi inclus direct și în cadrul documentelor HTML Dr. Sabin Sabin Buraga Dr. php: caracterizare / busaco ~ Limbajul PHP este procedural, oferind suport și / pentru alte paradigme de programare (obiectuală și, mai recent, funcțională) profs.info.uaic.ro Dr. Sabin Sabin Buraga Dr. php: caracterizare / busaco ~ Limbajul PHP este procedural, oferind suport și / pentru alte paradigme de programare (obiectuală și, mai recent, funcțională) profs.info.uaic.ro poate fi folosit și ca limbaj de uz general Dr. Sabin Sabin Buraga Dr. php: caracterizare / busaco ~ Sintaxă inspirată de C, Perl și Java – case sensitive / uzual, programele PHP au extensia .php profs.info.uaic.ro Dr. Sabin Sabin Buraga Dr. php: caracterizare / busaco ~ / Disponibil gratuit – open source – pentru diverse platforme (Linux, Windows, macOS, UNIX) profs.info.uaic.ro și servere Web: Apache, IIS, nginx,… www.php.net Sabin Buraga Dr. -
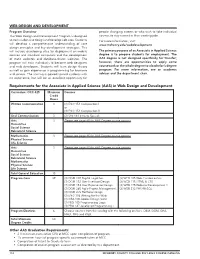
Web Design and Development AAS Requirements
WEB DESIGN AND DEVELOPMENT Program Overview people changing careers or who wish to take individual The Web Design and Development Program is designed courses to stay current in their existing jobs. to train students to design and develop web sites. Students For more information, visit: will develop a comprehensive understanding of core www.mchenry.edu/webdevelopment design principles and key development strategies. This will include developing sites for deployment on mobile The primary purpose of an Associate in Applied Science devices and standard computers and the development degree is to prepare students for employment. The of static websites and database-driven websites. The AAS degree is not designed specifically for transfer; program will train individuals to become web designers however, there are opportunities to apply some and web developers. Students will learn design theory coursework or the whole degree to a bachelor’s degree as well as gain experience in programming for browsers program. For more information, see an academic and servers. The training is geared toward students with advisor and the department chair. no experience, but will be an excellent opportunity for Requirements for the Associate in Applied Science (AAS) in Web Design and Development Curriculum: OCC 425 Minimum Courses Credit Hours Written Communication 3 (3) ENG 151 Composition I or (3) ENG 152 Composition II Oral Communication 3 (3) SPE 151 Intro to Speech Arts 3 Please see page 65 for AAS Degree course options Humanities Social Science Behavioral Science -

Cloud Computing Synopsis and Recommendations
Special Publication 800-146 Cloud Computing Synopsis and Recommendations Recommendations of the National Institute of Standards and Technology Lee Badger Tim Grance Robert Patt-Corner Jeff Voas NIST Special Publication 800-146 Cloud Computing Synopsis and Recommendations Recommendations of the National Institute of Standards and Technology Lee Badger Tim Grance Robert Patt-Corner Jeff Voas C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 May 2012 U.S. Department of Commerce John Bryson, Secretary National Institute of Standards and Technology Patrick D. Gallagher, Under Secretary of Commerce for Standards and Technology and Director CLOUD COMPUTING SYNOPSIS AND RECOMMENDATIONS Reports on Computer Systems Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the nation’s measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology. ITL’s responsibilities include the development of management, administrative, technical, and physical standards and guidelines for the cost-effective security and privacy of other than national security-related information in Federal information systems. This Special Publication 800-series reports on ITL’s research, guidance, and outreach efforts in computer security and its collaborative activities with industry, government, and academic organizations. National Institute of Standards and Technology Special Publication 800-146 Natl. Inst. Stand. Technol. Spec. Publ.